Lesson E19 En. Internet Troubleshooting, Disturbances, Maintenance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LAB MANUAL for Computer Network
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design, troubleshooting, modeling and evaluation of computer networks. In this course, students are going to experiment in a real test-bed networking environment, and learn about network design and troubleshooting topics and tools such as: network addressing, Address Resolution Protocol (ARP), basic troubleshooting tools (e.g. ping, ICMP), IP routing (e,g, RIP), route discovery (e.g. traceroute), TCP and UDP, IP fragmentation and many others. Student will also be introduced to the network modeling and simulation, and they will have the opportunity to build some simple networking models using the tool and perform simulations that will help them evaluate their design approaches and expected network performance. S.No Experiment 1 Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. 2 Study of Network Devices in Detail. 3 Study of network IP. 4 Connect the computers in Local Area Network. 5 Study of basic network command and Network configuration commands. 6 Configure a Network topology using packet tracer software. 7 Configure a Network topology using packet tracer software. 8 Configure a Network using Distance Vector Routing protocol. 9 Configure Network using Link State Vector Routing protocol. Hardware and Software Requirement Hardware Requirement RJ-45 connector, Climping Tool, Twisted pair Cable Software Requirement Command Prompt And Packet Tracer. EXPERIMENT-1 Aim: Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information. -

Ipswitch Failover V9.5 Administrator's Guide
Administrator's Guide For Ipswitch Failover v9.5 Copyright ©1991-2016 Ipswitch, Inc. All rights reserved. This document, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the express prior written consent of Ipswitch, Inc. The content of this document is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc., also assumes no liability for damages resulting from the use of the information contained in this document. WS_FTP, the WS_FTP logos, Ipswitch, and the Ipswitch logo, MOVEit and the MOVEit logo, MessageWay and the MessageWay logo are trademarks of Ipswitch, Inc. Other products and their brands or company names, are or may be trademarks or registered trademarks, and are the property of their respective companies. Contents Preface: About This Book.........................................................................vii Part I: Getting Started..................................................................................9 Chapter 1: Ipswitch Failover Concepts.................................................................................11 -

Reference Guide Vmware Vcenter Server Heartbeat 5.5 Update 1
Administrator Guide VMware vCenter Server Heartbeat 6.3 Update 1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document, see http://www.vmware.com/support/pubs. EN-000562-01 Administrator Guide You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] Copyright © 2010 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. VMware products are covered by one or more patents listed at http://www.vmware.com/go/patents. VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents About This Book 7 Getting Started 1 Introduction 11 Overview 11 vCenter Server Heartbeat Concepts 11 Architecture 11 Protection Levels 13 Communications 16 vCenter Server Heartbeat Switchover and Failover Processes 17 2 Configuring vCenter Server Heartbeat 21 Server Configuration Wizard 22 Configuring the Machine Identity 22 Configuring the Server Role 23 Configuring the Client Connection Port 23 Configuring Channel -

TCP/IP Fundamentals for Microsoft Windows
TCP/IP Fundamentals for Microsoft Windows Microsoft Corporation Published: May 21, 2006 Updated: Jan 9, 2012 Author: Joseph Davies Editor: Anne Taussig Abstract This online book is a structured, introductory approach to the basic concepts and principles of the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite, how the most important protocols function, and their basic configuration in the Microsoft® Windows Vista™, Windows Server® 2008, Windows® XP, and Windows Server 2003 families of operating systems. This book is primarily a discussion of concepts and principles to lay a conceptual foundation for the TCP/IP protocol suite and provides an integrated discussion of both Internet Protocol version 4 (IPv4) and Internet Protocol version 6 (IPv6). The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This content is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. The terms of use of this document can be found at http://www.microsoft.com/info/cpyright.mspx. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

An A-Z Index of the Windows CMD Command Line
An A-Z Index of the Windows CMD command line aaADDUSERSADDUSERS Add or list users to/from a CSV file ADmodcmd Active Directory Bulk Modify ARP Address Resolution Protocol ASSOC Change file extension associations• ASSOCIAT One step file association AT Schedule a command to run at a specific time ATTRIB Change file attributes bb BCDBOOT Create or repair a system partition BCDEDIT Manage Boot Configuration Data BITSADMIN Background Intelligent Transfer Service BOOTCFG Edit Windows boot settings BROWSTAT Get domain, browser and PDC info cc CACLS Change file permissions CALL Call one batch program from another• CERTREQ Request certificate from a certification authority CERTUTIL Utility for certification authority (CA) files and services CD Change Directory - move to a specific Folder• CHANGE Change Terminal Server Session properties CHKDSK Check Disk - check and repair disk problems CHKNTFS Check the NTFS file system CHOICE Accept keyboard input to a batch file CIPHER Encrypt or Decrypt files/folders CleanMgr Automated cleanup of Temp files, recycle bin CLEARMEM Clear memory leaks CLIP Copy STDIN to the Windows clipboard CLS Clear the screen• CLUSTER Windows Clustering CMD Start a new CMD shell CMDKEY Manage stored usernames/passwords COLOR Change colors of the CMD window• COMP Compare the contents of two files or sets of files COMPACT Compress files or folders on an NTFS partition COMPRESS Compress individual files on an NTFS partition CON2PRT Connect or disconnect a Printer CONVERT Convert a FAT drive to NTFS COPY Copy one or more files -

IP/Networking Commands
IP/Networking Commands There are a lot of IP commands with short descriptions listed here but you should only need the ones mentioned here at the top of the page to diagnose and configure your network. C:>ping C:>ipconfig C:>ipconfig /all C:>ipconfig /release C:>ipconfig /renew C:\>nbtstat –a Remember when typing from the command prompt you can only type one command per line, and press Enter after each one to execute it. C:\>arp –a: is short for address resolution protocol, It will show the IP address of your computer along with the IP address and MAC address of your router. C:\>hostname: This is the simplest of all TCP/IP commands. It simply displays the name of your computer. C:\>ipconfig: The ipconfig command displays information about the host (the computer your sitting at)computer TCP/IP configuration. C:\>ipconfig /all: This command displays detailed configuration information about your TCP/IP connection including Router, Gateway, DNS, DHCP, and type of Ethernet adapter in your system. C:\>Ipconfig /renew: Using this command will renew all your IP addresses that you are currently (leasing) borrowing from the DHCP server. This command is a quick problem solver if you are having connection issues, but does not work if you have been configured with a static IP address. C:\>Ipconifg /release: This command allows you to drop the IP lease from the DHCP server. C:\>ipconfig /flushdns: This command is only needed if you’re having trouble with your networks DNS configuration. The best time to use this command is after network configuration frustration sets in, and you really need the computer to reply with flushed. -

Useful DOS Commands
Useful DOS Commands Analyzing and troubleshooting computers and network can be difficult when problem arise. One can look at the Windows event viewer for warning and error event messages. Enough times these event messages can be informative. But it may not show the cause for errors or performance issues without further investigation. The network could be bogged down between computers and the server. The computer system could be problematic beside possible hard drive warnings and CLSID/APPID issues. The Windows operating system contain built-in tools as networking command line utilities that users and administrators could use to help troubleshoot. There are 11 built-in commands but the NbtStat has been depreciated since 2000 and NetDiag has been depreciated since Windows XP. Both will not be talked about here. • Ping • NetStat • NbtStat - depreciated • ARP • Hostname • Tracert • Ipconfig • NSLookup • Route • PathPing • NetDiag - depreciated The information below sufficiently describe these most commonly used commands. For more in- depth use, additional search may be required. Ping (Packet Internet Groper) Ping command is the most familiar and commonly used utility. It helps in determining the possible issues with the network both local and Internet. Ping is used to test the ability of one network host to communicate with another basically at the TCP/IP level. To use, open the command prompt then enter the Ping command, followed by the domain name or the IP address of the destination host. TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of rules (protocols to be exact) that governs communication among all computers on the network and Internet. -
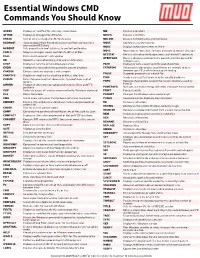
Essentials-Windows-CMD-Command-You-Should-Know-2.Pdf
https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15- cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- know/Essential https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ Windows CMD https://www.makeuseof.com/ tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every- windows-user-know/Commands https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ You Should Know https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- commands-every-windows-user-know/ASSOC Displays or modifies file extension associations https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-MD Creates a directory know/ATTRIB https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/Displays or changes file attributes MKDIR Creates a directory https://www.makeuseof.com/ tag/15-cmd-commands-every-windows-user-know/BREAK Sets or clears extended CTRL+C checking https://www.makeuseof.com/tag/15-cmd-commands-every-MKLINK Creates Symbolic Links and Hard Links windows-user-know/BCDBOOT Used to copy criticalhttps://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ files to the system partition and to crate a MODE Configures a system device https:// new system BCD store www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/MORE Displays https://www.makeuseof.com/tag/15-cmd- output one screen at a time BCDEDIT Sets -

Troubleshooting with the Command Line
The command line contains a powerful suite of tools that can be utilised in a variety of ways. This guide will show you how to use some common tools to diagnose issues with websites, domain names and DNS. Introduction ........................................................................................................................ 2 Overview of the command line tools .................................................................................... 2 Accessing and setting up the command line interface ............................................................. 3 Useful Commands ............................................................................................................... 5 Ping ............................................................................................................................................ 5 Whois......................................................................................................................................... 8 NSlookup ................................................................................................................................. 12 Tracert ..................................................................................................................................... 18 Pathping .................................................................................................................................. 20 Netstat .................................................................................................................................... -

Troubleshooting TCP/IP
CHAPTER 14 Troubleshooting TCP/IP One of the primary reasons to study networking is so that you can trouble- shoot a network when problems occur. At this point, you’re probably aware that many puzzle pieces must be in place when a user accesses network resources or just surfs the Internet. If any single piece is not exactly where it should be, the user will be asking for help. With a little bit of knowledge on troubleshooting, you can be the person who identifi es the problem and fi xes it. In this chapter, you’ll learn about key troubleshooting tools. ▶ Using the command prompt ▶ Checking TCP/IP configuration with ipconfig ▶ Troubleshooting connectivity with ping ▶ Identifying routers with tracert ▶ Verifying the routed path with pathping ▶ Viewing TCP/IP statistics with netstat All the trouble- ▶ Installing Telnet shooting commands in this chapter use the command Using the Command Prompt prompt. ▶ Although the Windows graphical user interface (GUI) is easy to use for most end user tasks, it does have some limitations when troubleshooting network connectivity issues. In contrast, the command prompt can be very useful in troubleshooting basic problems. That is, of course, if you know how to use it. ▶ You can launch the command prompt in just about any Windows system by clicking Start, selecting Run, typing cmd in the text box, and pressing Enter. There are many other ways to launch the You have a wealth of help available if you know how to ask. For example, you command prompt, can just enter the Help command to identify the available commands. -

Reference Guide Vmware Vcenter Server Heartbeat 5.5 Update 1
Reference Guide VMware vCenter Server Heartbeat 5.5 Update 2 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document, see http://www.vmware.com/support/pubs. EN-000206-01 Reference Guide You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] Copyright © 2009 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. VMware products are covered by one or more patents listed at http://www.vmware.com/go/patents. VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents About This Book 7 Getting Started 1 Introduction 11 vCenter Server Heartbeat Concepts 11 Server Protection 12 Network Protection 12 Application Protection 12 Performance Protection 13 Data Protection 14 Communications 14 Switchover Process 15 Auto Switchovers 16 Failover Process 17 Recovery from a Failover 17 Installation 2 vCenter Server Heartbeat Implementation 21 Overview 21 Environmental Prerequisites 21 Common Requirements