Prying Open Pandora's Box: KCI Attacks Against
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cryptography
56 Protecting Information With Cryptography Chapter by Peter Reiher (UCLA) 56.1 Introduction In previous chapters, we’ve discussed clarifying your security goals, determining your security policies, using authentication mechanisms to identify principals, and using access control mechanisms to enforce poli- cies concerning which principals can access which computer resources in which ways. While we identified a number of shortcomings and prob- lems inherent in all of these elements of securing your system, if we re- gard those topics as covered, what’s left for the operating system to worry about, from a security perspective? Why isn’t that everything? There are a number of reasons why we need more. Of particular im- portance: not everything is controlled by the operating system. But per- haps you respond, you told me the operating system is all-powerful! Not really. It has substantial control over a limited domain – the hardware on which it runs, using the interfaces of which it is given control. It has no real control over what happens on other machines, nor what happens if one of its pieces of hardware is accessed via some mechanism outside the operating system’s control. But how can we expect the operating system to protect something when the system does not itself control access to that resource? The an- swer is to prepare the resource for trouble in advance. In essence, we assume that we are going to lose the data, or that an opponent will try to alter it improperly. And we take steps to ensure that such actions don’t cause us problems. -

Using Frankencerts for Automated Adversarial Testing of Certificate
Using Frankencerts for Automated Adversarial Testing of Certificate Validation in SSL/TLS Implementations Chad Brubaker ∗ y Suman Janay Baishakhi Rayz Sarfraz Khurshidy Vitaly Shmatikovy ∗Google yThe University of Texas at Austin zUniversity of California, Davis Abstract—Modern network security rests on the Secure Sock- many open-source implementations of SSL/TLS are available ets Layer (SSL) and Transport Layer Security (TLS) protocols. for developers who need to incorporate SSL/TLS into their Distributed systems, mobile and desktop applications, embedded software: OpenSSL, NSS, GnuTLS, CyaSSL, PolarSSL, Ma- devices, and all of secure Web rely on SSL/TLS for protection trixSSL, cryptlib, and several others. Several Web browsers against network attacks. This protection critically depends on include their own, proprietary implementations. whether SSL/TLS clients correctly validate X.509 certificates presented by servers during the SSL/TLS handshake protocol. In this paper, we focus on server authentication, which We design, implement, and apply the first methodology for is the only protection against man-in-the-middle and other large-scale testing of certificate validation logic in SSL/TLS server impersonation attacks, and thus essential for HTTPS implementations. Our first ingredient is “frankencerts,” synthetic and virtually any other application of SSL/TLS. Server authen- certificates that are randomly mutated from parts of real cer- tication in SSL/TLS depends entirely on a single step in the tificates and thus include unusual combinations of extensions handshake protocol. As part of its “Server Hello” message, and constraints. Our second ingredient is differential testing: if the server presents an X.509 certificate with its public key. -

Not-Quite-So-Broken TLS Lessons in Re-Engineering a Security Protocol Specification and Implementation
Not-quite-so-broken TLS Lessons in re-engineering a security protocol specification and implementation David Kaloper Meršinjak Hannes Mehnert Peter Sewell Anil Madhavapeddy University of Cambridge, Computer Labs Usenix Security, Washington DC, 12 August 2015 INT SSL23_GET_CLIENT_HELLO(SSL *S) { CHAR BUF_SPACE[11]; /* REQUEST THIS MANY BYTES IN INITIAL READ. * WE CAN DETECT SSL 3.0/TLS 1.0 CLIENT HELLOS * ('TYPE == 3') CORRECTLY ONLY WHEN THE FOLLOWING * IS IN A SINGLE RECORD, WHICH IS NOT GUARANTEED BY * THE PROTOCOL SPECIFICATION: * BYTE CONTENT * 0 TYPE \ * 1/2 VERSION > RECORD HEADER * 3/4 LENGTH / * 5 MSG_TYPE \ * 6-8 LENGTH > CLIENT HELLO MESSAGE Common CVE sources in 2014 Class # Memory safety 15 State-machine errors 10 Certificate validation 5 ASN.1 parsing 3 (OpenSSL, GnuTLS, SecureTransport, Secure Channel, NSS, JSSE) Root causes Error-prone languages Lack of separation Ambiguous and untestable specification nqsb approach Choice of language and idioms Separation and modular structure A precise and testable specification of TLS Reuse between specification and implementation Choice of language and idioms OCaml: a memory-safe language with expressive static type system Well contained side-effects Explicit flows of data Value-based Explicit error handling We leverage it for abstraction and automated resource management. Formal approaches Either reason about a simplified model of the protocol; or reason about small parts of OpenSSL. In contrast, we are engineering a deployable implementation. nqsb-tls A TLS stack, developed from scratch, with dual goals: Executable specification Usable TLS implementation Structure nqsb-TLS ML module layout Core Is purely functional: VAL HANDLE_TLS : STATE -> BUFFER -> [ `OK OF STATE * BUFFER OPTION * BUFFER OPTION | `FAIL OF FAILURE ] Core OCaml helps to enforce state-machine invariants. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Hannes Tschofenig
Securing IoT applications with Mbed TLS Hannes Tschofenig Part#2: Public Key-based authentication March 2018 © 2018 Arm Limited Munich Agenda • For Part #2 of the webinar we are moving from Pre-Shared Secrets (PSKs) to certificated-based authentication. • TLS-PSK ciphersuites have • great performance, • low overhead, • small code size. • Drawback is the shared key concept. • Public key cryptography was invented to deal with this drawback (but itself has drawbacks). 2 © 2018 Arm Limited Public Key Infrastructure and certificate configuration © 2018 Arm Limited Public Key Infrastructure Various PKI deployments in existence Structure of our PKI The client has to store: self-signed • Client certificate plus corresponding private key. CA cert • CA certificate, which serves as the trust anchor. The server has to store: Signed by CA Signed by CA • Server certificate plus corresponding private key. Client cert Server cert (Some information for authenticating the client) 4 © 2018 Arm Limited Generating certificates (using OpenSSL tools) • When generating certificates you will be prompted to enter info. You are about to be asked to enter information that will be • The CA cert will end up in the trust incorporated into your certificate request. What you are about to enter is what is called a Distinguished anchor store of the client. Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, • The Common Name used in the server If you enter '.', the field will be left blank. ----- cert needs to be resolvable via DNS Country Name (2 letter code) [AU]:. -

PCI Assessment Evidence of PCI Policy Compliance
PCI Assessment Evidence of PCI Policy Compliance CONFIDENTIALITY NOTE: The information contained in this report document is for the Prepared for: exclusive use of the client specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this report is not the client or Prospect or Customer addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its contents in any way. Prepared by: Your Company Name Evidence of PCI Policy Compliance PCI ASSESSMENT Table of Contents 1 - Overview 1.1 - Security Officer 1.2 - Overall Risk 2 - PCI DSS Evidence of Compliance 2.1 - Install and maintain firewall to protect cardholder data 2.1.1.1 - Requirements for firewall at each Internet connections and between DMZ and internal network zone 2.1.1.2 - Business justification for use of all services, protocols and ports allowed 2.1.2 - Build firewall and router configurations that restrict connections between untrusted networks and the cardholder data environment 2.1.2.1 - Restrict inbound and outbound to that which is necessary for the cardholder data environment 2.1.2.3 - Do not allow unauthorized outbound traffic from the cardholder data environment to the Internet 2.1.2.4 - Implement stateful inspection (also known as dynamic packet filtering) 2.1.2.5 - Do not allow unauthorized outbound traffic from the cardholder data environment to the Internet 2.2 - Prohibition of vendor-supplied default password for systems and security parameters 2.2.1 -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

Sizzle: a Standards-Based End-To-End Security Architecture for the Embedded Internet
Sizzle: A Standards-based end-to-end Security Architecture for the Embedded Internet Vipul Gupta, Matthew Millard,∗ Stephen Fung*, Yu Zhu*, Nils Gura, Hans Eberle, Sheueling Chang Shantz Sun Microsystems Laboratories 16 Network Circle, UMPK16 160 Menlo Park, CA 94025 [email protected], [email protected], [email protected] [email protected], {nils.gura, hans.eberle, sheueling.chang}@sun.com Abstract numbers of even simpler, more constrained devices (sen- sors, home appliances, personal medical devices) get con- This paper introduces Sizzle, the first fully-implemented nected to the Internet. The term “embedded Internet” is end-to-end security architecture for highly constrained em- often used to refer to the phase in the Internet’s evolution bedded devices. According to popular perception, public- when it is invisibly and tightly woven into our daily lives. key cryptography is beyond the capabilities of such devices. Embedded devices with sensing and communication capa- We show that elliptic curve cryptography (ECC) not only bilities will enable the application of computing technolo- makes public-key cryptography feasible on these devices, it gies in settings where they are unusual today: habitat mon- allows one to create a complete secure web server stack itoring [26], medical emergency response [31], battlefield including SSL, HTTP and user application that runs effi- management and home automation. ciently within very tight resource constraints. Our small Many of these applications have security requirements. footprint HTTPS stack needs less than 4KB of RAM and For example, health information must only be made avail- interoperates with an ECC-enabled version of the Mozilla able to authorized personnel (authentication) and be pro- web browser. -

Fast Elliptic Curve Cryptography in Openssl
Fast Elliptic Curve Cryptography in OpenSSL Emilia K¨asper1;2 1 Google 2 Katholieke Universiteit Leuven, ESAT/COSIC [email protected] Abstract. We present a 64-bit optimized implementation of the NIST and SECG-standardized elliptic curve P-224. Our implementation is fully integrated into OpenSSL 1.0.1: full TLS handshakes using a 1024-bit RSA certificate and ephemeral Elliptic Curve Diffie-Hellman key ex- change over P-224 now run at twice the speed of standard OpenSSL, while atomic elliptic curve operations are up to 4 times faster. In ad- dition, our implementation is immune to timing attacks|most notably, we show how to do small table look-ups in a cache-timing resistant way, allowing us to use precomputation. To put our results in context, we also discuss the various security-performance trade-offs available to TLS applications. Keywords: elliptic curve cryptography, OpenSSL, side-channel attacks, fast implementations 1 Introduction 1.1 Introduction to TLS Transport Layer Security (TLS), the successor to Secure Socket Layer (SSL), is a protocol for securing network communications. In its most common use, it is the \S" (standing for \Secure") in HTTPS. Two of the most popular open- source cryptographic libraries implementing SSL and TLS are OpenSSL [19] and Mozilla Network Security Services (NSS) [17]: OpenSSL is found in, e.g., the Apache-SSL secure web server, while NSS is used by Mozilla Firefox and Chrome web browsers, amongst others. TLS provides authentication between connecting parties, as well as encryp- tion of all transmitted content. Thus, before any application data is transmit- ted, peers perform authentication and key exchange in a TLS handshake. -
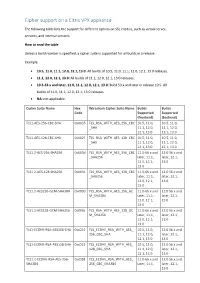
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -
![Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019](https://docslib.b-cdn.net/cover/5245/arxiv-1911-09312v2-cs-cr-12-dec-2019-485245.webp)
Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019
Revisiting and Evaluating Software Side-channel Vulnerabilities and Countermeasures in Cryptographic Applications Tianwei Zhang Jun Jiang Yinqian Zhang Nanyang Technological University Two Sigma Investments, LP The Ohio State University [email protected] [email protected] [email protected] Abstract—We systematize software side-channel attacks with three questions: (1) What are the common and distinct a focus on vulnerabilities and countermeasures in the cryp- features of various vulnerabilities? (2) What are common tographic implementations. Particularly, we survey past re- mitigation strategies? (3) What is the status quo of cryp- search literature to categorize vulnerable implementations, tographic applications regarding side-channel vulnerabili- and identify common strategies to eliminate them. We then ties? Past work only surveyed attack techniques and media evaluate popular libraries and applications, quantitatively [20–31], without offering unified summaries for software measuring and comparing the vulnerability severity, re- vulnerabilities and countermeasures that are more useful. sponse time and coverage. Based on these characterizations This paper provides a comprehensive characterization and evaluations, we offer some insights for side-channel of side-channel vulnerabilities and countermeasures, as researchers, cryptographic software developers and users. well as evaluations of cryptographic applications related We hope our study can inspire the side-channel research to side-channel attacks. We present this study in three di- community to discover new vulnerabilities, and more im- rections. (1) Systematization of literature: we characterize portantly, to fortify applications against them. the vulnerabilities from past work with regard to the im- plementations; for each vulnerability, we describe the root cause and the technique required to launch a successful 1. -

Secure Industrial Device Connectivity with Low-Overhead TLS
Secure Industrial Device Connectivity with Low-Overhead TLS Tuesday, October 3, 2017 1:10PM-2:10PM Chris Conlon - Engineering Manager, wolfSSL - B.S. from Montana State University (Bozeman, MT) - Software engineer at wolfSSL (7 years) Contact Info: - Email: [email protected] - Twitter: @c_conlon A. – B. – C. – D. – E. F. ● ● ● ○ ● ○ ● ○ ● Original Image Encrypted using ECB mode Modes other than ECB ● ○ ● ○ ● ● ● ● ○ ● ● ● ● ○ ● ○ ○ ○ ○ ● ○ ● ● ● ● ○ ● ● ○ By Original schema: A.J. Han Vinck, University of Duisburg-EssenSVG version: Flugaal - A.J. Han Vinck, Introduction to public key cryptography, p. 16, Public Domain, https://commons.wikimedia.org/w/index.php?curid=17063048 ● ○ ● ○ ■ ■ ■ ● ○ ■ ● ● ● ● ● ○ ● ● ● ● ● ● ● ○ ○ ○ ○ ● “Progressive” is a subjective term ● These slides talk about crypto algorithms that are: ○ New, modern ○ Becoming widely accepted ○ Have been integrated into SSL/TLS with cipher suites ● ChaCha20 ● Poly1305 ● Curve25519 ● Ed25519 Created by Daniel Bernstein a research professor at the University of Illinois, Chicago Chacha20-Poly1305 AEAD used in Google over HTTPS Ed25519 and ChaCha20-Poly1305 AEAD used in Apple’s HomeKit (iOS Security) ● Fast stream cipher ● Based from Salsa20 stream cipher using a different quarter-round process giving it more diffusion ● Can be used for AEAD encryption with Poly1305 ● Was published by Bernstein in 2008 Used by ● Google Chrome ● TinySSH ● Apple HomeKit ● wolfSSL ● To provide authenticity of messages (MAC) ● Extremely fast in comparison to others ● Introduced by a presentation given from Bernstein in 2002 ● Naming scheme from using polynomial-evaluation MAC (Message Authentication Code) over a prime field Z/(2^130 - 5) Used by ● Tor ● Google Chrome ● Apple iOS ● wolfSSL Generic Montgomery curve. Reference 5 Used by ● Tera Term ● GnuPG ● wolfSSL Generic Twisted Edwards Curve.