Secured On-The-Go™ - Flash Padlock with Portable Applications White Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2010 Survey Results
IT SERVICES 2010 Client Satisfaction Survey March, 2010 Acknowledgements The Stanford IT Services Client Satisfaction Team consisted of the following: Jan Cicero, Client Support Alvin Chew, Communication Services Liz Goesseringer, Business Services Tom Goodrich, Client Support Jim Knox, Facilitator, Client Support Phil Reese, Research Computing Nancy Ware, Strategic Planning Bryan Wear, Computing Services Brian McDonald, MOR Associates Chris Paquette, MOR Associates Alexis Bywater, MOR Associates MOR Associates, an external consulting firm, acted as project manager for this effort, analyzing the data and preparing this report. MOR Associates specializes in continuous improvement, strategic thinking and leadership development. MOR Associates has conducted a number of large-scale satisfaction surveys for IT organizations in higher education, including MIT, Northeastern University, the University of Chicago, and others. MOR Associates, Inc. 462 Main Street, Suite 300 Watertown, MA 02472 tel: 617.924.4501 fax: 617.924.8070 morassociates.com Brian McDonald, President [email protected] Contents Introduction. a1 Methodology . a2 Overview.of.the.Results . 1 Reading.the.Charts. 25 Customer.Service.and.Service.Attributes. 29 Research.Computing.and.IT.Services.Priorities. .33 General.Support. .41 Data.Storage.Services .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. ..51 Email.and.Webmail. 59 Calendaring. 63 Network.Services. 67 Telecommunications.Services. 73 Remote.Access . 83 Mobile.Devices . 87 Software. .89 Security. 93 Web.Services. 99 Appendix.A:.The.Full.Text.of.Written.Comments. .A-1 Appendix.B:.The.Survey.Instrument. B-. 1 Appendix.C:.Other.Observations . .C-1 Stanford Information Technology Services 2010 Client Survey • Introduction | a1 Introduction This report provides a summary of the purposes, the methodology and the results of the client satisfaction survey sponsored by Stanford Information Technology Services in March, 2010. -
Rohos Disk Encryption Tutorial
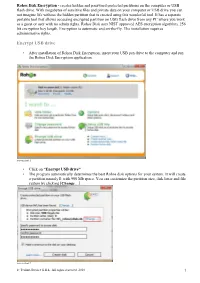
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Mailsite Fusion SP 10
DATA SHEET ® MailSite Fusion SP 10 MailSite WHAT IS IT? Fusion is a low MailSite Fusion is a messaging and cost collaboration server that delivers email, calendars and contacts to Microsoft Outlook. alternative to MailSite Fusion also pushes email, calendars Hosted and contacts over-the-air to iPhone, iPad, WHAT’S NEW? Exchange that BlackBerry, Android, Windows and Nokia delivers email, smartphones. MailSite has been voted among MailSite Fusion comes bundled with a new Sync Server calendars and the top 3 mail server products by readers of that provides full support for Microsoft Outlook 2013 Windows IT Pro Magazine four times. contacts to for email, calendar and contacts. MailSite Sync Server allows you to sync multiple mobile devices with the same Microsoft HOW IS IT DIFFERENT FROM HOSTED email account, allowing you to give all your sales team Outlook, EXCHANGE? access to the sales inbox. iPhone, iPad, MailSite Fusion can scale to millions of BlackBerry, subscribers on a fully active cluster of low cost FEATURES servers. MailSite Fusion costs less than 50% of Android, Email, calendar and contact server that works great the price of Microsoft Exchange and MailSite Windows and with Microsoft Outlook Fusion can run on low cost hardware. Shared calendar server that works with Microsoft Nokia Outlook, Google Calendar, Apple iCal and Mozilla Users can access the same email, calendars smartphones Sunbird and contacts from their desktop, a web browser Customizable AJAX Web Client that works with or on the road from whichever smartphone they -

Leveraging Open Source Software
1 Leveraging Open Source Software (Text of talk delivered by Justice Yatindra Singh Judge Allahabad High Court at the 9th e- Governance conference on 3rd February 2006 at Kochi, Kerala) FUD is an abbreviation of fear, uncertainty and doubt; it is often a salesman's strategy: spreading false rumours regarding others' products. Open source software (OSS) is its victim. In our country FUD for OSS arises out of ignorance. I am glad that, we are discussing OSS as it has crucial role to play in the IT world. WHAT IS OSS? A computer programme consists of two parts: Source Code and Object Code. Nowadays, computer programmes are written in high level computer languages using compact English words. This part is known as source code. These languages also have a programme called compiler and with their help, source code is compiled into machine language so that computers may understand it. When it is so done, it is called object code or machine code. Description―if it complies with certain conditions―is protected as a Copyright. Source code is a kind of description and can be protected as copyright provided it is published or disclosed. In the proprietery software, source code is generally not disclosed and in such a situation it is protected as a trade secret or undisclosed information. There was a debate whether object code is protected as a copyright or not but after TRIPS, it has to be protected as a copyright and now object code is so protected. Everyone is not using copyrights to have rights in computer programme. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

Mozilla Sunbird Le Calendrier
Mozilla Sunbird le calendrier Installation de Sunbird Dernière version traduite : SunbirdFr 0.2 finale http://frenchmozilla.sourceforge.net/calendar/#sunbird Version Windows (20/2/2005) Attention! avant d'installer la version Windows de SunbirdFr , veuillez désinstaller l'ancienne version et n'oubliez pas de supprimer également le dossier profil nommé Sunbird : • Sur Windows XP dans C:\Documents and Settings\nom utilisateur\Application Data\Mozilla ; • sur Windows 9x dans C:\Windows\Application Data\Mozilla. Si vous souhaitez conserver votre (vos) calendrier(s) veuillez sauvegarder le(s) fichier(s) *.ics se trouvant dans le dossier ...\Application Data \Mozilla \Sunbird \Profiles \xxxxxx.default \Calendar puis, après installation de la nouvelle version de SunbirdFr, replacez-les dans ce dossier. Démarrez SunbirdFr, et dans l'onglet Calendriers clic droit puis Nouveau calendrier. Recherchez le(s) fichier(s) *.ics que vous venez de replacer dans l'arborescence, sélectionnez- les l'un après l'autre et validez (même si une boîte vous signale que le fichier existe déjà !). Fichiers à télécharger au choix • Fichier *.exe (setup) permettant une installation simplifiée et personnalisable : Installeur (4,43 Mo) • Fichier *.zip à décompresser dans le dossier Program Files : Archive (5,45 Mo) Version Linux (20/2/2005) • l inuxGTK2+XFT (ne fonctionne pas avec 2.6 à moins de repasser à la version 2.4 ou inférieure, information donnée par Merinos) • l inuxGTK1 Version Mac OSX(20/2/2005) • i ci Patch affichage des mois (7/03/2005) Pour résoudre le problème d'affichage des mois de mars à août, veuillez télécharger le fichier calendar.jar (2 Mo) et le placer dans le dossier C:\Program Files\sunbird\chrome (acceptez l'écrasement du fichier en place). -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

WIKI on ACCESSIBILITY Completion Report March 2010
WIKI ON ACCESSIBILITY Completion report March 2010 By Nirmita Narasimhan Programme Manager Centre for Internet and Society Project Title: Wiki on “Accessibility, Disability and the Internet in India” Page | 1 REPORT Accessibility wiki: accessibility.cis-india.org The wiki project was envisaged and funded by the National Internet Exchange of India (www.nixi.in) and has been executed by the Centre for Internet and Society (www.cis-india.org), Bangalore. Project Start date: May 2009 End date: February 2010. Background India has a large percentage of disabled persons in its population— estimated to be over seven per cent as per the Census of 2001. Even this figure is believed to be a gross under representation of the total number of disabled persons residing in this large and diverse country. Taken in figures, this amounts to roughly 70-100 million persons with disabilities in the territory of India. Out of this number, a mere two per cent residing in urban areas have access to information and assistive technologies which enable them to function in society and enhance their performance. There are several reasons for this, one of them being that there is a deplorable lack of awareness which exists on the kinds of disabilities and about ways in which one can provide information and services to disabled persons. Parents, teachers, government authorities and society at large are all equally unaware about the options which exist in technology today to enable persons with disabilities to carry on independent and productive lives. Barring a few exceptions, India is still trapped in an era where a white cane and a Braille slate symbolises the future for blind people, while the world has progressed to newer forms of enabling technology such as screen readers, daisy players, the Kindle and so on. -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines. -

FOSS:Fostering Knowledge, Development and Communities
f r e e . a n d . o p e n . s o u r c e . community& n . s o u r c e . s o f t w a r e . independentmedia w a r e . f r e e . a n d . o p e n . s FOSS: Fostering a n d . o p e n . s o u r c e . s o Knowledge, e . f r e e . a n d . o p e n . s o f t w a r e . fff r e e . a n d . Development e n . s ooo u r c e . s o f t w a fff r e e . a n d . and Comme . sss ooounities u r c e . s o f t w a by Precy Obja-an n d . ooo p e n . s ooo u r c e . s o f t w a People’s Communications for Development (PC4D) may not have found new information and communications technologies empowering for grassroots women, owing to the practical constraints of equipment cost, intermittent electricity, and specialised skills and the structural constraints posed by the patriarchy project. But new ICTs are here to stay, forming the very backbone of modern communication systems, media production, trade and various services. And for intermediary groups such as women’s organisations, they are among the effective ways of pursuing advocacies and reaching out to more stakeholders. As the study noted, “[PC4D] does not ICTs have been seen as an opportunity signify that new ICTs cannot be useful in forwarding private interest, especially or empowering for grassroots women in the spirit of neoliberalism. -

Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on Appimages and Atomic Upgrades by Nitrux Latinoamerican S.C
ModSecurity Globbing Edit PDFs and nginx and Regex with Xournal Since 1994: The original magazine of the Linux community Linux Gaming A Talk with Linux Game Developers | Review: Thrones of Britannia Two Portable DIY Retro Console Projects | Survey of Native Linux Games TASBot the Linux-Powered Robot Plays Games for Charity ISSUE 290 | SEPTEMBER 2018 www.linuxjournal.com SEPTEMBER 2018 CONTENTS ISSUE 290 86 DEEP DIVE: Gaming 87 Crossing Platforms: a Talk with the Developers Building Games for Linux By K.G. Orphanides Games for Linux are booming like never before. The revolution comes courtesy of cross-platform dev tools, passionate programmers and community support. 105 Would You Like to Play a Linux Game? By Marcel Gagné A look at several games native to Linux. 117 Meet TASBot, a Linux-Powered Robot Playing Video Games for Charity By Allan Cecil Can a Linux-powered robot play video games faster than you? Only if he . takes a hint from piano rolls...and the game for Linux in November 2016. Enix. Feral Interactive released and published by Square , developed by Eidos Montréal doesn’t desync. 135 Review: Thrones Shroud of the Avatar Shroud of Britannia Deus Ex: Mankind Divided By Marcel Gagné from from A look at the recent game from the Total War series on the Linux desktop Image from Portalarium’s Portalarium’s Image from thanks to Steam and Feral Interactive. Cover image 2 | September 2018 | http://www.linuxjournal.com CONTENTS 6 Letters UPFRONT 14 Clearing Out /boot By Adam McPartlan 17 VCs Are Investing Big into a New Cryptocurrency: Introducing Handshake By Petros Koutoupis 20 Edit PDFs with Xournal By Kyle Rankin 22 Patreon and Linux Journal 23 FOSS Project Spotlight: Nitrux, a Linux Distribution with a Focus on AppImages and Atomic Upgrades By Nitrux Latinoamerican S.C. -

Laplink® Pcmover® Business User Guide
Laplink® PCmover® Business The Only Software that Moves Programs, Files, and Settings to a New PC! User Guide Customer Service/Technical Support: Web: http://www.laplink.com/contact E-mail: [email protected] Tel (USA): +1 (425) 952-6001 Fax (USA): +1 (425) 952-6002 Tel (UK): +44 (0) 870-2410-983 Fax (UK): +44 (0) 870-2410-984 Laplink Software, Inc. 600 108th Ave. NE, Suite 610 Bellevue, WA 98004 U.S.A. Copyright / Trademark Notice © Copyright 2019 Laplink Software, Inc. All rights reserved. Laplink, the Laplink logo, Connect Your World, and PCmover are registered trademarks or trademarks of Laplink Software, Inc. in the United States and/or other countries. Other trademarks, product names, company names, and logos are the property of their respective holder(s). MN-PCMBUS-EN-11 (REV. 2019-9-19) Laplink PCmover Business is a business-class migration utility capable of automatically moving selected files, users, settings, and programs from an old PC to the new PC. Transferring a PC or laptop across a network, Laplink USB cable, Laplink Ethernet cable or using external media or storage can be as simple as a single click. Computers with multiple users have the option to transfer some or all the users at once, with security information about file ownership and access control preserved for each user. Common PCmover Migration Scenarios 1. Transfer a user from an old machine to a new machine with the same or newer Windows Operating System. 2. Upgrade a user’s machine to a newer version OS, including Windows 8 (32-bit and 64-bit).