Key Establishment in TLS Chris Hawk, [email protected]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -
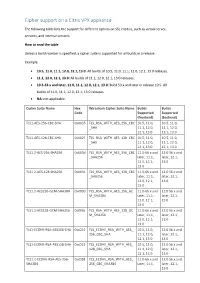
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Analysis of DTLS Implementations Using Protocol State Fuzzing
Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Brostean and Bengt Jonsson, Uppsala University; Robert Merget, Ruhr-University Bochum; Joeri de Ruiter, SIDN Labs; Konstantinos Sagonas, Uppsala University; Juraj Somorovsky, Paderborn University https://www.usenix.org/conference/usenixsecurity20/presentation/fiterau-brostean This paper is included in the Proceedings of the 29th USENIX Security Symposium. August 12–14, 2020 978-1-939133-17-5 Open access to the Proceedings of the 29th USENIX Security Symposium is sponsored by USENIX. Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Bro¸stean˘ Bengt Jonsson Robert Merget Joeri de Ruiter Uppsala University Uppsala University Ruhr University Bochum SIDN Labs Konstantinos Sagonas Juraj Somorovsky Uppsala University Paderborn University Abstract reach 11.6 billion by 2021 [26]. This will constitute half of all devices connected to the Internet, with the percentage set to Recent years have witnessed an increasing number of proto- grow in subsequent years. Such trends also increase the need cols relying on UDP. Compared to TCP, UDP offers perfor- to ensure that software designed for these devices is properly mance advantages such as simplicity and lower latency. This scrutinized, particularly with regards to its security. has motivated its adoption in Voice over IP, tunneling techno- DTLS is also used as one of the two security protocols in logies, IoT, and novel Web protocols. To protect sensitive data WebRTC, a framework enabling real-time communication. exchange in these scenarios, the DTLS protocol has been de- WebRTC can be used, for example, to implement video con- veloped as a cryptographic variation of TLS. -

Prying Open Pandora's Box: KCI Attacks Against
Prying open Pandora’s box: KCI attacks against TLS Clemens Hlauschek, Markus Gruber, Florian Fankhauser, Christian Schanes RISE – Research Industrial Systems Engineering GmbH {clemens.hlauschek, markus.gruber, florian.fankhauser, christian.schanes}@rise-world.com Abstract and implementations of the protocol: their utility is ex- tremely limited, their raison d’ˆetre is practically nil, and Protection of Internet communication is becoming more the existence of these insecure key agreement options common in many products, as the demand for privacy only adds to the arsenal of attack vectors against cryp- in an age of state-level adversaries and crime syndi- tographically secured communication on the Internet. cates is steadily increasing. The industry standard for doing this is TLS. The TLS protocol supports a multi- 1 Introduction tude of key agreement and authentication options which provide various different security guarantees. Recent at- The TLS protocol [1, 2, 3] is probably the most tacks showed that this plethora of cryptographic options widely used cryptographic protocol on the Internet. in TLS (including long forgotten government backdoors, It is designed to secure the communication between which have been cunningly inserted via export restric- client/server applications against eavesdropping, tamper- tion laws) is a Pandora’s box, waiting to be pried open by ing, and message forgery, and it also provides additional, heinous computer whizzes. Novel attacks lay hidden in optional security properties such as client authentica- plainsight. Parts of TLS areso oldthat theirfoul smell of tion. TLS is an historically grown giant: its predecessor, rot cannot be easily distinguished from the flowery smell SSL [4,5], was developed more than 20 years ago. -

Matrixssl Elliptic Curve Cipher Suites
MatrixSSL Elliptic Curve Cipher Suites Electronic versions are uncontrolled unless directly accessed from the QA Document Control system. Printed version are uncontrolled except when stamped with ‘VALID COPY’ in red. External release of this document may require a NDA. © INSIDE Secure - 2016 - All rights reserved TABLE OF CONTENTS 1 ELLIPTIC CURVE CRYPTOGRAPHY ....................................................................... 3 2 ECC CIPHER SUITES ......................................................................................... 4 2.1 Variations .......................................................................................................... 4 2.1.1 ECDHE_ECDSA ............................................................................................... 4 2.1.2 ECDHE_RSA ................................................................................................... 4 2.1.3 ECDH_ECDSA ................................................................................................. 4 2.1.4 ECDH_RSA ...................................................................................................... 4 2.2 Support in MatrixSSL ........................................................................................ 4 3 WHEN ECC CIPHER SUITES ARE A GOOD ALTERNATIVE ...................................... 5 4 API .................................................................................................................. 6 2 © INSIDE Secure – 2016 - All rights reserved 1 ELLIPTIC CURVE CRYPTOGRAPHY This document -

TLS Cipher Suites Recommendations: a Combinatorial Coverage Measurement Approach
TLS Cipher Suites Recommendations: A Combinatorial Coverage Measurement Approach Dimitris E. Simos∗, Kristoffer Kleine∗, Artemios G. Voyiatzis∗, Rick Kuhnx, Raghu Kackerx ∗ SBA Research, Vienna, Austria Email: fdsimos,kkleine,[email protected] x NIST, Information Technology Laboratory, Gaithersburg, MD, USA Email: fd.kuhn.nist.gov,[email protected] Abstract—We present a coverage measurement for TLS ci- channel and, at the same time, also conform to a desired pher suites recommendations provided by various regulatory level of security. It not enough for a TLS implementation and intelligence organizations such as the IETF, ENISA, the to support a set cryptographic algorithms for various tasks German BSI, Mozilla and the USA NSA. These cipher suites are measured and analyzed using a combinatorial approach, (e.g., encryption or authentication) but also to ensure that only which was made feasible via developing the necessary input “secure” combinations of them are accepted and used. models. Besides, shedding light on the coverage achieved by In this paper, we perform a study of the combinatorial the proposed recommendations we discuss implications towards coverage of the TLS cipher suites. The aim of the study is aspects of test quality. One of them relates to the testing of a TLS implementation, where a system designer or tester should expand to provide insights on the coverage achieved by the proposed the TLS cipher suite registry and integrate the information back recommendations and guide, if possible, the selection of ap- to the TLS implementation itself such that the (overall) testing propriate test suites that minimize the number of combinations effort is reduced. -

An Internet-Wide Analysis of Diffie-Hellman Key Exchange and X
Western University Scholarship@Western Electronic Thesis and Dissertation Repository 8-23-2017 1:30 PM An Internet-Wide Analysis of Diffie-Hellmane K y Exchange and X.509 Certificates in TLS Kristen Dorey The University of Western Ontario Supervisor Dr. Aleksander Essex The University of Western Ontario Graduate Program in Electrical and Computer Engineering A thesis submitted in partial fulfillment of the equirr ements for the degree in Master of Engineering Science © Kristen Dorey 2017 Follow this and additional works at: https://ir.lib.uwo.ca/etd Recommended Citation Dorey, Kristen, "An Internet-Wide Analysis of Diffie-Hellmane K y Exchange and X.509 Certificates in TLS" (2017). Electronic Thesis and Dissertation Repository. 4792. https://ir.lib.uwo.ca/etd/4792 This Dissertation/Thesis is brought to you for free and open access by Scholarship@Western. It has been accepted for inclusion in Electronic Thesis and Dissertation Repository by an authorized administrator of Scholarship@Western. For more information, please contact [email protected]. Abstract Transport Layer Security (TLS) is a mature cryptographic protocol, but has flexibility dur- ing implementation which can introduce exploitable flaws. New vulnerabilities are routinely discovered that affect the security of TLS implementations. We discovered that discrete logarithm implementations have poor parameter validation, and we mathematically constructed a deniable backdoor to exploit this flaw in the finite field Diffie-Hellman key exchange. We described attack vectors an attacker could use to position this backdoor, and outlined a man-in-the-middle attack that exploits the backdoor to force Diffie-Hellman use during the TLS connection. We conducted an Internet-wide survey of ephemeral finite field Diffie-Hellman (DHE) across TLS and STARTTLS, finding hundreds of potentially backdoored DHE parameters and partially recovering the private DHE key in some cases. -

IT Security Guidelines for Transport Layer Security (TLS)
IT Security Guidelines for Transport Layer Security (TLS) National Cyber Security Centre The National Cyber Security Centre (NCSC), in collaboration with The following organizations and individuals have provided the business community, government bodies and academics, is valuable contributions: working to increase the ability of Dutch society to defend itself in - Autoriteit Persoonsgegevens the digital domain. - Belastingdienst - Centric The NCSC supports the central government and organisations in - Dienst Publiek en Communicatie the critical infrastructure sectors by providing them with expertise - Forum Standaardisatie and advice, incident response and with actions to strengthen crisis - IBD management. In addition, the NCSC provides information and - KPN advice to citizens, the government and the business community - NLnet Labs relating to awareness and prevention. The NCSC thus constitutes - Northwave the central reporting and information point for IT threats and - Platform Internetstandaarden security incidents. - RDW - SURFnet These IT Security Guidelines for Transport Layer Security were frst - de Volksbank published by the NCSC in 2014. This update (v2.1) was published in - Z-CERT 2021. See the appendix Changes to these guidelines for more details. - Daniel Kahn Gillmor, ACLU This publication was produced in collaboration with the following - Tanja Lange, Eindhoven University of Technology partners: - Kenny Paterson, ETH Zurich - the national communication security agency (NBV), part of the - Rich Salz, Akamai Technologies general -

Matrixssl Developer's Guide
MatrixSSL Developer’s Guide MatrixSSL 3.2 Overview 1 Who Is This Document For? 1 Documentation Style Conventions 1 Commercial Version Differences 1 Security Considerations 2 SSL vs. TLS 2 Selecting Cipher Suites 2 Authentication Mode 3 Certificates and Private Keys 4 Application Integration Flow 5 ssl_t Structure 5 Initialization 6 Creating a Session 6 Handshaking 7 Communicating Securely With Peers 9 Ending a Session 11 Closing the Library 11 Configurable Features 12 Functionality Defines 12 PeerSec Networks, Inc. 410 Broadway Ave E. #205 Seattle, WA 98102 T 425.646.7850 F 206.501.4366 [email protected] www.peersec.com Debug Configuration 14 SSL Handshaking 16 Handshake Variations 16 Standard Handshake 16 Client Authentication 17 Session Resumption 18 Re-Handshakes 19 PeerSec Networks, Inc. 410 Broadway Ave E. #205 Seattle, WA 98102 T 425.646.7850 F 206.501.4366 [email protected] www.peersec.com Overview This developer’s guide is a general SSL/TLS overview and a MatrixSSL specific integration reference for adding SSL security into an application. Who Is This Document For? • Software developers that are securing applications with MatrixSSL • Anyone wanting to learn more about MatrixSSL • Anyone wanting to learn more about the SSL/TLS protocol Documentation Style Conventions • File names and directory paths are italicized. • C code literals are distinguished with the Monaco font. Commercial Version Differences Some of the compile options, functions, and structures in this document provide additional features only available in the commercially licensed version of MatrixSSL. Sections of this document that refer to the commercial version will be shaded. MatrixSSL Developer’s Guide © 2002-2011 1/19 Security Considerations Prior to working directly with the MatrixSSL library there are a couple SSL security concepts that application integrators should be familiar with. -

Matrixssl Diffie-Hellman Cipher Suites
MatrixSSL Diffie-Hellman Cipher Suites Electronic versions are uncontrolled unless directly accessed from the QA Document Control system. Printed version are uncontrolled except when stamped with ‘VALID COPY’ in red. External release of this document may require a NDA. © INSIDE Secure - 2013 - All rights reserved TABLE OF CONTENTS 1 ENABLING DIFFIE-HELLMAN IN MATRIXSSL ............................................................... 3 1.1 Raw Algorithm .................................................................................................... 3 1.2 Cipher Suites ...................................................................................................... 3 2 CLIENT SIDE DIFFIE-HELLMAN ................................................................................... 4 3 SERVER SIDE DIFFIE-HELLMAN .................................................................................. 5 3.1 matrixSslLoadDhParams ................................................................................... 5 3.2 matrixSslLoadDhParamsMem ........................................................................... 5 2 © INSIDE Secure - 2013 - All rights reserved 1 ENABLING DIFFIE-HELLMAN IN MATRIXSSL Diffie-Hellman is a key exchange algorithm that may be optionally included in the SSL protocol. 1.1 Raw Algorithm The define USE_DH must be enabled in the matrixsslConfig.h header file to compile in Diffie-Hellman support. 1.2 Cipher Suites The user must also enable any of the DH cipher suites that are desired. These defines are also listed in -

NIST Special Publication 800-78-4
NIST Special Publication 800-78-4 Cryptographic Algorithms and Key Sizes for Personal Identity Verification W. Timothy Polk Donna F. Dodson William E. Burr Hildegard Ferraiolo David Cooper This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-78-4 C O M P U T E R S E C U R I T Y NIST Special Publication 800-78-4 Cryptographic Algorithms and Key Sizes for Personal Identity Verification W. Timothy Polk Donna F. Dodson William E. Burr Hildegard Ferraiolo David Cooper Computer Security Division Information Technology Laboratory This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-78-4 May 2015 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Willie May, Under Secretary of Commerce for Standards and Technology and Director Special Publication 800-78-4 Cryptographic Algorithms and Key Sizes for PIV Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3541 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A-130, Appendix IV: Analysis of Key Sections. -

Advantage of Using Elliptic Curve Cryptography in SSL/TLS
DEPARTMENT OF COMPUTER SCIENCE UNIVERSITY OF CALIFORNIA SANTA BARBARA, CS 290G FALL TERM 2015 1 Advantage of using Elliptic curve cryptography in SSL/TLS Benjamin Clement Sebastian([email protected]) & Ugur Alpay Cenar([email protected]) Abstract—Mobile and wireless devices is experiencing an explo- in this protocol with release of TLS 1.0. In rest of this paper sive growth. These devices have strict Power, CPU power, mem- the phrase SSL are going to be used for both TLS and SSL, ory, bandwidth and latency constraints, which makes it important because both are frequently referred to as SSL in public. to have an efficient cryptosystem. It is also important for the web performance in general to have an efficient cryptosystem. Today Two communicating applications needs to use the same is RSA an widely used public-key cryptosystem.The problem with master key for encryption and decryption. This can be agreed RSA is that it requires large key sizes which can lead to lower by SSL handshake. bandwidth and higher CPU usage. Elliptic Curve Cryptography The Handshake protocol goes like: (ECC) is emerging as an attractive public-key cryptosystem. It offers equivalent security level with smaller key sizes, which can lead to faster computation and lower power usage. SSL/TLS is the most widely used security protocol on the web, Algorithm A: SSL handshake so more efficient SSL/TLS will have a significant impact on the web performance. This paper compares those two cryptosystems 1 Client: ClientHello message to the server. 1 to see if ECC gives significant advantage over RSA regarding to 2 performance when implemented in SSL/TLS protocol.