Openkode 1.0.2 Specification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GLSL 4.50 Spec
The OpenGL® Shading Language Language Version: 4.50 Document Revision: 7 09-May-2017 Editor: John Kessenich, Google Version 1.1 Authors: John Kessenich, Dave Baldwin, Randi Rost Copyright (c) 2008-2017 The Khronos Group Inc. All Rights Reserved. This specification is protected by copyright laws and contains material proprietary to the Khronos Group, Inc. It or any components may not be reproduced, republished, distributed, transmitted, displayed, broadcast, or otherwise exploited in any manner without the express prior written permission of Khronos Group. You may use this specification for implementing the functionality therein, without altering or removing any trademark, copyright or other notice from the specification, but the receipt or possession of this specification does not convey any rights to reproduce, disclose, or distribute its contents, or to manufacture, use, or sell anything that it may describe, in whole or in part. Khronos Group grants express permission to any current Promoter, Contributor or Adopter member of Khronos to copy and redistribute UNMODIFIED versions of this specification in any fashion, provided that NO CHARGE is made for the specification and the latest available update of the specification for any version of the API is used whenever possible. Such distributed specification may be reformatted AS LONG AS the contents of the specification are not changed in any way. The specification may be incorporated into a product that is sold as long as such product includes significant independent work developed by the seller. A link to the current version of this specification on the Khronos Group website should be included whenever possible with specification distributions. -
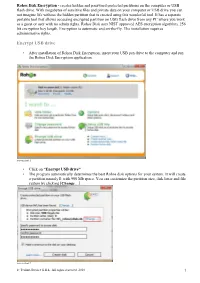
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

GLSL Specification
The OpenGL® Shading Language Language Version: 4.60 Document Revision: 3 23-Jul-2017 Editor: John Kessenich, Google Version 1.1 Authors: John Kessenich, Dave Baldwin, Randi Rost Copyright (c) 2008-2017 The Khronos Group Inc. All Rights Reserved. This specification is protected by copyright laws and contains material proprietary to the Khronos Group, Inc. It or any components may not be reproduced, republished, distributed, transmitted, displayed, broadcast, or otherwise exploited in any manner without the express prior written permission of Khronos Group. You may use this specification for implementing the functionality therein, without altering or removing any trademark, copyright or other notice from the specification, but the receipt or possession of this specification does not convey any rights to reproduce, disclose, or distribute its contents, or to manufacture, use, or sell anything that it may describe, in whole or in part. Khronos Group grants express permission to any current Promoter, Contributor or Adopter member of Khronos to copy and redistribute UNMODIFIED versions of this specification in any fashion, provided that NO CHARGE is made for the specification and the latest available update of the specification for any version of the API is used whenever possible. Such distributed specification may be reformatted AS LONG AS the contents of the specification are not changed in any way. The specification may be incorporated into a product that is sold as long as such product includes significant independent work developed by the seller. A link to the current version of this specification on the Khronos Group website should be included whenever possible with specification distributions. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

The Opencl Specification
The OpenCL Specification Version: 2.0 Document Revision: 22 Khronos OpenCL Working Group Editor: Aaftab Munshi Last Revision Date: 3/18/14 Page 1 1. INTRODUCTION ............................................................................................................... 10 2. GLOSSARY ......................................................................................................................... 12 3. THE OPENCL ARCHITECTURE .................................................................................... 23 3.1 Platform Model ................................................................................................................................ 23 3.2 Execution Model .............................................................................................................................. 25 3.2.1 Execution Model: Mapping work-items onto an NDRange ........................................................................28 3.2.2 Execution Model: Execution of kernel-instances ........................................................................................30 3.2.3 Execution Model: Device-side enqueue ......................................................................................................31 3.2.4 Execution Model: Synchronization .............................................................................................................32 3.2.5 Execution Model: Categories of Kernels ....................................................................................................33 3.3 Memory -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

Khronos Data Format Specification
Khronos Data Format Specification Andrew Garrard Version 1.3.1 2020-04-03 1 / 281 Khronos Data Format Specification License Information Copyright (C) 2014-2019 The Khronos Group Inc. All Rights Reserved. This specification is protected by copyright laws and contains material proprietary to the Khronos Group, Inc. It or any components may not be reproduced, republished, distributed, transmitted, displayed, broadcast, or otherwise exploited in any manner without the express prior written permission of Khronos Group. You may use this specification for implementing the functionality therein, without altering or removing any trademark, copyright or other notice from the specification, but the receipt or possession of this specification does not convey any rights to reproduce, disclose, or distribute its contents, or to manufacture, use, or sell anything that it may describe, in whole or in part. This version of the Data Format Specification is published and copyrighted by Khronos, but is not a Khronos ratified specification. Accordingly, it does not fall within the scope of the Khronos IP policy, except to the extent that sections of it are normatively referenced in ratified Khronos specifications. Such references incorporate the referenced sections into the ratified specifications, and bring those sections into the scope of the policy for those specifications. Khronos Group grants express permission to any current Promoter, Contributor or Adopter member of Khronos to copy and redistribute UNMODIFIED versions of this specification in any fashion, provided that NO CHARGE is made for the specification and the latest available update of the specification for any version of the API is used whenever possible. -

The Openvx™ Specification
The OpenVX™ Specification Version 1.0.1 Document Revision: r31169 Generated on Wed May 13 2015 08:41:43 Khronos Vision Working Group Editor: Susheel Gautam Editor: Erik Rainey Copyright ©2014 The Khronos Group Inc. i Copyright ©2014 The Khronos Group Inc. All Rights Reserved. This specification is protected by copyright laws and contains material proprietary to the Khronos Group, Inc. It or any components may not be reproduced, republished, distributed, transmitted, displayed, broadcast or otherwise exploited in any manner without the express prior written permission of Khronos Group. You may use this specifica- tion for implementing the functionality therein, without altering or removing any trademark, copyright or other notice from the specification, but the receipt or possession of this specification does not convey any rights to reproduce, disclose, or distribute its contents, or to manufacture, use, or sell anything that it may describe, in whole or in part. Khronos Group grants express permission to any current Promoter, Contributor or Adopter member of Khronos to copy and redistribute UNMODIFIED versions of this specification in any fashion, provided that NO CHARGE is made for the specification and the latest available update of the specification for any version of the API is used whenever possible. Such distributed specification may be re-formatted AS LONG AS the contents of the specifi- cation are not changed in any way. The specification may be incorporated into a product that is sold as long as such product includes significant independent work developed by the seller. A link to the current version of this specification on the Khronos Group web-site should be included whenever possible with specification distributions. -

Digital Asset Exchange
DDiiggiittaall AAsssseett EExxcchhaannggee Dr. Rémi Arnaud Sony Computer Entertainment Khronos Group Promoter © Copyright Khronos Group, 2007 - Page 1 •www.khronos.org •Founded in January 2000 by a number of leading media-centric companies, including: 3Dlabs, ATI, Discreet, Evans & Sutherland, Intel, NVIDIA, SGI and Sun Microsystems. (currently more than 100) •Dedicated to the creation of royalty-free open standard APIs to enable the playback of rich media on a wide variety of platforms and devices. •Home of 11 WG, including: OpenGL, OpenGL ES, OpenVG, OpenKODE, OpenSL, COLLADA •New WG introduced at GDC: glFX, Compositing © Copyright Khronos Group, 2007 - Page 2 CCOOLLLLAADDAA aass aa SSCCEE pprroojjeecctt •SCE project, started in August 2003 - Goal: raise the quality and productivity of content development - free the content from proprietary formats and API, bring more tools to game developers, lower the barrier to entry for small tool companies, facilitate middleware integration, bring ‘advanced’ features in the main stream, drastically improve artist productivity. •Common description language - Developers get the content in a standard form - Tools can interchange content - Developers can mix and match tools during development - Many specialized tools can be independently created, and incorporated into developer’s content pipeline •COLLAborative Design Activity, SCE brought to the same table the major DCC vendors: Discreet, Alias, Softimage •Released v1.0 specification in August 2004 •Gathered feedback, waiting for tools to provide useful -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

The Openvx™ Specification
The OpenVX™ Specification Version 1.2 Document Revision: dba1aa3 Generated on Wed Oct 11 2017 20:00:10 Khronos Vision Working Group Editor: Stephen Ramm Copyright ©2016-2017 The Khronos Group Inc. i Copyright ©2016-2017 The Khronos Group Inc. All Rights Reserved. This specification is protected by copyright laws and contains material proprietary to the Khronos Group, Inc. It or any components may not be reproduced, republished, distributed, transmitted, displayed, broadcast or otherwise exploited in any manner without the express prior written permission of Khronos Group. You may use this specifica- tion for implementing the functionality therein, without altering or removing any trademark, copyright or other notice from the specification, but the receipt or possession of this specification does not convey any rights to reproduce, disclose, or distribute its contents, or to manufacture, use, or sell anything that it may describe, in whole or in part. Khronos Group grants express permission to any current Promoter, Contributor or Adopter member of Khronos to copy and redistribute UNMODIFIED versions of this specification in any fashion, provided that NO CHARGE is made for the specification and the latest available update of the specification for any version of the API is used whenever possible. Such distributed specification may be re-formatted AS LONG AS the contents of the specifi- cation are not changed in any way. The specification may be incorporated into a product that is sold as long as such product includes significant independent work developed by the seller. A link to the current version of this specification on the Khronos Group web-site should be included whenever possible with specification distributions. -

모바일 그래픽스 라이브러리들: 크로노스 그룹의 표준을 중심으로 Mobile Graphics Libraries: Focusing on the Standards from Khronos Group
50 한국콘텐츠학회 제8권 제2호 모바일 그래픽스 라이브러리들: 크로노스 그룹의 표준을 중심으로 Mobile Graphics Libraries: focusing on the standards from Khronos Group 백낙훈 (경북대학교), 이환용 (㈜휴원 CTO, 경북대학교 박사과정) 차 례 1. 서론 2. OpenGL ES 3. OpenGL SC 4. OpenVG 5. 결론 1. 서론 전력 소모가 낮은 기기를 채택할 수 밖에 없는 것이다. 액정뿐만 아니라, 모든 컴퓨팅 자원들이 궁극적으로 전 컴퓨터는 그 출현 이후, 계속해서 그 크기를 줄여 왔고, 력 문제에 민감하여야 하고, 이 때문에, 제한된 기능만을 현재는 휴대폰, 네비게이터, 휴대용 게임기 등의 형태로 제공할 수 밖에 없는 상황이다. 모바일 컴퓨팅 환경을 제공하고 있다. 모바일 컴퓨팅 환 경의 대두와 함께, 이를 이용한 그래픽스 출력이 요구되 었고, 모바일 환경에서의 그래픽스 기능을 의미하는, 모 바일 그래픽스 환경이 구축되었다. 이 글에서는 현재의 모바일 그래픽스 환경 중에서도 특히 표준 라이브러리들 에 대해 이야기하고자 한다. 지난 10여년 사이에 모바일 그래픽스 분야는 눈부신 발전을 이루었다. 가장 대표적 인 기기인 휴대폰을 기준으로 본다면, 최초에 나온, 저해 상도에 흑백의 투박한 액정을 가진 모델이 불과 몇 년 사 이에 상당한 수준의 컬러 액정을 가진 제품으로 변했고, 3차원 그래픽스를 지원하는 특별한 하드웨어 칩들을 사 (a) 저해상도 2D (b) 3D 용하는 것도 이상하지 않은 상황이 되었다. 이에 따라, 소프트웨어 기술들도 눈부시게 발전하여, 그림 1에서 보 는 바와 같이, 2차원 저해상도에서 3차원 화면을 거쳐, 거의 PC 화면에 필적하는 수준의 고해상도 3차원 화면 이 급속히 사용되고 있다. 모바일 그래픽스 환경은 태생 상, 기존의 데스크 탑 또는 그 이상의 고급 기종들에 비 해, 상대적으로 열등한 하드웨어 환경을 제공할 수 밖에 없다. 가장 문제가 되는 것은 제한된 용량의 전원, 즉 배 터리의 수명을 고려해야 한다는 점이다. PC급의 고해상 (c) 하드웨어로 가속되는 3D 도 액정이 기술적으로 문제가 있는 것이 아니라, 채택하 ▶▶ 그림 1.