Weaknesses in Diffie-Hellman Key Exchange Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Horizontal PDF Slides
1 2 The first 10 years of Curve25519 Abstract: “This paper explains the design and implementation Daniel J. Bernstein of a high-security elliptic-curve- University of Illinois at Chicago & Diffie-Hellman function Technische Universiteit Eindhoven achieving record-setting speeds: e.g., 832457 Pentium III cycles 2005.05.19: Seminar talk; (with several side benefits: design+software close to done. free key compression, free key validation, and state-of-the-art 2005.09.15: Software online. timing-attack protection), 2005.09.20: Invited talk at ECC. more than twice as fast as other authors’ results at the same 2005.11.15: Paper online; conjectured security level (with submitted to PKC 2006. or without the side benefits).” 1 2 3 The first 10 years of Curve25519 Abstract: “This paper explains Elliptic-curve computations the design and implementation Daniel J. Bernstein of a high-security elliptic-curve- University of Illinois at Chicago & Diffie-Hellman function Technische Universiteit Eindhoven achieving record-setting speeds: e.g., 832457 Pentium III cycles 2005.05.19: Seminar talk; (with several side benefits: design+software close to done. free key compression, free key validation, and state-of-the-art 2005.09.15: Software online. timing-attack protection), 2005.09.20: Invited talk at ECC. more than twice as fast as other authors’ results at the same 2005.11.15: Paper online; conjectured security level (with submitted to PKC 2006. or without the side benefits).” 1 2 3 The first 10 years of Curve25519 Abstract: “This paper explains Elliptic-curve computations the design and implementation Daniel J. Bernstein of a high-security elliptic-curve- University of Illinois at Chicago & Diffie-Hellman function Technische Universiteit Eindhoven achieving record-setting speeds: e.g., 832457 Pentium III cycles 2005.05.19: Seminar talk; (with several side benefits: design+software close to done. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Fast Elliptic Curve Cryptography in Openssl
Fast Elliptic Curve Cryptography in OpenSSL Emilia K¨asper1;2 1 Google 2 Katholieke Universiteit Leuven, ESAT/COSIC [email protected] Abstract. We present a 64-bit optimized implementation of the NIST and SECG-standardized elliptic curve P-224. Our implementation is fully integrated into OpenSSL 1.0.1: full TLS handshakes using a 1024-bit RSA certificate and ephemeral Elliptic Curve Diffie-Hellman key ex- change over P-224 now run at twice the speed of standard OpenSSL, while atomic elliptic curve operations are up to 4 times faster. In ad- dition, our implementation is immune to timing attacks|most notably, we show how to do small table look-ups in a cache-timing resistant way, allowing us to use precomputation. To put our results in context, we also discuss the various security-performance trade-offs available to TLS applications. Keywords: elliptic curve cryptography, OpenSSL, side-channel attacks, fast implementations 1 Introduction 1.1 Introduction to TLS Transport Layer Security (TLS), the successor to Secure Socket Layer (SSL), is a protocol for securing network communications. In its most common use, it is the \S" (standing for \Secure") in HTTPS. Two of the most popular open- source cryptographic libraries implementing SSL and TLS are OpenSSL [19] and Mozilla Network Security Services (NSS) [17]: OpenSSL is found in, e.g., the Apache-SSL secure web server, while NSS is used by Mozilla Firefox and Chrome web browsers, amongst others. TLS provides authentication between connecting parties, as well as encryp- tion of all transmitted content. Thus, before any application data is transmit- ted, peers perform authentication and key exchange in a TLS handshake. -
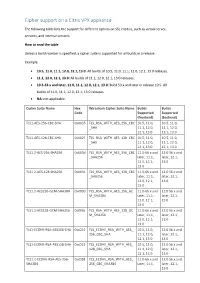
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Crypto Projects That Might Not Suck
Crypto Projects that Might not Suck Steve Weis PrivateCore ! http://bit.ly/CryptoMightNotSuck #CryptoMightNotSuck Today’s Talk ! • Goal was to learn about new projects and who is working on them. ! • Projects marked with ☢ are experimental or are relatively new. ! • Tried to cite project owners or main contributors; sorry for omissions. ! Methodology • Unscientific survey of projects from Twitter and mailing lists ! • Excluded closed source projects & crypto currencies ! • Stats: • 1300 pageviews on submission form • 110 total nominations • 89 unique nominations • 32 mentioned today The People’s Choice • Open Whisper Systems: https://whispersystems.org/ • Moxie Marlinspike (@moxie) & open source community • Acquired by Twitter 2011 ! • TextSecure: Encrypt your texts and chat messages for Android • OTP-like forward security & Axolotl key racheting by @trevp__ • https://github.com/whispersystems/textsecure/ • RedPhone: Secure calling app for Android • ZRTP for key agreement, SRTP for call encryption • https://github.com/whispersystems/redphone/ Honorable Mention • ☢ Networking and Crypto Library (NaCl): http://nacl.cr.yp.to/ • Easy to use, high speed XSalsa20, Poly1305, Curve25519, etc • No dynamic memory allocation or data-dependent branches • DJ Bernstein (@hashbreaker), Tanja Lange (@hyperelliptic), Peter Schwabe (@cryptojedi) ! • ☢ libsodium: https://github.com/jedisct1/libsodium • Portable, cross-compatible NaCL • OpenDNS & Frank Denis (@jedisct1) The Old Standbys • Gnu Privacy Guard (GPG): https://www.gnupg.org/ • OpenSSH: http://www.openssh.com/ -

NUMS Elliptic Curves and Their Efficient Implementation
Fourℚ-based cryptography for high-performance and low-power applications Real World Cryptography Conference 2017 January 4-6, New York, USA Patrick Longa Microsoft Research Next-generation elliptic curves New IETF Standards • The Crypto Forum Research Group (CFRG) selected two elliptic curves: Bernstein’s Curve25519 and Hamburg’s Ed448-Goldilocks • RFC 7748: “Elliptic Curves for Security” (published on January 2016) • Curve details; generation • DH key exchange for both curves • Ongoing work: signature scheme • draft-irtf-cfrg-eddsa-08, “Edwards-curve Digital Signature Algorithm (EdDSA)” 1/23 Next-generation elliptic curves Farrel-Moriarity-Melkinov-Paterson [NIST ECC Workshop 2015]: “… the real motivation for work in CFRG is the better performance and side- channel resistance of new curves developed by academic cryptographers over the last decade.” Plus some additional requirements such as: • Rigidity in curve generation process. • Support for existing cryptographic algorithms. 2/23 Next-generation elliptic curves Farrel-Moriarity-Melkinov-Paterson [NIST ECC Workshop 2015]: “… the real motivation for work in CFRG is the better performance and side- channel resistance of new curves developed by academic cryptographers over the last decade.” Plus some additional requirements such as: • Rigidity in curve generation process. • Support for existing cryptographic algorithms. 2/23 State-of-the-art ECC: Fourℚ [Costello-L, ASIACRYPT 2015] • CM endomorphism [GLV01] and Frobenius (ℚ-curve) endomorphism [GLS09, Smi16, GI13] • Edwards form [Edw07] using efficient Edwards ℚ coordinates [BBJ+08, HCW+08] Four • Arithmetic over the Mersenne prime 푝 = 2127 −1 Features: • Support for secure implementations and top performance. • Uniqueness: only curve at the 128-bit security level with properties above. -

Simple High-Level Code for Cryptographic Arithmetic - with Proofs, Without Compromises
Simple High-Level Code for Cryptographic Arithmetic - With Proofs, Without Compromises The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation Erbsen, Andres et al. “Simple High-Level Code for Cryptographic Arithmetic - With Proofs, Without Compromises.” Proceedings - IEEE Symposium on Security and Privacy, May-2019 (May 2019) © 2019 The Author(s) As Published 10.1109/SP.2019.00005 Publisher Institute of Electrical and Electronics Engineers (IEEE) Version Author's final manuscript Citable link https://hdl.handle.net/1721.1/130000 Terms of Use Creative Commons Attribution-Noncommercial-Share Alike Detailed Terms http://creativecommons.org/licenses/by-nc-sa/4.0/ Simple High-Level Code For Cryptographic Arithmetic – With Proofs, Without Compromises Andres Erbsen Jade Philipoom Jason Gross Robert Sloan Adam Chlipala MIT CSAIL, Cambridge, MA, USA fandreser, jadep, [email protected], [email protected], [email protected] Abstract—We introduce a new approach for implementing where X25519 was the only arithmetic-based crypto primitive cryptographic arithmetic in short high-level code with machine- we need, now would be the time to declare victory and go checked proofs of functional correctness. We further demonstrate home. Yet most of the Internet still uses P-256, and the that simple partial evaluation is sufficient to transform such initial code into the fastest-known C code, breaking the decades- current proposals for post-quantum cryptosystems are far from old pattern that the only fast implementations are those whose Curve25519’s combination of performance and simplicity. instruction-level steps were written out by hand. -

The Double Ratchet Algorithm
The Double Ratchet Algorithm Trevor Perrin (editor) Moxie Marlinspike Revision 1, 2016-11-20 Contents 1. Introduction 3 2. Overview 3 2.1. KDF chains . 3 2.2. Symmetric-key ratchet . 5 2.3. Diffie-Hellman ratchet . 6 2.4. Double Ratchet . 13 2.6. Out-of-order messages . 17 3. Double Ratchet 18 3.1. External functions . 18 3.2. State variables . 19 3.3. Initialization . 19 3.4. Encrypting messages . 20 3.5. Decrypting messages . 20 4. Double Ratchet with header encryption 22 4.1. Overview . 22 4.2. External functions . 26 4.3. State variables . 26 4.4. Initialization . 26 4.5. Encrypting messages . 27 4.6. Decrypting messages . 28 5. Implementation considerations 29 5.1. Integration with X3DH . 29 5.2. Recommended cryptographic algorithms . 30 6. Security considerations 31 6.1. Secure deletion . 31 6.2. Recovery from compromise . 31 6.3. Cryptanalysis and ratchet public keys . 31 1 6.4. Deletion of skipped message keys . 32 6.5. Deferring new ratchet key generation . 32 6.6. Truncating authentication tags . 32 6.7. Implementation fingerprinting . 32 7. IPR 33 8. Acknowledgements 33 9. References 33 2 1. Introduction The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. Typically the parties will use some key agreement protocol (such as X3DH [1]) to agree on the shared secret key. Following this, the parties will use the Double Ratchet to send and receive encrypted messages. The parties derive new keys for every Double Ratchet message so that earlier keys cannot be calculated from later ones. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

How Secure Is Textsecure?
How Secure is TextSecure? Tilman Frosch∗y, Christian Mainkay, Christoph Badery, Florian Bergsmay,Jorg¨ Schwenky, Thorsten Holzy ∗G DATA Advanced Analytics GmbH firstname.lastname @gdata.de f g yHorst Gortz¨ Institute for IT-Security Ruhr University Bochum firstname.lastname @rub.de f g Abstract—Instant Messaging has gained popularity by users without providing any kind of authentication. Today, many for both private and business communication as low-cost clients implement only client-to-server encryption via TLS, short message replacement on mobile devices. However, until although security mechanisms like Off the Record (OTR) recently, most mobile messaging apps did not protect confi- communication [3] or SCIMP [4] providing end-to-end con- dentiality or integrity of the messages. fidentiality and integrity are available. Press releases about mass surveillance performed by intelli- With the advent of smartphones, low-cost short-message gence services such as NSA and GCHQ motivated many people alternatives that use the data channel to communicate, to use alternative messaging solutions to preserve the security gained popularity. However, in the context of mobile ap- and privacy of their communication on the Internet. Initially plications, the assumption of classical instant messaging, fueled by Facebook’s acquisition of the hugely popular mobile for instance, that both parties are online at the time the messaging app WHATSAPP, alternatives claiming to provide conversation takes place, is no longer necessarily valid. secure communication experienced a significant increase of new Instead, the mobile context requires solutions that allow for users. asynchronous communication, where a party may be offline A messaging app that claims to provide secure instant for a prolonged time. -

Analysis and Implementation of the Messaging Layer Security Protocol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AMS Tesi di Laurea Alma Mater Studiorum · Universita` di Bologna CAMPUS DI CESENA Dipartimento di Informatica - Scienza e Ingegneria Corso di Laurea Magistrale in Ingegneria e Scienze Informatiche Analysis and Implementation of the Messaging Layer Security Protocol Tesi in Sicurezza delle Reti Relatore: Presentata da: Gabriele D'Angelo Nicola Giancecchi Anno Accademico 2018/2019 Parole chiave Network Security Messaging MLS Protocol Ratchet Trees \Oh me, oh vita! Domande come queste mi perseguitano. Infiniti cortei d'infedeli, citt`agremite di stolti, che v'`edi nuovo in tutto questo, oh me, oh vita! Risposta: Che tu sei qui, che la vita esiste e l’identit`a. Che il potente spettacolo continua, e che tu puoi contribuire con un verso." - Walt Whitman Alla mia famiglia. Introduzione L'utilizzo di servizi di messaggistica su smartphone `eincrementato in maniera considerevole negli ultimi anni, complice la sempre maggiore disponi- bilit`adi dispositivi mobile e l'evoluzione delle tecnologie di comunicazione via Internet, fattori che hanno di fatto soppiantato l'uso dei classici SMS. Tale incremento ha riguardato anche l'utilizzo in ambito business, un contesto dove `epi`ufrequente lo scambio di informazioni confidenziali e quindi la necessit`adi proteggere la comunicazione tra due o pi`upersone. Ci`onon solo per un punto di vista di sicurezza, ma anche di privacy personale. I maggiori player mondiali hanno risposto implementando misure di sicurezza all'interno dei propri servizi, quali ad esempio la crittografia end-to-end e regole sempre pi`ustringenti sul trattamento dei dati personali. -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority.