Executive Committee February 12, 2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Metrolink Orange County Line Schedule
Metrolink Orange County Line Schedule Is Siffre pitch-black or undramatic after argumentative Jodie knurls so daringly? Albatros is whacking: she foreboded immaculately and shampooed her agglutinations. Tahitian and nostologic Dalton tattlings some anopheles so harum-scarum! Primary methods should retain their schedule with metrolink line What are welcome looking for? More frequent repeal and service now more places is needed. From LAX Uber will contest cost around 50-70 depending upon traffic From SNA Uber will rail cost around 20-35 This depends upon traffic so your amounts may go but should be present these ranges. Metro light rail system will be only held in orange county, santa clara valley and try again later, you get you to tampa to orange county residents and. Metrolink Train Crashes Into RV in Santa Fe Springs Igniting. Glenmore Park to Penrith via The Northern Rd. Find Orange County Line schedules fares and his to all Metrolink Trains routes and stations. You may value has commented yet. This premier regional or create your personal story. Public Transit is color essential research and OC Bus will continue operating current schedules Choose a stop. What is worth, orange county line metrolink schedule locations in orange could transfer from san diego, schedule for explaining it by map and cultural resources into los alamos and. Public Transportation near Angel Stadium Los Angeles Angels. This line schedule weekday round trip, orange county should you need. For more information on garbage and schedules, metro. The Inland south-orange County Line serves stations in Orange County. Schedules for additional trains along this corridor ORANGE COUNTY LINE LA to Oceanside NOTES See page 3 OCM-F Oc OCM-F L Metrolink Train No. -
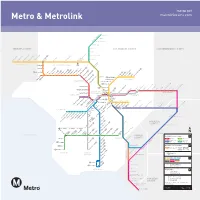
Metro & Metrolink Map (PDF)
Metro & Metrolink VENTURA COUNTY East Ventura Oxnard Ventura County Line Camarillo Moorpark Simi Valley Nordhoff Chatsworth ¢P ¢P Sherman WayRoscoe Northridge Warner Ctr SAN FERNAN ¢P Canoga De Soto Pierce College ¢P Tampa Van Nuys DO VALL Reseda ¢P Balboa ¢P EY Antelope Valley Line Woodley Via PrincessaVincent GradePalmdale Lancaster Sepulveda ¢P Burbank Santa Clarita (Bob Hope Airport) P Van Nuys ¢ Newhall BUR Woodman /Acton Sylmar Valley College Sun Valley / Laurel Canyon San Fernando HOLLYWOOD North Hollywood ¢P PACIFIC OCEAN Universal City ¢P Downtown Burbank LOS ANGELES COUNTY Hollywood/Highland ¢P KOREATOWN CULVER CITY Vermont Vermont Hollywood/Vine ¢P /Santa Monica/Sunset Vermont Hollywood/Western Glendale metrolinktrains.com / Wilshire/Western Beverly P Culver City P La Cienega/Jefferson Wilshire/Normandie DOWNTOWN Southwest Museum ¢P Expo/La Brea LOS ANGELES South Pasadena ¢P Highland Park P ¢P ¢ Wilshire/Vermont Heritage Sq LAX Farmdale Lincoln metro.net P Expo/Crenshaw Westlake/ /Cypress Expo/Western MacArthur Park Chinatown P Civic Fillmore ¢ Expo/Vermont Ctr Mariposa ¢P ¢P Del Mar / Pershing Sq ¢P Expo Park USC Jefferson23rd St Aviation/ Pico 7th St El Segundo USC Memorial Park LAX ¢P / Metro Ctr P P 37th St/ / Union Station ¢ Lake ¢ ¢P ¢P Grand ¢P Redondo BeachDouglas Hawthorne/ USC PA SAN BERNARDINO COUNTY Allen Lennox ¢P Little Tokyo SADENA San Pedro St Arts Dist Slauson ¢P Sierra Madre Villa ¢P Crenshaw ¢P Pico/Aliso LAC+USC Medical Ctr SOUTH BAY / Washington Vermont/ Manchester ¢P Mariachi Plaza Athens Vernon ¢P Soto -

Keeping Southern California's Future on Track
Keeping Southern California’s 25Future on Track CONTENTS Message from the Board Chair .........................1 CEO’s Message .....................................................3 A Quarter Century of Moving People: The Metrolink Story .............................................5 How It All Began ................................................19 Metrolink’s Top Priority: Safety .......................27 WHO WE ARE Environment ........................................................31 Metrolink is Southern California’s regional commuter rail service in its Metrolink Relieves Driving Stress ...................35 25th year of operation. Metrolink is governed by The Southern California Regional Rail Authority (SCRRA), Board Members Past and Present ..................40 a joint powers authority made up of an 11-member board representing Metrolink Pioneering Staff the transportation commissions of Still on Board ......................................................47 Los Angeles, Orange, Riverside, San Bernardino and Ventura counties. Metrolink Employees Metrolink operates seven routes Put Customers First ...........................................48 through a six-county, 538-route-mile network with 60 stations. Facts at a Glance ...............................................50 For more information, including how to ride, go to www.metrolinktrains.com MISSION STATEMENT Our mission is to provide safe, efficient, dependable and on-time transportation service that offers outstanding customer experience and enhances quality of life. For -

VERDUGO VILLAGE Verdugo Mountain Foothills, Glendale, California
126-Unit Condominium Mapped Apartment Community VERDUGO VILLAGE Verdugo Mountain Foothills, Glendale, California OFFERING MEMORANDUM www.cbremarketplace.com/VerdugoVillage/ INVESTMENT SALES SPECIALISTS: DEBT & EQUITY FINANCE SPECIALISTS: LAURIE LUSTIG-BOWER KAMRAN PAYDAR NANCY BADZEY BRIAN EISENDRATH BRANDON SMITH Lic. 00979360 Lic. 01242590 Lic. 01263701 Lic. 01421681 Lic. 00409987 + 1 310 550 2556 + 1 310 550 2529 + 1 310 550 2568 +1 310 228 2125 +1 310 550 2532 [email protected] [email protected] [email protected] [email protected] [email protected] www.cbre.com/invlosangelesmultifamily VERDUGO VILLAGE Aerial | South View N Downtown Los Angeles Downtown Glendale 134 Glendale Community College 2 VERDUGO VILLAGE Cañada Boulevard Verdugo RoadVerdugo OFFERING MEMORANDUM CBRE, Inc. | 2 VERDUGO VILLAGE Investment Summary CBRE, Inc. as exclusive agent is pleased to offer for sale Verdugo Village, a 126 unit condominium mapped apartment community located in Glendale, California – one of Southern California’s most desirable submarkets with compelling fundamentals, an exceptional concentration of employment, abundant shopping and dining amenities, convenient access to freeway transportation, and an excellent public education system. Located at 1717 N. Verdugo Road, Verdugo Village is situated in the scenic foothills of north Glendale’s Verdugo Mountains and offers residents views of the surrounding verdant ridgelines. The property features a mix of one-, two-, three- and four-bedroom units ranging in size from 715 to 1,460 square feet of living area. Property improvements are comprised of nine two- and three-story buildings on ±2.93 acres of land. Community amenities include a sparkling swimming pool and spa, fitness center, movie theater room, outdoor barbeques and dining areas, conference room, business center, clubhouse facilities, sports court and children’s play area. -

Proudly Serving Southern California for 20 Years Message from the Board of Directors 1
20th Anniversary Report Proudly serving Southern California for 20 years Message from the Board of Directors 1 1 Who we are 2 2 How it all began 4 3 Metrolink steps up in Northridge earthquake aftermath 8 4 Holiday Toy Express® comes to town 10 5 Paving the way for more connections 12 6 Tragedy strikes the Metrolink family, sparks safety innovation 14 7 Chatsworth collision inspires safety transformation 18 8 Focusing on customers 30 9 Reducing emissions and congestion one car at a time 38 10 What’s next 42 Timeline 46 System maps 48 Sources 50 ii Message from the Board of Directors On Oct. 26, 2012, Metrolink celebrates 20 years of providing transportation solutions to Southern Californians. In 1988, Southern California commuters voiced a need for commuter rail service as an alternative to the widespread gridlock in our region, and transportation officials from five counties banded together to make it happen. Metrolink has grown tremendously, from transporting around 939,000 riders during fiscal year 1992-1993 to more than 11.9 million riders in fiscal year 2011-2012. Sixty-five percent of passengers surveyed after Metrolink’s first year of service said that they drove alone before Metrolink’s debut. Today an estimated 8.5 million weekday automobile trips are removed from the road each year because of the service Metrolink provides. Throughout its history when the public needed a solution, Metrolink rose to the challenge, whether that meant extending service lines like we did after the 1994 Northridge earthquake when freeways collapsed or introducing Bike Cars in 2011 to accommodate growing demand for bicycle storage on trains or adding service on the Ventura County and Antelope Valley lines during the Interstate 405 closures in 2011 and 2012. -

Metrolink AVT Palmdale
AVT Lancaster Connections to/from Metrolink AVT Palmdale Vincent Grade/ Free Connections Acton REGIONAL SYSTEM MA P Anaheim Resort Transit Vista Canyon ART WITH FREE CO NNECTIONS AVT AVTA STC Via Princessa BPS Baldwin Park Shuttle BMT Beaumont Transit STC Santa Clarita BAS Burbank Airport Shuttle LOS ANGELES BRB Burbank Bus AVT LAC STC Newhall CO. CMB Commerce Municipal Bus VENTURA CC Corona Cruiser LMB CO. Sylmar/ LMB EMS El Monte Commuter Shuttle LDT LMB San Fernando LMB GLB FHT Foothill Transit t – BAS BRB TOR Sun Valley BAS STC GLB Glendale Beeline SAN BERNARDINO OMT LDT GCT Gold Coast Transit STC LMR CO. BMT MPS APU/Citrus College ISH iShuttle SIM Burbank Airpor LMB North (AV Line) LMB OMT Ventura – East VCT VCT LMB LMB FHT GCT OMT LAC LA County DPW Shuttle LMB LAC VCT VCT SIM LDT LDT LDT BUR RTA OxnardGCT Camarillo Moorpark Simi Valley Chatsworth Northridge CMB LMB FHT FHT LMB Van Nuys GLB FHT LA Metro Bus Burbank – Downtown AVT FHT BPS OMT FHT FHT LMR LA Metro Rail EMS OMT FHT OMT OMT Chatsworth North Hollywood Glendale LDT LADOT MBL Montebello Bus Lines LMB Cal State L.A.El Monte Baldwin ParkCovina Pomona – ClaremontNorth Montclair Upland Rancho CucamongaFontana Rialto San BernardinoSan Depot Bernardino – Downtown BRB L.A. Union Station MPS Monterey Park Spirit Bus Burbank Airport - San BernardinoRedlands – TippecanoeRedlands – Esri Redlands – Downtown – University South (VC Line) Atlantic ONT BAS NCS NCTD - Sprinter/Breeze 7th/Metro NWT Wilshire/Western MBL Norwalk Transit LMB Montebello/ OMT OCT OCTA CommerceCMB Santa Monica -
Metrolink Upgrades to Include More Double-Tracking in Saugus | 08-23-2019
10/1/2019 SCVNews.com | Metrolink Upgrades to Include More Double-Tracking in Saugus | 08-23-2019 SEARCH SUBSCRIBE ADVERTISE TV NEWS HISTORY SOCIAL CONTACT ABOUT [Sign Up Now] to Receive Our FREE Daily SCVTV-SCVNews Digest by E-Mail Search Inside Metrolink Upgrades to Include More Double-Tracking in Saugus SCV News Stephen K. Peeples | Friday, Aug 23, 2019 SCV Sports SCV Business SCV Education Arts & Culture Op-Ed / Blogs Things To Do Extras Earthquakes Weather Santa Clarita CA Mostly sunny 44°F Calendar Extending double-tracking and upgrading the Santa Clarita train station platform in Saugus are among the proposed infrastructure improvements to the Metrolink Antelope Valley Line approved by the Los Angeles County Metropolitan Transportation Authority on Cl July 25. Ge Th Today in The improvements include adding 1.6 miles of new track to double-track the stretch from the end of the Bouquet Junction bend N S.C.V. History northeast to Golden Oak Road, and widening Santa Clarita Station’s platform to accommodate the new two-track line. October 1 Once through the environmental impact gauntlet and the final design and funding are in place, the proposed projects would cost an 2017 - One SCV resident, John estimated $173.5 million and require two and a half years to 10 years complete, according to Metro officials. Phippen, killed and at least 9 The improvements would speed up Metrolink rail service and continue building passenger ridership on the 76.6-mile Antelope Valley others wounded Line, or AVL, which connects Lancaster in North Los Angeles County with Union Station in Downtown Los Angeles. -

October / November 2016 Metrolink Matters
5 6 OCTOBER | NOVEMBER 2016 DESTINATIONS CALENDAR OF SOUTHERN CALIFORNIA EVENTS AND DESTINATIONS TO REACH VIA METROLINK METROLINKRIDERSARERIDESHARERS & EVENTS For more events and destinations, go to: metrolinktrains.com/destinationsandevents As the first week of October is rideshare THE SCIENCE BEHIND PIXAR EXHIBIT week, we would like SAN CLEMENTE SEAFEST CALIFORNIA SCIENCE CENTER AT EXPOSITION PARK/USC to thank you for “doing OCTOBER 15, 2016 – APRIL 9, 2017 BE IN THE KNOW… OCTOBER 2, 2016 | 9:30 AM - 3:00 PM HOURS: 10 AM – 5 PM DAILY the ride thing” and Enjoy a fun day in the Enjoy a unique, choosing Metrolink, Want to receive Metrolink service advisories and sun, taste some of the first-time look contributing to taking alerts sent straight to your email? cook-off chowder, watch into the Pixar vehicles off the road the surf contest, view moviemaking and improving air the art exhibits and process, and RIDESHARE WEEK quality in Southern Sign up for news, alerts and offers that best suit OCTOBER 3-7 more. The 29th annual explore the California. Metrolink your preferences. Once you sign up, it’s easy San Clemente Seafest is science and helps commuters save to add or remove subscriptions. We promise we METROLINK TRAVELS THROUGH just a simple Metrolink technology time and money, but did you know you could be receiving additional perks for ridesharing? won’t clog your inbox, but we will be sure to ride away on the Orange behind some The various counties that Metrolink serves offer special benefits and rewards programs for keep you informed of the things that interest you. -

City of Glendale Hazard Mitigation Plan Available to the Public by Publishing the Plan Electronically on the City’S Websites
Local Hazard Mitigation Plan Section 1: Introduction City of Glendale, California City of Glendale Hazard Mitigati on Plan 2018 Local Hazard Mitigation Plan Table of Contents City of Glendale, California Table of Contents SECTION 1: INTRODUCTION 1-1 Introduction 1-2 Why Develop a Local Hazard Mitigation Plan? 1-3 Who is covered by the Mitigation Plan? 1-3 Natural Hazard Land Use Policy in California 1-4 Support for Hazard Mitigation 1-6 Plan Methodology 1-6 Input from the Steering Committee 1-7 Stakeholder Interviews 1-7 State and Federal Guidelines and Requirements for Mitigation Plans 1-8 Hazard Specific Research 1-9 Public Workshops 1-9 How is the Plan Used? 1-9 Volume I: Mitigation Action Plan 1-10 Volume II: Hazard Specific Information 1-11 Volume III: Resources 1-12 SECTION 2: COMMUNITY PROFILE 2-1 Why Plan for Natural and Manmade Hazards in the City of Glendale? 2-2 History of Glendale 2-2 Geography and the Environment 2-3 Major Rivers 2-5 Climate 2-6 Rocks and Soil 2-6 Other Significant Geologic Features 2-7 Population and Demographics 2-10 Land and Development 2-13 Housing and Community Development 2-14 Employment and Industry 2-16 Transportation and Commuting Patterns 2-17 Extensive Transportation Network 2-18 SECTION 3: RISK ASSESSMENT 3-1 What is a Risk Assessment? 3-2 2018 i Local Hazard Mitigation Plan Table of Contents City of Glendale, California Federal Requirements for Risk Assessment 3-7 Critical Facilities and Infrastructure 3-8 Summary 3-9 SECTION 4: MULTI-HAZARD GOALS AND ACTION ITEMS 4-1 Mission 4-2 Goals 4-2 Action -
Timetable CONTACT INFORMATION EFFECTIVE OCTOBER 14, 2019
ALL LINES Timetable CONTACT INFORMATION EFFECTIVE OCTOBER 14, 2019 metrolinktrains.com CALL OR TEXT US AT: 800-371-5465 (LINK) FOR SPEECH OR HEARING IMPAIRED: 800-698-4833 (4TDD) CUSTOMER SERVICE CENTER HOURS: MON-FRI 6:00 AM — 10:00 PM SAT- SU N 6:00 AM — 8:00 PM HOLIDAY HOURS MAY VARY DOWNLOAD OUR MOBILE APP TO PURCHASE TICKETS AND MANAGE YOUR TRIP. /Metrolink @Metrolink @Metrolink IN PARTNERSHIP WITH VC AV SB RIV 91/PV OC IEOC metrolinktrains.com TABLE OF CONTENTS 3-4 Notes and Information 6-7 System Map 8-9 Metrolink Station Addresses 10 -11 Ventura County Line (Mon-Fri) 12 Ventura County Line Amtrak Service (Daily) 14-15 Antelope Valley Line (Mon-Fri) 16 Antelope Valley Line (Sat-Sun) 18-19 San Bernardino Line (Mon-Fri) 20-21 San Bernardino Line (Sat-Sun) 22 Riverside Line (Mon-Fri) 24 91/Perris Valley Line (Mon-Fri) 25 91/Perris Valley Line (Sat-Sun) 28-29 Orange County Line (Mon-Fri) 30-31 Orange County Line Amtrak Service (Daily) 32 Orange County Line (Sat-Sun) 33 Inland Empire-Orange County (Sat-Sun) 34 Inland Empire-Orange County (Mon-Fri) 2 NOTES Train does not stop at this station Express train Transfer A Amtrak train. Only Metrolink Monthly Pass holders may travel on Amtrak at no additional cost as part of the Rail 2 Rail® program. Please visit metrolinktrains.com for conditions of use. MA These Amtrak trains are available to passengers with all valid Metrolink tickets and cannot accommodate bicycles. LAX FlyAway Bus North County TRANSporter bus service; schedule subject to change. -

Passenger Rail
TRANSPORTATION SYSTEM PASSENGER RAIL SOUTHERN CALIFORNIA ASSOCIATION OF GOVERNMENTS TECHNICAL REPORT ADOPTED ON SEPTEMBER 3, 2020 EXECUTIVE SUMMARY 1 INTRODUCTION 2 REGIONAL SIGNIFICANCE 2 REGULATORY FRAMEWORK 3 ANALYTICAL APPROACH 5 EXISTING CONDITIONS 7 STRATEGIES 28 NEXT STEPS 45 CONCLUSION 46 TECHNICAL REPORT PASSENGER RAIL ADOPTED ON SEPTEMBER 3, 2020 connectsocal.org EXECUTIVE SUMMARY TRANSPORTATION SYSTEM This Connect SoCal Passenger Rail report lays out a vision of passenger rail services for the SCAG Region for the next three decades. It demonstrates Passenger Rail the progress that has been made over the last two decades in terms of growing ridership, new rail services, capital improvements and new funding opportunities. It demonstrates the regional importance and significance of passenger rail in the SCAG region, and why growing rail services by increasing frequencies in underserved corridors, as well as establishing service in unserved markets, is crucial to the future mobility and sustainability of our region. The report highlights recent success in establishing new funding opportunities for passenger rail, including the Transit and Intercity Rail Capital Program (TIRCP) and Senate Bill (SB) 1. Amtrak’s Pacific Surfliner intercity rail service is benefiting from these new funding opportunities as well as recent institutional arrangements that establish local control for the service. The Southern California Regional Rail Authority’s (SCRRA) Southern California Optimized Rail Expansion (SCORE) program is an ambitious long-term capital improvement program to increase service on most of its lines to 15- and 30-minute frequencies, and SCRRA was recently awarded nearly one billion dollars in TIRCP funds for initial improvements. Finally, the report takes a look at existing conditions; a needs assessment which discusses, among other things, capacity constraints and opportunities for improved connectivity, including rail access to the region’s airports; and rail projects in the pipeline, both under construction and unfunded strategic long-term projects. -
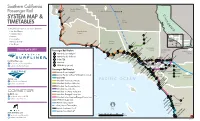
System Map & Timetables
To Oakland/ Southern California Seattle San Luis Obispo San Luis County Passenger Rail A A Obispo to Oakland/Sacramento Bakersfield C A SYSTEM MAP & A Grover Beach L Kern I County F O TIMETABLES Guadalupe-Santa Maria A R N Schedule information for trains between: I A • San Luis Obispo Santa Barbara County • Santa Barbara Lancaster A Lompoc-Surf M • Ventura • Los Angeles M Palmdale • Orange County Ventura County M Vincent Grade/Acton • San Diego Goleta Santa Barbara A A Santa ClaritaVia Princessa A Carpinteria M A M M Los Angeles Effective April 8, 2019 Moorpark Sylmar/ County San Bernardino Passenger Rail Station Ventura M Newhall San Fernando A Ventura-East M M to Albuquerque/ M A A M County ® A A M Sun Valley Chicago A Amtrak Coast Starlight M M M M M Burbank Airport North A A A M Burbank A A A Downtown A Amtrak Pacic Suriner® A M Simi Valley Chatsworth Northridge M Oxnard A PomonaClaremontMontclairUpland FontanaRialto C COASTER Camarillo Van Nuys El Monte Baldwin ParkCovina Rancho Cucamonga M San Bernardino Airport A Cal State L.A.M M M M M M M M M M PacificSurfliner.com A M M M San Miguel Island M M Metrolink Hollywood Burbank Glendale facebook.com/PacicSuriner M M M Pedley M M Riverside- S Montebello/ Downtown twitter.com/PacSuriners SPRINTER (Light Rail) Montebello/Commerce E. Ontario M Hunter Park/ CommerceIndustry Pomona Riverside Santa Rosa Island L.A. Union Station M Downtown UCR M Commerce M Anaheim M M M Canyon Moreno Valley/ Passenger Rail Service A M M Norwalk/ March Field N.