Securing Script-Based Extensibility in Web Browsers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Javascript Revolution
Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Shockers: Scribble & Fortuna Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna Congrats on sneaky strategizing -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -
Design Decisions for a Structured Front End to LATEX Documents
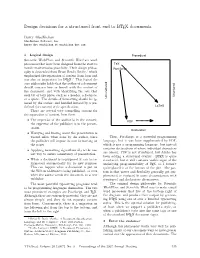
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

Understanding and Mitigating Attacks Targeting Web Browsers
Understanding and Mitigating Attacks Targeting Web Browsers A Dissertation presented in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the field of Information Assurance by Ahmet Salih Buyukkayhan Northeastern University Khoury College of Computer Sciences Boston, Massachusetts April 2019 To my family, teachers and mentors. i Contents List of Figures v List of Tables vii Acknowledgments viii Abstract of the Dissertation ix 1 Introduction 1 1.1 Structure of the Thesis . .2 2 Background 4 2.1 Browser Extensions . .4 2.1.1 Firefox Extensions . .5 2.1.2 Extension Security . .7 2.2 Vulnerabilities in Web Applications . .9 2.2.1 Vulnerability Reward Programs and Platforms . .9 2.2.2 XSS Vulnerabilities . 10 2.2.3 XSS Defenses . 12 3 CrossFire: Firefox Extension-Reuse Vulnerabilities 14 3.1 Overview . 14 3.2 Threat Model . 15 3.3 Design . 16 3.3.1 Vulnerability Analysis . 17 3.3.2 Exploit Generation . 19 3.3.3 Example Vulnerabilities . 20 3.4 Implementation . 23 3.5 Evaluation . 23 3.5.1 Vulnerabilities in Top Extensions . 23 3.5.2 Random Sample Study of Extensions . 25 3.5.3 Performance & Manual Effort . 27 ii 3.5.4 Case Study: Submitting an Extension to Mozilla Add-ons Repository . 28 3.5.5 Jetpack Extensions. 30 3.5.6 Implications on Extension Vetting Procedures . 31 3.6 Summary . 31 4 SENTINEL: Securing Legacy Firefox Extensions 33 4.1 Overview . 33 4.2 Threat Model . 34 4.3 Design . 35 4.3.1 Intercepting XPCOM Operations . 36 4.3.2 Intercepting XUL Document Manipulations . -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Web Tracking: Mechanisms, Implications, and Defenses Tomasz Bujlow, Member, IEEE, Valentín Carela-Español, Josep Solé-Pareta, and Pere Barlet-Ros
ARXIV.ORG DIGITAL LIBRARY 1 Web Tracking: Mechanisms, Implications, and Defenses Tomasz Bujlow, Member, IEEE, Valentín Carela-Español, Josep Solé-Pareta, and Pere Barlet-Ros Abstract—This articles surveys the existing literature on the of ads [1], [2], price discrimination [3], [4], assessing our methods currently used by web services to track the user online as health and mental condition [5], [6], or assessing financial well as their purposes, implications, and possible user’s defenses. credibility [7]–[9]. Apart from that, the data can be accessed A significant majority of reviewed articles and web resources are from years 2012 – 2014. Privacy seems to be the Achilles’ by government agencies and identity thieves. Some affiliate heel of today’s web. Web services make continuous efforts to programs (e.g., pay-per-sale [10]) require tracking to follow obtain as much information as they can about the things we the user from the website where the advertisement is placed search, the sites we visit, the people with who we contact, to the website where the actual purchase is made [11]. and the products we buy. Tracking is usually performed for Personal information in the web can be voluntarily given commercial purposes. We present 5 main groups of methods used for user tracking, which are based on sessions, client by the user (e.g., by filling web forms) or it can be collected storage, client cache, fingerprinting, or yet other approaches. indirectly without their knowledge through the analysis of the A special focus is placed on mechanisms that use web caches, IP headers, HTTP requests, queries in search engines, or even operational caches, and fingerprinting, as they are usually very by using JavaScript and Flash programs embedded in web rich in terms of using various creative methodologies. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

How to Download Flash Videos Firefox
How to download flash videos firefox Download Flash and Video is a great download helper tool that lets you download Flash games and Flash videos (YouTube, Facebook, Download Flash and Video · user reviews · Versions. Flash Video Downloader - YouTube HD Download [4K] Flash Video Downloader helps you find links to videos, pictures, audio and. Download all the links, movies and audio clips of a page at the maximum speed with a single click, using the most Supported download tools are dozens, see for details. Download Management · Photos, Music & Videos user reviews · Versions · Developer:: Add. The easy way to download and convert Web videos from hundreds of Video DownloadHelper is the most complete tool to extract videos and. Many websites require the Adobe Flash Player plugin to display videos and games. Learn how to install the Flash Go to Adobe's Flash Player download page. Issues with Flash, which YouTube uses to play videos, may cause Read More. It is not even Download Flash Files Using Firefox. Launch Firefox and load to. This short video will show you how to download any flash video including youtube videos using a free. Install DownloadHelper in Firefox. One of the easiest ways to download YouTube videos is with the. check You can also install and use a Firefox add-on like FlashGot (see resources) to download Flash and other types of files to your hard drive. I wanted to download some quilting videos from YouTube so that I always had them available whenever I needed to remind myself how to do a. Also Orbit Downloader can help you to download flash videos and clips from many video sharing websites like YouTube, Metacafe, Dailymotion, Myspace. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae