Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rooted Elements a Kinesthetic Approach Connecting Our Children to Their Nnei R and Outer World Alisha Meyer the University of Montana
University of Montana ScholarWorks at University of Montana Graduate Student Theses, Dissertations, & Graduate School Professional Papers 2012 Rooted Elements A Kinesthetic Approach Connecting Our Children to Their nneI r and Outer World Alisha Meyer The University of Montana Let us know how access to this document benefits ouy . Follow this and additional works at: https://scholarworks.umt.edu/etd Recommended Citation Meyer, Alisha, "Rooted Elements A Kinesthetic Approach Connecting Our Children to Their nneI r and Outer World" (2012). Graduate Student Theses, Dissertations, & Professional Papers. 1385. https://scholarworks.umt.edu/etd/1385 This Professional Paper is brought to you for free and open access by the Graduate School at ScholarWorks at University of Montana. It has been accepted for inclusion in Graduate Student Theses, Dissertations, & Professional Papers by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. ROOTED ELEMENTS A KINESTHETIC APPROACH CONNECTING OUR CHILDREN TO THEIR INNER AND OUTER WORLD By ALISHA BRIANNE MEYER BA Elementary Education, University of Montana, Missoula, Montana, 2003 Professional Paper presented in partial fulfillment of the requirements for the degree of Master of Arts Fine Arts, Integrated Arts and Education The University of Montana Missoula, MT May 2012 Approved by: Sandy Ross, Associate Dean of The Graduate School Graduate School Karen Kaufmann, Chair Fine Arts Jillian Campana, Committee Member Fine Arts Rick Hughes, Committee Member Fine Arts © COPYRIGHT by Alisha Brianne Meyer 2012 All Rights Reserved ii Meyer, Alisha, M.A., May 2012 Integrating Arts into Education Rooted Elements Chairperson: Karen Kaufmann Rooted Elements is a thematic naturalistic guide for classroom teachers to design engaging lessons focused in the earth elements. -

The Underpainter
Canadian Literature / Littérature canadienne A Quarterly of Criticism and Review Number 212, Spring 212 Published by The University of British Columbia, Vancouver Editor: Margery Fee Associate Editors: Judy Brown (Reviews), Joël Castonguay-Bélanger (Francophone Writing), Glenn Deer (Poetry), Laura Moss (Reviews) Past Editors: George Woodcock (1959–1977), W.H. New (1977–1995), Eva-Marie Kröller (1995–23), Laurie Ricou (23–27) Editorial Board Heinz Antor University of Cologne Alison Calder University of Manitoba Cecily Devereux University of Alberta Kristina Fagan University of Saskatchewan Janice Fiamengo University of Ottawa Carole Gerson Simon Fraser University Helen Gilbert University of London Susan Gingell University of Saskatchewan Faye Hammill University of Strathclyde Paul Hjartarson University of Alberta Coral Ann Howells University of Reading Smaro Kamboureli University of Guelph Jon Kertzer University of Calgary Ric Knowles University of Guelph Louise Ladouceur University of Alberta Patricia Merivale University of British Columbia Judit Molnár University of Debrecen Lianne Moyes Université de Montréal Maureen Moynagh St. Francis Xavier University Reingard Nischik University of Constance Ian Rae King’s University College Julie Rak University of Alberta Roxanne Rimstead Université de Sherbrooke Sherry Simon Concordia University Patricia Smart Carleton University David Staines University of Ottawa Cynthia Sugars University of Ottawa Neil ten Kortenaar University of Toronto Marie Vautier University of Victoria Gillian Whitlock University -

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -

Wertheimer, Editor Imagining the Seth Farber an American Orthodox American Jewish Community Dreamer: Rabbi Joseph B
Imagining the American Jewish Community Brandeis Series in American Jewish History, Culture, and Life Jonathan D. Sarna, Editor Sylvia Barack Fishman, Associate Editor For a complete list of books in the series, visit www.upne.com and www.upne.com/series/BSAJ.html Jack Wertheimer, editor Imagining the Seth Farber An American Orthodox American Jewish Community Dreamer: Rabbi Joseph B. Murray Zimiles Gilded Lions and Soloveitchik and Boston’s Jeweled Horses: The Synagogue to Maimonides School the Carousel Ava F. Kahn and Marc Dollinger, Marianne R. Sanua Be of Good editors California Jews Courage: The American Jewish Amy L. Sales and Leonard Saxe “How Committee, 1945–2006 Goodly Are Thy Tents”: Summer Hollace Ava Weiner and Kenneth D. Camps as Jewish Socializing Roseman, editors Lone Stars of Experiences David: The Jews of Texas Ori Z. Soltes Fixing the World: Jewish Jack Wertheimer, editor Family American Painters in the Twentieth Matters: Jewish Education in an Century Age of Choice Gary P. Zola, editor The Dynamics of American Jewish History: Jacob Edward S. Shapiro Crown Heights: Rader Marcus’s Essays on American Blacks, Jews, and the 1991 Brooklyn Jewry Riot David Zurawik The Jews of Prime Time Kirsten Fermaglich American Dreams and Nazi Nightmares: Ranen Omer-Sherman, 2002 Diaspora Early Holocaust Consciousness and and Zionism in Jewish American Liberal America, 1957–1965 Literature: Lazarus, Syrkin, Reznikoff, and Roth Andrea Greenbaum, editor Jews of Ilana Abramovitch and Seán Galvin, South Florida editors, 2001 Jews of Brooklyn Sylvia Barack Fishman Double or Pamela S. Nadell and Jonathan D. Sarna, Nothing? Jewish Families and Mixed editors Women and American Marriage Judaism: Historical Perspectives George M. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Tvorba Interaktivního Animovaného Příběhu
Středoškolská technika 2014 Setkání a prezentace prací středoškolských studentů na ČVUT Tvorba interaktivního animovaného příběhu Sami Salama Střední průmyslová škola na Proseku Novoborská 2, 190 00 Praha 9 1 Obsah 1 Obsah .................................................................................................................. 1 2 2D grafika (základní pojmy) ................................................................................. 3 2.1 Základní vysvětlení pojmu (počítačová) 2D grafika ....................................... 3 2.2 Rozdíl - 2D vs. 3D grafika .............................................................................. 3 2.3 Vektorová grafika ........................................................................................... 4 2.4 Rastrová grafika ............................................................................................ 6 2.5 Výhody a nevýhody rastrové grafiky .............................................................. 7 2.6 Rozlišení ........................................................................................................ 7 2.7 Barevná hloubka............................................................................................ 8 2.8 Základní grafické formáty .............................................................................. 8 2.9 Druhy komprese dat ...................................................................................... 9 2.10 Barevný model .......................................................................................... -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Installation of Apache Openmeetings 3.3.2 on Macos Sierra 10.12.6 It Is
Installation of Apache OpenMeetings 3.3.2 on macOS Sierra 10.12.6 It is tested with positive result. We will use the Apache's binary version OpenMeetings 3.3.2 stable, that is to say will suppress his compilation. It is done step by step. 22-9-2017 Starting.… 1) ------ Installation of Command line developer tools ------ We´ll install in first place the developer tools, that will help us to compile the sources. Run the shell as administrator, not as root, and install: xcode-select --install ...will open a window informing: Pag 1 clic Install button only, and will open other window. clic Agree button Pag 2 ...and will download and install the software ...telling when it finished ...clic Done. 2) ------ Installation of Homebrew ------ Homebrew install software. It is on Mac the same that apt-get on Debian or Ubuntu, yum on Centos or dnf on Fedora, for example. Install it: ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)" Pag 3 brew doctor ...and update: brew update 3) ------ Installation of need it paquets ------ Will install wget to download files, and ghostscript. After the installation, will ask to run a commands. Attention!: brew install wget ghostscript nmap 4) ------ Installation of Oracle Java 1.8 ------ Java 1.8 is need it to work OpenMeetings 3.3.2. Will install Oracle Java 1.8. Please, visit: http://www.oracle.com/technetwork/java/javase/downloads/jdk8-downloads-2133251.html ...clic on: Agree and proceed ...check: Accept License Agreement ...and download the file called: jdk-8u144-macosx-x64.dmg Once unloaded the file, do clic on it and follow the installation process by default. -

Visual Validation of SSL Certificates in the Mozilla Browser Using Hash Images
CS Senior Honors Thesis: Visual Validation of SSL Certificates in the Mozilla Browser using Hash Images Hongxian Evelyn Tay [email protected] School of Computer Science Carnegie Mellon University Advisor: Professor Adrian Perrig Electrical & Computer Engineering Engineering & Public Policy School of Computer Science Carnegie Mellon University Monday, May 03, 2004 Abstract Many internet transactions nowadays require some form of authentication from the server for security purposes. Most browsers are presented with a certificate coming from the other end of the connection, which is then validated against root certificates installed in the browser, thus establishing the server identity in a secure connection. However, an adversary can install his own root certificate in the browser and fool the client into thinking that he is connected to the correct server. Unless the client checks the certificate public key or fingerprint, he would never know if he is connected to a malicious server. These alphanumeric strings are hard to read and verify against, so most people do not take extra precautions to check. My thesis is to implement an additional process in server authentication on a browser, using human recognizable images. The process, Hash Visualization, produces unique images that are easily distinguishable and validated. Using a hash algorithm, a unique image is generated using the fingerprint of the certificate. Images are easily recognizable and the user can identify the unique image normally seen during a secure AND accurate connection. By making a visual comparison, the origin of the root certificate is known. 1. Introduction: The Problem 1.1 SSL Security The SSL (Secure Sockets Layer) Protocol has improved the state of web security in many Internet transactions, but its complexity and neglect of human factors has exposed several loopholes in security systems that use it. -
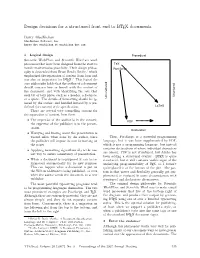
Design Decisions for a Structured Front End to LATEX Documents
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Flash E Software Libero Stefano Sabatini
Flash e software libero Stefano Sabatini GULCh Cagliari, 2009-10-24 GULCh - Gruppo Utenti Linux Cagliari - www.gulch.it Stefano Sabatini, Flash e software libero 1 La tecnologia alla base di Flash ● Un file flash / SWF (Small Web Format / ShockWave Format) è interpretato da una macchina virtuale Flash ● I file SWF possono essere interpretati sia da un interprete standalone sia da un plugin inserito all'interno del browser. ● Il linguaggio della VM è orientato alla renderizzazione di animazioni ● Motore di rendering basato su grafica scalare ● Il linguaggio solitamente utilizzato per la programmazione degli SWF è un file Action Script (2 / 3), gli ambiente di sviluppo visuale generano automaticamente il codice (programmazione “visuale”). ● Esistono vari formati del linguaggio della VM (SWF 1– SWF 10). ● L'esecuzione di uno swiff è soggetto a delle restrizioni di sicurezza ● Con la tecnologia AIR (Adobe Integrate Realtime) è possibile utilizzare la stessa teconologia di sviluppo e renderizzazione per applicazioni desktop native (senza le limitazioni di sicurezza di Flash) ● A partire da Flash 10, supporto a un motore 3D Cagliari, 2009-10-24 GULCh - Gruppo Utenti Linux Cagliari - www.gulch.it Stefano Sabatini, Flash e software libero 2 La tecnologia alla base di Flash ● Supporto a stream multimediali: ● Video: On2 VP6 (Flash 8), Sorenson Spark (Flash 6/7), H.264 (Flash 10) ● Audio: MP3, Nellymoser, Speex (Flash 10), ADPCM ● Tecnologia di comunicazione e streaming multimediale (RTMP, RTMPT, RTMPS, RTMPE) Cagliari, 2009-10-24 GULCh - Gruppo Utenti Linux Cagliari - www.gulch.it Stefano Sabatini, Flash e software libero 3 Ambiti di utilizzo di Flash ● Presentazione di elementi multimediali all'interno di pagine web (youtube / vimeo / facebook) ● Inclusione di animazioni all'interno di pagine web (e.g.