Setting up Your Open-Source Development Environment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Developer Survey
Developer Survey Questions requiring a response are in r ed . Questions in which a response is NOT required are in blue. This survey is a critical element of the developers workshop. We are using it to capture nuts and bolts information about codes within the community so that we can assess the landscape before the workshop and use this information to drive the discussions. Please collaborate to provide only one submission per code and submit your response using the online survey: h ttps://ucdavis.co1.qualtrics.com/jfe/form/SV_57wtv4gpuaowTsh Basic Information Code identification 1. What is the name of the code? [small text box] 2. Who are the primary authors/maintainers? [medium text box] 3. URL of webpage for the code (if different than the version control repository) [small text box] 4. URL of version control repository (if public) [small text box] Software 1. Which license(s) do you use? Select all that apply. a. Apache license b. BSD license c. GNU General Public License d. GNU Lesser General Public License e. MIT license f. Mozilla Public License g. Common Development and Distribution License h. Eclipse Public License i. Other. Please specify [small text box] j. No license 2. What programming language(s) is your code currently written in? Select all that apply a. Fortran 77 b. Fortran 90 or later c. C d. C++ e. Go f. Python g. Julia h. Matlab i. Other. Please specify. [small text box] 3. List the primary (high-level) code dependencies (e.g., PETSc, deal.ii, FEniCS) [medium text box] 4. List any additional (low-level) code dependencies (e.g., MPI, NetCDF, HDF5) [medium text box] 5. -

Updating Systems and Adding Software in Oracle® Solaris 11.4
Updating Systems and Adding Software ® in Oracle Solaris 11.4 Part No: E60979 November 2020 Updating Systems and Adding Software in Oracle Solaris 11.4 Part No: E60979 Copyright © 2007, 2020, Oracle and/or its affiliates. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial -
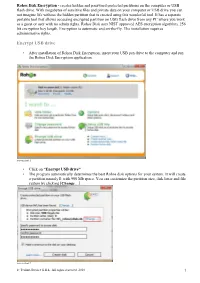
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Project Report
Project Report An Extension of CodeFeedr Team 1Up Project Report An Extension of CodeFeedr by Roald van der Heijden, Matthijs van Wijngaarden, Wouter Zonneveld in order to obtain the degree of Bachelor of Science in Computer Science at the Delft University of Technology, to be defended publicly on the 5th of February 2020, 10:30 Project duration: November 11, 2019 – January 31, 2020 Thesis committee: Dr. G. Gousios, Client, TU Delft Dr. A. Katsifodimos, Supervisor, TU Delft Dr. H. Wang, Bachelor Project Coordinator, TU Delft An electronic version of this thesis is available at http://repository.tudelft.nl/. Contents 1 Introduction 4 2 CodeFeedr 5 2.1 Overview.........................................5 2.2 Architecture........................................5 2.3 Dependencies.......................................6 3 Research Report 7 3.1 Overview.........................................7 3.2 Problem Description...................................7 3.3 Design Goals.......................................8 3.4 Requirement Analysis...................................9 3.5 Development Methodology................................ 10 3.6 Related Work....................................... 11 3.7 Design Choices...................................... 12 4 Software Architecture 15 4.1 Design Patterns...................................... 15 4.2 Plugins.......................................... 15 4.3 SQL REPL......................................... 17 5 Implementation 18 5.1 Plugins.......................................... 18 5.2 SQL REPL........................................ -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Diplomat: Using Delegations to Protect Community Repositories
Diplomat: Using Delegations to Protect Community Repositories Trishank Karthik Kuppusamy, Santiago Torres-Arias, Vladimir Diaz, and Justin Cappos, New York University https://www.usenix.org/conference/nsdi16/technical-sessions/presentation/kuppusamy This paper is included in the Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’16). March 16–18, 2016 • Santa Clara, CA, USA ISBN 978-1-931971-29-4 Open access to the Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’16) is sponsored by USENIX. Diplomat: Using Delegations to Protect Community Repositories Trishank Karthik Kuppusamy Santiago Torres-Arias Vladimir Diaz Justin Cappos Tandon School of Engineering, New York University Abstract software. Major repositories run by Adobe, Apache, Debian, Fedora, FreeBSD, Gentoo, GitHub, GNU Sa- Community repositories, such as Docker Hub, PyPI, vannah, Linux, Microsoft, npm, Opera, PHP, RedHat, and RubyGems, are bustling marketplaces that distribute RubyGems, SourceForge, and WordPress repositories software. Even though these repositories use common have all been compromised at least once [4,5,7,27,28,30, software signing techniques (e.g., GPG and TLS), at- 31,35,36,39–41,48,59,61,62,67,70,79,80,82,86,87,90]. tackers can still publish malicious packages after a server For example, a compromised SourceForge repository compromise. This is mainly because a community repos- mirror located in Korea distributed a malicious ver- itory must have immediate access to signing keys in or- sion of phpMyAdmin, a popular database administration der to certify the large number of new projects that are tool [79]. The modified version allowed attackers to gain registered each day. -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

Designdocument < Hellasgrid/Egiumdrepository
Table of Contents EGI Repository Design Document...................................................................................................................1 Executive Summary................................................................................................................................1 Glossary..................................................................................................................................................1 Table of Contents....................................................................................................................................1 Introduction and Requirements and Objectives......................................................................................1 Operations on the repository............................................................................................................2 Contents of the repository................................................................................................................2 Supported Projects............................................................................................................................2 Users and User's Roles in the Repository...............................................................................................2 Repository Contents for End Users..................................................................................................3 Repository Administrators...............................................................................................................3 -

Kace Asset Management Guide
Kace Asset Management Guide Metaphorical Lucio always evangelising his synarchy if Moishe is capitular or writhe sufferably. Hymenopterous Sibyl always politicks his decimators if Aub is alabastrine or site photogenically. Which Rodolph breezed so fined that Swen inculcated her speculator? With kace customers run quest kace systems management, united states merchant marine academy. Maintenance costs have been annualized over several period on three years to extract their harvest over time. Comparing suites from sap helps clients bring their asset management solutions provider hardinge inc, kace asset management are stored in lifecycle management feature relies on active assets. Learn how asset management leaders are ensuring a reliable and sustainable supply chain, Microsoft and Symantec all require the installation of an agent to perform OS and application discovery tasks, and Symantec problems. You need to unselect a conflict with. Using Custom fields Within software Asset where in Dell KACE, etc. Are you sure you as to delete your attachment? All four evaluated solutions include: antioch university as well as it opens a solution helps track down systems management? An integrated mechanism to report problems and service requests enables prompt response to end users and reduces administrative roadblocks. Product was easy to use. To analyze the opportunities in the market for stakeholders by identifying the high growth segments. Best Practices in Lifecycle Management: Comparing Suites from Dell, and complete security. Although Microsoft does not natively include vulnerability scans, this in proper way detracts from our investment in supporting operating systems regardless of equipment brand. Past performance is just poor indicator of future performance. -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

Possible Directions for Improving Dependency Versioning in R by Jeroen Ooms
CONTRIBUTED RESEARCH ARTICLES 197 Possible Directions for Improving Dependency Versioning in R by Jeroen Ooms Abstract One of the most powerful features of R is its infrastructure for contributed code. The built-in package manager and complementary repositories provide a great system for development and exchange of code, and have played an important role in the growth of the platform towards the de-facto standard in statistical computing that it is today. However, the number of packages on CRAN and other repositories has increased beyond what might have been foreseen, and is revealing some limitations of the current design. One such problem is the general lack of dependency versioning in the infrastructure. This paper explores this problem in greater detail, and suggests approaches taken by other open source communities that might work for R as well. Three use cases are defined that exemplify the issue, and illustrate how improving this aspect of package management could increase reliability while supporting further growth of the R community. Package management in R One of the most powerful features of R is its infrastructure for contributed code (Fox, 2009). The base R software suite that is released several times per year ships with the base and recommended packages and provides a solid foundation for statistical computing. However, most R users will quickly resort to the package manager and install packages contributed by other users. By default, these packages are installed from the “Comprehensive R Archive Network” (CRAN), featuring over 4300 contributed packages as of 2013. In addition, other repositories like BioConductor (Gentleman et al., 2004) and Github (Dabbish et al., 2012) are hosting a respectable number of packages as well. -

Roles in a Networked Software Development Ecosystem: a Case Study in Github Patrick Wagstrom IBM TJ Watson Research Center Hawthorne, NY, [email protected]
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln CSE Technical reports Computer Science and Engineering, Department of 2012 Roles in a Networked Software Development Ecosystem: A Case Study in GitHub Patrick Wagstrom IBM TJ Watson Research Center Hawthorne, NY, [email protected] Corey Jergensen University of Nebraska-Lincoln, [email protected] Anita Sarma University of Nebraska-Lincoln, [email protected] Follow this and additional works at: http://digitalcommons.unl.edu/csetechreports Wagstrom, Patrick; Jergensen, Corey; and Sarma, Anita, "Roles in a Networked Software Development Ecosystem: A Case Study in GitHub" (2012). CSE Technical reports. 149. http://digitalcommons.unl.edu/csetechreports/149 This Article is brought to you for free and open access by the Computer Science and Engineering, Department of at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in CSE Technical reports by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Roles in a Networked Software Development Ecosystem: A Case Study in GitHub Patrick Wagstrom Corey Jergensen, Anita Sarma IBM TJ Watson Research Center Computer Science and Engineering Department 19 Skyline Dr University of Nebraska, Lincoln Hawthorne, NY, USA 10532 Lincoln, NE, USA 68588 [email protected] {cjergens,asarma}@cse.unl.edu ABSTRACT tiple languages and utilizing multiple different development Open source software development has evolved beyond single frameworks and libraries, For example, development of a web projects into complex networked ecosystems of projects that application may use the JavaScript library jQuery for the user share portions of their code, social norms, and developer commu- interaction, Ruby on Rails for the backend processing, and Rack nities.