SSL/TLS Implementation CIO-IT Security-14-69
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Treasury X.509 Certificate Policy [TREASURYCP].” It Only Addresses Where an OLT PKI’S Requirements Differ from the Requirements for Basic Assurance in [TREASURYCP]](https://docslib.b-cdn.net/cover/6254/treasury-x-509-certificate-policy-treasurycp-it-only-addresses-where-an-olt-pki-s-requirements-differ-from-the-requirements-for-basic-assurance-in-treasurycp-6254.webp)
Treasury X.509 Certificate Policy [TREASURYCP].” It Only Addresses Where an OLT PKI’S Requirements Differ from the Requirements for Basic Assurance in [TREASURYCP]
UNCLASSIFIED UNITED STATES DEPARTMENT OF THE TREASURY DEPARTMENT OF THE TREASURY PUBLIC KEY INFRASTRUCTURE (PKI) X.509 CERTIFICATE POLICY VERSION 3.4 April 27, 2021 PKI Policy Management Authority (PMA) DATE DANIEL W. WOOD 1 UNCLASSIFIED DOCUMENT VERSION CONTROL Version Date Author(s) Description Reason For Change Bring the Treasury PKI Policy into Department of the compliance with FPKIPA change Treasury PKI Policy in 2.0 January 2008 James Schminky proposal requiring all cross certified RFC PKI Policies to be in RFC 3647 3647 format. format. As a result of mapping the Treasury Errata changes to sections PKI Policy to Federal Policy, a 2.2.1, 2.1 March 17, 2009 James Schminky number of minor changes and 4.8, 4.912, 5.5, and omissions where identified and 7.1.3. corrected. As a result of the PMA annual Errata changes to sections review a number of minor 5.6, and 6.3.2. Change corrections, Federal Bridge proposal changes to 2.4, 2.2 March 11, 2010 James Schminky Certification Authority (FBCA) 4.2.2, 5.1, 5.1.1 5.1.2.1, Policy Change Proposal Number: 5.4.4, 5.4.5, 6.1.6, 6.5.1, 2009-02 and 2010-01, and Treasury and 6.7. Change Proposal Change proposal changes As a result of FBCA Policy Change 2.3 April 15, 2010 James Schminky to 8.1 and 8.4. Proposal Number: 2010-02. Changes Proposal As a result of FBCA Policy Change Changes to 1.3.1.8, Proposal Numbers; 2010-3 thru 8 2.4 March 22, 2011 James Schminky 3.1.1&.2, 3.1.5, 3.2.3.1, and CPCA policy Change Proposal 4.7, 6.1.5, 8.1, and 9.4.3. -

SSL/TLS Implementation CIO-IT Security-14-69
DocuSign Envelope ID: BE043513-5C38-4412-A2D5-93679CF7A69A IT Security Procedural Guide: SSL/TLS Implementation CIO-IT Security-14-69 Revision 6 April 6, 2021 Office of the Chief Information Security Officer DocuSign Envelope ID: BE043513-5C38-4412-A2D5-93679CF7A69A CIO-IT Security-14-69, Revision 6 SSL/TLS Implementation VERSION HISTORY/CHANGE RECORD Person Page Change Posting Change Reason for Change Number of Number Change Change Initial Version – December 24, 2014 N/A ISE New guide created Revision 1 – March 15, 2016 1 Salamon Administrative updates to Clarify relationship between this 2-4 align/reference to the current guide and CIO-IT Security-09-43 version of the GSA IT Security Policy and to CIO-IT Security-09-43, IT Security Procedural Guide: Key Management 2 Berlas / Updated recommendation for Clarification of requirements 7 Salamon obtaining and using certificates 3 Salamon Integrated with OMB M-15-13 and New OMB Policy 9 related TLS implementation guidance 4 Berlas / Updates to clarify TLS protocol Clarification of guidance 11-12 Salamon recommendations 5 Berlas / Updated based on stakeholder Stakeholder review / input Throughout Salamon review / input 6 Klemens/ Formatting, editing, review revisions Update to current format and Throughout Cozart- style Ramos Revision 2 – October 11, 2016 1 Berlas / Allow use of TLS 1.0 for certain Clarification of guidance Throughout Salamon server through June 2018 Revision 3 – April 30, 2018 1 Berlas / Remove RSA ciphers from approved ROBOT vulnerability affected 4-6 Salamon cipher stack -

Using Frankencerts for Automated Adversarial Testing of Certificate
Using Frankencerts for Automated Adversarial Testing of Certificate Validation in SSL/TLS Implementations Chad Brubaker ∗ y Suman Janay Baishakhi Rayz Sarfraz Khurshidy Vitaly Shmatikovy ∗Google yThe University of Texas at Austin zUniversity of California, Davis Abstract—Modern network security rests on the Secure Sock- many open-source implementations of SSL/TLS are available ets Layer (SSL) and Transport Layer Security (TLS) protocols. for developers who need to incorporate SSL/TLS into their Distributed systems, mobile and desktop applications, embedded software: OpenSSL, NSS, GnuTLS, CyaSSL, PolarSSL, Ma- devices, and all of secure Web rely on SSL/TLS for protection trixSSL, cryptlib, and several others. Several Web browsers against network attacks. This protection critically depends on include their own, proprietary implementations. whether SSL/TLS clients correctly validate X.509 certificates presented by servers during the SSL/TLS handshake protocol. In this paper, we focus on server authentication, which We design, implement, and apply the first methodology for is the only protection against man-in-the-middle and other large-scale testing of certificate validation logic in SSL/TLS server impersonation attacks, and thus essential for HTTPS implementations. Our first ingredient is “frankencerts,” synthetic and virtually any other application of SSL/TLS. Server authen- certificates that are randomly mutated from parts of real cer- tication in SSL/TLS depends entirely on a single step in the tificates and thus include unusual combinations of extensions handshake protocol. As part of its “Server Hello” message, and constraints. Our second ingredient is differential testing: if the server presents an X.509 certificate with its public key. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Fast Elliptic Curve Cryptography in Openssl
Fast Elliptic Curve Cryptography in OpenSSL Emilia K¨asper1;2 1 Google 2 Katholieke Universiteit Leuven, ESAT/COSIC [email protected] Abstract. We present a 64-bit optimized implementation of the NIST and SECG-standardized elliptic curve P-224. Our implementation is fully integrated into OpenSSL 1.0.1: full TLS handshakes using a 1024-bit RSA certificate and ephemeral Elliptic Curve Diffie-Hellman key ex- change over P-224 now run at twice the speed of standard OpenSSL, while atomic elliptic curve operations are up to 4 times faster. In ad- dition, our implementation is immune to timing attacks|most notably, we show how to do small table look-ups in a cache-timing resistant way, allowing us to use precomputation. To put our results in context, we also discuss the various security-performance trade-offs available to TLS applications. Keywords: elliptic curve cryptography, OpenSSL, side-channel attacks, fast implementations 1 Introduction 1.1 Introduction to TLS Transport Layer Security (TLS), the successor to Secure Socket Layer (SSL), is a protocol for securing network communications. In its most common use, it is the \S" (standing for \Secure") in HTTPS. Two of the most popular open- source cryptographic libraries implementing SSL and TLS are OpenSSL [19] and Mozilla Network Security Services (NSS) [17]: OpenSSL is found in, e.g., the Apache-SSL secure web server, while NSS is used by Mozilla Firefox and Chrome web browsers, amongst others. TLS provides authentication between connecting parties, as well as encryp- tion of all transmitted content. Thus, before any application data is transmit- ted, peers perform authentication and key exchange in a TLS handshake. -

Configuring SSL for Services and Servers
Barracuda Web Application Firewall Configuring SSL for Services and Servers https://campus.barracuda.com/doc/4259877/ Configuring SSL for SSL Enabled Services You can configure SSL encryption for data transmitted between the client and the service. In the BASIC > Services page, click Edit next to a listed service and configure the following fields: Status – Set to On to enable SSL on your service. Status defaults to On for a newly created SSL enabled service. Certificate – Select a certificate presented to the browser when accessing the service. Note that only RSA certificates are listed here. If you have not created the certificate, select Generate Certificate from the drop-down list to generate a self-signed certificate. For more information on how to create self- signed certificates, see Creating a Client Certificate. If you want to upload a self-signed certificate, select Upload Certificate from the drop- down list. Provide the details about the certificate in the Upload Certificate dialog box. For information on how to upload a certificate, see Adding an SSL Certificate. Select ECDSA Certificate – Select an ECDSA certificate presented to the browser when accessing the service. SSL/TLS Quick Settings - Select an option to automatically configure the SSL/TLS protocols and ciphers. Use Configured Values - This option allows you to use the previously saved values. If the values are not saved, the Factory Preset option can be used. Factory Preset - This option allows you to enable TLS 1.1, TLS 1.2 and TLS 1.3 protocols without configuring override ciphers. Mozilla Intermediate Compatibility (Default, Recommended) - This configuration is a recommended configuration when you want to enable TLS 1.2 and TLS 1.3 and configure override ciphers for the same. -
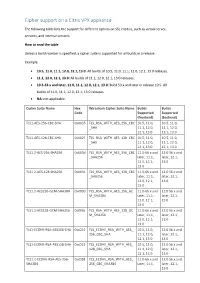
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Implementing PKI Services on Z/OS
Front cover Implementing PKI Services on z/OS Installation of PKI and all of its prerequistes on z/OS An example of the PKI Exit PKI’s use of ICSF to store Master Key Chris Rayns Theo Antoff Jack Jones Patrick Kappeler Vicente Ranieri Roland Trauner ibm.com/redbooks International Technical Support Organization Implementing PKI Services on z/OS February 2004 SG24-6968-00 Note: Before using this information and the product it supports, read the information in “Notices” on page vii. First Edition (February 2004) This edition applies to z/OS Version 1, Release 3. © Copyright International Business Machines Corporation 2004. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . vii Trademarks . viii Preface . ix The team that wrote this redbook. ix Become a published author . x Comments welcome. xi Chapter 1. Security Server PKI Services. 1 1.1 Overview of digital certificate. 2 1.2 The PKIX standards . 4 1.2.1 CA hierarchy . 6 1.2.2 The X.509 certificate and Certificate Revocation List . 9 1.2.3 The x.509 v3 certificate extension fields . 14 1.2.4 Certificate and CRL appearance. 17 1.3 The z/OS PKI Services . 21 1.3.1 Security Server PKI Services in z/OS . 21 1.3.2 Prerequisite products . 22 1.3.3 Requests supported by z/OS PKI Services. 23 1.3.4 Browser and server certificates. 24 1.3.5 The z/OS PKI Services architecture . 26 1.4 Security Server PKI Services enhancement in z/OS V1R4. -

Amazon Trust Services Certificate Policy
Certificate Policy Version 1.0.9 1 1 INTRODUCTION ................................................................................................................................................... 13 1.1 Overview ...................................................................................................................................................... 13 1.1.1 Compliance ............................................................................................................................................ 13 1.1.2 Types of Certificates .............................................................................................................................. 13 1.1.2.1 CA-Certificates .............................................................................................................................. 13 1.1.2.1.1 Missing Heading ........................................................................................................................ 14 1.1.2.1.2 Missing Heading ........................................................................................................................ 14 1.1.2.1.3 Terminus CA-Certificates .......................................................................................................... 14 1.1.2.1.4 Policy CA-Certificates ................................................................................................................ 14 1.1.2.1.5 Technically Constrained CA-Certificates .................................................................................. -

Dynamic Public Key Certificates with Forward Secrecy
electronics Article Dynamic Public Key Certificates with Forward Secrecy Hung-Yu Chien Department of Information Management, National Chi Nan University, Nantou 54561, Taiwan; [email protected] Abstract: Conventionally, public key certificates bind one subject with one static public key so that the subject can facilitate the services of the public key infrastructure (PKI). In PKI, certificates need to be renewed (or revoked) for several practical reasons, including certificate expiration, private key breaches, condition changes, and possible risk reduction. The certificate renewal process is very costly, especially for those environments where online authorities are not available or the connection is not reliable. A dynamic public key certificate (DPKC) facilitates the dynamic changeover of the current public–private key pairs without renewing the certificate authority (CA). This paper extends the previous study in several aspects: (1) we formally define the DPKC; (2) we formally define the security properties; (3) we propose another implementation of the Krawczyk–Rabin chameleon-hash- based DPKC; (4) we propose two variants of DPKC, using the Ateniese–Medeiros key-exposure-free chameleon hash; (5) we detail two application scenarios. Keywords: dynamic public key certificate; chameleon signature; certificate renewal; wireless sensor networks; perfect forward secrecy 1. Introduction Citation: Chien, H.-Y. Dynamic Certificates act as the critical tokens in conventional PKI systems. With the trust Public Key Certificates with Forward of the CA, a -

SSL Checklist for Pentesters
SSL Checklist for Pentesters Jerome Smith BSides MCR, 27th June 2014 # whoami whoami jerome • Pentester • Author/trainer – Hands-on technical – Web application, infrastructure, wireless security • Security projects – Log correlation – Dirty data – Incident response exercises • Sysadmin • MSc Computing Science (Dist) • www.exploresecurity.com | @exploresecurity Introduction • Broad review of SSL/TLS checks – Viewpoint of pentester – Pitfalls – Manually replicating what tools do (unless you told the client that SSL Labs would be testing them ) – Issues to consider reporting (but views are my own) • While SSL issues are generally low in priority, it’s nice to get them right! • I’m not a cryptographer: this is all best efforts SSLv2 • Flawed, e.g. no handshake protection → MITM downgrade • Modern browsers do not support SSLv2 anyway – Except for IE but it’s disabled by default from IE7 – That mitigates the risk these days – http://en.wikipedia.org/wiki/Transport_Layer_Security#W eb_browsers • OpenSSL 1.0.0+ doesn’t support it – Which means SSLscan won’t find it – General point: tools that dynamically link to an underlying SSL library in the OS can be limited by what that library supports SSLv2 • Same scan on different OpenSSL versions: SSLv2 • testssl.sh warns you – It can work with any installed OpenSSL version • OpenSSL <1.0.0 s_client -ssl2 switch – More on this later • Recompile OpenSSL – http://blog.opensecurityresearch.com/2013/05/fixing-sslv2-support- in-kali-linux.html • SSLyze 0.7+ is statically linked – Watch out for bug https://github.com/iSECPartners/sslyze/issues/73 -

Hosting Multiple Certs on One IP
Hosting multiple SSL Certicates on a single IP S Solving the IPv4 shortage dilemma FULL COMPATIBILITY When it comes to SSL security, hosting companies are increasingly facing In public environments, using SNI alone would mean cutting access to a issues related to IP addresses scarcity. Today every digital certificate used large number of potential site visitors as around 15% of systems (as of to provide an SSL connection on a webserver needs a dedicated IP January 2013) are incompatible with SNI. address, making it difficult for hosting companies to respond to increas- ing demand for security. The true solution GlobalSign has developed a solution to address hosting companies’ operational limitations and to let them run multiple certificates on a By coupling the Server Name Indication technology with SSL Certificates single IP address, at no detriment to browser and operating system and a CloudSSL Certificate from GlobalSign, multiple certificates can compatibility. now be hosted on a single IP without losing potential visitors that might lack SNI support. Host Headers GlobalSign SSL Certificates can be installed on several name-based virtual hosts as per any SNI-based https website. Each website has its To address the current concern of shortage of IPv4 addresses, most own certificate, allowing for even the highest levels of security (such as websites have been configured as name-based virtual hosts for years. Extended Validation Certificates). When several websites share the same IP number, the server will select the website to display based on the name provided in the Host Header. GlobalSign will then provide a free fall-back CloudSSL certificate for legacy configurations, enabling the 15% of visitors that do not have SNI Unfortunately this doesn’t allow for SSL security as the SSL handshake compatibility to access the secure websites on that IP address.