PRISM Vol. 2 No 4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Somalia's Insurgents Embrace Twitter As a Weapon
Nxxx,2011-12-15,A,010,Bs-BW,E1 A10 N THE NEW YORK TIMES INTERNATIONAL THURSDAY, DECEMBER 15, 2011 Somalia’s Insurgents EmbraceTHURSDAY, Twitter DECEMBER 15, 2011 as a Weapon By JEFFREY GETTLEMAN NAIROBI, Kenya — Think of it as the Battle of the Tweets. Somalia’s powerful Islamist in- surgents, the Shabab, best known for chopping off hands and starv- ing their own people, just opened a Twitter account, and in the past week they have been writing up a storm, bragging about recent at- tacks and taunting their enemies. “Your inexperienced boys flee from confrontation & flinch in the face of death,” the Shabab wrote in a post to the Kenyan Army. It is an odd, almost downright hypocritical move from brutal militants in one of world’s most broken-down countries, where millions of people do not have enough food to eat, let alone a laptop. The Shabab have vehe- mently rejected Western prac- tices — banning Western music, movies, haircuts and bras, and even blocking Western aid for famine victims, all in the name of their brand of puritanical Islam — only to embrace Twitter, one of the icons of a modern, networked society. On top of that, the Shabab MOHAMED SHEIKH NOR/ASSOCIATED PRESS clearly have their hands full right The Shabab’s fighters are waging a war against Somalia’s interim government and peacekeepers. now, facing thousands of African Union peacekeepers, the Kenyan bab wrote. “Sure your comments lost only 10. African Union offi- statements. He added that the military, the Ethiopian military will invite derision but try to cials later conceded that the Sha- carefully composed e-mails and and the occasional American muster (or feign) courage at bab had been correct. -

Citizen Cyborg.” Citizen a Groundbreaking Work of Social Commentary, Citizen Cyborg Artificial Intelligence, Nanotechnology, and Genetic Engineering —DR
hughes (continued from front flap) $26.95 US ADVANCE PRAISE FOR ARTIFICIAL INTELLIGENCE NANOTECHNOLOGY GENETIC ENGINEERING MEDICAL ETHICS INVITRO FERTILIZATION STEM-CELL RESEARCH $37.95 CAN citizen LIFE EXTENSION GENETIC PATENTS HUMAN GENETIC ENGINEERING CLONING SEX SELECTION ASSISTED SUICIDE UNIVERSAL HEALTHCARE human genetic engineering, sex selection, drugs, and assisted In the next fifty years, life spans will extend well beyond a century. suicide—and concludes with a concrete political agenda for pro- cyborg Our senses and cognition will be enhanced. We will have greater technology progressives, including expanding and deepening control over our emotions and memory. Our bodies and brains “A challenging and provocative look at the intersection of human self-modification and human rights, reforming genetic patent laws, and providing SOCIETIES MUST RESPOND TO THE REDESIGNED HUMAN OF FUTURE WHY DEMOCRATIC will be surrounded by and merged with computer power. The limits political governance. Everyone wondering how society will be able to handle the coming citizen everyone with healthcare and a basic guaranteed income. of the human body will be transcended, as technologies such as possibilities of A.I. and genomics should read Citizen Cyborg.” citizen A groundbreaking work of social commentary, Citizen Cyborg artificial intelligence, nanotechnology, and genetic engineering —DR. GREGORY STOCK, author of Redesigning Humans illuminates the technologies that are pushing the boundaries of converge and accelerate. With them, we will redesign ourselves and humanness—and the debate that may determine the future of the our children into varieties of posthumanity. “A powerful indictment of the anti-rationalist attitudes that are dominating our national human race itself. -

Pakistan-U.S. Relations
Pakistan-U.S. Relations K. Alan Kronstadt Specialist in South Asian Affairs July 1, 2009 Congressional Research Service 7-5700 www.crs.gov RL33498 CRS Report for Congress Prepared for Members and Committees of Congress Pakistan-U.S. Relations Summary A stable, democratic, prosperous Pakistan actively combating religious militancy is considered vital to U.S. interests. U.S. concerns regarding Pakistan include regional and global terrorism; Afghan stability; democratization and human rights protection; the ongoing Kashmir problem and Pakistan-India tensions; and economic development. A U.S.-Pakistan relationship marked by periods of both cooperation and discord was transformed by the September 2001 terrorist attacks on the United States and the ensuing enlistment of Pakistan as a key ally in U.S.-led counterterrorism efforts. Top U.S. officials praise Pakistan for its ongoing cooperation, although long-held doubts exist about Islamabad’s commitment to some core U.S. interests. Pakistan is identified as a base for terrorist groups and their supporters operating in Kashmir, India, and Afghanistan. Pakistan’s army has conducted unprecedented and, until recently, largely ineffectual counterinsurgency operations in the country’s western tribal areas, where Al Qaeda operatives and pro-Taliban militants are said to enjoy “safe haven.” U.S. officials increasingly are concerned that indigenous religious extremists represent a serious threat to the stability of the Pakistani state. The United States strongly encourages maintenance of a bilateral cease-fire and a continuation of substantive dialogue between Pakistan and neighboring India, which have fought three wars since 1947. A perceived Pakistan-India nuclear arms race has been the focus of U.S. -

Fort Leavenworth Ethics Symposium
Fort Leavenworth Ethics Symposium Ethical and Legal Issues in Contemporary Conflict Symposium Proceedings Frontier Conference Center Fort Leavenworth, Kansas November 16-18, 2009 Edited by Mark H. Wiggins and Ted Ihrke Co-sponsored by the U.S. Army Command and General Staff College and the Command and General Staff College Foundation, Inc. Special thanks to our key corporate sponsor Other supporting sponsors include: Published by the CGSC Foundation Press 100 Stimson Ave., Suite 1149 Fort Leavenworth, Kansas 66027 Copyright © 2010 by CGSC Foundation, Inc. All rights reserved. www.cgscfoundation.org Papers included in this symposium proceedings book were originally submitted by military officers and other subject matter experts to the U.S. Army Command and General Staff College at Fort Leavenworth, Kansas. The CGSC Foundation/CGSC Foundation Press makes no claim to the authors’ copyrights for their individual work. ISBN 978-0-615-36738-5 Layout and design by Mark H. Wiggins MHW Public Relations and Communications Printed in the United States of America by Allen Press, Lawrence, Kansas iv Contents Acknowledgements ...................................................................................................................... ix Foreword by Brig. Gen. Ed Cardon, Deputy Commandant, CGSC & Col. (Ret.) Bob Ulin, CEO, CGSC Foundation ......................................................................... xi Symposium Participants ............................................................................................................ -

Countering Terrorism in East Africa: the U.S
Countering Terrorism in East Africa: The U.S. Response Lauren Ploch Analyst in African Affairs November 3, 2010 Congressional Research Service 7-5700 www.crs.gov R41473 CRS Report for Congress Prepared for Members and Committees of Congress Countering Terrorism in East Africa: The U.S. Response Summary The United States government has implemented a range of programs to counter violent extremist threats in East Africa in response to Al Qaeda’s bombing of the U.S. embassies in Tanzania and Kenya in 1998 and subsequent transnational terrorist activity in the region. These programs include regional and bilateral efforts, both military and civilian. The programs seek to build regional intelligence, military, law enforcement, and judicial capacities; strengthen aviation, port, and border security; stem the flow of terrorist financing; and counter the spread of extremist ideologies. Current U.S.-led regional counterterrorism efforts include the State Department’s East Africa Regional Strategic Initiative (EARSI) and the U.S. military’s Combined Joint Task Force – Horn of Africa (CJTF-HOA), part of U.S. Africa Command (AFRICOM). The United States has also provided significant assistance in support of the African Union’s (AU) peace operations in Somalia, where the country’s nascent security forces and AU peacekeepers face a complex insurgency waged by, among others, Al Shabaab, a local group linked to Al Qaeda that often resorts to terrorist tactics. The State Department reports that both Al Qaeda and Al Shabaab pose serious terrorist threats to the United States and U.S. interests in the region. Evidence of linkages between Al Shabaab and Al Qaeda in the Arabian Peninsula, across the Gulf of Aden in Yemen, highlight another regional dimension of the threat posed by violent extremists in the area. -

Pakistan in the Danger Zone a Tenuous U.S
Pakistan in the Danger Zone A Tenuous U.S. – Pakistan Relationship Shuja Nawaz The Atlantic Council promotes constructive U.S. leadership and engagement in international affairs based on the central role of the Atlantic community in meeting the international challenges of the 21st century. The Council embodies a non-partisan network of leaders who aim to bring ideas to power and to give power to ideas by: 7 stimulating dialogue and discussion about critical international issues with a view to enriching public debate and promoting consensus on appropriate responses in the Administration, the Congress, the corporate and nonprofit sectors, and the media in the United States and among leaders in Europe, Asia, Africa and the Americas; 7 conducting educational and exchange programs for successor generations of U.S. leaders so that they will come to value U.S. international engagement and have the knowledge and understanding necessary to develop effective policies. Through its diverse networks, the Council builds broad constituencies to support constructive U.S. leadership and policies. Its program offices publish informational analyses, convene conferences among current and/or future leaders, and contribute to the public debate in order to integrate the views of knowledgeable individuals from a wide variety of backgrounds, interests, and experiences. The South Asia Center is the Atlantic Council’s focal point for work on Afghanistan, Pakistan, India, Bangladesh, Sri Lanka, Nepal and Bhutan as well as on relations between these countries and China, Central Asia, Iran, the Arab world, Europe and the U.S. As part of the Council’s Asia program, the Center seeks to foster partnerships with key institutions in the region to establish itself as a forum for dialogue between decision makers in South Asia, the U.S. -
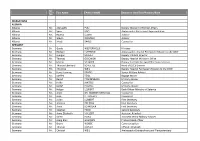
Mr. Ms. First Name FAMILY NAME Section Or Unit/Title/Position/Rank
Mr. First Name FAMILY NAME Section or Unit/Title/Position/Rank Ms. DELEGATIONS ALBANIA Albania Mr. Alqiviadhi PULI Deputy Minister of Foreign Affairs Albania Mr. Spiro KOÇI Ambassador, Permanent Representative Albania Ms. Ravesa LLESHI Advisor Albania Mr. Glevin DERVISHI Advisor Albania Mr. Xhodi SAKIQI Counsellor GERMANY Germany Dr. Guido WESTERWELLE Minister Germany Mr. Rüdiger LÜDEKING Ambassador, Head of Permanent Mission to the OSCE Germany Mr. Juergen SCHULZ Deputy Political Director Germany Mr. Thomas OSSOWSKI Deputy Head of Minister’s Office Germany Mr. Martin SCHÄFER Deputy Federale Foreign Office Spokesperson Germany Mr. Thomas Eberhard SCHULTZE Head of OSCE Division Germany Ms. Christine WEIL Deputy Head of Permanent Mission to the OSCE Germany Mr. Hans-Henning PRADEL Senior Military Adviser Germany Mr. Steffen FEIGL Bagage Master Germany Mr. Bernd PFAFFENBACH Military Adviser Germany Ms. Heike JANTSCH Counsellor Germany Mr. Detlef HEMPEL Military Adviser Germany Mr. Holger LEUKERT Desk Officer Ministry of Defence Germany Ms. Anne DR. WAGNER-MITCHELL Counsellor Germany Mr. Jean P. FROEHLY Counsellor Germany Mr. Julian LÜBBERT First Secretary Germany Ms. Annette PÖLKING First Secretary Germany Mr. Anna SCHRÖDER First Secretary Germany Mr. Stephan FAGO Second Secretary Germany Ms. Anna-Elisabeth VOLLERT Assistant Attacheé Germany Mr. Sören HEINE Assistent Senior Military Adviser Germany Mr. Joerg Emil GAUDIAN Protocol desk officer Germany Mr. Bruno WOBBE Communication Germany Mr. Thomas KÖHLER Official Fotograph Germany Mr. Christof WEIL Ambassador Extraordinary and Plenipotentiary Germany Ms. Anka FELDHUSEN Minister Counsellor and Deputy Head of Mission Germany Ms. Daniela BERGELT First Secretary Germany Mr. Christopher FUCHS First Secretary Germany Ms. Tanja BEYER First Secretary Germany Mr. -

Developing Countries in World Politics
IR 344: Developing Countries in World Politics Fall 2010 WPH B28 School of International Relations University of Southern California Tuesday and Thursday, 9:30-10:50AM Instructor: Dr. Eric Blanchard SOS 268 [email protected] (213) 740-2554 Office Hours: Wednesday 5-6PM, Thursday 11AM-1PM, and by appointment I. Course Description, Objectives and Requirements: “Developing Countries in World Politics” is a course that blends history and theory to help students (as future policymakers, scholars or informed citizens) better understand the politics of the developing world and the role of the United States in these politics. In other words, students will become familiar with the impact of U.S. involvement in the developing world, and the role this involvement played in constituting the American ascendency. We will engage in a historically grounded survey of the politics of developing countries in Asia, Africa, Latin America and the Caribbean, and the Middle East, developing an understanding of the particular issues faced in these countries such as underdevelopment, poverty, debt, religious and ethnic conflict, and climate change. In addition, we will pay close attention to the successes and failures of attempts on the part of Third World to organize outside of the Cold War system dominated by the most powerful states. Along the way, we will also consider the strengths and weaknesses of theories of International Relations, political science and sociology for understanding the developing world or global “South” and its relations with the advanced -

Religious Studies 1.800.405.1619/Yalebooks.Com
2019 RELIGIOUS STUDIES 1.800.405.1619/yalebooks.com Radical Sacrifice Restless Secularism TERRY EAGLETON Modernism and the Religious Inheritance Terry Eagleton pursues the concept of MATTHEW MUTTER sacrifice through the history of human Through a study of Wallace Stevens, thought, from antiquity to modernity, in Virginia Woolf, and other major writers, religion, politics, and literature. He sheds this thoughtful and provocative survey skewed perceptions of the idea, honing in of modernist literature explores how on a radical structural reconception that modernism understood the far-reaching relates the ancient world to our own in consequences of secularism for key fields terms of civilization and violence. of experience: language, aesthetics, Hardcover 2018 216 pp. emotion, and material life. 978-0-300-23335-3 $25.00 HC - Paper over Board 2017 336 pp. 978-0-300-22173-2 $85.00 & The New Cosmic Story Inside Our Awakening Universe & Before Religion JOHN F. HAUGHT A History of a Modern Concept In this inviting and thought-provoking BRENT NONGBRI book a foremost thinker on the intersec- Examining a wide array of ancient tion of science and religion argues that writings, Nongbri demonstrates that in an adequate understanding of cosmic antiquity, there was no conceptual arena history cannot be based on science that could be designated as “religious” alone. It must also take into account as opposed to “secular.” Surveying the implications of the awakening of representative episodes from a two- interiority and religious awareness. thousand-year period, Nongbri offers Hardcover 2017 240 pp. a concise and readable account of the 978-0-300-21703-2 $25.00 emergence of the concept of religion. -

Expertise and Democracy
Expertise and Democracy Cathrine Holst (ed.) ARENA Report No 1/14 Expertise and democracy Cathrine Holst (ed.) Copyright ARENA and authors ISBN (print) 978-82-93137-45-0 ISBN (online) 978-82-93137-95-5 ARENA Report Series (print) | ISSN 0807-3139 ARENA Report Series (online) | ISSN 1504-8152 Printed at ARENA Centre for European Studies University of Oslo P.O. Box 1143, Blindern N-0318 Oslo, Norway Tel: + 47 22 85 87 00 Fax: + 47 22 85 87 10 E-mail: [email protected] http://www.arena.uio.no Oslo, February 2014 Cover picture: Plato and Aristotle. Excerpt of the fresco painting School of Athens (1511) by Raphael, Stanza della Segnatura, Apostolic Palace in the Vatican. Preface Why not epistocracy? Political legitimacy and ‘the fact of expertise – (EPISTO) is a five year research project hosted by ARENA Centre for European Studies, University of Oslo. The EPISTO project is financed by the Research Council of Norway. EPISTO inquires into the role of knowledge and expertise in modern democracies. Epistocracy means rule of the knowers, and the project has a particular focus on ‘epistocratic’ developments in the European Union (EU). The kick-off conference took place in Oslo on 4 and 5 April 2013 and was the first of several international events to take place within the project. This report includes a majority of the papers presented at this conference, which was organized around three main themes: 1. Expert-rule and democratic legitimacy 2. The role of knowledge and expertise in EU governance 3. The European Commission’s use of expertise Discussions around the first theme concentrated on implications of modern democracies’ knowledge and expertise dependence for political and democratic theory, with a particular focus on epistemic approaches to deliberative democracy. -

Conceptualizing Afpak: the Prospects and Perils
Asia Programme Paper: ASP PP 2010/01 Conceptualizing AfPak: The Prospects and Perils Ayesha R. Khan Associate Fellow, Asia Programme, Chatham House January 2010 The views expressed in this document are the sole responsibility of the author and do not necessarily reflect the view of Chatham House, its staff, associates or Council. Chatham House is independent and owes no allegiance to any government or to any political body. It does not take institutional positions on policy issues. This document is issued on the understanding that if any extract is used, the author and Chatham House should be credited, preferably with the date of the publication. Programme Paper: ASP PP 2010/01 Conceptualizing AfPak: The Prospects and Perils EXECUTIVE SUMMARY The Obama administration’s AfPak strategy has created the opportunity to recalibrate US engagement with Afghanistan and Pakistan to reverse the Taliban momentum and ‘disrupt and dismantle’ the terrorist threat from the border region. The strategy advocates an increase in US/NATO troops, reconciliation with ‘moderate’ Taliban, and a regional approach to the conflict that includes tackling the Taliban in Pakistan’s tribal areas. In its current conceptualization, it lacks implementation mechanisms and analysis of the border region to manage the insurgency and quell the violence. This paper analyses some of the contradictions, anomalies and structural flaws in the AfPak strategy that risk further destabilizing the Afghanistan–Pakistan border region. As part of the AfPak strategy, President Obama has ordered a ‘military surge’ of approximately 50,000 US troops to implement a shift from counterterrorism to counterinsurgency with an emphasis on the ‘clear, hold, build and engage’ strategy. -

Nation Making in Russia's Jewish Autonomous Oblast: Initial Goals
Nation Making in Russia’s Jewish Autonomous Oblast: Initial Goals and Surprising Results WILLIAM R. SIEGEL oday in Russia’s Jewish Autonomous Oblast (Yevreiskaya Avtonomnaya TOblast, or EAO), the nontitular, predominately Russian political leadership has embraced the specifically national aspects of their oblast’s history. In fact, the EAO is undergoing a rebirth of national consciousness and culture in the name of a titular group that has mostly disappeared. According to the 1989 Soviet cen- sus, Jews compose only 4 percent (8,887/214,085) of the EAO’s population; a figure that is decreasing as emigration continues.1 In seeking to uncover the reasons for this phenomenon, I argue that the pres- ence of economic and political incentives has motivated the political leadership of the EAO to employ cultural symbols and to construct a history in its effort to legitimize and thus preserve its designation as an autonomous subject of the Rus- sian Federation. As long as the EAO maintains its status as one of eighty-nine federation subjects, the political power of the current elites will be maintained and the region will be in a more beneficial position from which to achieve eco- nomic recovery. The founding in 1928 of the Birobidzhan Jewish National Raion (as the terri- tory was called until the creation of the Jewish Autonomous Oblast in 1934) was an outgrowth of Lenin’s general policy toward the non-Russian nationalities. In the aftermath of the October Revolution, the Bolsheviks faced the difficult task of consolidating their power in the midst of civil war. In order to attract the support of non-Russians, Lenin oversaw the construction of a federal system designed to ease the fears of—and thus appease—non-Russians and to serve as an example of Soviet tolerance toward colonized peoples throughout the world.