Macos Filename Homoglyphs Revisited Vx-Underground Collection // Xpn
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Unicode Cookbook for Linguists: Managing Writing Systems Using Orthography Profiles
Zurich Open Repository and Archive University of Zurich Main Library Strickhofstrasse 39 CH-8057 Zurich www.zora.uzh.ch Year: 2017 The Unicode Cookbook for Linguists: Managing writing systems using orthography profiles Moran, Steven ; Cysouw, Michael DOI: https://doi.org/10.5281/zenodo.290662 Posted at the Zurich Open Repository and Archive, University of Zurich ZORA URL: https://doi.org/10.5167/uzh-135400 Monograph The following work is licensed under a Creative Commons: Attribution 4.0 International (CC BY 4.0) License. Originally published at: Moran, Steven; Cysouw, Michael (2017). The Unicode Cookbook for Linguists: Managing writing systems using orthography profiles. CERN Data Centre: Zenodo. DOI: https://doi.org/10.5281/zenodo.290662 The Unicode Cookbook for Linguists Managing writing systems using orthography profiles Steven Moran & Michael Cysouw Change dedication in localmetadata.tex Preface This text is meant as a practical guide for linguists, and programmers, whowork with data in multilingual computational environments. We introduce the basic concepts needed to understand how writing systems and character encodings function, and how they work together. The intersection of the Unicode Standard and the International Phonetic Al- phabet is often not met without frustration by users. Nevertheless, thetwo standards have provided language researchers with a consistent computational architecture needed to process, publish and analyze data from many different languages. We bring to light common, but not always transparent, pitfalls that researchers face when working with Unicode and IPA. Our research uses quantitative methods to compare languages and uncover and clarify their phylogenetic relations. However, the majority of lexical data available from the world’s languages is in author- or document-specific orthogra- phies. -

Suitcase Fusion 8 Getting Started
Copyright © 2014–2018 Celartem, Inc., doing business as Extensis. This document and the software described in it are copyrighted with all rights reserved. This document or the software described may not be copied, in whole or part, without the written consent of Extensis, except in the normal use of the software, or to make a backup copy of the software. This exception does not allow copies to be made for others. Licensed under U.S. patents issued and pending. Celartem, Extensis, LizardTech, MrSID, NetPublish, Portfolio, Portfolio Flow, Portfolio NetPublish, Portfolio Server, Suitcase Fusion, Type Server, TurboSync, TeamSync, and Universal Type Server are registered trademarks of Celartem, Inc. The Celartem logo, Extensis logos, LizardTech logos, Extensis Portfolio, Font Sense, Font Vault, FontLink, QuickComp, QuickFind, QuickMatch, QuickType, Suitcase, Suitcase Attaché, Universal Type, Universal Type Client, and Universal Type Core are trademarks of Celartem, Inc. Adobe, Acrobat, After Effects, Creative Cloud, Creative Suite, Illustrator, InCopy, InDesign, Photoshop, PostScript, Typekit and XMP are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apache Tika, Apache Tomcat and Tomcat are trademarks of the Apache Software Foundation. Apple, Bonjour, the Bonjour logo, Finder, iBooks, iPhone, Mac, the Mac logo, Mac OS, OS X, Safari, and TrueType are trademarks of Apple Inc., registered in the U.S. and other countries. macOS is a trademark of Apple Inc. App Store is a service mark of Apple Inc. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license. Elasticsearch is a trademark of Elasticsearch BV, registered in the U.S. -

13A04806 LINUX PROGRAMMING and SCRIPTING UNIT 4 TCL/ TK SCRIPTING:Tcl Fundamentals, String and Pattern Matching, Tcl Data Struct
13A04806 LINUX PROGRAMMING AND SCRIPTING UNIT 4 TCL/ TK SCRIPTING:Tcl Fundamentals, String and Pattern Matching, Tcl Data Structures ,Control Flow Commands, Procedures and Scope , Evel, Working With UNIX, Reflection and Debugging, Script Libraries, Tk Fundamentals ,Tk by Examples, The Pack Geometry Manager, Binding Commands to X Events, Buttons and Menus, Simple Tk Widgets, Entry and Listbox Widgets Focus, Grabs and Dialogs 13A04806 LINUX PROGRAMMING AND SCRIPTING Tcl - Overview Tcl is shortened form of Tool Command Language. John Ousterhout of the University of California, Berkeley, designed it. It is a combination of a scripting language and its own interpreter that gets embedded to the application, we develop with it. Tcl was developed initially for Unix. It was then ported to Windows, DOS, OS/2, and Mac OSX. Tcl is much similar to other unix shell languages like Bourne Shell (Sh), the C Shell (csh), the Korn Shell (sh), and Perl. It aims at providing ability for programs to interact with other programs and also for acting as an embeddable interpreter. Even though, the original aim was to enable programs to interact, you can find full-fledged applications written in Tcl/Tk. Features of Tcl The features of Tcl are as follows − ∑ Reduced development time. ∑ Powerful and simple user interface kit with integration of TK. ∑ Write once, run anywhere. It runs on Windows, Mac OS X, and almost on every Unix platform. ∑ Quite easy to get started for experienced programmers; since, the language is so simple that they can learn Tcl in a few hours or days. ∑ You can easily extend existing applications with Tcl. -

Washington Apple Pi Journal, July-August 2008
July/August 2008 Volume 30, No. 4 Washington Apple Pi Cl) ..c +.l M -c m o r a A Journal for Macintosh Computer Users Day Sund:1y ER DISCUSSION lil!i;iiiiif;tifij;pfl~Q~o°4./i_~r{,J;'/i;;J~ Ll / - ·· . -±2-0449 luz bevern. ge or s· Topic A specinc week and day of the \~' eek I 2nd ~ J l Wednesday-- -------- Washington Apple Pi Meetings July 2008 General Meeting July 2 6, 9:30 a.m., Luther Jackson Middle School Little Apps I Love! This month's meeting is going to be chock-full of discoveries with several presenters sharing some of their favorite little apps (applications) or widgets with you. Also featured: genealogy on the Mac. Come, watch and learn! There are tens of thousands of really cool third-party programs available. Learn how to find them yourself, d iscover new ways to do neat things, enhance your computing productivity, or express your creativity in new ways.There is no doubt the Mac can help you be productive but it can be fun too! After exploring little apps, Dick Nugent, a long time Pi member, will guide us through doing family genealogy on the Mac. He will continue in the Genealogy SIG with a demonstration of the popular Mac genealogy software, Reunion. As we have for thirty years, we will start with our legendary Q & A session, followed by Pi business. Kitty's Coffee Break will reenergize everyone for the main presentations. We will close with a short Town Hall meeting where your questions or comments for the leadership will be taken.Then comes lunch! The afternoon is reserved for three Special Interest Group meetings.The Beginners SIG, the ilife SIG and the rejuvenated Genealogy SIG provide opportunity for more focused attention, so bring your questions and your projects to share with the others. -

A. Introduction
Date: Oct. 30, 2011 To: Unicode Technical Committee Subject: Emoji Variation Sequences From: Peter Edberg, with input from Asmus Freytag, Ned Holbrook, Yasuo Kida, Mark Davis, Kat Momoi, Murray Sargent, and Ken Lunde (though I don’t claim that they agree with this document or that it accurately represents their input). A. Introduction As part of encoding the emoji core set for Unicode 6.0, 114 emoji from that core set were mapped to (unified with) existing characters or character sequences from Unicode 5.2 or earlier. The associated document “Unified Emoji Reference” provides more detail on the representation across various systems of these 114 emoji. When these Unicode characters result from text created as emoji, such as e-mail or text messages generated on a Japanese cell phone or via an emoji input palette, users may expect them to be displayed in other contexts using an emoji style similar to the one used when they were created. Such an emoji style usually involves color display, and may sometimes involve other stylistic differences and/or animation. However, since these Unicode characters were in Unicode prior to the emoji additions — with some dating back to Unicode 1.1 — many systems have already supported such characters using a more traditional black-and-white glyph, and users who created documents with characters displayed this way expect them to remain displayed this way (even when interchanged display). For example: For U+2764 HEAVY BLACK HEART (in the Dingbats block) the Unicode charts (and Dingbats fonts) use the first of these glyphs while the other glyphs are used by Japanese cell phones and emoji fonts: These characters may be sent as part of SMS text messages and e-mail subjects where font information is not available, and a given character may be used with both an emoji style and a non-emoji style in the same document. -

The Apple Personal Computer for Beginners 1982.Pdf
The Apple Personal Computer for Beginners The Apple Personal Computer for Beginners Seamus Dunn and Valerie Morgan (New University of Ulster) Englewood Cliffs, New Jersey London New Delhi Singapore Sydney Tokyo Toronto Wellington / Library of Congress Cataloging in Publication Data Dunn, Seamus, 1939- The Apple personal computer for beginners. Bibliography: p. Includes index. 1. Apple computer. I. Morgan, Valerie, 1943- 11. Title. QA 76.8.A66D86 001.64 82-618 ISBN 0-13-039149-2 AACR2 ISBN 0-13-039131-X {pbk.} British Library Cataloging in Publication Data Dunn, Seamus The Apple personal computer for beginners. 1. Apple computer I. Title II. Morgan, Valerie 001.64'04 QA 76.8.A/ ISBN 0-13-039149-2 ISBN 0-13-039131-X Pbk c 1982 by Prentice-Hall International, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior permis sion of Prentice-Hall International Inc. For permission within the United States contact Prentice-Hall, Inc., Englewood Cliffs, N.J. 07632. PRENTICE-HALL INTERNATIONAL, INC., London PRENTICE-HALL OF AUSTRALIA PTY. LTD., Sydney PRENTICE-HALL CANADA, INC., Toronto PRENTICE-HALL OF INDIA PRIVATE LIMITED, New Delhi PRENTICE-HALL OF JAPAN, INC., Tokyo PRENTICE-HALL OF SOUTHEAST ASIA PTE., LTD., Singapore PRENTICE-HALL, INC., Englewood Cliffs, New Jersey WHITEHALL BOOKS LIMITED, Wellington, New Zealand 109876543 Printed in the United States of America This book -

Apple Symbol Fonts: a Quick Survey
Apple Symbol Fonts: A Quick Survey Karl Pentzlin ‐ 2011‐07‐15 In WG2 N4085 "Further proposed additions to ISO/IEC 10646 and comments to other proposals" (2011‐ 05‐25), the German NB had requested re WG2 N4022 "Proposal to add Wingdings and Webdings Symbols" besides other points: "Also, in doing this work, other fonts widespread on the computers of leading manufacturers (e.g. Apple) shall be included, thus avoiding the impression that Unicode or SC2/WG2 favor a single manufacturer." In this quick survey, the symbol fonts regularly delivered with computers manufactured by Apple are addressed. These are two fonts: 1. "Apple Symbols" The version examined here was retrieved 2010‐06‐06 from a MacBook. The original file contained no mapping to code points for any glyphs, but glyph names like "uni2440" indicated the intended Unicode points for the larger part of the glyphs. After discarding a large sequence of empty glyphs assigned by glyph names to PUA code points above U+10FC00, the font contains 4103 glyphs. These were remapped to the PUA code points U+E000...U+F006. The code charts below uses these code points (as said, these were not assigned in the original font). The listed character names are the original glyph names from the font, conversed to uppercase, and dots replaced by hyphens. All following characters were not included in the charts: – Characters which are mapped to an Unicode code point by the glyph name. – Characters contained in a sequence which obviously maps to a Unicode block. – Characters which are mirror images of an existing Unicode character which is bidi mirrored, and which are mapped to this character by a glyph name of the form "uniXXXX.mirror". -

Complete Issue 25:0 As One
TEX Users Group PREPRINTS for the 2004 Annual Meeting TEX Users Group Board of Directors These preprints for the 2004 annual meeting are Donald Knuth, Grand Wizard of TEX-arcana † ∗ published by the TEX Users Group. Karl Berry, President Kaja Christiansen∗, Vice President Periodical-class postage paid at Portland, OR, and ∗ Sam Rhoads , Treasurer additional mailing offices. Postmaster: Send address ∗ Susan DeMeritt , Secretary changes to T X Users Group, 1466 NW Naito E Barbara Beeton Parkway Suite 3141, Portland, OR 97209-2820, Jim Hefferon U.S.A. Ross Moore Memberships Arthur Ogawa 2004 dues for individual members are as follows: Gerree Pecht Ordinary members: $75. Steve Peter Students/Seniors: $45. Cheryl Ponchin The discounted rate of $45 is also available to Michael Sofka citizens of countries with modest economies, as Philip Taylor detailed on our web site. Raymond Goucher, Founding Executive Director † Membership in the TEX Users Group is for the Hermann Zapf, Wizard of Fonts † calendar year, and includes all issues of TUGboat ∗member of executive committee for the year in which membership begins or is †honorary renewed, as well as software distributions and other benefits. Individual membership is open only to Addresses Electronic Mail named individuals, and carries with it such rights General correspondence, (Internet) and responsibilities as voting in TUG elections. For payments, etc. General correspondence, membership information, visit the TUG web site: TEX Users Group membership, subscriptions: http://www.tug.org. P. O. Box 2311 [email protected] Portland, OR 97208-2311 Institutional Membership U.S.A. Submissions to TUGboat, Institutional Membership is a means of showing Delivery services, letters to the Editor: continuing interest in and support for both TEX parcels, visitors [email protected] and the TEX Users Group. -

MAPS BIBLIOGRAPHY Previous
publications keywords authors titles introduction MAPS BIBLIOGRAPHY previous Volumes 1–46, 1988–2015 next exit Publications publications Maps 1 1988 Maps 27 2002 Maps 2 1989 Maps 28 2002 keywords Maps 3 1989 Maps 29 2003 Maps 4 1990 Maps 30 2004 Maps 5 1990 Maps 31 2004 authors Maps 6 1991 Maps 32 2005 Maps 7 1991 Maps 33 2005 Maps 8 1992 Maps 34 2006 titles Maps 9 1992 Maps 35 2007 Maps 10 1993 Maps 36 2007 Maps 11 1993 Maps 37 2008 introduction Maps 12 1994 Maps 38 2009 Maps 13 1994 Maps 39 2009 Maps 14 1995 Maps 40 2010 Maps 15 1995 Maps 41 2010 Maps 15a 1995 Maps 42 2011 Maps 16 1996 Maps 43 2011 Maps 17 1996 Maps 44 2013 Maps 18 1997 Maps 45 2012 Maps 19 1997 Maps 46 2015 Maps 20 1998 Maps 21 1998 Maps 22 1999 Maps 23 1999 previous Maps 24 2000 Maps 25 2000 Maps 26 2001 next publications keywords authors titles help previous next search exit exit Maps 1 1988 publications Verslag TEX Listserver keywords TEXHaX T X publications information E authors titles introduction previous next publications keywords authors titles help previous next search exit exit Verslag TEX report members meeting Opening en Mededelingen; Introductie deelnemers; Brainstorming TEX aandachtsgebieden; Instellen werkgroe- pen voor de aandachtsgebieden; Formele zaken; Rondvraag; Sluiting. Gerard van Nes Maps 1 1988 p 1-10 126 kB publications keywords authors titles help previous next search exit view Listserver listserver TEX-NL Overzicht gebruikers listserver. Maps 1 1988 p 13-14 55 kB publications keywords authors titles help previous next search exit view TEXHaX TEXHaX mailing list listserver Information on subscribing to TEXHaX. -

The Unicode Cookbook for Linguists
The Unicode Cookbook for Linguists Managing writing systems using orthography profiles Steven Moran Michael Cysouw language Translation and Multilingual Natural science press Language Processing 10 Translation and Multilingual Natural Language Processing Editors: Oliver Czulo (Universität Leipzig), Silvia Hansen-Schirra (Johannes Gutenberg-Universität Mainz), Reinhard Rapp (Johannes Gutenberg-Universität Mainz) In this series: 1. Fantinuoli, Claudio & Federico Zanettin (eds.). New directions in corpus-based translation studies. 2. Hansen-Schirra, Silvia & Sambor Grucza (eds.). Eyetracking and Applied Linguistics. 3. Neumann, Stella, Oliver Čulo & Silvia Hansen-Schirra (eds.). Annotation, exploitation and evaluation of parallel corpora: TC3 I. 4. Czulo, Oliver & Silvia Hansen-Schirra (eds.). Crossroads between Contrastive Linguistics, Translation Studies and Machine Translation: TC3 II. 5. Rehm, Georg, Felix Sasaki, Daniel Stein & Andreas Witt (eds.). Language technologies for a multilingual Europe: TC3 III. 6. Menzel, Katrin, Ekaterina Lapshinova-Koltunski & Kerstin Anna Kunz (eds.). New perspectives on cohesion and coherence: Implications for translation. 7. Hansen-Schirra, Silvia, Oliver Czulo & Sascha Hofmann (eds). Empirical modelling of translation and interpreting. 8. Svoboda, Tomáš, Łucja Biel & Krzysztof Łoboda (eds.). Quality aspects in institutional translation. 9. Fox, Wendy. Can integrated titles improve the viewing experience? Investigating the impact of subtitling on the reception and enjoyment of film using eye tracking and questionnaire data. 10. Moran, Steven & Michael Cysouw. The Unicode cookbook for linguists: Managing writing systems using orthography profiles ISSN: 2364-8899 The Unicode Cookbook for Linguists Managing writing systems using orthography profiles Steven Moran Michael Cysouw language science press Steven Moran & Michael Cysouw. 2018. The Unicode Cookbook for Linguists: Managing writing systems using orthography profiles (Translation and Multilingual Natural Language Processing 10). -
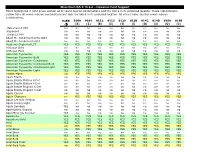
Macintosh OS X 10.6.4 - Hawaiian Font Support Fonts Highlighted in Light Green Contain All of Vowel-Macron Combinations and the ‘Okina in Its Preferred Location
Macintosh OS X 10.6.4 - Hawaiian Font Support Fonts highlighted in light green contain all of vowel-macron combinations and the ‘okina in its preferred location. Those highlighted in yellow have all vowel-macron combinations but lack the ‘okina in its preferred location. All others have missing vowel-macron combinations. 02BB 0100 0101 0112 0113 012A 012B 014C 014D 016A 016B (ʻ) (Ā) (ā) (Ē) (ē) (Ī) (ī) (Ō) (ō) (Ū) (ū) .Helvetica LT MM no no no no no no no no no no no .Keyboard no no no no no no no no no no no .Times LT MM no no no no no no no no no no no Abadi MT Condensed Extra Bold no no no no no no no no no no no Abadi MT Condensed Light no no no no no no no no no no no Academy Engraved LET YES YES YES YES YES YES YES YES YES YES YES Al Bayan Bold no no no no no no no no no no no Al Bayan Plain no no no no no no no no no no no American Typewriter YES YES YES YES YES YES YES YES YES YES YES American Typewriter Bold YES YES YES YES YES YES YES YES YES YES YES American Typewriter Condensed YES YES YES YES YES YES YES YES YES YES YES American Typewriter Condensed Bold YES YES YES YES YES YES YES YES YES YES YES American Typewriter Condensed Light YES YES YES YES YES YES YES YES YES YES YES American Typewriter Light YES YES YES YES YES YES YES YES YES YES YES Andale Mono no YES YES YES YES YES YES YES YES YES YES Apple Braille no no no no no no no no no no no Apple Braille Outline 6 Dot no no no no no no no no no no no Apple Braille Outline 8 Dot no no no no no no no no no no no Apple Braille Pinpoint 6 Dot no no no no no no no no no no -

Suitcase Fusion 7 Guide
Copyright © 2014–2017 Celartem, Inc., doing business as Extensis. This document and the software described in it are copyrighted with all rights reserved. This document or the software described may not be copied, in whole or part, without the written consent of Extensis, except in the normal use of the software, or to make a backup copy of the software. This exception does not allow copies to be made for others. Licensed under U.S. patents issued and pending. Extensis is a registered trademark of Celartem, Inc. The Extensis logos, Extensis Portfolio, Font Sense, Font Vault, FontLink, QuickComp, QuickFind, QuickMatch, QuickType, Suitcase, Suitcase Attaché, TurboSync, Universal Type, Universal Type Client, and Universal Type Core are trademarks of Extensis. Portfolio Flow, Portfolio NetPublish, Suitcase Fusion, Type Server, and Universal Type Server are registered trademarks of Extensis. Celartem, Celartem, Inc., and the Celartem logo are trademarks of Celartem, Inc. Adobe, Acrobat, After Effects, Creative Cloud, Creative Suite, Illustrator, InCopy, InDesign, Photoshop, PostScript, Typekit and XMP are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple, Bonjour, the Bonjour logo, Finder, iBooks, iPhone, Mac, the Mac logo, Mac OS, OS X, Safari, and TrueType are trademarks of Apple Inc., registered in the U.S. and other countries. macOS is a trademark of Apple Inc. App Store is a service mark of Apple Inc. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license. Microsoft, Excel, Internet Explorer, PowerPoint, SQL Server, and Windows are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.