Essentials-Windows-CMD-Command-You-Should-Know-2.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Network Printing Guide
Network Printing Guide Windows 95/98/Me Configuration Windows 2000 Configuration Windows XP Configuration Windows NT 4.0 Configuration NetWare Configuration Macintosh Configuration Appendix For safe and correct use of this machine, please be sure to read the Safety Information in the Operating Instructions that comes with the machine before you use it. Introduction To get maximum versatility from this machine all operators should carefully read and follow the instruc- tions in this manual. Please keep this manual in a handy place near the machine. Important Contents of this manual are subject to change without prior notice. In no event will the company be li- able for direct, indirect, special, incidental, or consequential damages as a result of handling or oper- ating the machine. Software Version Conventions Used in this Manual • NetWare 3.x means NetWare 3.12 and 3.2. • NetWare 4.x means NetWare 4.1, 4.11 and IntranetWare. Trademarks Apple, AppleTalk, EtherTalk, LaserWriter, Macintosh and Mac are registered trademarks of Apple Computer, Inc. Ethernet is a registered trademark of Xerox Corporation. Microsoft, Windows and Windows NT are registered trademarks of Microsoft Corporation in the United States and/or other countries. Netscape and Netscape Navigator are registered trademarks of Netscape Communications Corpora- tion. Novell, NetWare and NDS are registered trademarks of Novell, Inc. PostScript is a registered trademark of Adobe Systems, Incorporated. Sun is a registered trademark of Sun Microsystems, Inc. SunOS is a trademark of Sun Microsystems, Inc. Other product names used herein are for identification purposes only and might be trademarks of their respective companies. -

Resolving Issues with Network Connectivity
Module 6: Resolving Issues with Network Connectivity Lab: Resolving Network Connectivity Issues (VMs: 10982D-LON-DC1, 10982D-LON-CL1) Exercise 1: Configuring Network Settings Task 1: Verify and configure network settings 1. Switch to LON-CL1. 2. Right-click Start, and then select Windows PowerShell (Admin). 3. At the Windows PowerShell (Admin) command prompt, type the following command, and then press Enter: test-connection LON-DC1 4. At the command prompt, type the following command, and then press Enter: netstat –n 5. If no connections appear, create a connection. To create a connection, in the Type here to search box, type \\LON-DC1 and then press Enter. 6. In File Explorer, double-click NETLOGON. 7. At the command prompt, type the following command, and then press Enter: netstat –n Note: If no connections are present, move on to the next step. 8. Click Start, type Control Panel and then press Enter. 9. In Control Panel, click Network and Internet, and then click Network and Sharing Center. 10. In Network and Sharing Center, click Ethernet. 11. In the Ethernet Status dialog box, click Properties. 12. Click Internet Protocol Version 4 (TCP/IPv4), and then click Properties. 13. In the Properties dialog box, click Obtain an IP address automatically. 14. Click Obtain DNS server address automatically. 15. Click OK to save the changes. 16. In the Ethernet Properties dialog box, click Close. 17. In the Ethernet Status dialog box, click Close. 18. At the Windows PowerShell command prompt, type the following command, and then press Enter: Get-NetIPAddress Task 2: Troubleshoot name resolution 1. -

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Customizing and Extending Powerdesigner SAP Powerdesigner Documentation Collection Content
User Guide PUBLIC SAP PowerDesigner Document Version: 16.6.2 – 2017-01-05 Customizing and Extending PowerDesigner SAP PowerDesigner Documentation Collection Content 1 PowerDesigner Resource Files.................................................... 9 1.1 Opening Resource Files in the Editor.................................................10 1.2 Navigating and Searching in Resource Files............................................ 11 1.3 Editing Resource Files........................................................... 13 1.4 Saving Changes................................................................13 1.5 Sharing and Embedding Resource Files...............................................13 1.6 Creating and Copying Resource Files.................................................14 1.7 Specifying Directories to Search for Resource Files.......................................15 1.8 Comparing Resource Files........................................................ 15 1.9 Merging Resource Files.......................................................... 16 2 Extension Files................................................................18 2.1 Creating an Extension File.........................................................19 2.2 Attaching Extensions to a Model....................................................20 2.3 Exporting an Embedded Extension File for Sharing.......................................21 2.4 Extension File Properties......................................................... 21 2.5 Example: Adding a New Attribute from a Property -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

Užitečné Postupy Pro Windows a Office Nepublikované V Oficiální Literatuře Artur Cimbálník
UNIVERZITA PARDUBICE Fakulta elektrotechniky a informatiky Užitečné postupy pro Windows a Office nepublikované v oficiální literatuře Artur Cimbálník Bakalářská práce 2011 Prohlášení autora Prohlašuji, ţe jsem tuto práci vypracoval samostatně. Veškeré literární prameny a informace, které jsem v práci vyuţil, jsou uvedeny v seznamu pouţité literatury. Byl jsem seznámen s tím, ţe se na moji práci vztahují práva a povinnosti vyplývající ze zákona č. 121/2000 Sb., autorský zákon, zejména se skutečností, ţe Univerzita Pardubice má právo na uzavření licenční smlouvy o uţití této práce jako školního díla podle § 60 odst. 1 autorského zákona, a s tím, ţe pokud dojde k uţití této práce mnou nebo bude poskytnuta licence o uţití jinému subjektu, je Univerzita Pardubice oprávněna ode mne poţadovat přiměřený příspěvek na úhradu nákladů, které na vytvoření díla vynaloţila, a to podle okolností aţ do jejich skutečné výše. Souhlasím s prezenčním zpřístupněním své práce v Univerzitní knihovně. V Pardubicích dne 29. 04. 2011 Artur Cimbálník Poděkování Tímto bych chtěl poděkovat doc. Ing Milanu Javůrkovi, CSc., vedoucímu mé bakalářské práce za pomoc při shánění materiálu a jeho rady při psaní tohoto textu. Anotace Práce se zabývá testováním postupů racionalizujících práci ve Windows a programech Microsoft Office. Jsou zde popsány jednotlivé pracovní postupy doplněné grafickými obrazovkami a popisem dané problematiky. Dále hodnotí jednotlivé verze kancelářských balíků Microsoft Office. Klíčová slova Office, Word, Excel, Windows, tipy, postupy, rady Title Useful procedures for Windows and Office unpublished in the official literature. Annotation Bachelor thesis deals with the testing of procedures rationalizing work in Windows and Microsoft Office. There are describing individual work procedures with graphic screens. -

Networker Jukebox Control Command Nsrjb
Maintenance Procedures NSRJB ( 8 ) NAME nsrjb − NetWorker jukebox control command SYNOPSIS nsrjb [ −C ][−j name ][−s server ][−v ][−f device ][−S slots | −T Ta gs | volume names ] nsrjb −L [ −j name ][−s server ][−gimnqvG ][−Y | −N ][−R | −B ][−b pool ][−f device | −J hostname ][−e forev er ][−c capacity ][−o mode ][−S slots | −T tags | volume names ] nsrjb −l [ −j name ][−s server ][−nvqrG ][−R [ −b pool ]][−f device | −J hostname ][−S slot | −T tags | volume names ] nsrjb −u [ −j name ][−s server ][−qv ][−f device ][−S slot | −T tags | volume names ] nsrjb −I [ −j name ][−s server ][−Evpq ][−I | −f device ][−S slots | −T tags | volume_names ] nsrjb −p [ −j name ][−s server ][−vq ][−f device ][−S slot | −T tag | volume name ] nsrjb −o mode [ −j name ][−s server ][−Y ][−S slots | −T tags | volume names ] nsrjb −H [ −j name ][−s server ][−EHvp ] nsrjb −h [ −j name ][−s server ][−v ] nsrjb −U uses [ −j name ][−s server ][−S slots | −T tags ] nsrjb −V [ −j name ][−s server ] nsrjb −d [ −j name ][−s server ][−v ][−N ][−Y ][−P ports ][−S slots ][−T tags ][volume names ] nsrjb −w [ −j name ][−s server ][−v ][−N ][−Y ][−P ports ][−S slots | −T tags | volume names ] nsrjb −a [ −j name ][−s server ][−vd ][−T tags |[−T tags ] volume names ] nsrjb −x [ −j name ][−s server ][−vwX ][−T tags | −S slots ] nsrjb −F [ −j name ][−s server ][−v ] −f device DESCRIPTION The nsrjb program manages resources in two broad classes of jukeboxes, remotely managed jukeboxes and locally managed jukeboxes. Remotely managed jukeboxes are controlled through an external agent. -

Arc Hydro Geoprocessing Tools - Tutorial
Arc Hydro Geoprocessing Tools - Tutorial Version 2.0 – October 2011 ESRI 380 New York St., Redlands, CA 92373-8100, USA TEL 909-793-2853 FAX 909-793-5953 E-MAIL [email protected] WEB www.esri.com Arc Hydro GP Tools v 2.0 – Tutorial Copyright © 2011 Esri All rights reserved. Printed in the United States of America. The information contained in this document is the exclusive property of Esri. This work is protected under United States copyright law and other international copyright treaties and conventions. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or by any information storage or retrieval system, except as expressly permitted in writing by Esri. All requests should be sent to Attention: Contracts Manager, Esri, 380 New York Street, Redlands, CA 92373-8100, USA. The information contained in this document is subject to change without notice. October 2011 i Arc Hydro GP Tools v 2.0 – Tutorial Table of Contents Introduction 5 Objective 5 Loading Arc Hydro Tools Toolbox 5 Accessing the Arc Hydro Geoprocessing Tools Help 7 Arc Hydro Tools Configuration 9 Arc Hydro Setup 10 1. Set Target Locations 10 2. Set Batch Target Locations 13 3. Standard Geoprocessing Configuration 15 Terrain Preprocessing 16 1. Level DEM 17 2. DEM Reconditioning 22 3. Assign Stream Slope 25 4. Burn Stream Slope 27 5. Build Walls 28 6. Sink Prescreening 29 7. Sink Evaluation 29 8. Sink Selection 31 9. Fill Sinks 32 10. Flow Direction 33 11. -

LAB MANUAL for Computer Network
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design, troubleshooting, modeling and evaluation of computer networks. In this course, students are going to experiment in a real test-bed networking environment, and learn about network design and troubleshooting topics and tools such as: network addressing, Address Resolution Protocol (ARP), basic troubleshooting tools (e.g. ping, ICMP), IP routing (e,g, RIP), route discovery (e.g. traceroute), TCP and UDP, IP fragmentation and many others. Student will also be introduced to the network modeling and simulation, and they will have the opportunity to build some simple networking models using the tool and perform simulations that will help them evaluate their design approaches and expected network performance. S.No Experiment 1 Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. 2 Study of Network Devices in Detail. 3 Study of network IP. 4 Connect the computers in Local Area Network. 5 Study of basic network command and Network configuration commands. 6 Configure a Network topology using packet tracer software. 7 Configure a Network topology using packet tracer software. 8 Configure a Network using Distance Vector Routing protocol. 9 Configure Network using Link State Vector Routing protocol. Hardware and Software Requirement Hardware Requirement RJ-45 connector, Climping Tool, Twisted pair Cable Software Requirement Command Prompt And Packet Tracer. EXPERIMENT-1 Aim: Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. -
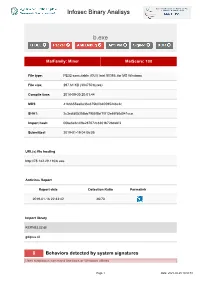
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

Command Control Interface Command Reference
Command Control Interface Command Reference Hitachi Virtual Storage Platform G1000 Hitachi Unified Storage VM Hitachi Virtual Storage Platform Hitachi Universal Storage Platform V/VM FASTFIND LINKS Contents Product Version Getting Help MK-90RD7009-19 © 2010-2014 Hitachi, Ltd. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or stored in a database or retrieval system for any purpose without the express written permission of Hitachi, Ltd. Hitachi, Ltd., reserves the right to make changes to this document at any time without notice and assumes no responsibility for its use. This document contains the most current information available at the time of publication. When new or revised information becomes available, this entire document will be updated and distributed to all registered users. Some of the features described in this document might not be currently available. Refer to the most recent product announcement for information about feature and product availability, or contact Hitachi Data Systems Corporation at https://portal.hds.com. Notice: Hitachi, Ltd., products and services can be ordered only under the terms and conditions of the applicable Hitachi Data Systems Corporation agreements. The use of Hitachi, Ltd., products is governed by the terms of your agreements with Hitachi Data Systems Corporation. Notice on Export Controls. The technical data and technology inherent in this Document may be subject to U.S. export control laws, including the U.S. Export Administration Act and its associated regulations, and may be subject to export or import regulations in other countries. -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information.