Hiview (GUI Application)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
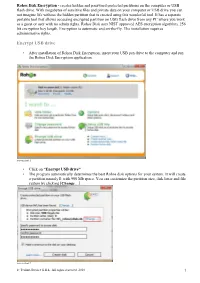
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on Appimages and Atomic Upgrades by Nitrux Latinoamerican S.C
ModSecurity Globbing Edit PDFs and nginx and Regex with Xournal Since 1994: The original magazine of the Linux community Linux Gaming A Talk with Linux Game Developers | Review: Thrones of Britannia Two Portable DIY Retro Console Projects | Survey of Native Linux Games TASBot the Linux-Powered Robot Plays Games for Charity ISSUE 290 | SEPTEMBER 2018 www.linuxjournal.com SEPTEMBER 2018 CONTENTS ISSUE 290 86 DEEP DIVE: Gaming 87 Crossing Platforms: a Talk with the Developers Building Games for Linux By K.G. Orphanides Games for Linux are booming like never before. The revolution comes courtesy of cross-platform dev tools, passionate programmers and community support. 105 Would You Like to Play a Linux Game? By Marcel Gagné A look at several games native to Linux. 117 Meet TASBot, a Linux-Powered Robot Playing Video Games for Charity By Allan Cecil Can a Linux-powered robot play video games faster than you? Only if he . takes a hint from piano rolls...and the game for Linux in November 2016. Enix. Feral Interactive released and published by Square , developed by Eidos Montréal doesn’t desync. 135 Review: Thrones Shroud of the Avatar Shroud of Britannia Deus Ex: Mankind Divided By Marcel Gagné from from A look at the recent game from the Total War series on the Linux desktop Image from Portalarium’s Portalarium’s Image from thanks to Steam and Feral Interactive. Cover image 2 | September 2018 | http://www.linuxjournal.com CONTENTS 6 Letters UPFRONT 14 Clearing Out /boot By Adam McPartlan 17 VCs Are Investing Big into a New Cryptocurrency: Introducing Handshake By Petros Koutoupis 20 Edit PDFs with Xournal By Kyle Rankin 22 Patreon and Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on AppImages and Atomic Upgrades By Nitrux Latinoamerican S.C. -

Laplink® Pcmover® Business User Guide
Laplink® PCmover® Business The Only Software that Moves Programs, Files, and Settings to a New PC! User Guide Customer Service/Technical Support: Web: http://www.laplink.com/contact E-mail: [email protected] Tel (USA): +1 (425) 952-6001 Fax (USA): +1 (425) 952-6002 Tel (UK): +44 (0) 870-2410-983 Fax (UK): +44 (0) 870-2410-984 Laplink Software, Inc. 600 108th Ave. NE, Suite 610 Bellevue, WA 98004 U.S.A. Copyright / Trademark Notice © Copyright 2019 Laplink Software, Inc. All rights reserved. Laplink, the Laplink logo, Connect Your World, and PCmover are registered trademarks or trademarks of Laplink Software, Inc. in the United States and/or other countries. Other trademarks, product names, company names, and logos are the property of their respective holder(s). MN-PCMBUS-EN-11 (REV. 2019-9-19) Laplink PCmover Business is a business-class migration utility capable of automatically moving selected files, users, settings, and programs from an old PC to the new PC. Transferring a PC or laptop across a network, Laplink USB cable, Laplink Ethernet cable or using external media or storage can be as simple as a single click. Computers with multiple users have the option to transfer some or all the users at once, with security information about file ownership and access control preserved for each user. Common PCmover Migration Scenarios 1. Transfer a user from an old machine to a new machine with the same or newer Windows Operating System. 2. Upgrade a user’s machine to a newer version OS, including Windows 8 (32-bit and 64-bit). -

IMPORTANT! Files Saved to This USB Are NOT Automatically Encrypted
IMPORTANT! Files saved to this USB are NOT automatically encrypted. You must use the SecureLock II software interface to secure your files. SecureLock II™ User Manual Encryption Application for USB Flash Drives User Manual Version 1.0.0.3 © 2004-2012 Integral Memory plc Table of Contents Table of Contents ................................................................................................... 2 1. Introduction..................................................................................................... 3 2. System Requirements .................................................................................... 4 3. Working with SecureLock II ............................................................................ 5 3.1. Setting up SecureLock II ........................................................................ 5 3.2. Setting up a Password ........................................................................... 6 3.3. Password retries .................................................................................... 8 3.4. Display Settings ..................................................................................... 8 3.5. Using Drag & Drop to copy files ............................................................. 9 3.6. Opening and modifying files within SecureLock II ................................ 11 3.7. Security settings ................................................................................... 12 4. Safely Remove Hardware ........................................................................... -

Web Publishing Framework and Design Principles
ISSN 2348 - 2249 Volume-3, Issue-1, January-March, 2015 International Journal for Multi Disciplinary Engineering and Business Management (IJMDEBM) Platform Independent Portable Application for Smartphones: A Review Jagjit Singh Gurjit Singh Bhathal Research Scholar, Department of Computer Engineering Department of Computer Engineering Punjabi University, Patiala Punjabi University, Patiala India India [email protected] [email protected] Abstract – In today’s IT industry, we have different types of and availability but with mobile phones we are connected and operating systems. Each has their own capacity to interact approachable to everyone all times. As it is portable and handy with application. Sometimes, performance decreases due to we can easily carry it anywhere. Same concept can be applied complexity of OS and application. To reduce the overhead, to software also. So that it is available to us where ever we go prevent any loss of data and application of OS and increase the whether we are connected to internet or not, whether we are performance of any application software, we have number of on our own PC or not, same application with same technologies available in the market, which are redefined to environment. handle the current scenario of IT industry. We can protect our devices from virus like threats and other security threats. This II. PORTING, PORTABILITY AND PORTABLE technology breaks the boundary of hardware compatibility APPLICATIONS problem on all types of devices including smart phones. In this Porting means to create an executable version of a system paper, we will discuss part of a technology that is application unit, so that it may run in a new environment based on existing virtualization, which is using portable software as a solution to version. -

How Linux Containers Have Evolved Daniel Walsh 11 Containers Have Come a Long Way in the Past Few Years
. ........ .... ... .. .. .. ... .. OPENSOURCE.COM Opensource.com publishes stories about creating, adopting, and sharing open source solutions. Visit Opensource.com to learn more about how the open source way is improving technologies, education, business, government, health, law, entertainment, humanitarian efforts, and more. Submit a story idea: https://opensource.com/story Email us: [email protected] Chat with us in Freenode IRC: #opensource.com . OPEN SOURCE YEARBOOK 2017 . OPENSOURCE.COM 3 ............................. AUTOGRAPHS . .... ... .. .. .. ........ ... .. ............................. AUTOGRAPHS . .... ... .. .. .. ........ ... .. OPENSOURCE.COM............................. ........ WRITE FOR US ................... 7 big reasons to contribute to Opensource.com: Career benefits: “I probably would not have gotten my most recent job if it had not been for my articles on 1 Opensource.com.” Raise awareness: “The platform and publicity that is available through Opensource.com is extremely 2 valuable.” Grow your network: “I met a lot of interesting people after that, boosted my blog stats immediately, and 3 even got some business offers!” Contribute back to open source communities: “Writing for Opensource.com has allowed me to give 4 back to a community of users and developers from whom I have truly benefited for many years.” Receive free, professional editing services: “The team helps me, through feedback, on improving my 5 writing skills.” We’re loveable: “I love the Opensource.com team. I have known some of them for years and they are 6 good people.” 7 Writing for us is easy: “I couldn't have been more pleased with my writing experience.” Email us to learn more or to share your feedback about writing for us: https://opensource.com/story Visit our Participate page to more about joining in the Opensource.com community: https://opensource.com/participate Find our editorial team, moderators, authors, and readers on Freenode IRC at #opensource.com: https://opensource.com/irc . -

Setting up Your Open-Source Development Environment
Setting Up Your Open-Source Development Environment Mark Irish [email protected] Staff Software Developer IBM April 28, 2021 POW3R Digital Outline Open-Source Software on IBM i Setting Up Your Development Environment Access Client Solutions Installing Yum Setting up SSH Mounting the File System Using a Sane Text Editor Setting up ODBC Containers (optional) © 2021 IBM Corporation Open-Source Software on IBM i © 2021 IBM Corporation Open-Source Software (OSS) Open-source software has publicly available source code Why would anyone make open-source software? – Greater transparency of what software does – Others can find/fix bugs and add functionality – Wider adoption and popularity “Free”, but... Use of open-source software is dictated by a license © 2021 IBM Corporation Open-Source Software on IBM i Delivered on PASE (Portable Application Solutions Environment) Delivered through yum (package manager) – Very “normal”, will feel familiar to Unix users (Linux, Mac) 600+ packages available DO NOT USE 5733-OPS (out of support) © 2021 IBM Corporation OSS as a Gateway Artificial Intelligence (AI) / Machine Learning (ML) – IBM Watson Solutions ● Watson Studio ● Watson Machine Learning ● Watson Machine Learning Accelerator Quantum Computing Internet of Things (IoT) REST APIs and more! © 2021 IBM Corporation Things That Don’t Go Together © 2021 IBM Corporation Things That Don’t Go Together © 2021 IBM Corporation Things That Don’t Go Together © 2021 IBM Corporation Need a More “Normal” Environment The 5250 “green screen” terminal -

USB Software
Now you can carry your favorite computer programs along with all of your bookmarks, settings, email and more with you. Use them on any Windows computer. All without leaving any personal data behind. USB Apps .. Provides a truly open platform that works with any hardware you like (USB flash drive, iPod, portable hard drive, etc). It's open source built around an open format that any hardware vendor or software developer can use. SanDisk and Microsoft technology announcement On May 11, 2007, Microsoft and SanDisk announced an agreement that expands on SanDisk's existing U3 Smart Technology. Under the terms of the agreement, MS will develop a new software experience and SanDisk will develop new hardware capabilities, including the addition of TrustedFlash security technology. The new offering will be commercially available starting in the second half of 2008. Page 1 Computer Users Group of Greeley Colorado ... DonW 6/13/200 A portable application, or portable app for short, is a software program that does not require any kind of formal installation onto a computer's permanent storage device to be executed, and can be stored on a removable storage device such as a CD- ROM, USB flash drive, flash card, or even a floppy disk, enabling it to be used on multiple computers. This does not mean that it can be taken and used on a different operating system, processing platform, or another computer with completely different hardware (i.e., those that are not compatible with the software as stated by its requirements), so it is not to be confused with the concept of software portability, which is the ability for software to be run or compiled with little modification on diverse computing platforms. -

Bakalářská Práce
Jiho česká univerzita v Českých Bud ějovicích Pedagogická fakulta Katedra fyziky Bakalá řská práce České Bud ějovice 2009 Kamil Vojík Jiho česká univerzita v Českých Bud ějovicích Pedagogická fakulta Katedra fyziky Přenosné aplikace a Virtualizace aplikací pro OS Windows Bakalá řská práce Vedoucí práce: Ing. Michal Šerý Autor: Kamil Vojík, DiS. Anotace Obsahem práce je popsání oblasti p řenosných aplikací. V teoretické části je popsána definice p řenosných aplikací a výhody jejich použití. Jsou zde dále popsány zp ůsoby jak tyto aplikace získat. Jedná se o oblast virtualizace aplikací, platformy p řenosných aplikací, Live OS a Cloud computing. Praktickou část tvo ří popis a ukázka postup ů, jak přenosné aplikace pomocí jednotlivých technologií vytvo řit. Jsou popsány vlastnosti výsledných řešení na základ ě post řeh ů, které jsem p ři jejich realizaci získal. Záv ěr práce tvo ří porovnání a doporu čení technologií na základ ě získaných poznatk ů. Neexistuje univerzální řešení a je nutné se rozhodnout na základ ě požadavk ů každého uživatele. Při porovnání podle kritéria cena/výkon nejlépe dopadla platforma Ceedo, která používá virtualizaci aplikací. Abstract The content of this theses „Portable applications and Application virtualization for Windows OS“ is to describe the area of Portable applications. The theoretical part describes definition of Portable applications and benefits of theirs use. There are also described ways how to get these applications. This is area of Application virtualization, Portable applications platform, Live OS and Cloud computing. The practical part consists of descriptions and demonstrations of procedures how to create Portable applications using various technologies. There are described properties of the resultant solutions on the basis of observations that I gained during their implementation.