TLS) Protocol Configurations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mihir Bellare Curriculum Vitae Contents
Mihir Bellare Curriculum vitae August 2018 Department of Computer Science & Engineering, Mail Code 0404 University of California at San Diego 9500 Gilman Drive, La Jolla, CA 92093-0404, USA. Phone: (858) 534-4544 ; E-mail: [email protected] Web Page: http://cseweb.ucsd.edu/~mihir Contents 1 Research areas 2 2 Education 2 3 Distinctions and Awards 2 4 Impact 3 5 Grants 4 6 Professional Activities 5 7 Industrial relations 5 8 Work Experience 5 9 Teaching 6 10 Publications 6 11 Mentoring 19 12 Personal Information 21 2 1 Research areas ∗ Cryptography and security: Provable security; authentication; key distribution; signatures; encryp- tion; protocols. ∗ Complexity theory: Interactive and probabilistically checkable proofs; approximability ; complexity of zero-knowledge; randomness in protocols and algorithms; computational learning theory. 2 Education ∗ Massachusetts Institute of Technology. Ph.D in Computer Science, September 1991. Thesis title: Randomness in Interactive Proofs. Thesis supervisor: Prof. S. Micali. ∗ Massachusetts Institute of Technology. Masters in Computer Science, September 1988. Thesis title: A Signature Scheme Based on Trapdoor Permutations. Thesis supervisor: Prof. S. Micali. ∗ California Institute of Technology. B.S. with honors, June 1986. Subject: Mathematics. GPA 4.0. Class rank 4 out of 227. Summer Undergraduate Research Fellow 1984 and 1985. ∗ Ecole Active Bilingue, Paris, France. Baccalauréat Série C, June 1981. 3 Distinctions and Awards ∗ PET (Privacy Enhancing Technologies) Award 2015 for publication [154]. ∗ Fellow of the ACM (Association for Computing Machinery), 2014. ∗ ACM Paris Kanellakis Theory and Practice Award 2009. ∗ RSA Conference Award in Mathematics, 2003. ∗ David and Lucille Packard Foundation Fellowship in Science and Engineering, 1996. (Twenty awarded annually in all of Science and Engineering.) ∗ Test of Time Award, ACM CCS 2011, given for [81] as best paper from ten years prior. -

Know Before You Go
Know Before You Go NORWAY A Guide to Keep You Safe Abroad provided by: Pathways to Safety International Updated May 2019 KNOW BEFORE YOU GO: NORWAY 2 Let’s be perfectly clear, the number one way to prevent sexual assault is to not rape. While the responsibility of ending sexual gender based violence is on the perpetrators, this guide will offer general safety tips, country-specific information, and resources to help prevent and prepare travelers for the possibility of sexual assault abroad. GENERAL SAFETY TIPS: 1. Use the buddy system and travel with friends. 7 out of 10 2. Be aware of social and cultural norms. For example, looking at someone in rapes are the eyes when you speak to them is perfectly normal in the U.S., but in committed another country that could signify you’re interested in the person. by someone known to the 3. Recognize controlling behavior when entering a relationship. Most rape 1 survivors recall feeling “uncomfortable” about some of their partner’s behaviors victim such as degrading jokes/language or refusal to accept “no” as an answer, whether in a sexual context or otherwise.2 4. Avoid secluded places where you could be more vulnerable. Meet new people in public spaces and let a trusted friend know where you’ll be beforehand. Always have a backup plan in mind. 5. Trust your gut. Many victims have a “bad feeling” right before an assault takes place. It’s okay to leave a situation that is making you feel uncomfortable. Stay alert and aware in new social settings and places. -

The Order of Encryption and Authentication for Protecting Communications (Or: How Secure Is SSL?)?
The Order of Encryption and Authentication for Protecting Communications (Or: How Secure is SSL?)? Hugo Krawczyk?? Abstract. We study the question of how to generically compose sym- metric encryption and authentication when building \secure channels" for the protection of communications over insecure networks. We show that any secure channels protocol designed to work with any combina- tion of secure encryption (against chosen plaintext attacks) and secure MAC must use the encrypt-then-authenticate method. We demonstrate this by showing that the other common methods of composing encryp- tion and authentication, including the authenticate-then-encrypt method used in SSL, are not generically secure. We show an example of an en- cryption function that provides (Shannon's) perfect secrecy but when combined with any MAC function under the authenticate-then-encrypt method yields a totally insecure protocol (for example, ¯nding passwords or credit card numbers transmitted under the protection of such protocol becomes an easy task for an active attacker). The same applies to the encrypt-and-authenticate method used in SSH. On the positive side we show that the authenticate-then-encrypt method is secure if the encryption method in use is either CBC mode (with an underlying secure block cipher) or a stream cipher (that xor the data with a random or pseudorandom pad). Thus, while we show the generic security of SSL to be broken, the current practical implementations of the protocol that use the above modes of encryption are safe. 1 Introduction The most widespread application of cryptography in the Internet these days is for implementing a secure channel between two end points and then exchanging information over that channel. -

Multi-Device for Signal
Multi-Device for Signal S´ebastienCampion3, Julien Devigne1, C´elineDuguey1;2, and Pierre-Alain Fouque2 1 DGA Maˆıtrisede l’information, Bruz, France [email protected] 2 Irisa, Rennes, France, [email protected], [email protected] Abstract. Nowadays, we spend our life juggling with many devices such as smartphones, tablets or laptops, and we expect to easily and efficiently switch between them without losing time or security. However, most ap- plications have been designed for single device usage. This is the case for secure instant messaging (SIM) services based on the Signal proto- col, that implements the Double Ratchet key exchange algorithm. While some adaptations, like the Sesame protocol released by the developers of Signal, have been proposed to fix this usability issue, they have not been designed as specific multi-device solutions and no security model has been formally defined either. In addition, even though the group key exchange problematic appears related to the multi-device case, group solutions are too generic and do not take into account some properties of the multi-device setting. Indeed, the fact that all devices belong to a single user can be exploited to build more efficient solutions. In this paper, we propose a Multi-Device Instant Messaging protocol based on Signal, ensuring all the security properties of the original Signal. Keywords: cryptography, secure instant messaging, ratchet, multi-device 1 Introduction 1.1 Context Over the last years, secure instant messaging has become a key application ac- cessible on smartphones. In parallel, more and more people started using several devices - a smartphone, a tablet or a laptop - to communicate. -

Cryptographic Agility in Practice Emerging Use-Cases
CRYPTOGRAPHIC AGILITY IN PRACTICE EMERGING USE-CASES AUTHORS: Tyson Macaulay Chief Product Officer InfoSec Global Richard Henderson Chief Technology Officer North America InfoSec Global USE CASES WHITEPAPER Summary Cryptography is the bedrock upon which modern data and communications security rests. Cryptography provides the ability to not just keep data and communications confidential, but also underlies virtually all means to establish the identity of people and things in a virtualized world. But cryptography has historically been static: “set and forget”. The world has changed while cryptography has not, and there is a pressing need to move towards dynamically managed and agile cryptographic systems: “cryptographic agility”. Data transparently moves in and out of trusted and untrusted hardware, software, within complex, integrated IoT/IIoT (Internet of Things/Industrial Internet of Things) devices and platforms, and across international borders. Once deployed or implemented, virtually all of these are unable to make changes to their digital identities or the cryptography they use without a hands-on, bespoke process of re-installation, re-configuration, and downtime... if fixes and updates are available at all. What does this mean? For devices and platforms, a cryptographic vulnerability in may require the device be replaced, discarded, or additional in-line infrastructure be deployed to mitigate the threat. For applications and systems, patches must be applied, systems shut down, and expensive human expertise contracted to make it all work. This “static” cryptographic security model has already caused substantial public safety, consumer privacy, financial, and health risks - all associated with device and system vulnerabilities exploited by malicious actors. For now, there are no standards and few tools for the management of cryptography. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Agile and Versatile Quantum Communication: Signatures and Secrets
PHYSICAL REVIEW X 11, 011038 (2021) Agile and Versatile Quantum Communication: Signatures and Secrets ‡ † ‡ Stefan Richter ,1,2,*, Matthew Thornton ,3, , Imran Khan,1,2 Hamish Scott ,3 Kevin Jaksch ,1,2 Ulrich Vogl,1,2 Birgit Stiller,1,2 Gerd Leuchs,1,2 Christoph Marquardt,1,2 and Natalia Korolkova 3 1Max Planck Institute for the Science of Light, Staudtstraße 2, 91058 Erlangen, Germany 2Institute of Optics, Information and Photonics, University of Erlangen-Nuremberg, Staudtstraße 7/B2, Erlangen, Germany 3School of Physics and Astronomy, University of St Andrews, North Haugh, St Andrews KY16 9SS, United Kingdom (Received 27 January 2020; revised 24 November 2020; accepted 18 December 2020; published 24 February 2021; corrected 9 March 2021) Agile cryptography allows for a resource-efficient swap of a cryptographic core in case the security of an underlying classical cryptographic algorithm becomes compromised. Conversely, versatile cryptography allows the user to switch the cryptographic task without requiring any knowledge of its inner workings. In this paper, we suggest how these related principles can be applied to the field of quantum cryptography by explicitly demonstrating two quantum cryptographic protocols, quantum digital signatures (QDS) and quantum secret sharing (QSS), on the same hardware sender and receiver platform. Crucially, the protocols differ only in their classical postprocessing. The system is also suitable for quantum key distribution (QKD) and is highly compatible with deployed telecommunication infrastructures, since it uses standard quadrature phase-shift keying encoding and heterodyne detection. For the first time, QDS protocols are modified to allow for postselection at the receiver, enhancing protocol performance. The cryptographic primitives QDS and QSS are inherently multipartite, and we prove that they are secure not only when a player internal to the task is dishonest, but also when (external) eavesdropping on the quantum channel is allowed. -

A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based on Elliptic Curve Cryptography
applied sciences Article A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based on Elliptic Curve Cryptography Haotian Liang , Guidong Zhang *, Wenjin Hou, Pinyi Huang, Bo Liu and Shouliang Li * School of Information Science and Engineering, Lanzhou University, Lanzhou 730000, China; [email protected] (H.L.); [email protected] (W.H.); [email protected] (P.H.); [email protected] (B.L.) * Correspondence: [email protected] (G.Z.); [email protected] (S.L.); Tel.: +86-185-0948-7799 (S.L.) Abstract: Most of the image encryption schemes based on chaos have so far employed symmetric key cryptography, which leads to a situation where the key cannot be transmitted in public channels, thus limiting their extended application. Based on the elliptic curve cryptography (ECC), we proposed a public key image encryption method where the hash value derived from the plain image was encrypted by ECC. Furthermore, during image permutation, a novel algorithm based on different- sized block was proposed. The plain image was firstly divided into five planes according to the amount of information contained in different bits: the combination of the low 4 bits, and other four planes of high 4 bits respectively. Second, for different planes, the corresponding method of block partition was followed by the rule that the higher the bit plane, the smaller the size of the partitioned block as a basic unit for permutation. In the diffusion phase, the used hyperchaotic sequences in permutation were applied to improve the efficiency. Lots of experimental simulations and cryptanalyses were implemented in which the NPCR and UACI are 99.6124% and 33.4600% Citation: Liang, H.; Zhang, G.; Hou, respectively, which all suggested that it can effectively resist statistical analysis attacks and chosen W.; Huang, P.; Liu, B.; Li, S. -

<Document Title>
TLS Specification for Storage Systems Version 1.0.1 ABSTRACT: This document specifies the requirements and guidance for use of the Transport Layer Security (TLS) protocol in conjunction with data storage technologies. The requirements are intended to facilitate secure interoperability of storage clients and servers as well as non-storage technologies that may have similar interoperability needs. This document was developed with the expectation that future versions of SMI-S and CDMI could leverage these requirements to ensure consistency between these standards as well as to more rapidly adjust the security functionality in these standards. This document has been released and approved by the SNIA. The SNIA believes that the ideas, methodologies and technologies described in this document accurately represent the SNIA goals and are appropriate for widespread distribution. Suggestion for revision should be directed to http://www.snia.org/feedback/. SNIA Technical Position November 20, 2014 USAGE The SNIA hereby grants permission for individuals to use this document for personal use only, and for corporations and other business entities to use this document for internal use only (including internal copying, distribution, and display) provided that: 1. Any text, diagram, chart, table or definition reproduced shall be reproduced in its entirety with no alteration, and, 2. Any document, printed or electronic, in which material from this document (or any portion hereof) is reproduced shall acknowledge the SNIA copyright on that material, and shall credit the SNIA for granting permission for its reuse. Other than as explicitly provided above, you may not make any commercial use of this document, sell any or this entire document, or distribute this document to third parties. -

Quantum Computing Threat: How to Keep Ahead
Think openly, build securely White paper: Quantum Computing Threat: How to Keep Ahead Ë PQShield Ƕ February 2021 © PQShield Ltd | www.pqshield.com | PQShield Ltd, Oxford, OX2 7HT, UK Cryptographic agility and a clear roadmap to the upcoming NIST standards are key to a smooth and secure transition. 1 Background 1.1 New Cryptography Standards The NIST (U.S. National Institute of Standards and Technology) Post‐Quantum Cryptography (PQC) Project has been running since 2016 and is now in its third, final evaluation round. This project standardizes new key establishment and digital signature algorithms that have been designed to be resistant against attacks by quantum computers. These new algorithms are intended to replace current classical‐security RSA and Elliptic Cryptography (ECDH, ECDSA) standards in applications. The particular mathematical problems that RSA and Elliptic Cryptography are based onareeasy (polynomial‐time solvable) for quantum computers. Unless complemented with quantum‐safe cryptography, this will allow for the forgery of digital signatures (integrity compromise) and de‐ cryption of previously encrypted data (confidentiality compromise) in the future. This is aheight‐ ened risk for organizations that need to secure data for long periods of time; government orga‐ nizations that handle and secure classified information have largely been the drivers ofthepost‐ quantum standardization and its adoption in the field, but banks, financial services, healthcare providers, those developing intellectual property and many others increasingly feel the need to ensure that they can protect their customers and IP – now and in the future. 1.2 Quantum Threat and Post-Quantum Cryptography The current position of NCSC (UK’s National Cyber Security Centre) and NSA (USA’s National Se‐ curity Agency) is that the best mitigation against the threat of quantum computers is quantum‐ safe cryptography, also known as post‐quantum cryptography (PQC). -
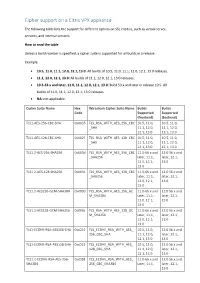
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session.