Fiber Distributed Data Interface
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Digital Technical Journal, Number 7, August 1988: CVAX
Digital Technical Tournal Digital Equipment Corporation Managing Editor Richard W Beam Edltor Jane C. Dlak Pcoductloa St& Production Editor - Helen 1 Partenon Designer - Charlotte Bell Typographers -Jonathan M. Bohy Macgaret Burdine lllusultor - Deborah Kc~lcy Advisoiy Board Samuel H. Fuller, Chairman Robert M. Glorioso John W. McCredle Mahendra R. Patel F. Grant Saviers William D. Srrcckr Victor A. Vyssutsky The Digital Technical Journal is published by Digital Equipment Corporatloa, 77 Reed Road, Hudson, Magsachu~etts0 1749. Changes of address should be sent to Digital Equipment Corporation. attention: List Maintenance. I0 Forbes Road, Northboro, MA 01532 Please indude the address label wlth changes marked. Comments on the content of any paper arc welcomed. Write to the editor at Mall Stop HL02.3/K11 at the published~bpaddress. Comments can ahbe sent on the BNET to RDVAX: :BIAKEor on the ARPANET to B~%RDVAX.DE~DE~. Copyright @ 1988 Digital Equipment Corporation. Copying without fee is permitted provided that such copies are made for use in educational lnstltutions by faculty members and are nor distributed for commercial advantage. Abstncting with credit of Digital Equipment Corporation's authorship is permltted. Requests for other copies for a Pee may br made to Digiul Press of Digital Equipment Corporation. A11 rights reserved. The information in this journal is subject to change without notice and should not bc construed as a com- mltment by Digital Equipment Corporation. Digital Equipment Corpmtion assumes no responslbllity for any errors that may appcss in this document ISSN 0898.901X Documentatlcm Number EY-6742H-DP The following are wademarks of Digital Gquipmcnt Corporation: ALL.IN-I. -

VAX 6000 Series Installation Guide
VAX 6000 Series Installation Guide Order Number EK–600EB–IN.002 This guide is intended for use by Digital customer service engineers and self-maintenance customers installing a VAX 6000 series system. digital equipment corporation maynard, massachusetts First Printing, October 1990 Revised, November 1991 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1990, 1991 by Digital Equipment Corporation. All Rights Reserved. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: DEC PDP VAXcluster DEC LANcontroller ULTRIX VAXELN DECnet UNIBUS VMS DECUS VAX XMI DWMVA VAXBI FCC NOTICE: The equipment described in this manual generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference when operated in a commercial environment. Operation of this equipment in a residential area may cause interference, in which case the user at his own expense may be required to take measures to correct the interference. -

VAX 6000 Platform Technical User's Guide
VAX 6000 Platform Technical User’s Guide Order Number: EK–600EA–TM-001 This manual serves as a reference for field-level repair or programming for systems based on the VAX 6000 platform. The manual describes the platform architecture, the XMI system bus, the DWMBB XMI-to-VAXBI adapter, and the power and cooling systems found in the H9657-CA/CB/CU cabinet. Digital Equipment Corporation First Printing, May 1991 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1991 by Digital Equipment Corporation All Rights Reserved. Printed in U.S.A. The postpaid READER’S COMMENTS form on the last page of this document requests the user’s critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: DEMNA PDP VAXcluster DEC ULTRIX VAXELN DEC LANcontroller UNIBUS VMS DECnet VAX XMI DECUS VAXBI dt This document was prepared using VAX DOCUMENT, Version 1.2 Contents PREFACE xiii CHAPTER 1 THE VAX 6000 PLATFORM OVERVIEW 1–1 1.1 SPECIFICATIONS 1–2 1.2 SYSTEM FRONT VIEW 1–4 -

Digital Technical Journal, Number 7, August 1988: CVAX-Based Systems
CVAX-based Systems Digital Technical Journal Digital Equipment Corporation umhcr 7 August I9R8 Managing Editor Richard W Beane Editor jane C. Blake Production Staff Produnion Editor- Helen L. Paucrson Designer- Charlo!!<: Bell Typographers- Jonathan !\·f. Uohy Margart:t Burdine lllustrawr- Dt:borah Keeley Advisory Board Samuel H. Fuller, Chairman Robert M. Glorioso John W McCredie Mahendra R. Patel F. Grant Saviers William D. Strecker Victor A. Vyssotsky The Digital Tecbnical jnumal is published by Digital Equipmt:nt Corporation. 77 Reed Road. Hudson. Massachuscus 01749. Changes of address should be sent to Digital E quipment Corporation. aut:ntion: List Maintenance. I 0 Forbes Road. Northboro. MA 015j2. Please includt: the address label with changes marked. Comments on the content of any paper are wclcomt:d. Write to the editor at Mail Stop 1-lLOl-.�/Kil at the published-by address. Comments can also be sent on the ENET to RDV�'X::OIAKE or on the ARPANET to BLA.K.E'X,RDVAX. DEC�)l)ECWRL. Copyright © 1988 Digital Equ ipment Corporation. Copying without fee is permiued providt:d that such copies are made for use in t:duc:uional institmions by faculty members and arc not distributed for commercial advamage. Abstracting with credit of Digital Equipment Corporation's authorship is pcrmiued. Requests for other copies for a fee may be made 10 Digital Press of Digital Equipmem Corporation. All rights reserved. The information in this journal is subject to change without notice and should not be construed as a com miunem by Digital E quipment Corporation. Digital Equipment Corporation assumt:s no responsibility for any errors that may appear in this document. -

Openvms I/O User's Reference Manual
OpenVMS I/O User’s Reference Manual Order Number: AA–PV6SD–TK April 2001 This manual contains the information necessary to interface directly with the I/O device drivers supplied as part of the Compaq OpenVMS operating system. Several examples of programming techniques are included. This document does not contain information on I/O operations using the OpenVMS Record Management Services. Revision/Update Information: This manual supersedes the OpenVMS I/O User’s Reference Manual, OpenVMS Alpha Version 7.2, OpenVMS VAX Version 7.2 Software Version: OpenVMS Alpha Version 7.3 OpenVMS VAX Version 7.3 Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation Compaq, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS and Tru64 are trademarks of Compaq Information Technologies Group, L.P in the United States and other countries. Microsoft, MS-DOS, Visual C++, Windows, and Windows NT are trademarks of Microsoft Corporation in the United States and other countries. Intel, Intel Inside, and Pentium are trademarks of Intel Corporation in the United States and other countries. Motif, OSF/1, and UNIX are trademarks of The Open Group in the United States and other countries. All other product names mentioned herein may be trademarks of their respective companies. Confidential computer software. Valid license from Compaq required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. -

VAX 6000 Model 500 Mini-Reference
VAX 6000 Model 500 Mini-Reference Order Number EK–650EA–HR–001 This manual supplies easy-to-access key information on VAX 6000 Model 500 systems. digital equipment corporation maynard, massachusetts First Printing, October 1990 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1990 by Digital Equipment Corporation. All Rights Reserved. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: DEMNA PDP VAXcluster DEC ULTRIX VAXELN DEC LANcontroller UNIBUS VMS DECnet VAX XMI DECUS VAXBI FCC NOTICE: The equipment described in this manual generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference when operated in a commercial environment. Operation of this equipment in a residential area may cause interference, in which case the user at his own expense may be required to take measures to correct the interference. Contents Preface xi Chapter 1 Console Operation Chapter 2 Self-Test Chapter 3 Address Space 3.1 How to Find a Register in XMI Address Space . -

A Conceptual Design for the Triumf Kaon Factory Control System
TRIUMF A CONCEPTUAL DESIGN FOR THE TRIUMF KAON FACTORY CONTROL SYSTEM W.K. Dawson, R.W. Dobinson,* D.P. Gurd and Ch. Serre* TRIUMF Technology Division *on leave of absence from CERN CANADA'S NATIONAL MESON FACILITY OPERATED AS A JOINT VENTURE BY: UNIVERSITY OF ALBERTA SIMON FRASER UNIVERSITY UNIVERSITY OF VICTORIA UNIVERSITY OF BRITISH COLUMBIA UNDER A CONTRIBUTION FROM THE NATIONAL RESEARCH COUNCIL OF CANADA TRI-87-1 TRI-87-1 A CONCEPTUAL DESIGN FOR THE TRIUMF KAON FACTORY CONTROL SYSTEM W.K. Dawson, R.W. Dobinson,* D.P. Gurd and Ch. Serre* TRIUMF Technology Division *on leave of absence from CERN Postal address: TRIUMF 4004 Wesbrook Mall Vancouver, B.C. Canada V6T 2A3 December 1987 All trademarks found in this report are acknowledged as such. ii TABLE OF CONTENTS 1.0 Introduction 1-1 1.1 Why Was a Design Study Undertaken? 1-1 1.2 How Was the Work Carried Out? 1-1 1.3 Report Layout 1-2 1.4 Acknowledgements 1-3 2.0 Requirements 2-1 2.1 The Accelerators - 2-1 2.2 Timing and Synchronization 2-1 2.3 Multiple Rings, Physical Size and Complexity 2-4 2.4 High Intensity 2-5 2.5 Safety Systems 2-6 2.6 Users of the Control System 2-7 2.7 General Needs - Motherhood and Apple Pie 2-9 3.0 Review of Current Technologies and Trends in Other Laboratories . 3-1 3.1 The Importance and Role of Protocols and Standards 3-1 3.1.1 Review 3-1 3.1.2 Trends in Other Laboratories 3-2 3.2 Software 3-3 3.2.1 Review 3-3 3.2.2 Trends in Other Laboratories . -

Designer's Notebook
DESIGNER'S NOTEBOOK EK-VBIDS-RM-001 DIGITAL EQUIPMENT CORPORATION CONFIDENTIAL AND PROPRIETARY DIGITAL CONFIDENTIAL & PROPRIETARY ( .... ~•. ... ,,)' VAXBI DESIGNER'S NOTEBOOK EK-VBIDS-RM-001 o Digital Equipment Corporation. Maynard, Massachusetts DIGITAL CONFIDENTIAL & PROPRIETARY First Printing, January 1986 Digital Equipment Corporation makes no representation that the interconnection of its products in the manner described herein will not infringe on existing or future patent rights, nor do the descrip tions contained herein imply the granting of license to make, use, or sell equipment constructed in accordance with this description. The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The manuscript for this book was created using generic coding and, via a translation program, was automatically typeset. Book production was done by Educational Services Development and Pub lishing in Bedford, MA. Copyright © Digital Equipment Corporation 1985, 1986 All Rights Reserved Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: DEC MASSBUS UNIBUS DECmate PDP ULTRIX DECnet P/OS VAX "----- / DECUS Professional VAXBI DECwriter Rainbow VAXELN DIBOL RSTS VMS ~DmDDmD'" RSX VT RT Work Processor DIGITAL CONFIDENTIAL & PROPRIETARY Contents Preface Chapter 1 Introduction to VAXBI Option Design 1-1 by VAXBI Development Group Overview -

VAX 6000 Model 600 System Technical User's Guide
VAX 6000 Model 600 System Technical User’s Guide Order Number: EK–660EA–TM.001 This manual serves as a reference on how to write software to this machine and covers the information needed to do field-level repair or programming customized to the CPU. It includes information on interrupts, error handling, and detailed theory of operation. Digital Equipment Corporation First Printing, January 1992 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1992 by Digital Equipment Corporation All Rights Reserved. Printed in U.S.A. The postpaid READER’S COMMENTS form on the last page of this document requests the user’s critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: DEC PDP VAXcluster DEC LANcontroller ULTRIX VAXELN DECnet UNIBUS VMS DECUS VAX XMI DWMVA VAXBI dt This document was prepared using VAX DOCUMENT, Version 1.2 Contents PREFACE xv CHAPTER 1 THE VAX 6000 MODEL 600 SYSTEM 1–1 1.1 SYSTEM ARCHITECTURE 1–2 1.2 SAMPLE SYSTEM 1–4 1.3 SYSTEM FRONT -
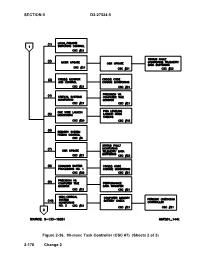
SECTION II D2-27524-5 2-178 Change 2 Figure 2-36. 90-Msec Task Controller (CSC #7) (Sheets 2 of 3)
SECTION II D2-27524-5 Figure 2-36. 90-msec Task Controller (CSC #7) (Sheets 2 of 3) 2-178 Change 2 D2-27524-5 SECTION II Figure 2-36. 90-msec Task Controller (CSC #7) (Sheets 3 of 3) Change 2 2-179 SECTION II D2-27524-5 Figure 2-37. Aperiodic Missile Test and GST Controller (Sheets 1 of 2) 2-180 Change 2 D2-27524-5 SECTION II Figure 2-37. Aperiodic Missile Test and GST Controller (Sheets 2 of 2) Change 2 2-181 SECTION II D2-27524-5 Figure 2-38. Aperiodic Terminal Countdown Controller (CSC #7) 2-182 Change 2 D2-27524-5 SECTION II Figure 2-39. 90-msec IMU Task Controller (CSC #7) Change 2 2-183 SECTION II D2-27524-5 Figure 2-40. Background Task Controller 2-184 Change 2 D2-27524-5 SECTION II Figure 2-41. Strategic Alert Biasing Sequence Change 2 2-185 SECTION II D2-27524-5 Figure 2-42. Strategic Alert PIGA Leveling Sequence (Sheet 1 of 2) 2-186 Change 2 D2-27524-5 SECTION II Figure 2-42. Strategic Alert PIGA Leveling Sequence (Sheet 2 of 2) Change 2 2-187 SECTION II D2-27524-5 Figure 2-43. Terminal Countdown (Sheet 1 of 2) 2-188 Change 2 D2-27524-5 SECTION II Figure 2-43. Terminal Countdown (Sheet 2 of 2) Change 2 2-189 D2-27524-5 SECTION II Figure 2-44. Missile Test Sequence – Sequential Timing Diagram (Sheet 2 of 2) Change 2 2-191/(2-192 blank) D2-27524-5 SECTION III SECTION III - MGS OPERATION TABLE OF CONTENTS Paragraph Page 3-1. -

VAX 6000 Platform Service Manual
VAX 6000 Platform Service Manual Order Number EK–600EA–MG–001 This manual is intended for Digital customer service engineers. It covers the removal and replacement of field-replaceable units (FRUs) in the H9657-CA/CB/ CU cabinet. digital equipment corporation maynard, massachusetts First Printing, December 1990 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1990 by Digital Equipment Corporation. All Rights Reserved. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: DEMNA PDP VAXcluster DEC ULTRIX VAXELN DEC LANcontroller UNIBUS VMS DECnet VAX XMI DECUS VAXBI dt FCC NOTICE: The equipment described in this manual generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference when operated in a commercial environment. Operation of this equipment in a residential area may cause interference, in which case the user at his own expense may be required to take measures to correct the interference. -

Student Guide
EY -5554E-SG-0002 This course is designed for internal use only NOT FOR SALE OR RENT VAXBI Adapters Student Guide ~DmDDmDW Educational Services Second Edition, February 1987 Copyright©Digital Equipment Corporation 1987 All Rights Reserved The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: rM DECwriter RSX mamaama DIBOL Scholar DEC MASSBUS ULTRIX DECmate PDP UNIBUS DECset p/OS VAX DECsystem-l0 Professional VMS DECSYSTEM-20 Rainbow VT DEC US RSTS Work Processor CONTENTS SG STUDENT GUIDE INTRODUCTION THE VAXBI ADAPTERS INFORMATION DATABASE • • • • • • SG-3 Practice and Tests • • • • • SG-4 The Menu • • • • • • • • • SG-4 TYPES OF ADAPTERS •••• • • • SG-7 PIO Adapters • • . • • • • . • . SG-7 Window Adapters •• • SG-9 Port Adapters ••• • • • • • • • • • SG-IO VAXBI ADDRESS SPACE ••• • • • • • • • • • • SG-ll THINGS TO REMEMBER • • • • • • SG-13 UNIT 1 DWBUA ADAPTER LESSON 1 - INTRODUCTION. • • •• 1-3 Functional Description · . .. ... 1-4 Block Diagram. • • . 1-4 Transactions • • • · . 1-7 LESSON 2 - DWBUA REGISTERS · . .. 1-9 LESSON 3 - INSTALLATION ••• · . 1-11 Self-Test ••••••• • • • • • • • 1-16 Macrodiagnostic Program. • • • • . • • • • • • • 1-1 7 LESSON 4 - TROUBLESHOOTING • • • • • • • • 1-19 LESSON 5 - RELATED DOCUMENTATION • · . 1-28 UNIT 2 DMB32 ADAPTER LESSON 1 - INTRODUCTION. 2-3 Functional Description • • • • • • • • • • •• 2-5 Data Transfer •• . .. 2-8 Interrupts • • • • • • • • • • • • 2-9 Physical Description • • • • • • 2-10 The DMB32 Option • • • • • • • • • • • • • 2-10 The H3033 Distribution Panel • • • 2-10 LESSON 2 - DMB32 REGISTERS • • • • 2-12 iii LESSON 3 - INSTALLATION ••• • • 2-13 Installation Task List • • • • • • 2-13 DMB32 Installation Kits.