Overview of TLS V1.3 What’S New, What’S Removed and What’S Changed? About Me
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Fast Elliptic Curve Cryptography in Openssl
Fast Elliptic Curve Cryptography in OpenSSL Emilia K¨asper1;2 1 Google 2 Katholieke Universiteit Leuven, ESAT/COSIC [email protected] Abstract. We present a 64-bit optimized implementation of the NIST and SECG-standardized elliptic curve P-224. Our implementation is fully integrated into OpenSSL 1.0.1: full TLS handshakes using a 1024-bit RSA certificate and ephemeral Elliptic Curve Diffie-Hellman key ex- change over P-224 now run at twice the speed of standard OpenSSL, while atomic elliptic curve operations are up to 4 times faster. In ad- dition, our implementation is immune to timing attacks|most notably, we show how to do small table look-ups in a cache-timing resistant way, allowing us to use precomputation. To put our results in context, we also discuss the various security-performance trade-offs available to TLS applications. Keywords: elliptic curve cryptography, OpenSSL, side-channel attacks, fast implementations 1 Introduction 1.1 Introduction to TLS Transport Layer Security (TLS), the successor to Secure Socket Layer (SSL), is a protocol for securing network communications. In its most common use, it is the \S" (standing for \Secure") in HTTPS. Two of the most popular open- source cryptographic libraries implementing SSL and TLS are OpenSSL [19] and Mozilla Network Security Services (NSS) [17]: OpenSSL is found in, e.g., the Apache-SSL secure web server, while NSS is used by Mozilla Firefox and Chrome web browsers, amongst others. TLS provides authentication between connecting parties, as well as encryp- tion of all transmitted content. Thus, before any application data is transmit- ted, peers perform authentication and key exchange in a TLS handshake. -
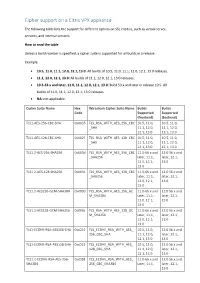
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Key Derivation Functions and Their GPU Implementation
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS Key derivation functions and their GPU implementation BACHELOR’S THESIS Ondrej Mosnáˇcek Brno, Spring 2015 This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 4.0 International License. https://creativecommons.org/licenses/by-nc-sa/4.0/ cbna ii Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Ondrej Mosnáˇcek Advisor: Ing. Milan Brož iii Acknowledgement I would like to thank my supervisor for his guidance and support, and also for his extensive contributions to the Cryptsetup open- source project. Next, I would like to thank my family for their support and pa- tience and also to my friends who were falling behind schedule just like me and thus helped me not to panic. Last but not least, access to computing and storage facilities owned by parties and projects contributing to the National Grid In- frastructure MetaCentrum, provided under the programme “Projects of Large Infrastructure for Research, Development, and Innovations” (LM2010005), is also greatly appreciated. v Abstract Key derivation functions are a key element of many cryptographic applications. Password-based key derivation functions are designed specifically to derive cryptographic keys from low-entropy sources (such as passwords or passphrases) and to counter brute-force and dictionary attacks. However, the most widely adopted standard for password-based key derivation, PBKDF2, as implemented in most applications, is highly susceptible to attacks using Graphics Process- ing Units (GPUs). -

The Double Ratchet Algorithm
The Double Ratchet Algorithm Trevor Perrin (editor) Moxie Marlinspike Revision 1, 2016-11-20 Contents 1. Introduction 3 2. Overview 3 2.1. KDF chains . 3 2.2. Symmetric-key ratchet . 5 2.3. Diffie-Hellman ratchet . 6 2.4. Double Ratchet . 13 2.6. Out-of-order messages . 17 3. Double Ratchet 18 3.1. External functions . 18 3.2. State variables . 19 3.3. Initialization . 19 3.4. Encrypting messages . 20 3.5. Decrypting messages . 20 4. Double Ratchet with header encryption 22 4.1. Overview . 22 4.2. External functions . 26 4.3. State variables . 26 4.4. Initialization . 26 4.5. Encrypting messages . 27 4.6. Decrypting messages . 28 5. Implementation considerations 29 5.1. Integration with X3DH . 29 5.2. Recommended cryptographic algorithms . 30 6. Security considerations 31 6.1. Secure deletion . 31 6.2. Recovery from compromise . 31 6.3. Cryptanalysis and ratchet public keys . 31 1 6.4. Deletion of skipped message keys . 32 6.5. Deferring new ratchet key generation . 32 6.6. Truncating authentication tags . 32 6.7. Implementation fingerprinting . 32 7. IPR 33 8. Acknowledgements 33 9. References 33 2 1. Introduction The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. Typically the parties will use some key agreement protocol (such as X3DH [1]) to agree on the shared secret key. Following this, the parties will use the Double Ratchet to send and receive encrypted messages. The parties derive new keys for every Double Ratchet message so that earlier keys cannot be calculated from later ones. -

TMF: Asymmetric Cryptography Security Layer V1.0
GlobalPlatform Device Technology TMF: Asymmetric Cryptography Security Layer Version 1.0 Public Release March 2017 Document Reference: GPD_SPE_122 Copyright 2013-2017 GlobalPlatform, Inc. All Rights Reserved. Recipients of this document are invited to submit, with their comments, notification of any relevant patents or other intellectual property rights (collectively, “IPR”) of which they may be aware which might be necessarily infringed by the implementation of the specification or other work product set forth in this document, and to provide supporting documentation. The technology provided or described herein is subject to updates, revisions, and extensions by GlobalPlatform. Use of this information is governed by the GlobalPlatform license agreement and any use inconsistent with that agreement is strictly prohibited. TMF: Asymmetric Cryptography Security Layer – Public Release v1.0 THIS SPECIFICATION OR OTHER WORK PRODUCT IS BEING OFFERED WITHOUT ANY WARRANTY WHATSOEVER, AND IN PARTICULAR, ANY WARRANTY OF NON-INFRINGEMENT IS EXPRESSLY DISCLAIMED. ANY IMPLEMENTATION OF THIS SPECIFICATION OR OTHER WORK PRODUCT SHALL BE MADE ENTIRELY AT THE IMPLEMENTER’S OWN RISK, AND NEITHER THE COMPANY, NOR ANY OF ITS MEMBERS OR SUBMITTERS, SHALL HAVE ANY LIABILITY WHATSOEVER TO ANY IMPLEMENTER OR THIRD PARTY FOR ANY DAMAGES OF ANY NATURE WHATSOEVER DIRECTLY OR INDIRECTLY ARISING FROM THE IMPLEMENTATION OF THIS SPECIFICATION OR OTHER WORK PRODUCT. Copyright 2013-2017 GlobalPlatform, Inc. All Rights Reserved. The technology provided or described herein is subject to updates, revisions, and extensions by GlobalPlatform. Use of this information is governed by the GlobalPlatform license agreement and any use inconsistent with that agreement is strictly prohibited. TMF: Asymmetric Cryptography Security Layer – Public Release v1.0 3 / 38 Contents 1 Introduction ........................................................................................................................... -

Modes of Operation for Compressed Sensing Based Encryption
Modes of Operation for Compressed Sensing based Encryption DISSERTATION zur Erlangung des Grades eines Doktors der Naturwissenschaften Dr. rer. nat. vorgelegt von Robin Fay, M. Sc. eingereicht bei der Naturwissenschaftlich-Technischen Fakultät der Universität Siegen Siegen 2017 1. Gutachter: Prof. Dr. rer. nat. Christoph Ruland 2. Gutachter: Prof. Dr.-Ing. Robert Fischer Tag der mündlichen Prüfung: 14.06.2017 To Verena ... s7+OZThMeDz6/wjq29ACJxERLMATbFdP2jZ7I6tpyLJDYa/yjCz6OYmBOK548fer 76 zoelzF8dNf /0k8H1KgTuMdPQg4ukQNmadG8vSnHGOVpXNEPWX7sBOTpn3CJzei d3hbFD/cOgYP4N5wFs8auDaUaycgRicPAWGowa18aYbTkbjNfswk4zPvRIF++EGH UbdBMdOWWQp4Gf44ZbMiMTlzzm6xLa5gRQ65eSUgnOoZLyt3qEY+DIZW5+N s B C A j GBttjsJtaS6XheB7mIOphMZUTj5lJM0CDMNVJiL39bq/TQLocvV/4inFUNhfa8ZM 7kazoz5tqjxCZocBi153PSsFae0BksynaA9ZIvPZM9N4++oAkBiFeZxRRdGLUQ6H e5A6HFyxsMELs8WN65SCDpQNd2FwdkzuiTZ4RkDCiJ1Dl9vXICuZVx05StDmYrgx S6mWzcg1aAsEm2k+Skhayux4a+qtl9sDJ5JcDLECo8acz+RL7/ ovnzuExZ3trm+O 6GN9c7mJBgCfEDkeror5Af4VHUtZbD4vALyqWCr42u4yxVjSj5fWIC9k4aJy6XzQ cRKGnsNrV0ZcGokFRO+IAcuWBIp4o3m3Amst8MyayKU+b94VgnrJAo02Fp0873wa hyJlqVF9fYyRX+couaIvi5dW/e15YX/xPd9hdTYd7S5mCmpoLo7cqYHCVuKWyOGw ZLu1ziPXKIYNEegeAP8iyeaJLnPInI1+z4447IsovnbgZxM3ktWO6k07IOH7zTy9 w+0UzbXdD/qdJI1rENyriAO986J4bUib+9sY/2/kLlL7nPy5Kxg3 Et0Fi3I9/+c/ IYOwNYaCotW+hPtHlw46dcDO1Jz0rMQMf1XCdn0kDQ61nHe5MGTz2uNtR3bty+7U CLgNPkv17hFPu/lX3YtlKvw04p6AZJTyktsSPjubqrE9PG00L5np1V3B/x+CCe2p niojR2m01TK17/oT1p0enFvDV8C351BRnjC86Z2OlbadnB9DnQSP3XH4JdQfbtN8 BXhOglfobjt5T9SHVZpBbzhDzeXAF1dmoZQ8JhdZ03EEDHjzYsXD1KUA6Xey03wU uwnrpTPzD99cdQM7vwCBdJnIPYaD2fT9NwAHICXdlp0pVy5NH20biAADH6GQr4Vc -

CSE 291-I: Applied Cryptography
CSE 291-I: Applied Cryptography Nadia Heninger UCSD Fall 2020 Lecture 7 Legal Notice The Zoom session for this class will be recorded and made available asynchronously on Canvas to registered students. Announcements 1. HW 3 is due next Tuesday. 2. HW 4 is online, due before class in 1.5 weeks, November 3. Last time: Hash functions This time: Hash-based MACs, authenticated encryption Constructing a MAC from a hash function Recall: Collision-resistant hash function: Unkeyed function • H : 0, 1 0, 1 n hard to find inputs mapping to same { }⇤ !{ } output. MAC: Keyed function Mac (m)=t,hardforadversaryto • k construct valid (m, t) pair. functor alone not- MAC : anyone can (m Hcm)) Hash forge , No secrets . Insecure. Vulnerable to length extension attacks for Merkle-Damgård functions. Secure for SHA3 sponge. Ok, but vulnerable to offline collision-finding attacks against H. Ok, but nobody uses. Secure, similar to HMAC. Candidate MAC constructions Mac(k, m)=H(k m) • || Mac(k, m)=H(m k) • || Mac(k, m)=H(k m k) • || || Mac(k , k , m)=H(k H(k m)) • 1 2 2|| 1|| Ok, but vulnerable to offline collision-finding attacks against H. Ok, but nobody uses. Secure, similar to HMAC. Candidate MAC constructions Mac(k, m)=H(k m) • || Insecure. Vulnerable to length extension attacks for Merkle-Damgård functions. Secure for SHA3 sponge. Mac(k, m)=H(m k) • || Mac(k, m)=H(k m k) • || || Mac(k , k , m)=H(k H(k m)) • 1 2 2|| 1|| Ok, but nobody uses. Secure, similar to HMAC. -

Dynamic Public Key Certificates with Forward Secrecy
electronics Article Dynamic Public Key Certificates with Forward Secrecy Hung-Yu Chien Department of Information Management, National Chi Nan University, Nantou 54561, Taiwan; [email protected] Abstract: Conventionally, public key certificates bind one subject with one static public key so that the subject can facilitate the services of the public key infrastructure (PKI). In PKI, certificates need to be renewed (or revoked) for several practical reasons, including certificate expiration, private key breaches, condition changes, and possible risk reduction. The certificate renewal process is very costly, especially for those environments where online authorities are not available or the connection is not reliable. A dynamic public key certificate (DPKC) facilitates the dynamic changeover of the current public–private key pairs without renewing the certificate authority (CA). This paper extends the previous study in several aspects: (1) we formally define the DPKC; (2) we formally define the security properties; (3) we propose another implementation of the Krawczyk–Rabin chameleon-hash- based DPKC; (4) we propose two variants of DPKC, using the Ateniese–Medeiros key-exposure-free chameleon hash; (5) we detail two application scenarios. Keywords: dynamic public key certificate; chameleon signature; certificate renewal; wireless sensor networks; perfect forward secrecy 1. Introduction Citation: Chien, H.-Y. Dynamic Certificates act as the critical tokens in conventional PKI systems. With the trust Public Key Certificates with Forward of the CA, a -

SSL Checklist for Pentesters
SSL Checklist for Pentesters Jerome Smith BSides MCR, 27th June 2014 # whoami whoami jerome • Pentester • Author/trainer – Hands-on technical – Web application, infrastructure, wireless security • Security projects – Log correlation – Dirty data – Incident response exercises • Sysadmin • MSc Computing Science (Dist) • www.exploresecurity.com | @exploresecurity Introduction • Broad review of SSL/TLS checks – Viewpoint of pentester – Pitfalls – Manually replicating what tools do (unless you told the client that SSL Labs would be testing them ) – Issues to consider reporting (but views are my own) • While SSL issues are generally low in priority, it’s nice to get them right! • I’m not a cryptographer: this is all best efforts SSLv2 • Flawed, e.g. no handshake protection → MITM downgrade • Modern browsers do not support SSLv2 anyway – Except for IE but it’s disabled by default from IE7 – That mitigates the risk these days – http://en.wikipedia.org/wiki/Transport_Layer_Security#W eb_browsers • OpenSSL 1.0.0+ doesn’t support it – Which means SSLscan won’t find it – General point: tools that dynamically link to an underlying SSL library in the OS can be limited by what that library supports SSLv2 • Same scan on different OpenSSL versions: SSLv2 • testssl.sh warns you – It can work with any installed OpenSSL version • OpenSSL <1.0.0 s_client -ssl2 switch – More on this later • Recompile OpenSSL – http://blog.opensecurityresearch.com/2013/05/fixing-sslv2-support- in-kali-linux.html • SSLyze 0.7+ is statically linked – Watch out for bug https://github.com/iSECPartners/sslyze/issues/73 -

Sicherheit in Kommunikationsnetzen (Network Security)
Sicherheit in Kommunikationsnetzen (Network Security) Transport Layer Security Dr.-Ing. Matthäus Wander Universität Duisburg-Essen Transport Layer Security (TLS) PrivateTLS data Web browser Web server ∙ Cryptographic protocol ∘ Provides security on top of reliable transport (TCP) ∘ Used to secure HTTP, SMTP, IMAP, XMPP and others ∙ Security goals ∘ Authentication of server and optionally client ∘ Data integrity (no manipulation of data) ∘ Confidentiality (encryption) Universität Duisburg-Essen Matthäus Wander 2 Verteilte Systeme History ∙ Predecessor: Secure Sockets Layer (SSL) ∘ Developed by Netscape for HTTPS (= HTTP + SSL) ∙ 1994: SSL 2.0 ∘ Insecure, major security weaknesses ∙ 1995: SSL 3.0 ∘ Insecure, deprecated since 2015 (RFC 7568) ∙ 1999: TLS 1.0, minor improvements to SSL 3.0 ∘ Standardization and further development by IETF Universität Duisburg-Essen Matthäus Wander 3 Verteilte Systeme History ∙ 2003: TLS Extensions ∘ New features or security mechanisms (e.g. Encrypt-then-MAC, RFC 7366) ∙ 2006: TLS 1.1 ∘ Security improvements ∙ 2008: TLS 1.2 Presented in this lecture ∘ Added new or replaced old cryptographic algorithms ∙ TLS 1.3 is work in progress as of 2017 ∘ Outlook: new handshake and other major changes Universität Duisburg-Essen Matthäus Wander 4 Verteilte Systeme Protocol Overview Application Layer (e.g. HTTP) Handshake Change Cipher Application Alert Protocol Protocol Spec Protocol Data Protocol Record Protocol Transport Layer (e.g. TCP) ∙ TLS consists of two layers: ∘ Handshake Protocol and other protocols ∘ Record Protocol -

Analysis of DTLS Implementations Using Protocol State Fuzzing
Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Brostean and Bengt Jonsson, Uppsala University; Robert Merget, Ruhr-University Bochum; Joeri de Ruiter, SIDN Labs; Konstantinos Sagonas, Uppsala University; Juraj Somorovsky, Paderborn University https://www.usenix.org/conference/usenixsecurity20/presentation/fiterau-brostean This paper is included in the Proceedings of the 29th USENIX Security Symposium. August 12–14, 2020 978-1-939133-17-5 Open access to the Proceedings of the 29th USENIX Security Symposium is sponsored by USENIX. Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Bro¸stean˘ Bengt Jonsson Robert Merget Joeri de Ruiter Uppsala University Uppsala University Ruhr University Bochum SIDN Labs Konstantinos Sagonas Juraj Somorovsky Uppsala University Paderborn University Abstract reach 11.6 billion by 2021 [26]. This will constitute half of all devices connected to the Internet, with the percentage set to Recent years have witnessed an increasing number of proto- grow in subsequent years. Such trends also increase the need cols relying on UDP. Compared to TCP, UDP offers perfor- to ensure that software designed for these devices is properly mance advantages such as simplicity and lower latency. This scrutinized, particularly with regards to its security. has motivated its adoption in Voice over IP, tunneling techno- DTLS is also used as one of the two security protocols in logies, IoT, and novel Web protocols. To protect sensitive data WebRTC, a framework enabling real-time communication. exchange in these scenarios, the DTLS protocol has been de- WebRTC can be used, for example, to implement video con- veloped as a cryptographic variation of TLS.