Reconstruction Under Fire: Unifying Civil and Military Counterinsurgency
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
UNHCR Republic of Congo Fact Sheet
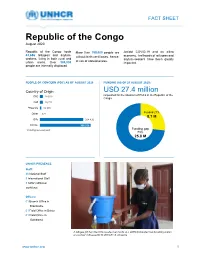
FACT SHEET Republic of the Congo August 2020 Republic of the Congo hosts More than 155,000 people are Amidst COVID-19 and an ailing 43,656 refugees and asylum- without birth certificates, hence, economy, livelihoods of refugees and seekers, living in both rural and asylum-seekers have been greatly at risk of statelessness. urban areas. Over 304,000 impacted. people are internally displaced PEOPLE OF CONCERN (POC) AS OF AUGUST 2020 FUNDING (AS OF 25 AUGUST 2020) Country of Origin USD 27.4 million requested for the situation of PoCs in the Republic of the DRC 20 810 Congo CAR 20,722 *Rwanda 10 565 Funded 27% Other 421 8.1 M IDPs 304 430 TOTAL: 356 926 * Including non-exempted Funding gap 73% 25.8 M UNHCR PRESENCE Staff: 46 National Staff 9 International Staff 8 IUNV (affiliated workforce) Offices: 01 Branch Office in Brazzaville 01 Field Office in Betou 01 Field Office in Gamboma A refugee girl from the DRC washes her hands at a UNHCR-installed handwashing station at a school in Brazzaville © UNHCR / S. Duysens www.unhcr.org 1 FACT SHEET > Republic of the Congo / August 2020 Working with Partners ■ Aligning with the Global Compact on Refugees (GCR), UNHCR in the Republic of the Congo (RoC) has diversified its partnership base to include five implementing partners, comprising local governmental and non-governmental organizations (NGOs), as well as international NGOs. ■ The National Committee for Assistance to Refugees (CNAR), is UNHCR’s main governmental partner, covering general refugee issues, particularly Refugee Status Determination (RSD). Other specific governmental partners include the Ministry of Social and Humanitarian Affairs (MASAH), the Ministries of Justice and Interior (for judicial issues and policies on issues related to statelessness and civil status registration), and the National Human Rights Commission (CNDH). -

War and Insurgency in the Western Sahara
Visit our website for other free publication downloads http://www.StrategicStudiesInstitute.army.mil/ To rate this publication click here. STRATEGIC STUDIES INSTITUTE The Strategic Studies Institute (SSI) is part of the U.S. Army War College and is the strategic-level study agent for issues relat- ed to national security and military strategy with emphasis on geostrategic analysis. The mission of SSI is to use independent analysis to conduct strategic studies that develop policy recommendations on: • Strategy, planning, and policy for joint and combined employment of military forces; • Regional strategic appraisals; • The nature of land warfare; • Matters affecting the Army’s future; • The concepts, philosophy, and theory of strategy; and, • Other issues of importance to the leadership of the Army. Studies produced by civilian and military analysts concern topics having strategic implications for the Army, the Department of Defense, and the larger national security community. In addition to its studies, SSI publishes special reports on topics of special or immediate interest. These include edited proceedings of conferences and topically-oriented roundtables, expanded trip reports, and quick-reaction responses to senior Army leaders. The Institute provides a valuable analytical capability within the Army to address strategic and other issues in support of Army participation in national security policy formulation. Strategic Studies Institute and U.S. Army War College Press WAR AND INSURGENCY IN THE WESTERN SAHARA Geoffrey Jensen May 2013 The views expressed in this report are those of the authors and do not necessarily reflect the official policy or position of the Department of the Army, the Department of Defense, or the U.S. -

United Nations Manual for the Generation and Deployment of Military and Formed Police Units to Peace Operations
United Nations Manual for the Generation and Deployment of Military and Formed Police Units to Peace Operations May 2021 DEPARTMENT OF PEACE OPERATIONS DEPARTMENT OF OPERATIONAL SUPPORT 0 Produced by: Office of Military Affairs and Office of the Police Adviser Department of Peace Operations UN Secretariat New York, NY 10017 Tel. 917-367-2487 Approved by: Jean-Pierre Lacroix, Under-Secretary-General for Peace Operations Department of Peace Operations (DPO). Atul Khare Under-Secretary-General for Operational Support Department of Operational Support (DOS) This is the first version of this Manual, May 2021 Contact: DPO/OMA/FGS and DPO/PD/SRS Review date: May 2024 Reference number: 2021.05 Printed at the UN, New York © UN 2021. This publication enjoys copyright under Protocol 2 of the Universal Copyright Convention. Nevertheless, governmental authorities or Member States may freely photocopy any part of this publication for exclusive use within their training institutes. However, no portion of this publication may be reproduced for sale or mass publication without the express consent, in writing, of the Office of Military Affairs and Office of the Police Adviser, UN Department of Peace Operations. 1 Contents Preface ............................................................................................................................................................4 Purpose and Scope .........................................................................................................................................4 Chapter 1. Introduction -

Reconstruction Under Fire: Case Studies and Further Analysis Of
THE ARTS This PDF document was made available CHILD POLICY from www.rand.org as a public service of CIVIL JUSTICE the RAND Corporation. EDUCATION ENERGY AND ENVIRONMENT Jump down to document6 HEALTH AND HEALTH CARE INTERNATIONAL AFFAIRS The RAND Corporation is a nonprofit NATIONAL SECURITY research organization providing POPULATION AND AGING PUBLIC SAFETY objective analysis and effective SCIENCE AND TECHNOLOGY solutions that address the challenges SUBSTANCE ABUSE facing the public and private sectors TERRORISM AND HOMELAND SECURITY around the world. TRANSPORTATION AND INFRASTRUCTURE Support RAND WORKFORCE AND WORKPLACE Purchase this document Browse Books & Publications Make a charitable contribution For More Information Visit RAND at www.rand.org Explore the RAND National Defense Research Institute View document details Limited Electronic Distribution Rights This document and trademark(s) contained herein are protected by law as indicated in a notice appearing later in this work. This electronic representation of RAND intellectual property is provided for non-commercial use only. Unauthorized posting of RAND PDFs to a non-RAND Web site is prohibited. RAND PDFs are protected under copyright law. Permission is required from RAND to reproduce, or reuse in another form, any of our research documents for commercial use. For information on reprint and linking permissions, please see RAND Permissions. This product is part of the RAND Corporation monograph series. RAND monographs present major research findings that address the challenges facing the public and private sectors. All RAND mono- graphs undergo rigorous peer review to ensure high standards for research quality and objectivity. Reconstruction Under Fire Case Studies and Further Analysis of Civil Requirements A COMPANION VOLUME TO RECONSTRUCTION UNDER FIRE: UNIFYING CIVIL AND MILITARY COUNTERINSURGENCY Brooke Stearns Lawson, Terrence K. -

GAO-05-419T Military Personnel: Preliminary Observations On
United States Government Accountability Office Testimony GAO Before the Subcommittee on Military Personnel, Committee on Armed Services, House of Representatives For Release on Delivery Expected at 2:00 p.m. EST MILITARY PERSONNEL Wednesday, March 16, 2005 Preliminary Observations on Recruiting and Retention Issues within the U.S. Armed Forces Statement of Derek B. Stewart, Director, Defense Capabilities and Management a GAO-05-419T March 16, 2005 MILITARY PERSONNEL Accountability Integrity Reliability Highlights Preliminary Observations on Recruiting Highlights of GAO-05-419T, a testimony to and Retention Issues within the U.S. the Chairman, Subcommittee on Military Personnel, Committee on Armed Services, Armed Forces House of Representatives Why GAO Did This Study What GAO Found To meet its human capital needs, DOD’s 10 military components generally met their overall recruitment and the Department of Defense (DOD) retention goals for each of the past 5 fiscal years (FY), but some of the must convince several hundred components experienced difficulties in meeting their overall goals in early thousand people to join the military FY 2005. However, it should be noted that several components introduced a each year while, at the same time, “stop loss” policy shortly after September 11, 2001. The “stop loss” policy retain thousands of personnel to sustain its active duty, reserve, and requires some servicemembers to remain in the military beyond their National Guard forces. Since contract separation date, which may reduce the number of personnel the September 11, 2001, DOD has components must recruit. During FY 2000-2004, each of the active launched three major military components met or exceeded their overall recruiting goals. -

Of the United Nations Mission in the DRC / MONUC – MONUSCO
Assessing the of the United Nations Mission in the DRC / MONUC – MONUSCO REPORT 3/2019 Publisher: Norwegian Institute of International Affairs Copyright: © Norwegian Institute of International Affairs 2019 ISBN: 978-82-7002-346-2 Any views expressed in this publication are those of the author. Tey should not be interpreted as reflecting the views of the Norwegian Institute of International Affairs. Te text may not be re-published in part or in full without the permission of NUPI and the authors. Visiting address: C.J. Hambros plass 2d Address: P.O. Box 8159 Dep. NO-0033 Oslo, Norway Internet: effectivepeaceops.net | www.nupi.no E-mail: [email protected] Fax: [+ 47] 22 99 40 50 Tel: [+ 47] 22 99 40 00 Assessing the Efectiveness of the UN Missions in the DRC (MONUC-MONUSCO) Lead Author Dr Alexandra Novosseloff, International Peace Institute (IPI), New York and Norwegian Institute of International Affairs (NUPI), Oslo Co-authors Dr Adriana Erthal Abdenur, Igarapé Institute, Rio de Janeiro, Brazil Prof. Tomas Mandrup, Stellenbosch University, South Africa, and Royal Danish Defence College, Copenhagen Aaron Pangburn, Social Science Research Council (SSRC), New York Data Contributors Ryan Rappa and Paul von Chamier, Center on International Cooperation (CIC), New York University, New York EPON Series Editor Dr Cedric de Coning, NUPI External Reference Group Dr Tatiana Carayannis, SSRC, New York Lisa Sharland, Australian Strategic Policy Institute, Canberra Dr Charles Hunt, Royal Melbourne Institute of Technology (RMIT) University, Australia Adam Day, Centre for Policy Research, UN University, New York Cover photo: UN Photo/Sylvain Liechti UN Photo/ Abel Kavanagh Contents Acknowledgements 5 Acronyms 7 Executive Summary 13 Te effectiveness of the UN Missions in the DRC across eight critical dimensions 14 Strategic and Operational Impact of the UN Missions in the DRC 18 Constraints and Challenges of the UN Missions in the DRC 18 Current Dilemmas 19 Introduction 21 Section 1. -

Usama Bin Ladin's
Usama bin Ladin’s “Father Sheikh”: Yunus Khalis and the Return of al-Qa`ida’s Leadership to Afghanistan Harmony Program Kevin Bell USAMA BIN LADIN’S “FATHER SHEIKH:” YUNUS KHALIS AND THE RETURN OF AL‐QA`IDA’S LEADERSHIP TO AFGHANISTAN THE COMBATING TERRORISM CENTER AT WEST POINT www.ctc.usma.edu 14 May 2013 The views expressed in this paper are the author’s and do not necessarily reflect those of the Combating Terrorism Center, the U.S. Military Academy, the Department of Defense or the U.S. government. Author’s Acknowledgments This report would not have been possible without the generosity and assistance of the director of the Harmony Research Program at the Combating Terrorism Center (CTC), Don Rassler. Mr. Rassler provided me with the support and encouragement to pursue this project, and his enthusiasm for the material always helped to lighten my load. I should state here that the first tentative steps on this line of inquiry were made during my time as a student at the Program in Near Eastern Studies at Princeton University. If not for professor Şükrü Hanioğlu’s open‐minded approach to directing my MA thesis, it is unlikely that I would have embarked on this investigation of Yunus Khalis. Professor Michael Reynolds also deserves great credit for his patience with this project as a member of my thesis committee. I must also extend my utmost appreciation to my reviewers—Carr Center Fellow Michael Semple, professor David Edwards and Vahid Brown—whose insightful comments, I believe, have led to a substantially improved and more thoughtful product. -

Volume 2A: Chapter 2: Military Personnel Appropriations
DoD Financial Management Regulation Volume 2A, Chapter 2 +June 2004 CHAPTER 2 MILITARY PERSONNEL APPROPRIATIONS Table of Contents 0201 GENERAL ...................................................................................................................................................1 020101 Purpose ..................................................................................................................................................1 0202 ACTIVE MILITARY PERSONNEL APPROPRIATIONS ....................................................................2 020201 General...................................................................................................................................................2 020202 Uniform Budget and Fiscal Accounting Classification .........................................................................2 020203 Budget Presentation Structure Requirements ......................................................................................16 020204 Program and Budget Review Submission............................................................................................22 020205 Congressional Justification/Presentation .............................................................................................24 0203 RESERVE MILITARY PERSONNEL APPROPRIATIONS...............................................................25 020301 General.................................................................................................................................................25 -

Law of Armed Conflict
Lesson 1 THE LAW OF ARMED CONFLICT Basic knowledge International Committee of the Red Cross Unit for Relations with Armed and Security Forces 19 Avenue de la Paix 1202 Geneva, Switzerland T +41 22 734 60 01 F +41 22 733 20 57 E-mail: [email protected] www.icrc.org Original: English – June 2002 INTRODUCTION TO THE LAW OF ARMED CONFLICT BASIC KNOWLEDGE LESSON 1 [ Slide 2] AIM [ Slide 3] The aim of this lesson is to introduce the topic to the class, covering the following main points: 1. Background: setting the scene. 2. The need for compliance. 3. How the law evolved and its main components. 4. When does the law apply? 5. The basic principles of the law. INTRODUCTION TO THE LAW OF ARMED CONFLICT 1. BACKGROUND: SETTING THE SCENE Today we begin a series of lectures on the law of armed conflict, which is also known as the law of war, international humanitarian law, or simply IHL. To begin, I’d like to take a guess at what you’re thinking right now. Some of you are probably thinking that this is an ideal opportunity to catch up on some well-earned rest. “Thank goodness I’m not on the assault course or on manoeuvres. This is absolutely marvellous. I can switch off and let this instructor ramble on for 45 minutes. I know all about the Geneva Conventions anyway – the law is part of my culture and our military traditions. I really don't need to listen to all this legal ‘mumbo jumbo’.” The more sceptical and cynical among you might well be thinking along the lines of a very famous orator of ancient Rome – Cicero. -

Repupublic of Congo
BE TOU & IMPFONDO MARKET ASSESSMENT IN LIKOUALA – REPUBLIC OF CONGO Cash Based Transfer Market This market assessment assesses the feasibility of markets in Bétou and Assessment: Impfondo to absorb and respond to a CBT intervention aimed at supporting CAR refugees’ food security in The Republic of Congo’s Likouala region. The December report explores appropriate measures a CBT intervention in Likouala would 2015 need to adopt in order to address hurdles limiting Bétou and Impfondo markets’ functionality. Contents Executive Summary: ............................................................................................................................... 4 Section 1: Introduction and Macro-Economic Analysis of RoC .............................................................. 5 1.1: Introduction ..................................................................................................................................... 5 1.2: The Economy ................................................................................................................................... 6 Section 2: Market Assessment Introduction and Methodology ............................................................. 9 2.1: Market Assessment Introduction .................................................................................................... 9 2.2: Market Assessment Methodology ................................................................................................... 9 Section 3: Limitations of the Market Assessment ............................................................................... -

Länderinformationen Afghanistan Country
Staatendokumentation Country of Origin Information Afghanistan Country Report Security Situation (EN) from the COI-CMS Country of Origin Information – Content Management System Compiled on: 17.12.2020, version 3 This project was co-financed by the Asylum, Migration and Integration Fund Disclaimer This product of the Country of Origin Information Department of the Federal Office for Immigration and Asylum was prepared in conformity with the standards adopted by the Advisory Council of the COI Department and the methodology developed by the COI Department. A Country of Origin Information - Content Management System (COI-CMS) entry is a COI product drawn up in conformity with COI standards to satisfy the requirements of immigration and asylum procedures (regional directorates, initial reception centres, Federal Administrative Court) based on research of existing, credible and primarily publicly accessible information. The content of the COI-CMS provides a general view of the situation with respect to relevant facts in countries of origin or in EU Member States, independent of any given individual case. The content of the COI-CMS includes working translations of foreign-language sources. The content of the COI-CMS is intended for use by the target audience in the institutions tasked with asylum and immigration matters. Section 5, para 5, last sentence of the Act on the Federal Office for Immigration and Asylum (BFA-G) applies to them, i.e. it is as such not part of the country of origin information accessible to the general public. However, it becomes accessible to the party in question by being used in proceedings (party’s right to be heard, use in the decision letter) and to the general public by being used in the decision. -

Afghanistan Ministry of Counter Narcotics
Government of Afghanistan Ministry of Counter Narcotics Vienna International Centre, PO Box 500, 1400 Vienna, Austria Tel.: (+43-1) 26060-0, Fax: (+43-1) 26060-5866, www.unodc.org Afghanistan Opium Survey 2010 Summary Findings September 2010 ABBREVIATIONS AGE Anti-government Elements ANP Afghan National Police CNPA Counter Narcotics Police of Afghanistan GLE Governor-led eradication ICMP Illicit Crop Monitoring Programme (UNODC) ISAF International Security Assistance Force MCN Ministry of Counter-Narcotics UNODC United Nations Office on Drugs and Crime ACKNOWLEDGEMENTS The following organizations and individuals contributed to the implementation of the 2009 Afghanistan Opium Survey and to the preparation of this report: Ministry of Counter-Narcotics: Mohammad Ibrahim Azhar (Deputy Minister), Mohammad Zafar (Deputy Minister), Ahmad Haroon Shirzad (Director General), Policy &Coordination, Mir Abdullah (Deputy Director of Survey and Monitoring Directorate), Saraj Ahmad (Deputy Director of Survey and Monitoring Directorate). Survey Coordinators: Eshaq Masumi (Central Region), Abdul Mateen (Eastern Region), Abdul Latif Ehsan (Western Region), Fida Mohammad (Northern Region), Mohammed Ishaq Anderabi (North- Eastern Region), Khalil Ahmad (Southern Region), Khiali Jan Mangal (Eradication Verification Reporter), Mohammad Khyber Wardak (Database officer), Mohammad Sadiq Rizaee (Remote Sensing), Shiraz Khan Hadawe (GIS & Remote Sensing Analyst), Mohammad Ajmal (Data entry), Sahar (Data entry), Mohammad Hakim Hayat (Data entry). United Nations Office on Drugs and Crime (Kabul) Jean-Luc Lemahieu (Country Representative), Ashita Mittal (Deputy Representative, Programme), Devashish Dhar (International Project Coordinator), Ziauddin Zaki (National Project Coordinator), Abdul Mannan Ahmadzai (Survey Officer), Noor Mohammad Sadiq (Database Developer) Remote sensing analysts: Ahmad Jawid Ghiasee and Sayed Sadat Mehdi Eradication reporters: Ramin Sobhi and Zia Ulhaq.