CSC 370 – Computer Architecture and Organization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
E0C88 CORE CPU MANUAL NOTICE No Part of This Material May Be Reproduced Or Duplicated in Any Form Or by Any Means Without the Written Permission of Seiko Epson
MF658-04 CMOS 8-BIT SINGLE CHIP MICROCOMPUTER E0C88 Family E0C88 CORE CPU MANUAL NOTICE No part of this material may be reproduced or duplicated in any form or by any means without the written permission of Seiko Epson. Seiko Epson reserves the right to make changes to this material without notice. Seiko Epson does not assume any liability of any kind arising out of any inaccuracies contained in this material or due to its application or use in any product or circuit and, further, there is no representation that this material is applicable to products requiring high level reliability, such as medical products. Moreover, no license to any intellectual property rights is granted by implication or otherwise, and there is no representation or warranty that anything made in accordance with this material will be free from any patent or copyright infringement of a third party. This material or portions thereof may contain technology or the subject relating to strategic products under the control of the Foreign Exchange and Foreign Trade Control Law of Japan and may require an export license from the Ministry of International Trade and Industry or other approval from another government agency. Please note that "E0C" is the new name for the old product "SMC". If "SMC" appears in other manuals understand that it now reads "E0C". © SEIKO EPSON CORPORATION 1999 All rights reserved. CONTENTS E0C88 Core CPU Manual PREFACE This manual explains the architecture, operation and instruction of the core CPU E0C88 of the CMOS 8-bit single chip microcomputer E0C88 Family. Also, since the memory configuration and the peripheral circuit configuration is different for each device of the E0C88 Family, you should refer to the respective manuals for specific details other than the basic functions. -

X86 Assembly Language Syllabus for Subject: Assembly (Machine) Language
VŠB - Technical University of Ostrava Department of Computer Science, FEECS x86 Assembly Language Syllabus for Subject: Assembly (Machine) Language Ing. Petr Olivka, Ph.D. 2021 e-mail: [email protected] http://poli.cs.vsb.cz Contents 1 Processor Intel i486 and Higher – 32-bit Mode3 1.1 Registers of i486.........................3 1.2 Addressing............................6 1.3 Assembly Language, Machine Code...............6 1.4 Data Types............................6 2 Linking Assembly and C Language Programs7 2.1 Linking C and C Module....................7 2.2 Linking C and ASM Module................... 10 2.3 Variables in Assembly Language................ 11 3 Instruction Set 14 3.1 Moving Instruction........................ 14 3.2 Logical and Bitwise Instruction................. 16 3.3 Arithmetical Instruction..................... 18 3.4 Jump Instructions........................ 20 3.5 String Instructions........................ 21 3.6 Control and Auxiliary Instructions............... 23 3.7 Multiplication and Division Instructions............ 24 4 32-bit Interfacing to C Language 25 4.1 Return Values from Functions.................. 25 4.2 Rules of Registers Usage..................... 25 4.3 Calling Function with Arguments................ 26 4.3.1 Order of Passed Arguments............... 26 4.3.2 Calling the Function and Set Register EBP...... 27 4.3.3 Access to Arguments and Local Variables....... 28 4.3.4 Return from Function, the Stack Cleanup....... 28 4.3.5 Function Example.................... 29 4.4 Typical Examples of Arguments Passed to Functions..... 30 4.5 The Example of Using String Instructions........... 34 5 AMD and Intel x86 Processors – 64-bit Mode 36 5.1 Registers.............................. 36 5.2 Addressing in 64-bit Mode.................... 37 6 64-bit Interfacing to C Language 37 6.1 Return Values.......................... -

(PSW). Seven Bits Remain Unused While the Rest Nine Are Used
8086/8088MP INSTRUCTOR: ABDULMUTTALIB A. H. ALDOURI The Flags Register It is a 16-bit register, also called Program Status Word (PSW). Seven bits remain unused while the rest nine are used. Six are status flags and three are control flags. The control flags can be set/reset by the programmer. 1. DF (Direction Flag) : controls the direction of operation of string instructions. (DF=0 Ascending order DF=1 Descending order) 2. IF (Interrupt Flag): controls the interrupt operation in 8086µP. (IF=0 Disable interrupt IF=1 Enable interrupt) 3. TF (Trap Flag): controls the operation of the microprocessor. (TF=0 Normal operation TF=1 Single Step operation) The status flags are set/reset depending on the results of some arithmetic or logical operations during program execution. 1. CF (Carry Flag) is set (CF=1) if there is a carry out of the MSB position resulting from an addition operation or subtraction. 2. AF (Auxiliary Carry Flag) AF is set if there is a carry out of bit 3 resulting from an addition operation. 3. SF (Sign Flag) set to 1 when result is negative. When result is positive it is set to 0. 4. ZF (Zero Flag) is set (ZF=1) when result of an arithmetic or logical operation is zero. For non-zero result this flag is reset (ZF=0). 5. PF (Parity Flag) this flag is set to 1 when there is even number of one bits in result, and to 0 when there is odd number of one bits. 6. OF (Overflow Flag) set to 1 when there is a signed overflow. -

Overview of IA-32 Assembly Programming
Overview of IA-32 assembly programming Lars Ailo Bongo University of Tromsø Contents 1 Introduction ...................................................................................................................... 2 2 IA-32 assembly programming.......................................................................................... 3 2.1 Assembly Language Statements................................................................................ 3 2.1 Modes........................................................................................................................4 2.2 Registers....................................................................................................................4 2.2.3 Data Registers .................................................................................................... 4 2.2.4 Pointer and Index Registers................................................................................ 4 2.2.5 Control Registers................................................................................................ 5 2.2.6 Segment registers ............................................................................................... 7 2.3 Addressing................................................................................................................. 7 2.3.1 Bit and Byte Order ............................................................................................. 7 2.3.2 Data Types......................................................................................................... -

The 8086 Microprocessor
11 The 8086 Microprocessor 1. Draw the pin diagram of 8086. Ans. There would be two pin diagrams—one for MIN mode and the other for MAX mode of 8086, shown in Figs. 11.1 and 11.2 respectively. The pins that differ with each other in the two modes are from pin-24 to pin-31 (total 8 pins). GND 1 40 VCC AD –AD 35–38 0 15 2–16 & 39 A/S16 3–A/S 19 6 NMI 17 34 BHE/S7 INTR 18 33 MN/MX CLK 19 32 RD INTEL GND 20 31 HOLD 8086 RESET 21 30 HLDA READY 22 29 WR TEST 23 28 M/IO INTA 24 27 DT/R ALE 25 26 DEN Fig. 11.1: Signals of intel 8086 for minimum mode of operation 2. What is the technology used in 8086 µµµP? Ans. It is manufactured using high performance metal-oxide semiconductor (HMOS) technology. It has approximately 29,000 transistors and housed in a 40-pin DIP package. 3. Mention and explain the modes in which 8086 can operate. Ans. 8086 µP can operate in two modes—MIN mode and MAX mode. When MN/MX pin is high, it operates in MIN mode and when low, 8086 operates in MAX mode. 194 Understanding 8085/8086 Microprocessors and Peripheral ICs through Questions and Answers For a small system in which only one 8086 microprocessor is employed as a CPU, the system operates in MIN mode (Uniprocessor). While if more than one 8086 operate in a system then it is said to operate in MAX mode (Multiprocessor). -

Optimizing Subroutines in Assembly Language an Optimization Guide for X86 Platforms
2. Optimizing subroutines in assembly language An optimization guide for x86 platforms By Agner Fog. Copenhagen University College of Engineering. Copyright © 1996 - 2012. Last updated 2012-02-29. Contents 1 Introduction ....................................................................................................................... 4 1.1 Reasons for using assembly code .............................................................................. 5 1.2 Reasons for not using assembly code ........................................................................ 5 1.3 Microprocessors covered by this manual .................................................................... 6 1.4 Operating systems covered by this manual................................................................. 7 2 Before you start................................................................................................................. 7 2.1 Things to decide before you start programming .......................................................... 7 2.2 Make a test strategy.................................................................................................... 9 2.3 Common coding pitfalls............................................................................................. 10 3 The basics of assembly coding........................................................................................ 12 3.1 Assemblers available ................................................................................................ 12 3.2 Register set -
Assembly Language: IA-X86
Assembly Language for x86 Processors X86 Processor Architecture CS 271 Computer Architecture Purdue University Fort Wayne 1 Outline Basic IA Computer Organization IA-32 Registers Instruction Execution Cycle Basic IA Computer Organization Since the 1940's, the Von Neumann computers contains three key components: Processor, called also the CPU (Central Processing Unit) Memory and Storage Devices I/O Devices Interconnected with one or more buses Data Bus Address Bus data bus Control Bus registers Processor I/O I/O IA: Intel Architecture Memory Device Device (CPU) #1 #2 32-bit (or i386) ALU CU clock control bus address bus Processor The processor consists of Datapath ALU Registers Control unit ALU (Arithmetic logic unit) Performs arithmetic and logic operations Control unit (CU) Generates the control signals required to execute instructions Memory Address Space Address Space is the set of memory locations (bytes) that are addressable Next ... Basic Computer Organization IA-32 Registers Instruction Execution Cycle Registers Registers are high speed memory inside the CPU Eight 32-bit general-purpose registers Six 16-bit segment registers Processor Status Flags (EFLAGS) and Instruction Pointer (EIP) 32-bit General-Purpose Registers EAX EBP EBX ESP ECX ESI EDX EDI 16-bit Segment Registers EFLAGS CS ES SS FS EIP DS GS General-Purpose Registers Used primarily for arithmetic and data movement mov eax 10 ;move constant integer 10 into register eax Specialized uses of Registers eax – Accumulator register Automatically -

Arithmetic Flags and Instructions
Arithmetic Flags and Instructions Chapter 6 S. Dandamudi Outline • Status flags • Application examples ∗ Zero flag ∗ PutInt8 ∗ Carry flag ∗ GetInt8 ∗ Overflow flag • Multiword arithmetic ∗ Sign flag ∗ Addition ∗ Auxiliary flag ∗ Subtraction ∗ Parity flag ∗ Multiplication • Arithmetic instructions ∗ Division ∗ Addition instructions • Performance: Multiword ∗ Subtraction instructions multiplication ∗ Multiplication instructions ∗ Division instructions 1998 S. Dandamudi Arithmetic: Page 2 To be used with S. Dandamudi, “Introduction to Assembly Language Programming,” Springer-Verlag, 1998. Status Flags • Six status flags monitor the outcome of arithmetic, logical, and related operations Flags Register FLAGS 3 2 2 2 1 1 1 1 1 1 1 1 1 1 1 2 1 0 9 8 7 6 5 4 3 2 109 8 7 6 5 4 3 2 1 0 V V I I I A V R N IO O D I T S Z 0 A 0 P 1 C EFLAGS 0 000 000000D P F C M F 0 T PL F F F F F F F F F Status Flags Control Flags System Flags CF = Carry Flag DF = Direction Flag TF = Trap Flag PF = Parity Flag IF = Interrupt Flag AF = Auxiliary Carry Flag IOPL = I/O Privilege Level ZF = Zero Flag NT = Nested Task SF = Sign Flag RF = Resume Flag OF = Overflow Flag VM = Virtual 8086 Mode AC = Alignment Check VIF = Virtual Interrupt Flag VIP = Virtual Interrupt Pending ID = ID Flag Instruction Pointer 31 16 15 0 EIP IP 1998 S. Dandamudi Arithmetic: Page 3 To be used with S. Dandamudi, “Introduction to Assembly Language Programming,” Springer-Verlag, 1998. Status Flags (cont’d) • Status flags are updated to indicate certain properties of the result ∗ Example: If the result is zero, zero flag is set • Once a flag is set, it remains in that state until another instruction that affects the flags is executed • Not all instructions affect all status flags ∗ add and sub affect all six flags ∗ inc and dec affect all but the carry flag ∗ mov, push, and pop do not affect any flags 1998 S. -

Introduction to Assembly a User’S View of Computer Systems
Introduction to Assembly A User’s View of Computer Systems 2 Courtesy: Guide to Assembly Language Programming in Linux, Sivarama P. Dandamudi, 2005 What is Assembly Language ? • Low-level programming language • Influenced by: • The architecture of the processor • The instruction set • Two basic types of processors • CISC (Complex Instruction Set Computers) • RISC (Reduced Instruction Set Computers) • Pentium is an example of a CISC processor • Assembler translates assembly to machine code • NASM is a popular assembler for x86 architecture 3 Advantage of High-Level Languages • Program development is faster • Programs are easier to maintain • Programs are portable so, why to program in the Assembly language ? 4 Why to program in Assembly ? • Efficiency • Time efficiency • Space efficiency • Direct hardware control 5 When is it Useful? • Practical purposes (embedded systems) • Cracking Personal Satisfaction 6 Example _start: mov ecx, [var1] cmp ecx, [var2] ; Data section begins jg check_third_var section .data mov ecx, [var2] var1 dd 40 var2 dd 20 check_third_var: var3 dd 30 cmp ecx, [var3] jg _exit section .text mov ecx, [var3] global _start _exit: mov ebx, ecx mov eax, 1 int 80h 7 IA – 32 Architecture (IA - Intel Architecture, i386) • 32 bit Registers • Logical and Arithmetic instructions (instruction set) • Fetch-decode-execute cycle • Addressing Modes • Registers • Immediate • Direct • Indirect 8 Fetch-decode-execute Fetch Execute Decode 9 Registers 32-bit, 16-bit, and 8-bit registers: . General registers . Control registers . Segment -

Intel X86 Assembly Language & Microarchitecture
Intel x86 Assembly Language & Microarchitecture #x86 Table of Contents About 1 Chapter 1: Getting started with Intel x86 Assembly Language & Microarchitecture 2 Remarks 2 Examples 2 x86 Assembly Language 2 x86 Linux Hello World Example 3 Chapter 2: Assemblers 6 Examples 6 Microsoft Assembler - MASM 6 Intel Assembler 6 AT&T assembler - as 7 Borland's Turbo Assembler - TASM 7 GNU assembler - gas 7 Netwide Assembler - NASM 8 Yet Another Assembler - YASM 9 Chapter 3: Calling Conventions 10 Remarks 10 Resources 10 Examples 10 32-bit cdecl 10 Parameters 10 Return Value 11 Saved and Clobbered Registers 11 64-bit System V 11 Parameters 11 Return Value 11 Saved and Clobbered Registers 11 32-bit stdcall 12 Parameters 12 Return Value 12 Saved and Clobbered Registers 12 32-bit, cdecl — Dealing with Integers 12 As parameters (8, 16, 32 bits) 12 As parameters (64 bits) 12 As return value 13 32-bit, cdecl — Dealing with Floating Point 14 As parameters (float, double) 14 As parameters (long double) 14 As return value 15 64-bit Windows 15 Parameters 15 Return Value 16 Saved and Clobbered Registers 16 Stack alignment 16 32-bit, cdecl — Dealing with Structs 16 Padding 16 As parameters (pass by reference) 17 As parameters (pass by value) 17 As return value 17 Chapter 4: Control Flow 19 Examples 19 Unconditional jumps 19 Relative near jumps 19 Absolute indirect near jumps 19 Absolute far jumps 19 Absolute indirect far jumps 20 Missing jumps 20 Testing conditions 20 Flags 21 Non-destructive tests 21 Signed and unsigned tests 22 Conditional jumps 22 Synonyms and terminology 22 Equality 22 Greater than 23 Less than 24 Specific flags 24 One more conditional jump (extra one) 25 Test arithmetic relations 25 Unsigned integers 25 Signed integers 26 a_label 26 Synonyms 27 Signed unsigned companion codes 27 Chapter 5: Converting decimal strings to integers 28 Remarks 28 Examples 28 IA-32 assembly, GAS, cdecl calling convention 28 MS-DOS, TASM/MASM function to read a 16-bit unsigned integer 29 Read a 16-bit unsigned integer from input. -
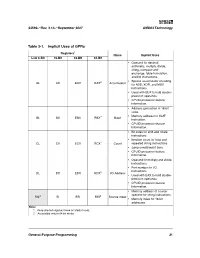
Implicitly Modified Registers
24592—Rev. 3.14—September 2007 AMD64 Technology Table 3-1. Implicit Uses of GPRs Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Operand for decimal arithmetic, multiply, divide, string, compare-and- exchange, table-translation, and I/O instructions. 2 • Special accumulator encoding AL AX EAX RAX Accumulator for ADD, XOR, and MOV instructions. • Used with EDX to hold double- precision operands. • CPUID processor-feature information. • Address generation in 16-bit code. • Memory address for XLAT BL BX EBX RBX 2 Base instruction. • CPUID processor-feature information. • Bit index for shift and rotate instructions. • Iteration count for loop and CL CX ECX RCX 2 Count repeated string instructions. • Jump conditional if zero. • CPUID processor-feature information. • Operand for multiply and divide instructions. • Port number for I/O instructions. DL DX EDX RDX 2 I/O Address • Used with EAX to hold double- precision operands. • CPUID processor-feature information. • Memory address of source operand for string instructions. SIL 2 SI ESI RSI 2 Source Index • Memory index for 16-bit addresses. Note: 1. Gray-shaded registers have no implicit uses. 2. Accessible only in 64-bit mode. General-Purpose Programming 31 AMD64 Technology 24592—Rev. 3.14—September 2007 Table 3-1. Implicit Uses of GPRs (continued) Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Memory address of destination Destination operand for string instructions. DIL 2 DI EDI RDI 2 Index • Memory index for 16-bit addresses. • Memory address of stack- BPL 2 BP EBP RBP 2 Base Pointer frame base pointer. -

Assembly Language Tutorial
Assembly Language Tutorial ASSEMBLY LANGUAGE TUTORIAL Simply Easy Learning by tutorialspoint.com tutorialspoint.com i ABOUT THE TUTORIAL Assembly Programming Tutorial Assembly language is a low-level programming language for a computer, or other programmable device specific to a particular computer architecture in contrast to most high- level programming languages, which are generally portable across multiple systems. Assembly language is converted into executable machine code by a utility program referred to as an assembler like NASM, MASM etc. Audience This tutorial has been designed for software programmers with a need to understand the Assembly programming language starting from scratch. This tutorial will give you enough understanding on Assembly programming language from where you can take yourself at higher level of expertise. Prerequisites Before proceeding with this tutorial you should have a basic understanding of Computer Programming terminologies. A basic understanding of any of the programming languages will help you in understanding the Assembly programming concepts and move fast on the learning track. TUTORIALS POINT Simply Easy Learning Copyright & Disclaimer Notice All the content and graphics on this tutorial are the property of tutorialspoint.com. Any content from tutorialspoint.com or this tutorial may not be redistributed or reproduced in any way, shape, or form without the written permission of tutorialspoint.com. Failure to do so is a violation of copyright laws. This tutorial may contain inaccuracies or errors and tutorialspoint provides no guarantee regarding the accuracy of the site or its contents including this tutorial. If you discover that the tutorialspoint.com site or this tutorial content contains some errors, please contact us at [email protected] TUTORIALS POINT Simply Easy Learning Table of Content Assembly Programming Tutorial .............................................