Security Network Authentication Service 7.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Rohos Disk Encryption Tutorial
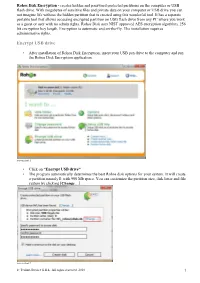
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Oregon Department of Forestry Equipment & Personnel Rate Guide 2019
Oregon Department of Forestry Equipment & Personnel Rate Guide 2019 Finance i Table of Contents Page Definitions 1 General Provisions 2 - 4 Payment Provisions 5 - 8 Responsibilities and Procedures 9 - 10 Forms, Filing System, and Supply 10 - 11 Emergency Personnel Rates 12 - 19 Heavy Equipment Rates 20 - 25 Water Handling Rates 26 - 27 Support Equipment Rates 27 - 28 Mileage and Hours Chart 29 - 32 Finance ii Definitions Administratively Determined (AD)/Emergency Hire Employee: An individual who is hired at the AD Wage Rate and paid directly by the Oregon Department of Forestry (ODF) when extra capacity is required to meet the objectives of an incident. Check-In Form: Required documentation that records resource information such as: resource order number, contact information, equipment type, and rate of pay. Required for contract crews, equipment, and overhead personnel. Must be signed by vendor/operator. District Business Manager (DBM): The ODF staff person responsible for all incident business related matters in each district. Previously titled Office Manager or OM. Guarantee: For each calendar day that heavy equipment is under hire, the amount earned for that day will be no less than 2.5 hours. OF 286: Summarized emergency equipment invoice. All time recorded on equipment shift tickets will be posted on this form. Signature is required for payment. OF 288: Summarized emergency personnel invoice. All time recorded on shift tickets will be posted on this form. Signature is required for payment. On Shift (Compensable) Time: Employees are compensated for on shift time. On shift time includes travel to and from the point of hire and/or other travel necessary for the performance of work (such as from base camp to fire line), actual hours worked, and time when an individual is held, by direction or ordered, to a specific location fully outfitted, and ready for assignment. -

Pacific Coast Steelhead Management Meeting
SUMMARY OF THE TWELFTH PACIFIC COAST STEELHEAD MANAGEMENT MEETING March 9-11, 2010 Eagle Crest Resort - Redmond, Oregon Sponsored by: Pacific States Marine Fisheries Commission & U.S. Fish and Wildlife Service TABLE OF CONTENTS I. SUMMARY……..…………………………………………………………………………...1 II. STEELHEAD STOCK STATUS REVIEW AND ESA……………………………….....3 A. California....................................................................................................................................... 3 B. Oregon ........................................................................................................................................... 4 C. Idaho .............................................................................................................................................. 4 D. Washington ................................................................................................................................... 5 E. Alaska ............................................................................................................................................ 6 F. Progress Report on Developing Viability Criteria for Threatened Puget Sound Steelhead -- Jeff Hard, NOAA Fisheries ....................................................................................... 7 III. REINTRODUCTION OF STEELHEAD ........................................................................8 A. Documenting Onchorhynchus mykiss Life Histories in Rattlesnake Creek and White Salmon River Prior to the Reintroduction of Anadromous Fish Above Condit -

Use of Passage Structures at Bonneville and John Day Dams by Pacific Lamprey, 2013 and 2014
Technical Report 2015-11-DRAFT USE OF PASSAGE STRUCTURES AT BONNEVILLE AND JOHN DAY DAMS BY PACIFIC LAMPREY, 2013 AND 2014 by M.A. Kirk, C.C. Caudill, C.J. Noyes, E.L. Johnson, S.R. Lee, and M.L. Keefer Department of Fish and Wildlife Sciences University of Idaho, Moscow, ID 83844-1136 and H. Zobott, J.C. Syms, R. Budwig, and D. Tonina Center for Ecohydraulics Research University of Idaho Boise, ID 83702 for U.S. Army Corps of Engineers Portland District 2015 Technical Report 2015-11-DRAFT USE OF PASSAGE STRUCTURES AT BONNEVILLE AND JOHN DAY DAMS BY PACIFIC LAMPREY, 2013 AND 2014 by M.A. Kirk, C.C. Caudill, C.J. Noyes, E.L. Johnson, S.R. Lee, and M.L. Keefer Department of Fish and Wildlife Sciences University of Idaho, Moscow, ID 83844-1136 and H. Zobott, J.C. Syms, R. Budwig, and D. Tonina Center for Ecohydraulics Research University of Idaho Boise, ID 83702 for U.S. Army Corps of Engineers Portland District 2015 i Acknowledgements This project was financed by the U.S. Army Corps of Engineers, Portland District and was facilitated by Sean Tackley. We would like to thank Andy Traylor, Brian Bissell, Ida Royer, Ben Hausman, Miro Zyndol, Dale Klindt and the additional project biologists at Bonneville and John Day dams who provided on-site support. We would like to thank Dan Joosten, Kaan Oral, Inga Aprans, Noah Hubbard, Mike Turner, Robert Escobar, Kate Abbott, Matt Dunkle, Chuck Boggs, Les Layng, and Jeff Garnett from the University of Idaho for assisting with the construction, maintenance, and field sampling associated with both Lamprey Passage Structures (LPSs). -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

Seasonal Life History of Oncorhynchus Mykiss in the South Fork John Day River Basin, Oregon
AN ABSTRACT OF THE THESIS OF Ian A. Tattam for the degree of Master of Science in Fisheries Science presented on December 22, 2006. Title: Seasonal Life History of Oncorhynchus mykiss in the South Fork John Day River Basin, Oregon Abstract approved: ______________________________________________ Hiram W. Li Understanding seasonal changes in growth, survival, and movement rates is crucial to salmonid management. These life history characteristics provide a context for evaluation of management actions. We evaluated the life history of individually marked Oncorhynchus mykiss gairdneri in the South Fork John Day River basin in Northeastern Oregon. This thesis focuses on Murderers and Black Canyon creeks, two tributaries to the South Fork John Day. These are semi-arid, mid elevation basins with naturally reproducing populations of summer steelhead and redband trout (both O. mykiss). Summer steelhead populations in this basin have declined from historic abundances, and are protected under the Endangered Species Act. In Chapter 2, we evaluate life history variation in Murderers Creek during four consecutive seasons. Growth rate varied significantly with season (F3,88 = 62.56, P < 0.0001), with most growth occurring during spring. Location and season interacted (F6,88 = 4.45, P < 0.001) to influence individual growth rates. As a result, regions of high growth potential shifted up and down-stream seasonally. However, we found low rates of O. mykiss movement (< 3 %) in Murderers Creek during summer, suggesting that individuals did not track resource availability at a large scale. Apparent survival rate varied among reaches, but was consistently higher in the upstream most reach compared to the two lowermost reaches. -

John Day Fossil Beds NM: Geology and Paleoenvironments of the Clarno Unit
John Day Fossil Beds NM: Geology and Paleoenvironments of the Clarno Unit JOHN DAY FOSSIL BEDS Geology and Paleoenvironments of the Clarno Unit John Day Fossil Beds National Monument, Oregon GEOLOGY AND PALEOENVIRONMENTS OF THE CLARNO UNIT John Day Fossil Beds National Monument, Oregon By Erick A. Bestland, PhD Erick Bestland and Associates, 1010 Monroe St., Eugene, OR 97402 Gregory J. Retallack, PhD Department of Geological Sciences University of Oregon Eugene, OR 7403-1272 June 28, 1994 Final Report NPS Contract CX-9000-1-10009 TABLE OF CONTENTS joda/bestland-retallack1/index.htm Last Updated: 21-Aug-2007 http://www.nps.gov/history/history/online_books/joda/bestland-retallack1/index.htm[4/18/2014 12:20:25 PM] John Day Fossil Beds NM: Geology and Paleoenvironments of the Clarno Unit (Table of Contents) JOHN DAY FOSSIL BEDS Geology and Paleoenvironments of the Clarno Unit John Day Fossil Beds National Monument, Oregon TABLE OF CONTENTS COVER ABSTRACT ACKNOWLEDGEMENTS CHAPTER I: INTRODUCTION AND REGIONAL GEOLOGY INTRODUCTION PREVIOUS WORK AND REGIONAL GEOLOGY Basement rocks Clarno Formation John Day Formation CHAPTER II: GEOLOGIC FRAMEWORK INTRODUCTION Stratigraphic nomenclature Radiometric age determinations CLARNO FORMATION LITHOSTRATIGRAPHIC UNITS Lower Clarno Formation units Main section JOHN DAY FORMATION LITHOSTRATIGRAPHIC UNITS Lower Big Basin Member Middle and upper Big Basin Member Turtle Cove Member GEOCHEMISTRY OF LAVA FLOW AND TUFF UNITS Basaltic lava flows Geochemistry of andesitic units Geochemistry of tuffs STRUCTURE OF CLARNO -

Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on Appimages and Atomic Upgrades by Nitrux Latinoamerican S.C
ModSecurity Globbing Edit PDFs and nginx and Regex with Xournal Since 1994: The original magazine of the Linux community Linux Gaming A Talk with Linux Game Developers | Review: Thrones of Britannia Two Portable DIY Retro Console Projects | Survey of Native Linux Games TASBot the Linux-Powered Robot Plays Games for Charity ISSUE 290 | SEPTEMBER 2018 www.linuxjournal.com SEPTEMBER 2018 CONTENTS ISSUE 290 86 DEEP DIVE: Gaming 87 Crossing Platforms: a Talk with the Developers Building Games for Linux By K.G. Orphanides Games for Linux are booming like never before. The revolution comes courtesy of cross-platform dev tools, passionate programmers and community support. 105 Would You Like to Play a Linux Game? By Marcel Gagné A look at several games native to Linux. 117 Meet TASBot, a Linux-Powered Robot Playing Video Games for Charity By Allan Cecil Can a Linux-powered robot play video games faster than you? Only if he . takes a hint from piano rolls...and the game for Linux in November 2016. Enix. Feral Interactive released and published by Square , developed by Eidos Montréal doesn’t desync. 135 Review: Thrones Shroud of the Avatar Shroud of Britannia Deus Ex: Mankind Divided By Marcel Gagné from from A look at the recent game from the Total War series on the Linux desktop Image from Portalarium’s Portalarium’s Image from thanks to Steam and Feral Interactive. Cover image 2 | September 2018 | http://www.linuxjournal.com CONTENTS 6 Letters UPFRONT 14 Clearing Out /boot By Adam McPartlan 17 VCs Are Investing Big into a New Cryptocurrency: Introducing Handshake By Petros Koutoupis 20 Edit PDFs with Xournal By Kyle Rankin 22 Patreon and Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on AppImages and Atomic Upgrades By Nitrux Latinoamerican S.C. -

Laplink® Pcmover® Business User Guide
Laplink® PCmover® Business The Only Software that Moves Programs, Files, and Settings to a New PC! User Guide Customer Service/Technical Support: Web: http://www.laplink.com/contact E-mail: [email protected] Tel (USA): +1 (425) 952-6001 Fax (USA): +1 (425) 952-6002 Tel (UK): +44 (0) 870-2410-983 Fax (UK): +44 (0) 870-2410-984 Laplink Software, Inc. 600 108th Ave. NE, Suite 610 Bellevue, WA 98004 U.S.A. Copyright / Trademark Notice © Copyright 2019 Laplink Software, Inc. All rights reserved. Laplink, the Laplink logo, Connect Your World, and PCmover are registered trademarks or trademarks of Laplink Software, Inc. in the United States and/or other countries. Other trademarks, product names, company names, and logos are the property of their respective holder(s). MN-PCMBUS-EN-11 (REV. 2019-9-19) Laplink PCmover Business is a business-class migration utility capable of automatically moving selected files, users, settings, and programs from an old PC to the new PC. Transferring a PC or laptop across a network, Laplink USB cable, Laplink Ethernet cable or using external media or storage can be as simple as a single click. Computers with multiple users have the option to transfer some or all the users at once, with security information about file ownership and access control preserved for each user. Common PCmover Migration Scenarios 1. Transfer a user from an old machine to a new machine with the same or newer Windows Operating System. 2. Upgrade a user’s machine to a newer version OS, including Windows 8 (32-bit and 64-bit). -

IMPORTANT! Files Saved to This USB Are NOT Automatically Encrypted
IMPORTANT! Files saved to this USB are NOT automatically encrypted. You must use the SecureLock II software interface to secure your files. SecureLock II™ User Manual Encryption Application for USB Flash Drives User Manual Version 1.0.0.3 © 2004-2012 Integral Memory plc Table of Contents Table of Contents ................................................................................................... 2 1. Introduction..................................................................................................... 3 2. System Requirements .................................................................................... 4 3. Working with SecureLock II ............................................................................ 5 3.1. Setting up SecureLock II ........................................................................ 5 3.2. Setting up a Password ........................................................................... 6 3.3. Password retries .................................................................................... 8 3.4. Display Settings ..................................................................................... 8 3.5. Using Drag & Drop to copy files ............................................................. 9 3.6. Opening and modifying files within SecureLock II ................................ 11 3.7. Security settings ................................................................................... 12 4. Safely Remove Hardware ...........................................................................