Bakalářská Práce
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
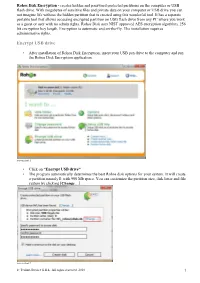
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

Easy2boot Usb Multiboot.Docx
Boot all your ISO's from one USB drive! 13. 16.13 Adding 'Install Windows xxx from ISO' menu entries to the Main menu Contents 14. 16.14 Removing the DOS, BACKUP and UTILITIES Main 1. 1 Introduction menu entries 1. 1.1 Three ways to add 'payload files' to E2B 15. 16.15 Change the way that payload files are listed in the 2. 2 E2B Version History menus 3. 3 Thanks for your help, feedback and support! 16. 16.16 Hotkey support 1. 3.1 Easy2Boot Introductory video 17. 16.17 Prevent the menu items from being automatically 4. 4 How to make a new Easy2Boot USB drive numbered 1. 4.1 Quick Instructions (video) 18. 16.18 Remove or change the 'Boot to first HDD [F7]' menu 2. 4.2 Quick Instructions (text) entry 3. 4.3 Really Detailed Instructions 19. 16.19 Remove or change the 'Reload Main Menu [F8]' menu 4. 4.4 3. Download E2B entry 5. 5 Getting Started - How to add payload (.ISO) files to 20. 16.20 Remove the 'Reboot [F9]' menu entry and function Easy2Boot 21. 16.21 Remove the 'Power Off [F10]' menu entry and function 1. 5.1 TWO GOLDEN RULES FOR E2B PAYLOAD FILES 22. 16.22 Add blank lines as separators to a menu 2. 5.2 FAQs 23. 16.23 Remove the 'Set default menu entry and timeout' Main 3. 5.3 Error 60: File not contiguous menu entry 4. 5.4 E2B Upgrade Packages 24. 16.24 Only show the Windows Install menu 5. -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

BASIC PC SECURITY a Ciphers by Ritter Page Terry Ritter a = Ritter B = Ciphersby [email protected] 2009 October 30
BASIC PC SECURITY A Ciphers By Ritter Page Terry Ritter A = ritter B = ciphersby [email protected] 2009 October 30 MY CONCLUSIONS: Microsoft has bumbled into an epic fail: The Windows environment is dangerous for on-line purchasing and banking, even when patched and with reasonable user attention. To reject malware, do not browse the Web in Windows; use some other operating system (OS). To prevent infection, boot your browsing OS from CD or DVD. There is a Web war on, and we are losing. Distant criminals can and do subvert the computers in our homes for their own profit. When criminals get control, they can distribute advertising, expose our passwords and data, find our personal information, and do whatever they want on our computers. When a Web computer is infected, anything on it can be exposed, changed or deleted remotely, so even "removing" the malware may not put things right. We do not have to give up the Web. We do have to give it some attention. MY CONCLUSIONS Wikipedia reports that about 93 percent of browsing occurs from a Windows operating system (OS). Even though Microsoft effectively owns the browsing environment, Panda Security has estimated that 58 percent of US PC's are infected with malware. If that is true, then Microsoft is responsible for an environment that has failed to protect most users. Panda also reports,"The huge amount of Trojans in circulation is due to the spectacular increase in the number of banker Trojans aimed at stealing user data." Malware makes on-line banking risky for most of us. -

Adrian Crenshaw
Adrian Crenshaw Irongeek.com I run Irongeek.com I have an interest in InfoSec education I don’t know everything - I’m just a geek with time on my hands (ir)Regular on the ISDPodcast http://www.isd-podcast.com/ Prepare yourselves for a disorganized boot CD/DVD/UFD braindump, but as notes they may help you to avoid my mistakes Irongeek.com Malware removal Forensics Privacy Access to restricted tools Imaging Physical access = pwnage These guys may come to visit Irongeek.com Something like this System Start Primary Boot Loader: BIOS, UEFI Secondary Boot Loader: SYSLINUX, Grub, NTLDR, BCD, Chainboot from one loader to another OS: Linux, Windows, Rule34OS Irongeek.com Why use memory? For optical media, it’s read only (mostly) For USB, it only has so many write cycles For both: Speed For some hardware, RAM disk just works better than UFD Not quite the same thing UnionFS, AuFS or EWF, which redirect writes to what would otherwise be a read only file system Irongeek.com Just a few: BackTrack Linux http://www.backtrack-linux.org Tails (The Amnesic Incognito Live System) http://tails.boum.org/ Bart’s PE/UBCD4Win http://www.nu2.nu/pebuilder/ http://www.ubcd4win.com/ Winbuilder/Win7PE SE http://winbuilder.net/ & http://reboot.pro/12427/ Konboot http://www.piotrbania.com/all/kon-boot/ Irongeek.com Tons of security tools Awesome hardware support for odd wireless needs Well maintained Can do a hard drive install if Image from http://www.backtrack-linux.org/screenshots/ you wish Irongeek.com Boot from CD/DVD to leave less of -

Microsoft Windows 7 Boot Disk Free Download
microsoft windows 7 boot disk free download How to Create and Use Windows 7 Repair Disk with ISO? Want to create Windows 7 repair disk with ISO image files? See this article and I’ll show you how to create a Windows 7 Home Premium/Ultimate/ Professional repair disk ISO? By Ivy / Last update May 18, 2021. Where can I download Windows 7 ISO? “After reading through numerous threads on similar topics, I am stumped. I am "simply" trying to create a USB stick with System Repair image so I can restore a system image. I do not have a CD/DVD drive and was hoping to download the ISO but no joy, because the link I found didn’t have a download URL, or it was paid. Thanks for help” You can download windows 7 repair disk ISO from Microsoft as long as you have the product key of your computer. it’s a very authoritative website, which is used by many users in worldwide. You can use it with confidence. How to create Windows 7 repair disk with ISO? Before you start, you need to download Windows 7 repair disk ISO from Microsoft and Windows 7 USB DVD download tool. Besides, you still need a USB drive with 4GB capacity. Step 1. Open Windows 7 USB DVD download tool, click Browse to find your ISO image files, then click Next . Step 2. Choose USB as your media type. Step 3. Insert USB flash drive and select it, then click Begin copying . Note: This tool will format your USB flash drive first, then create bootable USB device. -

Multi-Boot Mit Sardu 2.0.2A: Das Tool Installiert Live-Systeme Wie Fedora 14 Auf Hungsweise Ihrer DVD Im Unterord- Len
PRAXIS SARDU 2.0.2A Windows-System mit 64 Bit einsetzen, dann verwenden Sie stattdessen die Datei Multi-Boot mit “sardu_x64.exe“. Live-CDs einbinden Die Software-Auswahl erfolgt in Sardu über die Reiter “Antivirus“, “Utility“, “Linux Live“ Sardu 2.0.2a und “Windows“. Fast alle Live-Systeme der ersten drei Kategorien lädt Sardu direkt aus dem Internet. Nur die Live-Systeme der Rubrik Prüfen Sie PCs auf Viren, partitionieren Sie Festplatten neu und retten Sie Daten: “Windows“ müssen Sie selbst erstellen. Auf der Heft-DVD finden Sie zudem zahlrei- Sardu 2.0.2a installiert bis zu 50 Live-Systeme auf USB-Stick oder DVD. che ISO-Dateien, die Ihnen das zeitaufwendi- ge Herunterladen vom Internet ersparen. Wenn Sie diese Dateien in Sardu übernehmen wol- ardu 2.0.2a verwandelt USB-Sticks und Multi-Boot-Auswahl len, wechseln Sie in Ihr Sardu-Verzeichnis und S DVD-Rohlinge in multibootfähige All- kopieren die ISO-Dateien in den Unterordner round-Werkzeuge (kostenlos, www.sarducd.it Mit Sardu stellen Sie eine individuelle Aus- “ISO“. Nach einem Neustart des Tools lassen und auf ). Das Tool installiert bis zu 50 Live- wahl von Boot-CDs zusammen, die Sie auf Systeme auf einem Boot-Medium (Bild A). USB-Sticks installieren oder auf eine DVD Der Artikel beschreibt, wie Sie mit Sardu brennen. Kompakt ausgewählte Live-Systeme auf USB-Stick oder ■ Sardu 2.0.2a macht aus einem USB-Stick DVD installieren. Mit Hilfe dieser Systeme ret- Sardu starten oder einem DVD-Rohling eine Multi-Boot- ten Sie Daten, prüfen Rechner auf Viren und Sardu ist ein Sofort-Tool, das ohne Installation Plattform. -

It's That Time
December 2014 / January 2015 | Vol. 8 No. 1 VirtualizationReview.com 2015 READERS CHOICE AWARDS WINNER IT’S THAT TIME OFYEAR! Eggnog, presents and the products you like best. PLUS > VIRTUAL PREDICTIONS > DELL’S VDI STRATEGY > UNTANGLING VMWARE DRS VISIT VIRTUALIZATIONREVIEW.COM contents The objective is helping organizations accomplish their 6 goals; not to push any specifi c type of technology. By Dan Kusnetzky 2015Readers Choice Awards “Chromebook desktop ÌÌÌÌ Winner ÌÌÌÌ access looks especially promising, especially in the education market.” Garret Grajek, dinCloud 18 6 December 2014 / January 2015 | VIRTUALIZATION REVIEW | VOL. 7, NO. 2 FEATURES 11 Best Cloud Storage Product 15 Best Network 4 The 2015 Reader’s Choice 12 Best Cloud Security Product Virtualization Product Awards and Buyer’s Guide 12 Best Cloud Software Product 16 Best Virtualization Security Product You, the readers, have spoken. 13 Best Business Continuity Product Here are the virtualization and Best Converged 14 Best Virtualization 17 cloud computing products that Automation Product Infrastructure Product rock your world. Best Virtualization Training 15 Best Storage 17 6 Best Application Virtualization Product Virtualization Product 6 Best Server Virtualization Product Best Desktop Virtualization/ 7 18 2015 Virtualization Predictions COLUMNS Virtual Desktop Infrastructure Product What can you expect to happen 2 Editor’s Note: KEITH WARD in the virtualization and cloud 3 Expectations for 2015 8 Best Mobile Virtualization/ BYOD Product industries in the coming year? -

Open Source Publication Report – Honda RES
Open Source Publication Report – Honda RES Academic Free License v2.1 Full name Academic Free License v2.1 Short identifier AFL-2.1 Other web pages for this license http://opensource.linux-mirror.org/licenses/afl-2.1.txt Notes None Text The Academic Free License v.2.1 This Academic Free License (the "License") applies to any original work of authorship (the "Original Work") whose owner (the "Licensor") has placed the following notice immediately following the copyright notice for the Original Work: Licensed under the Academic Free License version 2.1 1) Grant of Copyright License. Licensor hereby grants You a world-wide, royalty-free, non-exclusive, perpetual, sublicenseable license to do the following: a) to reproduce the Original Work in copies; b) to prepare derivative works ("Derivative Works") based upon the Original Work; c) to distribute copies of the Original Work and Derivative Works to the public; d) to perform the Original Work publicly; and e) to display the Original Work publicly. 2) Grant of Patent License. Licensor hereby grants You a world-wide, royalty-free, non-exclusive, perpetual, sublicenseable license, under patent claims owned or controlled by the Licensor that are embodied in the Original Work as furnished by the Licensor, to make, use, sell and offer for sale the Original Work and Derivative Works. 3) Grant of Source Code License. The term "Source Code" means the preferred form of the Original Work for making modifications to it and all available documentation describing how to modify the Original Work. Licensor hereby agrees to provide a machine-readable copy of the Source Code of the Original Work along with each copy of the Original Work that Licensor distributes. -

Redalyc.Aplicaciones Portables, Una Alternativa Para La Gestión
Innovación Educativa ISSN: 1665-2673 [email protected] Instituto Politécnico Nacional México Jiménez León, Alejandro; Gutiérrez Vallejo, Ma. Graciela Aplicaciones portables, una alternativa para la gestión informativa en los sistemas de educación a distancia Innovación Educativa, vol. 11, núm. 57, octubre-diciembre, 2011, pp. 219-224 Instituto Politécnico Nacional Distrito Federal, México Disponible en: http://www.redalyc.org/articulo.oa?id=179422350024 Cómo citar el artículo Número completo Sistema de Información Científica Más información del artículo Red de Revistas Científicas de América Latina, el Caribe, España y Portugal Página de la revista en redalyc.org Proyecto académico sin fines de lucro, desarrollado bajo la iniciativa de acceso abierto Aplicaciones portables, una alternativa para la gestión informativa en los sistemas de educación a distancia Alejandro Jiménez León y Ma. Graciela Gutiérrez Vallejo Resumen El desarrollo tecnológico alcanzado en los últimos años ofrece a las instituciones de educación su- Palabras clave perior la posibilidad de implementar diversos programas de educación a distancia con el fin de sa- Aplicación portable, tisfacer la demanda educativa no cubierta por el sistema educativo tradicional. El problema es que, educación a distancia, tanto la institución como los alumnos, requieren hacer un uso intensivo de aplicaciones informáticas instituciones educativas, las cuales, en muchos casos, no están disponibles debido al elevado costo del software comercial. pendrive, software libre, Por ello, el objetivo de este artículo es proponer que las instituciones educativas implementen el uso tecnología. aplicaciones portables desarrolladas con software libre para que sus alumnos puedan gestionar sus datos en el momento y lugar que deseen. Tales aplicaciones son instaladas y ejecutadas desde un pendrive brindándole al usuario portabilidad y compatibilidad con el entorno informático, además, el uso de ellas elimina las restricciones informáticas que impedían maximizar los beneficios de los sistemas de educación a distancia.