Standoff Markup Peter L
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

THE TEXT ENCODING INITIATIVE Edward
THE TEXT ENCODING INITIATIVE Edward Vanhoutte & Ron Van den Branden Centre for Scholarly Editing and Document Studies Royal Academy of Dutch Language and Literature - Belgium Koningstraat 18 9000 Gent Belgium [email protected] [email protected] KEYWORDS: text-encoding, markup, markup languages, XML, humanities Preprint © Edward Vanhoutte & Ron Van den Branden - The Text Encoding Initiative Bates & Maack (eds.), Encyclopedia of Library and Information Sciences - 1 ABSTRACT The result of community efforts among computing humanists, the Text Encoding Initiative or TEI is the de facto standard for the encoding of texts in the humanities. This article explains the historical context of the TEI, its ground principles, history, and organisation. Preprint © Edward Vanhoutte & Ron Van den Branden - The Text Encoding Initiative Bates & Maack (eds.), Encyclopedia of Library and Information Sciences - 2 INTRODUCTION The Text Encoding Initiative (TEI) is a standard for the representation of textual material in digital form through the means of text encoding. This standard is the collaborative product of a community of scholars, chiefly from the humanities, social sciences, and linguistics who are organized in the TEI Consortium (TEI-C <http://www.tei-c.org>). The TEI Consortium is a non-profit membership organisation and governs a wide variety of activities such as the development, publication, and maintenance of the text encoding standard documented in the TEI Guidelines, the discussion and development of the standard on the TEI mailing list (TEI-L) and in Special Interest Groups (SIG), the gathering of the TEI community on yearly members meetings, and the promotion of the standard in publications, on workshops, training courses, colloquia, and conferences. -
Design Decisions for a Structured Front End to LATEX Documents
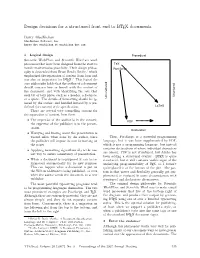
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

Towards a Content-Based Billing Model: the Synergy Between Access Control and Billing
TOWARDS A CONTENT-BASED BILLING MODEL: THE SYNERGY BETWEEN ACCESS CONTROL AND BILLING Peter J. de Villiers and Reinhardt A. Botha Faculty of Computer Studies, Port Elizabeth Technikon, Port Elizabeth [email protected], [email protected] Abstract In the internet environment the importance of content has grown. This has brought about a change in emphasis to provide content-based ser- vices in addition to traditional Internet transactions and services. The introduction of content-based services is the key to increase revenues. To e®ectively increase revenues through content-based services e±cient billing systems need to be implemented. This paper will investigate a presumed synergy between access control and billing. The investigation identi¯es three phases. Subsequently the similarities and di®erences be- tween access control and billing in each of these phases are investigated. This investigation assumes that information delivery takes place in an XML format. Keywords: access control, billing, XML 1. INTRODUCTION The global economy has made a transition from an economy with an industrial focus to being an economy based on knowledge and infor- mation. This new paradigm is enabled by the use of Information and Communication Technologies (ICT). The increasing pace of technological innovations in the ¯eld of ICT has given rise to new ways of communicating, learning and conducting business. The Internet has facilitated the establishment of a "borderless" environment for communications and the electronic delivery of certain services. This is known as electronic business (e-business). Electronic business is the key to doing business in the new global economy that is based on knowledge and information [15]. -

3.4 the Extensible Markup Language (XML)
TEI BY EXAMPLE MODULE 0: INTRODUCTION TO TEXT ENCODING AND THE TEI Edward Vanhoutte Ron Van den Branden Melissa Terras Centre for Scholarly Editing and Document Studies (CTB) , Royal Academy of Dutch Language and Literature, Belgium, Gent, 9 July 2010 Last updated September 2020 Licensed under a Creative Commons Attribution ShareAlike 3.0 License Module 0: Introduction to Text Encoding and the TEI TABLE OF CONTENTS 1. Introduction....................................................................................................................................................................1 2. Text Encoding in the Humanities...............................................................................................................................2 3. Markup Languages in the Humanities.......................................................................................................................3 3.1 Procedural and Descriptive Markup.................................................................................................................... 3 3.2 Early Attempts......................................................................................................................................................... 3 3.3 The Standard Generalized Markup Language (SGML)...................................................................................... 4 3.4 The eXtensible Markup Language (XML)............................................................................................................5 4. XML: Ground Rules........................................................................................................................................................5 -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Never the Same Stream: Netomat, Xlink, and Metaphors of Web Documents Colin Post Patrick Golden Ryan Shaw
Never the Same Stream: netomat, XLink, and Metaphors of Web Documents Colin Post Patrick Golden Ryan Shaw University of North Carolina at University of North Carolina at University of North Carolina at Chapel Hill Chapel Hill Chapel Hill School of Information and School of Information and School of Information and Library Science Library Science Library Science [email protected] [email protected] [email protected] ABSTRACT value for designers and engineers of studying “paths not taken” during the history of the technologies we work on today. Document engineering employs practices of modeling and representation that ultimately rely on metaphors. Choices KEYWORDS among possible metaphors, however, often receive less Hypertext; XLink; browsers; XML; digital art attention than choices driven by practical requirements such as performance or usability. Contemporary debates over how to meet practical requirements always presume some shared 1 Introduction metaphors, making them hard to discern from the surrounding context in which the engineering tasks take place. One way to The metaphor of the printed page has been a prominent address this issue is by taking a historical perspective. In this and indeed from the earliest implementations of hypertext. paper, we attend to metaphorical choices by comparing two structuring principle of Web documentsd hypertext since in the contrast �irst browser, to the historical case studies of “failed” designs for hypertext on the printed page, as whatever “could not conveniently be netomat (1999), a Web browser created preAlthoughsented Nelsonor represented �irst de�ine on paper” [29, page 96], many by the artist Maciej Wisniewski, which responded to search subsequent hypertext systems treated documents as queriesWeb. -

Streaming-Based Processing of Secured XML Documents
Streaming-based Processing of Secured XML Documents Chair for Network- and Data Security Horst Görtz Institute for IT Security Ruhr-University Bochum Juraj Somorovský Matriculation Number: 108 006 245 025 2.10.2009 Supervisors: Prof. Jörg Schwenk Dipl.-Inf. Meiko Jensen Eidesstattliche Erklärung Ich versichere hiermit, dass ich meine Masterarbeit mit dem Thema Streaming-based Processing of Secured XML Documents selbständig verfasst und keine anderen als die angegebenen Quellen und Hilfsmittel benutzt habe. Die Arbeit wurde bisher keiner anderen Prüfungsbehörde vorgelegt und auch nicht veröentlicht. Bochum, den 2. Oktober 2009 Abstract WS-Security is a standard providing message-level security in Web Services. It allows exible application of security mechanisms in SOAP messages. Therewith it ensures their integrity, condentiality and authenticity. However, using sophisticated security algorithms can lead to high memory consumptions and long evaluation times. In the combination with the standard XML DOM processing approach the Web Services servers become a simple target of Denial-of-Service attacks. This thesis presents a solution for these problems an external streaming-based WS-Security Gateway. First the diculties and limitations of the streaming-based approach applied on secured XML documents are discussed. Then the implementation of the WS-Security Gateway is presented. The implementation is capable of processing XML signatures in SOAP messages. The evaluation shows that streaming-based approach enhances the performance and is much more ecient in comparison to standard DOM-based frameworks. It is also proved that the implementation is under certain circumstances resistant against signature wrapping attacks. Contents 1 Introduction1 2 Related work3 2.1 XML Signature . -

Here.Is.Only.Xul
Who am I? Alex Olszewski Elucidar Software Co-founder Lead Developer What this presentation is about? I was personally assigned to see how XUL and the Mozilla way measured up to RIA application development standards. This presentation will share my journey and ideas and hopefully open your minds to using these concepts for application development. RIA and what it means Different to many “Web Applications” that have features and functions of “Desktop” applications Easy install (generally requires only application install) or one-time extra(plug in) Updates automatically through network connections Keeps UI state on desktop and application state on server Runs in a browser or known “Sandbox” environment but has ability to access native OS calls to mimic desktop applications Designers can use asynchronous communication to make applications more responsive RIA and what it means(continued) Success of RIA application will ultimately be measured by how will it can match user’s needs, their way of thinking, and their behaviour. To review RIA applications take advantage of the “best” of both web and desktop apps. Sources: http://www.keynote.com/docs/whitepapers/RichInternet_5.pdf http://en.wikipedia.org/wiki/Rich_Internet_application My First Steps • Find working examples Known Mozilla Applications Firefox Thunderbird Standalone Applications Songbird Joost Komodo FindthatFont Prism (formerly webrunner) http://labs.mozilla.com/featured- projects/#prism XulMine-demo app http://benjamin.smedbergs.us/XULRunner/ Mozilla -

Scalable Vector Graphics (SVG) 1.2
Scalable Vector Graphics (SVG) 1.2 Scalable Vector Graphics (SVG) 1.2 W3C Working Draft 27 October 2004 This version: http://www.w3.org/TR/2004/WD-SVG12-20041027/ Previous version: http://www.w3.org/TR/2004/WD-SVG12-20040510/ Latest version of SVG 1.2: http://www.w3.org/TR/SVG12/ Latest SVG Recommendation: http://www.w3.org/TR/SVG/ Editor: Dean Jackson, W3C, <[email protected]> Authors: See Author List Copyright ©2004 W3C® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. Abstract SVG is a modularized XML language for describing two-dimensional graphics with animation and interactivity, and a set of APIs upon which to build graphics- based applications. This document specifies version 1.2 of Scalable Vector Graphics (SVG). Status of this Document http://www.w3.org/TR/SVG12/ (1 of 10)30-Oct-2004 04:30:53 Scalable Vector Graphics (SVG) 1.2 This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This is a W3C Last Call Working Draft of the Scalable Vector Graphics (SVG) 1.2 specification. The SVG Working Group plans to submit this specification for consideration as a W3C Candidate Recommendation after examining feedback to this draft. Comments for this specification should have a subject starting with the prefix 'SVG 1.2 Comment:'. Please send them to [email protected], the public email list for issues related to vector graphics on the Web.