NIS Export Control Observer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Location, Event&Q
# from what/ where which how why who for MOBILE versi on click here when who who where when index source "location, event" "phys, pol, med, doc" detail physical detail political name "9/11 Truth Interactive Spreadsheet Click on dow n arrow to sort / filter, click again to undo." Top 100 / compilations entity entity detail country / state date Item .. right-click on li nk to open in new tab 1 "Francis, Stephen NFU" WTC physical Controlled demolition Explosive experts "Overwhelming evidence indicates that a combination of n uclear, thermitic and conventional explosives were used in a controlled demoliti on of the WTC on 9/11. Nanothermite contributed but does not have sufficient det onation velocity to pulverize the WTC into dust. Architects & Engineers for 9/11 Truth is leading gatekeeper trying to deflect Israel's role. See Cozen O'Connor 9/11 lawsuit." pic "9/11 Truth, anti-Zionists" Engineers / Scie ntists "U.S., Israel, SA, Britain" 2 "Francis, Stephen NFU" "WTC, Pentagon, PA" political False flag Cabal "The cabal: U.S., Britain, Saudi Arabia and Israel execu ted the 9/11 false flag attack in order to usher in a new 'war on terror' along with the Iraq and Afghanistan wars and fullfil the PNAC's 'Full Spectrum Dominan ce' of the Middle East and its resources ... all have roots that go back to Zion ist / Nazi Germany, the Cold War ... 9/11 was a planned step." lnk Intel ag encies "Cabal: US, UK, Israel & SA" Mossad / Sayeret Matkal "U.S., Israel, S A, Britain" 3 "Fox, Donald" WTC 1-2 physical "Mini Neutron, Fissionless Fusio n" Controlled demolition "VeteransToday: Fox, Kuehn, Prager, Vike n,Ward, Cimono & Fetzer on mini neutron bombs discuss all major WTC theories micr o nuke (neutron) most promising comparatively low blast effects, a quick blast o f radiation that doesn't linger, a series of shape charged mini-neutron bombs we re detonated from top to bottom to simulate a free fall collapse. -

Assessing Asymmetry in International Politics: Us-South Africa Relations: 1994-2008
ASSESSING ASYMMETRY IN INTERNATIONAL POLITICS: US-SOUTH AFRICA RELATIONS: 1994-2008 by SCOTT THOMAS FIRSING submitted in accordance with the requirements for the degree of DOCTOR OF LITERATURE AND PHILOSOPHY in the subject INTERNATIONAL POLITICS at the UNIVERSITY OF SOUTH AFRICA SUPERVISOR: DR T HOEANE CO-SUPERVISOR: MS J K VAN WYK NOVEMBER 2010 TABLE OF CONTENTS List of Figures and Tables…………………………………………………………………………..9 List of Acronyms………………………………………………………………………………......10 CHAPTER ONE: INTRODUCTION TO THIS THESIS 1. Introduction……………………………………………………………………………………..13 2. Literature review……………………………………………………………………………......14 3. Purpose and objectives……………………………………………………………………….....16 4. Approaches and methodology…………………………………………………………………..16 5. Scope and limitations of the thesis……………………………………………………………...18 6. Contribution of study…………………………………………………………………………....20 7. Research questions and structure of study….……………………………………………...........21 CHAPTER TWO: OVERVIEW OF ASYMMETRY THEORY 1. Introduction……………………………………………………………………………………...26 2. Asymmetry theory.........................................................................................................................26 3. Strong versus the weak…………………………………………………………………………..29 4. Inattention and overattention…………………………………………………………………….31 5. Deference, autonomy and misperception……………………………………………………......33 6. Managing the asymmetric relationship…………………………………………………………37 6.1 Routinization…………………………………………………………………………………...37 6.2 Diplomatic ritual……………………………………………………………………………….38 6.3 Neutralization………………………………………………………………………………......39 -

South Africa's Nuclear Dismantlement Continues to Astonish
6/21/2017 South Africa’s nuclear dismantlement continues to astonish | International Affairs at LSE Dec 8 2011 South Africa’s nuclear dismantlement continues to astonish LSE IDEAS With the world’s focus now on Iran’s nuclear ambition, Dr Scott Firsing argues that South Africa’s nuclear dismantlement and its leading role in nuclear disarmament and nonproliferation continues to amaze over two decades later. He looks back at some of South Africa’s achievements and its affect on United StatesSouth African relations. By Dr Scott Firsing Lecturer and Acting Head: International Studies Monash South Africa The world is currently focused on Iran. Today, 06 December 2012, Australia joined the United States (US), Canada and the United Kingdom in widening sanctions against Iran as the EU debates the possibility of an oil embargo. Various questions are now being pondered including will the US and/or Israel attack Iran’s nuclear facilities? While reading these articles, one cannot help but think of the bravery and vision of South Africa to possess the world’s most powerful weapon then voluntarily dismantle its entire program. Although the Iranian and South African case studies are very different in regards to the internal and external political and security aspects, one can continue to hope [as I am sure Washington is] that Iran will follow in South Africa’s footsteps and abandon its nuclear ambitions. It has been over 20 years since South Africa signed the nuclear Nonproliferation Treaty (NPT) as a non nuclearweapon state. In the wake of the April/May 1995 NPT Review and Extension Conference, Martha Bridgman of the South African Institute for International Affairs observes that American pronouncements on South Africa created an impression that the two countries were taking great strides in their defense relations.[i] America believed the NPT should be indefinitely extended under which the developed world could maintain some control over the spread of nuclear weapons while working to reduce its own stockpiles. -

Measuring Nuclear Export Controls in Nuclear- Powered Nations and Nuclear Aspirants
Measuring Nuclear Export Controls in Nuclear- Powered Nations and Nuclear Aspirants Peter Crail 1 Nuclear export controls had once been the prerogative of a handful of states which were able to act as gatekeepers to nuclear technology. As a result of the diffusion of technology and a rapidly altered proliferation environment, however, they are now a necessary component of responsible nuclear stewardship. Security Council Resolution 1540 (2004) created the first international mandate for all states to adopt export controls over weapons of mass destruction technologies. Six years later, key gaps still exist in the export control systems of many countries with nuclear energy sectors, and even greater weaknesses exist in states seeking nuclear power. It will be important for the international community to take steps to strengthen the global system of export controls as it anticipates a surge in nuclear energy development. Introduction Over the past several years, controls over the export of nuclear goods and technologies have increased in legitimacy and international application. Once the sole reserve of a select group of nuclear suppliers, export controls are now firmly part of the international toolbox for countering proliferation. This development, however, has been outpaced by rapid technological diffusion over the past two-decades and innovation on the part of both state and non-state proliferators. Sophisticated nuclear supply networks have become the preferred acquisition tool for state proliferators and non-state actors may now be both the suppliers and the recipients of nuclear weapons-related goods and technology. In the event of a much anticipated “nuclear renaissance,” with over thirty countries which do not currently have nuclear power programs considering such an endeavor, these challenges will grow even further. -

Export, Customs & Trade
ReedSmith Export, Customs & Trade Fall 2005 Volume II, Number 4 Sentinenel International Trade Remedies are Available to In This Issue: Enforce Intellectual Property Rights International Trade Remedies are Available to Enforce Intellectual Whereas many companies are aware of the traditional means of enforc- Property Rights—Page 1 ing company-owned intellectual property rights (patents, trademarks and copyrights) through litigation in federal district court, companies operat- UN Trade Sanctions After the ing in the international arena or facing infringement from international ac- Oil-for-Food Program—Page 2 tors have a number of additional international trade remedies available to Enforcement Highlights—Page 4 protect intellectual property assets. International trade remedies available OFAC Reissues Burma Sanctions through the U.S. International Trade Commission (“ITC”) and the U.S. Regulations—Page 5 Customs Service (“Customs”) may offer fast, broad, and effective relief from intellectual property right infringement. Reed Smith in Print and at the Podium—Page 7 International Trade Commission “337” Investigations Recent Reed Smith Publications— Under Section 337 of the Tariff Act of 1930, as amended, it is unlaw- Page 11 ful to import, sell for importation, or sell within the United States after importation, articles that infringe upon a valid U.S. patent, trademark, or copyright. The Tariff Act empowers the ITC to conduct “337” investiga- tions into all allegations of unfair practices in import trade, including infringement of patents, trademarks, or copyrights. The ITC may institute a 337 investigation on its own initiative, but usually such investigations are initiated based upon the fi ling of a complaint. If a “Complainant” fi les a complaint before the ITC, certain pre-institution proceedings may be undertaken between the Complainant and the ITC staff to ensure the adequacy of the complaint. -

'Understanding Clandestine Nuclear Procurement Networks' Mark
1 ‘Understanding Clandestine Nuclear Procurement Networks’ Mark Fitzpatrick, International Institute for Strategic Studies, London IAEA Scientific Forum, Session 4: Safeguards and Nuclear Verification 19 September 2007 (as prepared) It is an honour to be invited to address the IAEA Scientific Forum, and I congratulate the organizers for putting together an impressive programme. Speaking after two distinguished ambassadors and before a respected governor, I have to ask if I am in the right league. But I have one advantage in that I represent no country and can therefore speak frankly and even undiplomatically. In addressing the subject of, ‘Understanding Clandestine Nuclear Procurement Networks,’ I will draw heavily on a report my institute, the IISS, published in May: ‘Nuclear Black Markets: Pakistan, A.Q. Khan and the rise of proliferation networks’, for which I was the editor. Our report defines ‘nuclear black market’ to mean the trade in nuclear‐related technologies, components or material that is pursued for non‐peaceful purposes and most often by secretive means. Often the trade is not explicitly illegal, but exploits loopholes in national export regulations. ‘Black’, in this case, often means shades of grey. Global problem At least a dozen countries have sought clandestine procurement of nuclear technology. In addition to Pakistan, our report summarizes some of the black market procurement attempts by Iraq, Iran, North Korea, Libya, Israel, India, South Africa, Brazil, Argentina, Egypt, and Syria (although in Syria’s case we do not claim that it was pursuing a weapons program). In fact, every country that has developed nuclear weapons has done so with a key assist from technology obtained elsewhere. -

Illicit Networks Targeting the Nexus Between Terrorists, Proliferators, and Narcotraffickers
CORE Metadata, citation and similar papers at core.ac.uk Provided by Calhoun, Institutional Archive of the Naval Postgraduate School Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2010-12 Illicit networks targeting the nexus between terrorists, proliferators, and narcotraffickers Dietz, Rebekah K. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/5008 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS ILLICIT NETWORKS: TARGETING THE NEXUS BETWEEN TERRORISTS, PROLIFERATORS, AND NARCOTRAFFICKERS by Rebekah K. Dietz December 2010 Thesis Advisor: Zachary Davis Second Reader: Dorothy Denning Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington DC 20503. 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED December 2010 Master’s Thesis 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS Illicit Networks: Targeting the Nexus Between Terrorists, Proliferators, and Narcotraffickers 6. AUTHOR(S) Rebekah K. Dietz 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING ORGANIZATION Naval Postgraduate School REPORT NUMBER Monterey, CA 93943-5000 9. -

Security Council Distr.: General 12 April 2010
United Nations S/AC.44/2007/10 Security Council Distr.: General 12 April 2010 Original: English Security Council Committee established pursuant to resolution 1540 (2004) Letter dated 21 December 2007 from the Permanent Representative of the United States of America to the United Nations addressed to the Chairman of the Committee I have the honour to respond to your letter, dated 17 October 2007, on behalf of the Security Council Committee established pursuant to resolution 1540 (2004), and to enclose an update to the 2004 United States report to the Committee (see annex). The enclosed report is a comprehensive update of United States laws, policies, projects, and initiatives to prevent illicit trafficking in weapons of mass destruction, their delivery systems, and related materials, and in particular to prevent terrorist acquisition of such items. It is intended to supplement and not replace the 2004 report and incorporates input from numerous United States Government agencies. The report presents a picture of steps taken since the initial report of United States efforts related to the implementation of resolution 1540 (2004), as well as steps the United States intends to take. Separately, the United States will contact the members of the Committee’s panel of experts to discuss United States revisions to the matrix. Once the United States matrix has been revised and completed, the United States would like to request that the Committee post it on the Committee’s website as a public document. The United States looks forward to continued cooperation with the Committee. (Signed) Zalmay Khalilzad 10-31900 (E) 110610 *1031900* S/AC.44/2007/10 Annex to the letter dated 21 December 2007 from the Permanent Representative of the United States of America to the United Nations addressed to the Chairman of the Committee United States update to the 2004 United States report to the Committee 1. -

Turkish Perceptions and Nuclear Proliferation by Ibrahim Al-Marashi and Nilsu Goren
Turkish Perceptions and Nuclear Proliferation by Ibrahim Al-Marashi and Nilsu Goren Strategic Insights is a quarterly electronic journal produced by the Center for Contemporary Conflict at the Naval Postgraduate School in Monterey, California. The views expressed here are those of the author(s) and do not necessarily represent the views of NPS, the Department of Defense, or the U.S. Government. Introduction Turkey is a “middle power” in Eurasia and in the Middle East aspiring to become a regional power. Due to the complexity of its security environment, Turkey seeks protection from weapons of mass destruction (WMD) threats, Islamic fundamentalism endangering the Republic’s secularism, and ethnic separatism. From a systemic perspective, Turkey plays the role of an “insulator” for the European Union (EU) by isolating the complexity of the Middle Eastern security environment. Turkey also has a crucial position in the regional balance as a transit country in the Caspian energy corridor. It is argued that Turkish membership to EU would enhance the European security structure, as it would benefit from Turkey’s geopolitical position and military capabilities as a NATO member. Turkey serves to enhance European security vis-à-vis global terrorism and transnational threats. Wood and Quaisser write that Turkey is “an irreplaceable southeast flanking power, without whom a forward defence or security sphere for Europe would not be possible in the Eastern Mediterranean or Black Sea, not to mention the Middle East.”[ 1] At the same time, considering its regional security environment, Turkey’s realpolitik security characteristics are incompatible with European civilian-normative security measures based on soft power.[ 2] This is the milieu in which the Turkish security policy community operates. -

Illicit Procurement of Items with Nuclear Applications for Pakistan1
Institute for Science and International Security ISIS REPORT February 27, 2009 Profitable and Low-Penalty: Illicit Procurement of Items with Nuclear 1 Applications for Pakistan David Albright, Paul Brannan and Andrea Scheel In 2004, U.S. authorities arrested Asher Karni, an Israeli citizen living in South Africa, for re-exporting U.S.-made triggered spark gaps and oscilloscopes from South Africa to Pakistan, which were likely intended for Pakistan’s nuclear weapons program. Triggered spark gaps are listed as a dual-use item under U.S. and Nuclear Supplier Group (NSG) guidelines. Their non-military use is in lithotripters, a medical device used to disintegrate kidney stones. They can also be used to detonate nuclear weapons or separate missile stages, creating a burst of precisely timed electrical current that causes detonation. Oscilloscopes are equipment that exhibit graphs of electrical signals, displaying the timing, voltages, frequency, and other attributes of signals. The models of oscilloscopes sought by Karni had application in nuclear weapons and missile delivery systems, capable in particular of being used to measure the yields and effects of nuclear weapons tests. Karni was the owner and sales director of Top-Cape Technology, located in Cape Town, South Africa, a company which boasted on its website about its skill in acquiring civilian and military electronic goods. U.S. authorities arrested him on U.S. territory for export control violations following close cooperation with South African authorities. According to the U.S. Government’s Sentencing Memorandum against Karni, he also procured items for entities affiliated with the nuclear weapon and missile programs of India, Russia, China, and Israel. -
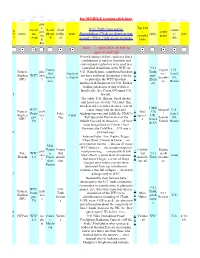
For MOBILE Version Click Here 9/11 Truth Interactive Spreadsheet Click on Down Arrow to Sort / Filter, Click Again to Undo. Item
what/ whi # from where ch how why who for MOBILE version click here when who who where when phy s, Top 100 locati detail detail 9/11 Truth Interactive countr in pol, / entity de source on, physic politic name entity y / date me Spreadsheet Click on down arrow compila detail x event al al state d, to sort / filter, click again to undo. tions doc Item ….. right-click on link to open in new tab Overwhelming evidence indicates that a combination of nuclear, thermitic and conventional explosives were used in a controlled demolition of the WTC on 9/11 Contro Engine U.S., Francis, phy 9/11. Nanothermite contributed but does p Truth, lled Explosiv ers / Israel, Stephen WTC sica not have sufficient detonation velocity i anti- demoli e experts Scientis SA, NFU l to pulverize the WTC into dust. c Zioni tion ts Britain Architects & Engineers for 9/11 Truth is sts leading gatekeeper trying to deflect Israel's role. See Cozen O'Connor 9/11 1 lawsuit. The cabal: U.S., Britain, Saudi Arabia and Israel executed the 9/11 false flag attack in order to usher in a new 'war on Cabal WTC, terror' along with the Iraq and Mossad U.S., Francis, poli l Intel : US, Penta False Afghanistan wars and fullfil the PNAC's / Israel, Stephen tica Cabal n agencie UK, gon, flag 'Full Spectrum Dominance' of the Sayeret SA, NFU l k s Israel PA Middle East and its resources ... all have Matkal Britain & SA roots that go back to Zionist / Nazi Germany, the Cold War .. -

Israel Nuclear Chronology
Israel Nuclear Chronology 2009-2007 | 2006 | 2005 | 2004-2000 | 1999-1990 | 1989-1970 | 1969-1960 | 1959-1947 Last update: April 2008 As of April 2008, this chronology is no longer being updated. For current developments, please see the India Biological Overview. This annotated chronology is based on the data sources that follow each entry. Public sources often provide conflicting information on classified military programs. In some cases we are unable to resolve these discrepancies, in others we have deliberately refrained from doing so to highlight the potential influence of false or misleading information as it appeared over time. In many cases, we are unable to independently verify claims. Hence in reviewing this chronology, readers should take into account the credibility of the sources employed here. Inclusion in this chronology does not necessarily indicate that a particular development is of direct or indirect proliferation significance. Some entries provide international or domestic context for technological development and national policymaking. Moreover, some entries may refer to developments with positive consequences for nonproliferation. 2009-2007 26 February 2009 Following Iran's announcement of the completion of its first nuclear power plant at Bushehr, outgoing Israeli Prime Minister Olmert reiterates Israel's ability "…to defend itself in all situations, against all threats, [and] against all enemies." Although the Prime Minister did not mention Iran by name, his statement was widely interpreted to have been directed at Iran. —Borzou Daragahi,"Iran, Russia test joint nuclear reactor in Bushehr," Los Angeles Times, 26 February, 2009; "We are very strong, Israel Warns Iran," The Sydney Morning Herald, 27 February 2009; Behrouz Mehri, "Olmert warns Iran over nuclear plant," Agence France-Presse, 26 February 2009.