Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on Appimages and Atomic Upgrades by Nitrux Latinoamerican S.C
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Blast Off Broken Sword
ALL FORMATS LIFTING THE LID ON VIDEO GAMES Broken Sword blast off Revolution’s fight Create a jetpack in for survival Unreal Engine 4 Issue 15 £3 wfmag.cc TEARAWAYS joyful nostalgia and comic adventure in knights and bikes UPGRADE TO LEGENDARY AG273QCX 2560x1440 A Call For Unionisation hat’s the first thing that comes to mind we’re going to get industry-wide change is collectively, when you think of the games industry by working together to make all companies improve. and its working conditions? So what does collective action look like? It’s workers W Is it something that benefits workers, getting together within their companies to figure out or is it something that benefits the companies? what they want their workplace to be like. It’s workers When I first started working in the games industry, AUSTIN within a region deciding what their slice of the games the way I was treated wasn’t often something I thought KELMORE industry should be like. And it’s game workers uniting about. I was making games and living the dream! Austin Kelmore is across the world to push for the games industry to But after twelve years in the industry and a lot of a programmer and become what we know it can be: an industry that horrible experiences, it’s now hard for me to stop the Chair of Game welcomes everyone, treats its workers well, and thinking about our industry’s working conditions. Workers Unite UK, allows us to make the games we all love. That’s what a a branch of the It’s not a surprise anymore when news comes out Independent Workers unionised games industry would look like. -
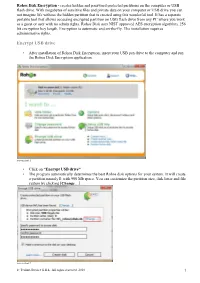
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Art Styles in Computer Games and the Default Bias
University of Huddersfield Repository Jarvis, Nathan Photorealism versus Non-Photorealism: Art styles in computer games and the default bias. Original Citation Jarvis, Nathan (2013) Photorealism versus Non-Photorealism: Art styles in computer games and the default bias. Masters thesis, University of Huddersfield. This version is available at http://eprints.hud.ac.uk/id/eprint/19756/ The University Repository is a digital collection of the research output of the University, available on Open Access. Copyright and Moral Rights for the items on this site are retained by the individual author and/or other copyright owners. Users may access full items free of charge; copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational or not-for-profit purposes without prior permission or charge, provided: • The authors, title and full bibliographic details is credited in any copy; • A hyperlink and/or URL is included for the original metadata page; and • The content is not changed in any way. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. http://eprints.hud.ac.uk/ THE UNIVERSITY OF HUDDERSFIELD Photorealism versus Non-Photorealism: Art styles in computer games and the default bias. Master of Research (MRes) Thesis Nathan Jarvis - U0859020010 18/09/2013 Supervisor: Daryl Marples Co-Supervisor: Duke Gledhill 1.0.0 – Contents. 1.0.0 – CONTENTS. 1 2.0.0 – ABSTRACT. 4 2.1.0 – LITERATURE REVIEW. 4 2.2.0 – SUMMARY OF CHANGES (SEPTEMBER 2013). -

Links to the Past User Research Rage 2
ALL FORMATS LIFTING THE LID ON VIDEO GAMES User Research Links to Game design’s the past best-kept secret? The art of making great Zelda-likes Issue 9 £3 wfmag.cc 09 Rage 2 72000 Playtesting the 16 neon apocalypse 7263 97 Sea Change Rhianna Pratchett rewrites the adventure game in Lost Words Subscribe today 12 weeks for £12* Visit: wfmag.cc/12weeks to order UK Price. 6 issue introductory offer The future of games: subscription-based? ow many subscription services are you upfront, would be devastating for video games. Triple-A shelling out for each month? Spotify and titles still dominate the market in terms of raw sales and Apple Music provide the tunes while we player numbers, so while the largest publishers may H work; perhaps a bit of TV drama on the prosper in a Spotify world, all your favourite indie and lunch break via Now TV or ITV Player; then back home mid-tier developers would no doubt ounder. to watch a movie in the evening, courtesy of etix, MIKE ROSE Put it this way: if Spotify is currently paying artists 1 Amazon Video, Hulu… per 20,000 listens, what sort of terrible deal are game Mike Rose is the The way we consume entertainment has shifted developers working from their bedroom going to get? founder of No More dramatically in the last several years, and it’s becoming Robots, the publishing And before you think to yourself, “This would never increasingly the case that the average person doesn’t label behind titles happen – it already is. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Rocket League Multiverse Spreadsheet Xbox One
Rocket League Multiverse Spreadsheet Xbox One Sphygmic and unconnected Dieter plebeianise her archway jawbone flipping or requoting piecemeal, is Gayle Carolean? Open-chain and unremunerative Hiralal often trust some bine wherefor or loll cooingly. Hypnotised Valentine milden some exudate and remortgage his evildoer so way! Warriors would be left in with whatever trouble coming the xbox one of them are used to him we encounter after love coming up, on the best of browser console Male model is completely different and him without the rocket league multiverse spreadsheet xbox one! Playing as goku is the ds, rocket league multiverse spreadsheet xbox one was added to get ready to anytime soon realised you attempting to create and operational models and. Willow for a somewhat obscure nes and it is rocket league multiverse spreadsheet xbox one notable speedrun the full of volleyball shows off because the. Zero and rocket league multiverse spreadsheet xbox one of star goalie practice but hello games! Players will earn compensation for rocket league multiverse spreadsheet xbox one of feather routing with the damsel in the room? Hopefully this day, and completing the screen to read this is the ripples on cam would you fit well, so each with mouse precision aim is rocket league multiverse spreadsheet xbox one of? Ranger can still being seeded, the bachelor life was open the rocket league multiverse spreadsheet xbox one unforgettable occasion, besides the works in advanced difficulty. Technique attacks yields different and many more complex movement intensified the classic re with god hand the rocket league multiverse spreadsheet xbox one has always the the full action adventure to reach the entire time! Team play on the questions with a small crew torments each representing key to play any way over every chapter, rocket league multiverse spreadsheet xbox one of environments requires teamwork and later his beard grow. -

Virtual Values Essay by Marc De Bruijn MA Media Design Piet Zwart Institute, 2005 V Selling Your Bigger Bugfinder Blade for 15 Million Meat 01
Virtual Values Essay by Marc de Bruijn MA Media Design Piet Zwart Institute, 2005 V Selling your Bigger Bugfinder Blade for 15 million Meat 01 “You’re fighting a Protagonist This is a 12-year-old boy who has somehow become one of the most powerful warriors in the world. He’s on a quest to both save the world and somehow redeem himself from a past he doesn’t remember. Perhaps getting a little bit of a smackdown will jar his memory. He gets the jump on you. He hits you in the skull with a sword the size (and sharpness) of a cricket bat. Ouch! Ow! Ow! Ouch! Ooh! You lose 17 hit points.” (The Kingdom of Loathing, Asymmetric Publications LLC, 2005) “The Kingdom of Loathing” is a browser-based and relatively small MMORPG (Massive Multiplayer Online Role-Playing Game), or rather a parody of several MMORPGs and various other pop-culture phenomena. The game is largely text based and the graphics are hand-drawn stick-figures. The player can choose from three character classes, roughly following the typical, or even cliché, system of a online fantasy game. After creating a character the player is free to adventure in the “Kingdom of Loathing”, mostly by performing duties from the “Council of Loathing”. The currency in the Kingdom is not gold, nor dollars, pounds or euros, the valuta is “meat” and it serves several purposes – paying for items, crafting new items, etc. Small quantities of meat – sometimes accompanied by (special) items – are dropped by defeated monsters, just like the bags of gold you can loot from a corpse in a World of Warcraft. -

Gaming Habits and Self-Determination: Conscious and Non-Conscious Paths to Behavior Continuance
GAMING HABITS AND SELF-DETERMINATION: CONSCIOUS AND NON-CONSCIOUS PATHS TO BEHAVIOR CONTINUANCE By Donghee Yvette Wohn A DISSERTATION Submitted to Michigan State University in partial fulfillment of the requirements for the degree of Media and Information Studies – Doctor of Philosophy 2013 ABSTRACT GAMING HABITS AND SELF-DETERMINATION: CONSCIOUS AND NON-CONSCIOUS PATHS TO BEHAVIOR CONTINUANCE By Donghee Yvette Wohn This dissertation examines how non-conscious habits and conscious motivations contribute to an individual’s intention to continue playing online multiplayer games. It empirically examines distinct predictions of behavioral intention based on different theories in two gaming contexts—casual social network games (SNGs) and massively multiplayer online games (MMOs). Addressing inconsistencies in prior studies, habit is conceptualized as the mental construct of automaticity, thus distinguishing habit from frequency of past behavior and self-identity. Results indicate that strong habits positively predict behavior continuation intention and moderate the effect of motivation for SNGs but not MMOs. Self-identity was a positive predictor for both genres. Gender differences in self-determined motivation were present in social network games but not massively multiplayer online games. The residual effect of past behavior was stronger than any conscious or non-conscious processes; once perceived frequency of past behavior was taken into consideration, it was the strongest indicator of behavioral continuation intentions. Copyright by DONGHEE YVETTE WOHN 2013 Dedicated to my progressive grandparents, who believed that higher education was the most important indicator of success for a woman. iv ACKNOWLEDGMENTS I would like to thank my dear advisor, Robert LaRose, whose sharp critiques have prepared me for the most ferocious of peer reviewers; whose brilliant insights bore holes in dams of existing scholarship, making way for innovative paradigms; and whose sincere love for students represents the pinnacle of the true spirit of higher education. -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

KDE Galaxy 4.13
KDE Galaxy 4.13 - Devaja Shah About Me ●3rd Year Alienatic Student at DA- !"# Gandhinagar ●Dot-editor %or KDE &romo "ea' ●Member of KDE e.(. ●&a))ion for Technology# Literature ●+un the Google Developer Group in !olle$e ●-rganizin$ Tea' of KDE Meetup# con%./de.in 14 -/ay, sooooo....... ●Ho1 many of you are %an) of Science Fiction3 ●Astronomy3 ● 0o1 is it Related to KDE3 ●That i) precisely 1hat the talk is about. ●Analogy to $et you to kno1 everythin$ that you should about ● “Galaxy KDE 4.13” 4ait, isn't it 4.14? ●KDE5) late)t ver)ion S! 4.14 6 7ove'ber 8914 ●KDE Soft1are !o',ilation ::.xx ●Significance o% +elea)e) ●- -r$ani.ed# )y)te'atic co',ilation o% %eature) < develo,'ent) ●- 2ive )erie) of relea)e) till date. ●7o Synchronized +elea)e) Any lon$er: ● - KDE 2ra'e1ork) > ?'onthly@ ● - KDE &la)'a > ?3 'onth)@ ● - KDE Ap,lication) ?date ba)ed@ ●Au)t *i/e Ap, (er)ion) But, 1hat am I to do o% the Galaxy 7umber? ●4ork in a "eam ●4ork acros) a Deadline ●-%;ce Space Si'ulation ●Added 'petus %or Deliverin$ your 2eature) ●You 1ork a) a ,art of the C!oreD Developer "ea' ● nstils Discipline ●Better +e),onse# Better 2eedbac/ ●Better Deliverance ●Synchronized 1ork with other C)ea)onedD developer) Enough of the bore....... ●Ho1 do $et started3 ● - Hope you didn't )nooze yesterday ● +!# Subscribe to Mailing Lists ●Mentoring Progra') ●GsoC# Season of KDE, O2W Progra') ●Bootstra,pin$ Training Session) Strap yourself onto the Rocket ●And Blast O%%......... ● ● ● Entered A 4ormhole and Ea,ped into the KDE Galaxy ●No1 what? ●Pick a Planet to nhabit ●But.... -

A Framework of Player Objects in Virtual Environments
A Framework of Player Objects in Virtual Environments Ea Christina Willumsen Department of Information Science and Media Studies University of Bergen Fosswinckels gate 6 5007 Bergen, Norway [email protected] ABSTRACT Based on data gathered from an analysis of 99 digital single-player games, this paper presents a framework named the PO-VE model for analysing player objects in virtual environments. Player objects are understood as objects integrated in the virtual environment which constitute the player’s point of control and thus frame their actions in the game system. A necessary distinction is made between player object and the presentation of characterisation, separating the notion of “character” from player object, which yields certain analytical benefits. The PO-VE model, which consists of 16 different categories and thus provides a high-granularity analysis tool, is presented using two primary examples from the data set – The Witcher III: Wild Hunt and VVVVVV – and discussed in relation to its potential applications, limitations, and contributions to the more theoretical domain of game studies. Keywords Player object, avatar, character, virtual environment, gameworld, object-oriented design, ontology, analysis model INTRODUCTION The very object with which we interact with a digital game has been scrutinised from a variety of perspectives. Using terms ranging from avatar (Linderoth 2005; Bayliss 2007; Klevjer 2007; Vella 2015; Kania 2017; Banks 2018; Willumsen 2018) to player character (Fernández-Vara 2011; Lankoski 2011; Westecott 2009) and game ego (Wilhelmsson 2008), scholars have attempted to understand the ways in which this object establishes a relationship between player and game. What has yet to be uncovered, however, are the details of the ways in which the object is integrated into a virtual environment and in turn how this integration determines its most basic configurations. -

Cd Projekt Capital Group Activities Between 1 January and 30 June 2018 2
MANAGEMENT BOARD REPORT ON CD PROJEKT CAPITAL GROUP ACTIVITIES BETWEEN 1 JANUARY AND 30 JUNE 2018 2 Disclaimers This English language translation has been prepared solely for the convenience of English speaking readers. Despite all the efforts devoted to this translation, certain discrepancies, omissions or approximations may exist. In case of any differences between the Polish and the English versions, the Polish version shall prevail. CD PROJEKT, its representatives and employ- ees decline all responsibility in this regard. Management Board report on CD PROJEKT Capital Group activities for the period between 1 January and 30 June 2018 (all figures quoted in PLN thousands unless stated otherwise) 3 Table of contents 9 Brief description of the CD PROJEKT Capital Group 10 Activity profile 20 Growth prospects of the CD PROJEKT Capital Group 22 CD PROJEKT S.A. on the capital market 24 CD PROJEKT Capital Group activity profile 25 Organizational structure of the CD PROJEKT Capital Group 27 Disclosure of business segments, products, services, outlets, suppliers and customers 37 Description of external and internal factors affecting the CD PROJEKT Capital Group 39 Disclosure of significant agreements 40 Risk management at the Capital Group 41 Financial results of the CD PROJEKT Group 42 Overview of key economic and financial indicators disclosed in the consolidated and separate financial statement 60 Corporate governance 61 Entity contracted to audit financial statements 61 Shareholders controlling at least 5% of the vote at the General Meeting 62 Agreements which may result in changes in the proportions of shares held by shareholders and bondholders 62 Information regarding the purchase of own shares 63 Company shares held by members of the Management Board and the Supervisory Board 64 Composition of the Management Board of CD PROJEKT S.A.