Deliverable Title
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wireless Technologies for the Next-Generation Train Control and Monitoring System
Wireless Technologies for the Next-Generation Train Control and Monitoring System Jérôme Härri Aitor Arriola Pedro Aljama Communication Systems Communication Systems Communication Systems EURECOM Ikerlan Ikerlan Sophia-Antipolis, France Arrasate-Mondragón, Spain Arrasate-Mondragón, Spain [email protected] [email protected] [email protected] Igor Lopez Uwe Fuhr Marvin Straub Technology Division TCMS Communcations TCMS Communcations CAF R&D Bombardier Transportation Bombardier Transportation Beasain, Spain Mannheim, Germany Mannheim, Germany [email protected] [email protected] [email protected] Abstract—The Next Generation Train Control and functionalities (e.g. [4]). Yet, a study introducing the global Monitoring System (NG-TCMS) represents a major innovation NG-TCMS requirements and matching with a technology- of the European Railway industry introducing a wireless agnostic survey of various available wireless technologies is architecture as an enabler to enhanced automation, flexible train still missing. management and increased railway capacity. This paper surveys various available and future wireless technologies matching the In this paper, we describe the vision and functionalities of requirements both at train backbone and consist levels. the NG-TCMS, putting into perspective the performance Illustrating the challenges for a single technology to match all requirements of wireless links for the WLTB and WLCN with requirements, this paper also highlights the benefits of the the performance of selected wireless technologies. Our upcoming 5G technology for future NG-TCMS. contributions are threefold: (i) we introduce the future NG- TCMS, in particular the WLTB and WLCN, (ii) we provide a Keywords—5G-V2X, LTE-V2X, Wireless Train Backbone, technology-agnostic comparison of selected technologies Wireless Consist Network, 5G, NG-TCMS. -

What's New from the OPC Foundation?
Interoperability on the Next Level: OPC-Unified Architecture JAI2010 18.11.2010 – Vigo Stefan Hoppe President OPC Europe [email protected] Agenda • Introduction OPC Foundation • OPC UA details • Advantages of Combined Standards • Demo OPC Foundation • International Industry Standard Organization • OPC Foundation • 407+ Member Companies / 80+ end-users Members • OPC Portfolio • 3500 + Total Companies Build OPC Products = 22000 + Products • OPC UA details • Millions & Millions of OPC Installations • Cooperation • The vision of OPC is secure reliable multi-vendor multi-platform interoperability • for moving information vertically from the data sources through the enterprise of multi-vendor systems (with stops in between…) • For moving information horizontally between data sources on different industrial networks from different vendors; • Not just data but information……. • Reliable, Secure Interoperability is not an option • Collaboration is key to incorporating many multiple “open” standards into an unified open platform architecture World Membership Demographics • OPC Foundation OPC Members By Region • OPC Portfolio • OPC UA details Rest of World , • Cooperation 41 China , 5 China Europe North America Europe , 216 Japan , 142 North America Rest of World Japan , 36 OPC Board of Directors • Reinhold Achatz, Siemens • OPC Foundation • OPC Portfolio Reinhold has been on the OPC Board of Directors longer • OPC UA details than any other board member, he is the founding member for Siemens on the Board of Directors (1997) • Cooperation -

SMART HOME SYSTEMS with the Contribution Of
Branko Dvoršak Juraj Havelka Elena Mainardi Hrvoje Pandžić Tea Selič Mario Tretinjak SMART HOME SYSTEMS With the contribution of: Vanja Husein Claudia Pacchiega Goran Švast 2 This publication is part of the SHVET project (https://www.smart-hvet.eu/), and has been made possible with the contribution of (in alphabetical order): Center Republike Slovenije za poklicno Izobraževanje (Slovenia) Centoform (Italy) Ecipa Nordest (Italy) Območna Obrtno-Podjetniška zbornica Krško (Slovenia) Obrtničko učilište – ustanova za obrazovanje odraslih (Croatia) Šolski center Novo mesto (Slovenia) Sveučilište u Zagrebu Fakultet elektrotehnike i računarstva (Croatia) This project has been funded with support from the European Commission. This publication reflects the views only of the authors and the Commission cannot be held responsible for any use which may be made of the information contained therein. 3 TABLE OF CONTENTS page 1 INTRODUCTION 4 1.1 WHAT EXACTLY IS A "SMART HOUSE" 5 1.2 HOME AND BUILDING AUTOMATION 6 1.3 FUNCTIONS YOU CAN DO WITH A SMART HOME SYSTEM 6 2 DIFFERENCE BETWEEN A SMART HOME SYSTEM AND A STANDARD ELECTRIC PLANT 13 2.1 ELEMENTS OF A CLASSIC RESIDENTIAL INSTALLATION 13 2.2 STRUCTURE OF A SMART HOME SYSTEM 18 2.3 MODULES OF A SMART HOME SYSTEM 20 3 SMART HOME SYSTEM TECHNOLOGIES 26 3.1 OVERVIEW OF AUTOMATION AND CONTROL TECHNOLOGIES 25 3.2 WHY KONNEX 28 4 KONNEX 30 4.1 HISTORY OF KNX/EIB AND KONNEX ORGANIZATION 30 4.2 TRANSMISSION MEDIA 30 4.3 NET ARCHITECTURE 32 4.4 TOPOLOGY 35 4.5 ADDRESSES 36 4.6 TELEGRAM 38 4.7 PARAMETERIZATION -

Universidad Nacional De Chimborazo Facultad De Ingeniería Carrera De Electrónica Y Telecomunicaciones
UNIVERSIDAD NACIONAL DE CHIMBORAZO FACULTAD DE INGENIERÍA CARRERA DE ELECTRÓNICA Y TELECOMUNICACIONES Proyecto de Investigación previo a la obtención del título de Ingeniero en Electrónica y Telecomunicaciones TRABAJO DE TITULACIÓN DISEÑO Y SIMULACIÓN DE UNA RED DE COMUNICACIÓN EN VAGONES DE FERROCARRILES A TRAVÉS DE LA UTILIZACIÓN DE LOS ESTÁNDARES IEC 61375 PARA LA RUTA TREN DEL HIELO I (RIOBAMBA – URBINA – LA MOYA – RIOBAMBA) Autor: Denis Andrés Maigualema Quimbita Tutor: Ing. PhD. Ciro Diego Radicelli García Riobamba - Ecuador Año 2020 I Los miembros del tribunal de graduación del proyecto de investigación de título: “DISEÑO Y SIMULACIÓN DE UNA RED DE COMUNICACIÓN EN VAGONES DE FERROCARRILES A TRAVÉS DE LA UTILIZACIÓN DE LOS ESTÁNDARES IEC 61375 PARA LA RUTA TREN DEL HIELO I (RIOBAMBA – URBINA – LA MOYA – RIOBAMBA)”, presentado por: Denis Andrés Maigualema Quimbita, y dirigido por el Ing. PhD. Ciro Diego Radicelli García. Una vez revisado el informe final del proyecto de investigación con fines de graduación escrito en el cual consta el cumplimento de las observaciones realizadas, remite la presente para uso y custodia en la Biblioteca de la Facultad de Ingeniería de la UNACH. Para constancia de lo expuesto firman. Ing. PhD. Ciro Radicelli Tutor Dr. Marlon Basantes Miembro del tribunal Ing. José Jinez Miembro del tribunal II DECLARACIÓN EXPUESTA DE TUTORÍA En calidad de tutor del tema de investigación: “DISEÑO Y SIMULACIÓN DE UNA RED DE COMUNICACIÓN EN VAGONES DE FERROCARRILES A TRAVÉS DE LA UTILIZACIÓN DE LOS ESTÁNDARES IEC 61375 PARA LA RUTA TREN DEL HIELO I (RIOBAMBA – URBINA – LA MOYA – RIOBAMBA ". Realizado por el Sr. -

Innovative Monitoring and Predictive Maintenance Solutions on Lightweight Wagon
Innovative Monitoring and Predictive Maintenance Solutions on Lightweight Wagon Grant Agreement no.: 730863 - S2R-OC-IP5-03-2015 Project Start Date: 01/11/2016 Project End Date: 30/04/2019 DELIVERABLE D1.1 Benchmark and market drivers for an integrated intelligent and lightweight wagon solution Work Package: WP 1 Deliverable type R Dissemination Level: PU Status: Final Leader beneficiary: UNEW Due date of deliverable: 31/03/2017 Actual submission date: 31/03/2017 Prepared by: Cristian Ulianov and Paul Hyde, Newcastle University (UNEW) Contributors: Sian Evans, Newcastle University (UNEW) Liang Cheng, Newcastle University (UNEW) Emmanuel Matsika, Newcastle University (UNEW) Raluca Marin-Perianu, Inertia Technology B.V. (INE) Martin Wischner, Havelländische Eisenbahn AG (HVLE) Daniele Regazzi, Lucchini RS S.p.A. (LRS) Franco Castagnetti, NewOpera Aisbl (NEWO) Giuseppe Rizzi, NewOpera Aisbl (NEWO) David Vincent, Perpetuum Ltd. (PER) Stefano Bruni, Politecnico di Milano (POLIM) Marco Macchi, Politecnico di Milano (POLIM) Dachuan Shi, Technische Universität Berlin (TUB) Philipp Krause, Technische Universität Berlin (TUB) Florentin Barbuceanu, Uzina de Vagoane Aiud S.A. (UVA) Verified by: Cristian Ulianov Deliverable D1.1 Document history Version Date Author(s) Description D1 02/12/2016 Cristian Ulianov [UNEW] Document initiated, draft structure D2 20/12/2016 Cristian Ulianov [UNEW] Document updated, structure and Paul Hyde [UNEW] content proposed D3 24/01/2017 All Update of structure and content D5 23/02/2017 All Content added and revised -

SEW Eurodrive MOVITRAC 31 INTERBUS Fieldbus Interface Manual
T MOVITRAC® 31.. Frequency Inverters INTERBUS Fieldbus Interface (FFI31.. option and size 0/INTERBUS) Manual Edition 1/99 08/198/96 U U C ® L ® L 0922 6915/ 199 Important Notes Important Notes • Read this user manual carefully before you start installation and commissioning work on MOVITRAC® frequency inverters with fieldbus options. This user manual assumes that the user is familiar with and has at his disposal all relevant documentation on the MOVITRAC® system, particularly the installation and operating instructions. • Safety notes: Always follow the safety notes contained in this user manual. Safety notes are marked as follows: Electrical hazard, e.g. during live working Mechanical hazard, e.g. when working on hoists. Important instructions for the safe and fault-free operation of the system, e.g. pre- setting before commissioning.Failure to follow these instructions may result in injury to people and damage to property. • General safety notes for bus systems: The fieldbus option gives you a communications system which allows you to match the MOVITRAC® 31.. drive system to the specifics of your application to a very high degree. As with all bus systems there is, however, the risk of parameters being changed, which will not show outside (i.e. the inverter) but affect the behaviour of the inverter. This may result in unexpected (not uncontrolled, though) system behaviour. • In these instructions, cross-references are marked with an →, e.g., (→ MC_SHELL) means: Please refer to the MC_SHELL User Manual for detailed information or information on how to carry out this instruction. (→ section x.x) means: Further information can be found in section x.x of this user manual. -
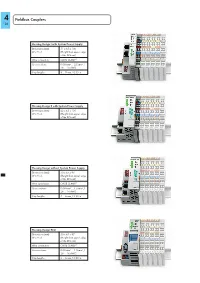
Fieldbus Couplers
4 Fieldbus Couple rs 126 Housing Design I with System Powe r Supply Dimensions (mm) 51 x 65 x 100 W x H x L (Height from upper edge of the DIN-rail) Wire connection CAGE CLAMP ® Cross sections 0.08 mm² ... 2.5 mm² / 28 ... 14 AWG Strip lengths 8 ... 9 mm / 0.33 in. Housing Design II with System Powe r Supply Dimensions (mm) 62 x 65 x 100 W x H x L (Height from upper edge of the DIN-rail) Housing Design without System Powe r Supply Dimensions (mm) 50 x 65 x 97 W x H x L (Height from upper edge of the DIN-rail) Wire connection CAGE CLAMP ® Cross sections 0.08 mm² ... 1.5 mm² / 28 ... 14 AWG Strip lengths 5 ... 6 mm / 0.22 in. Housing Design ECO Dimensions (mm) 50 x 65 x 97 W x H x L (Height from upper edge of the DIN-rail) Wire connection CAGE CLAMP ® Cross sections 0.08 mm² ... 1.5 mm² / 28 ... 16 AWG Strip lengths 5 ... 6 mm / 0.22 in. Modula r I/O- System Ove rview 4 r Fieldbus Couple s 127 Housing Design without System with System Power Supply Power Supply ECO Fi eldbus System Desc ription Item No. Page Fieldbus Couple r, 100 Mbit 750-340 128 Fieldbus Couple r, 2-port, 100 Mbit 750-370 130 Fieldbus Couple r, advanced, 2-port 750-375 132 Fieldbus Couple r, advanced, 2-port, extended operating temperature range: -20 °C ... +60 °C 750-375/025-000 132 Fieldbus Couple r, advanced, ECO, 2-port 750-377 134 Fieldbus Couple r, advanced, ECO, 2-port, extended operating temperature range: -20 °C .. -

Phoenix Contact Automation Catalog
I/O systems in the IP65/67 field 342 PHOENIX CONTACT Courtesy of Steven Engineering, Inc.-230 Ryan Way, South San Francisco, CA 94080-6370 Main Office: (650) 588-9200-Outside Local Area: (800) 258-9200-www.stevenengineering.com Inhalt 97% Breite skaliert I/O systems in the IP65/67 field More flexible – smaller – faster – better value Program overview Phoenix Contact is actively pursuing these trends with innovative I/O systems Fieldline Stand-Alone 345 for perfect solutions in field wiring and control cabinet construction. Fieldline Modular 361 Fieldline Stand-Alone Fieldline Extension AS-Interface 385 Fieldline Stand-Alone is optimally suitable for recording digital inputs and Rugged Line 401 outputs in harsh ambient conditions in machine and system engineering. Fieldline Stand-Alone is the compact design of the Fieldline I/O system. The combination of Manuals, data sheets, application notes and configuration files input/output modules makes a simple can be found in the download area at www.phoenixcontact.net/ connection of commonly used sensors and download. actuators possible. A Fieldline Stand-Alone IO-Link master has been added to the Fieldline Stand-Alone product range. Use of the IO-Link technology enables seamless You can find information regarding our product and solution-oriented communication from the controller services from page 11 onwards as well as in our online catalog to the sensor/actuator level. (www.phoenixcontact.net/eshop). Fieldline Modular Fieldline Modular offers a cost-effective and high-performance modular solution for complex I/O functions of field wiring. A Fieldline Modular IO-Link master is now available in the Fieldline Modular product range as well. -

Industrielle Bussysteme : Ethernet • Ethernet Link Schicht • Medium Access Control • Logical Link Control – LLC Dr
Inhalt • Ethernet Übersicht und Protokolle • Ethernet Schicht-1 Industrielle Bussysteme : Ethernet • Ethernet Link Schicht • Medium Access Control • Logical Link Control – LLC Dr. Leonhard Stiegler Automation • Ergänzende LAN Protokolle www.dhbw-stuttgart.de Industrielle Bussysteme , Teil 1 – Ethernet, L.Stiegler , 1 5. Semester, Automation, 2015 Industrielle Bussysteme , Teil 1 – Ethernet, L.Stiegler , 2 5. Semester, Automation, 2015 Definitionen IEEE 802 Standardisierung Ein Computernetz ist eine Zusammenschaltung von Host-Rechnern, die 802.1 LAN/MAN Architecture Informationen austauschen über WGs: Interworking, - Übertragungsverbindungen und Security, Audio/Video Bridging and Netzknoten - Congestion Management. Ein Lokales Netz (LAN) umfasst in der Regel einen begrenzten 802.2 : Logical Link Control (LLC) geografischen Bereich, wie z.B. ein Gebäude, Stockwerk oder einen 802.3 : Ethernet Campus Basic Ethernet 10 Mbit/s Ethernet ist eine weit verbreitete LAN Technologie. Sie definiert Fast Ethernet 100 Mbit/s over copper or fibre Gbit-Ethernet 1 Gbit/s over copper or fibre - das Übertragungsmedium 10G-Ethernet 10 Gbit/s over optical fibres - den Zugang zum Medium 802.11 : WLAN - die physikalischen Übertragungseigensaften und Prozeduren 802.16 : WMAN Ethernet ist Teil der Standardisierungsfamilie 802 802.17 : Resilient Packet Ring Industrielle Bussysteme , Teil 1 – Ethernet, L.Stiegler , 3 5. Semester, Automation, 2015 Industrielle Bussysteme , Teil 1 – Ethernet, L.Stiegler , 4 5. Semester, Automation, 2015 IEEE 802.3 Standards LAN Characteristika -

Industrial Networking Solutions for Mission Critical Applications
www.hirschmann.com GLOBAL LOCATIONS Industrial Networking Solutions for Mission Critical Applications For more information, please visit us at: www.belden.com/hirschmann Industrial Networking Solutions for Mission Critical Applications Critical Mission Industrial for Networking Solutions UNITED STATES CANADA LATIN AMERICA and the CARIBBEAN ISLANDS Division Headquarters Industrial Networking National Business Regional Office – Americas (Hirschmann/GarrettCom/ Center 6100 Hollywood Boulevard 2200 U.S. Highway 27 South Tofino Security) 2280 Alfred-Nobel Suite 110 Richmond, IN 47374 255 Fourier Ave. Suite 200 Hollywood, Florida 33024 Phone: 765-983-5200 Fremont, CA 94539, USA Saint-Laurent, QC Phone: 954-987-5044 Canada H4S 2A4 Inside Sales: 800-235-3361 Phone: 510-438-9071 Fax: 954-987-8022 Fax: 765-983-5294 Fax: 510-952-3456 Phone: 514-822-2345 [email protected] [email protected] www.belden.com Fax: 514-822-7979 www.belden.com [email protected] Belden 2200 U.S. Highway 27 South Richmond, IN 47374a Inside Sales: 1-800-BELDEN-1 (1-800-235-3361) Industry-specific solutions that can Phone: 765-983-5200 Fax: 765-983-5294 improve productivity and operational [email protected] efficiency today, while laying the foundations for tomorrow‘s IIoT opportunities. Belden, Belden Sending All The Right Signals, GarrettCom, Hirschmann, Lumberg Automation, Tofino Security, Tripwire and the Belden logo are trademarks or registered trademarks of Belden Inc. or its affiliated companies in the United States and other jurisdictions. Belden and other parties may also have trademark rights in other terms used herein. Edition 2017 ©Copyright 2017, Belden Inc. Edition 2017 Printed in Germany HIRSCHMANN-INDUSTRIAL-NETWORKING-SOLUTIONS_CA_INIT_HIR_0117_A_AG Prepare your infrastructure for the Industrial Internet of Things (IIoT) The IIoT is widely considered to be one of the primary trends affecting industrial businesses today and in the future. -

Instruction Manual Universal Fieldbus-Gateway UNIGATE® IC- Interbus
your ticket to all buses Instruction Manual Universal Fieldbus-Gateway UNIGATE® IC- Interbus Manual Art.-No.: V3317E Deutschmann Automation GmbH & Co. KG | Carl-Zeiss-Str. 8 | D-65520 Bad Camberg Tel:+49 6434 9433-0 | Hotline: +49 6434 9433-33 | Fax: +49 6434 9433-40 www.deutschmann.com Deutschmann Automation GmbH & Co. KG 1 General introduction . 9 2 The UNIGATE® IC . 10 2.1 Technical introduction . 10 2.2 Availability . 10 2.3 Firmware . 10 2.4 The serial standard interface . 10 2.5 The synchronous serial interface . 10 2.6 The Debug-interface . 10 2.7 UNIGATE® IC hardware survey . 11 3 Hardware design. 12 3.1 Ports . 12 3.2 Pinout . 12 3.2.1 -Boot enable . 13 3.2.2 Load out (SPI-Master: SS0-) . 13 3.2.3 Data out (SPI-Master: SS1-). 13 3.2.4 Data In (SPI: MISO) . 13 3.2.5 Load In (SPI: MOSI) . 13 3.2.6 Clock. 13 3.2.7 -Reset In . 14 3.2.8 LED RESREG-, RBDA, BA . 14 3.2.9 -Config Mode . 14 3.2.10 DbgTX, DbgRx. 14 3.2.11 TE . 14 3.2.12 TX, RX . 14 3.3 Software . 14 3.3.1 Basic line of proceeding . 15 3.4 Connection examples . 15 3.5 Layout examples . 18 3.6 Handling (mounting the UNIGATE® IC on the carrier board) . 20 4 The serial interface . 21 4.1 Overview . 21 4.2 Initialization of the serial interface . 21 4.3 Use of the serial interface . 21 4.4 Further operation modes . -

A Survey of Channel Measurements and Models
A Survey of Channel Measurements and Models for Current and Future Railway Communication Systems Paul Unterhuber, Stephan Pfletschinger, Stephan Sand, Mohamed Soliman, Thomas Jost, Aitor Arriola, Inaki Val, Cristina Cruces, Juan Moreno, Juan Pablo Garcia-Nieto, et al. To cite this version: Paul Unterhuber, Stephan Pfletschinger, Stephan Sand, Mohamed Soliman, Thomas Jost, et al.. A Survey of Channel Measurements and Models for Current and Future Railway Com- munication Systems. Mobile Information Systems, Hindawi/IOS Press, 2016, 2016, pp.7308604. 10.1155/2016/7308604. hal-01578998 HAL Id: hal-01578998 https://hal.archives-ouvertes.fr/hal-01578998 Submitted on 30 Aug 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Hindawi Publishing Corporation Mobile Information Systems Volume 2016, Article ID 7308604, 14 pages http://dx.doi.org/10.1155/2016/7308604 Review Article A Survey of Channel Measurements and Models for Current and Future Railway Communication Systems Paul Unterhuber,1 Stephan Pfletschinger,1 Stephan Sand,1 Mohammad Soliman,1 Thomas Jost,1 Aitor Arriola,2 Iñaki Val,2 Cristina Cruces,2 Juan Moreno,3 Juan Pablo García-Nieto,3 Carlos Rodríguez,3 Marion Berbineau,4 Eneko Echeverría,5 and Imanol Baz5 1 German Aerospace Center (DLR), Oberpfaffenhofen, 82234 Wessling, Germany 2IK4-IKERLAN, Arizmendiarrieta 2, 20500 Mondragon, Spain 3MetrodeMadrid(MDM),CalleCavanilles58,28007Madrid,Spain 4Universite´ Lille Nord de France, IFSTTAR, COSYS, 59650 Villeneuve d’Ascq, France 5Construcciones y Auxiliar de Ferrocarriles (CAF), J.M.