Proceedings of the 4Th Annual Linux Showcase & Conference, Atlanta
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Childnodes 1
Index Home | Projects | Docs | Jargon Bugzilla | LXR | Tree Status | Checkins Feedback | FAQ | Search A - B - C - D - E - F - G - H - I - J - K - L - M - N - O - P - Q - R - S - T - U - V - W - X - Y - Z Index Symbols _content 1 A addEventListener 1 alert() 1 align 1 alinkColor 1 anchors 1 appCodeName 1 appendChild 1 applets 1 appName 1 appVersion 1 attributes 1, 2 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (1 de 20) [09/06/2003 9:55:09] Index availLeft 1 availTop 1 availWidth 1 B back() 1 bgColor 1 blur 1 blur() 1 body 1 C captureEvents() 1 characterSet 1 childNodes 1 clear 1 clearInterval() 1 clearTimeout() 1 click 1 cloneContents 1 cloneNode 1 cloneRange 1 close 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (2 de 20) [09/06/2003 9:55:09] Index close() 1 closed 1 collapse 1 collapsed 1 colorDepth 1 commonAncestorContainer 1 compareBoundaryPoints 1 Components 1 confirm() 1 contentDocument 1, 2 contentWindow 1, 2 controllers 1 cookie 1 cookieEnabled 1 createAttribute 1 createDocumentFragment 1 createElement 1 createRange 1 createTextNode 1 crypto 1 cssRule 1 cssRule Object 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (3 de 20) [09/06/2003 9:55:09] Index cssRules 1 cssText 1 D defaultStatus 1 deleteContents 1 deleteRule 1 detach 1 directories 1 disabled 1 dispatchEvent 1 doctype 1 document 1 documentElement 1 DOM 1, 2 DOM 2 Range Interface 1 DOM window Interface 1 domain 1 dump() 1 E Elements Interface 1 embeds 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (4 de 20) [09/06/2003 9:55:09] -

TRABAJO DE DIPLOMA Título: Diseño De La Página Web De Antenas
FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Título: Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos Tutor: Dr. Roberto Jiménez Hernández Santa Clara 2006 “Año de la Revolución Energética en Cuba” Universidad Central “Marta Abreu” de Las Villas FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TTRRAABBAAJJOO DDEE DDIIPPLLOOMMAA Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos e-mail: [email protected] Tutor: Dr. Roberto Jiménez Hernández Prof. Dpto. de Telecomunicaciones y electrónica Facultad de Ing. Eléctrica. UCLV. e-mail: [email protected] Santa Clara Curso 2005-2006 “Año de la Revolución Energética en Cuba” Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO “El néctar de la victoria se bebe en la copa del sacrificio” DEDICATORIA Dedico este trabajo a mis padres, a mí hermana y a mi novia por ser las personas más hermosas que existen y a las cuales les debo todo. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Visual Validation of SSL Certificates in the Mozilla Browser Using Hash Images
CS Senior Honors Thesis: Visual Validation of SSL Certificates in the Mozilla Browser using Hash Images Hongxian Evelyn Tay [email protected] School of Computer Science Carnegie Mellon University Advisor: Professor Adrian Perrig Electrical & Computer Engineering Engineering & Public Policy School of Computer Science Carnegie Mellon University Monday, May 03, 2004 Abstract Many internet transactions nowadays require some form of authentication from the server for security purposes. Most browsers are presented with a certificate coming from the other end of the connection, which is then validated against root certificates installed in the browser, thus establishing the server identity in a secure connection. However, an adversary can install his own root certificate in the browser and fool the client into thinking that he is connected to the correct server. Unless the client checks the certificate public key or fingerprint, he would never know if he is connected to a malicious server. These alphanumeric strings are hard to read and verify against, so most people do not take extra precautions to check. My thesis is to implement an additional process in server authentication on a browser, using human recognizable images. The process, Hash Visualization, produces unique images that are easily distinguishable and validated. Using a hash algorithm, a unique image is generated using the fingerprint of the certificate. Images are easily recognizable and the user can identify the unique image normally seen during a secure AND accurate connection. By making a visual comparison, the origin of the root certificate is known. 1. Introduction: The Problem 1.1 SSL Security The SSL (Secure Sockets Layer) Protocol has improved the state of web security in many Internet transactions, but its complexity and neglect of human factors has exposed several loopholes in security systems that use it. -

Mozbackup 1.4.8) - Add: FS#152 - New Graphic for Mozbackup 1.4.8 - Fix: FS#143 - ZIP Version Should Contains Directory
Changelog (since MozBackup 1.4) ------------------------------- (MozBackup 1.4.8) - Add: FS#152 - New graphic for MozBackup 1.4.8 - Fix: FS#143 - ZIP version should contains directory (MozBackup 1.4.8 Beta) - Fix: FS#120 - Check Czech localization - Fix: FS#123 - language file hasn't applied correctry - Fix: FS#141 - Spelling error on component selection screen. (MozBackup 1.4.8 Alpha) - Add: FS#1 - Backup file urlbarhistory.sqlite from SeaMonkey 2.0 profile - Add: FS#6 - Add support for Netscape 9 - Add: FS#7 - Add support for logging - Add: FS#8 - Add support for SeaMonkey 2.0 - Add: FS#9 - Add support for Flock - Add: FS#10 - Add support for Sunbird - Add: FS#11 - Migrate to Nullsoft installer - Add: FS#13 - Add support for Firefox/Thunderbird portable - Add: FS#16 - Add option for disable password question dialog - Add: FS#22 - Option to save unsupported files from profile - Add: FS#18 - Enable extensions backup by default - Add: FS#38 - Add test if backup's file is ok after backup - Add: FS#39 - Rename Backup.exe to MozBackup.exe - Add: FS#45 - Backup file urlclassifier3.sqlite from profile - Add: FS#48 - backup.ini / fileformat: Add "Day of Week" (Monday, ...) - Add: FS#67 - Support for Netscape Messenger 9.0 - Add: FS#69 - Add license information to all source files - Add: FS#70 - Create profile for MozBackup - Add: FS#73 - Create documentation for compilation of MozBackup - Add: FS#75 - Add new bookmarks* files to backup process - Add: FS#77 - Backup new signons3.txt file. - Add: FS#81 - Backup file cert_override.txt - Add: FS#82 -
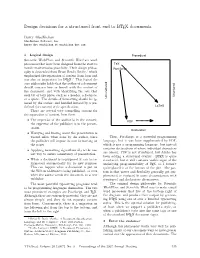
Design Decisions for a Structured Front End to LATEX Documents
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Mozilla: a Users Guide
Mozilla: A Users Guide. or Using the Mozilla Application Suite Kevin T. Neely October 17, 2003 Contents 1 Installation 15 1.1 Deciding which Mozilla to Run ........................ 15 1.1.1 Platform ................................. 15 1.1.2 Version .................................. 15 1.2 Installing Mozilla ................................ 16 1.2.1 Using an Installer Package ....................... 16 1.2.2 Manual Installation ........................... 17 1.3 Upgrading .................................... 19 1.3.1 Make a Backup ............................. 19 1.3.2 Uninstall ................................. 19 1.3.3 Install Mozilla .............................. 20 1.3.4 Retrieve Missing Files ......................... 20 1.4 Running Multiple versions of Mozilla ..................... 21 2 Getting Started and Mozilla Basics 23 2.1 Starting Mozilla ................................. 23 2.2 Exiting Mozilla ................................. 23 2.2.1 QuickLaunch .............................. 23 3 CONTENTS CONTENTS 2.3 Preferences ................................... 24 2.4 Advanced Settings ............................... 24 2.4.1 prefs.js .................................. 25 2.4.2 user.js .................................. 25 2.4.3 userContent.css ............................. 26 2.5 Profiles ...................................... 27 2.6 Themes ..................................... 27 2.7 Security ..................................... 27 2.7.1 Passwords ................................ 27 2.8 Cookies .................................... -

Community Tools Why? “It’S Really the Drupal Community and Not So Much the So!Tware That Makes the Drupal Project What It Is
Drupal Community Tools Why? “It’s really the Drupal community and not so much the so!tware that makes the Drupal project what it is. So fostering the Drupal community is actually more important than just managing the code base.” - Dries Buytaert Our tools ‣ Communication tools • Community websites • Issue queues • IRC ‣ Local development environment • AMP stack • Git Community Websites drupal.org groups.drupal.org groups.drupal.org groups.drupal.org groups.drupal.org groups.drupal.org api.drupal.org association.drupal.org drupalladder.org Drupal.org account Also gets you in to: ‣ groups.drupal.org ‣ api.drupal.org ‣ association.drupal.org ‣ DrupalCon sites Do it now. Do it now. Do it now. The Issue Queue The community todo list Dreditor ‣ Makes the issue queue easier to work with ‣ Is a browser user script (not a module) ‣ http://drupal.org/project/dreditor IRC (Internet Relay Chat) What you need to use IRC ‣ IRC client ‣ IRC Network to connect to ‣ Channels to join ‣ Nickname IRC Clients ‣ Web-based clients • webchat.freenode.net ‣ Application clients • Pidgin (Adium on Mac) - pidgin.im • ChatZilla (Firefox extension) Networks ‣ Over 650 networks ‣ Most Open Source projects use the Freenode network • irc.freenode.net Channels ‣ Freenode has over 10,000 public channels ‣ The Drupal community has over 100 channels • drupal.org/irc ‣ Drupal channel names all start with # Nicknames ‣ Someone might already have the name you want ‣ Register your nick Let’s do it ‣ Pidgin (http://pidgin.im) • Mac OS X: Adium • Windows: Pidgin • Ubuntu: Pidgin shipped with it • Linux: see if there is a package Local Dev Environment Not just for programmers What? ‣ A Development Environment is a collection of procedures and tools for developing, testing and debugging an application or program. -

Solaris 10 1106 Package List
Solaris 10 11/06 Package List Oracle Corporation 500 Oracle Parkway Redwood City, CA 94065 U.S.A. Part No: 819–6399–10 November 2006 Copyright © 2006, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract,and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007).