COMPUTER ARCHITECTURE and SECURITY Information Security Series
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Buses EE2222 Computer Interfacing and Microprocessors
System Buses EE2222 Computer Interfacing and Microprocessors Partially based on Computer Organization and Architecture by William Stallings Computer Electronics by Thomas Blum 2020 EE2222 1 Connecting • All the units must be connected • Different type of connection for different type of unit • CPU • Memory • Input/Output 2020 EE2222 2 CPU Connection • Reads instruction and data • Writes out data (after processing) • Sends control signals to other units • Receives (& acts on) interrupts 2020 EE2222 3 Memory Connection • Receives and sends data • Receives addresses (of locations) • Receives control signals • Read • Write • Timing 2020 EE2222 4 Input/Output Connection(1) • Similar to memory from computer’s viewpoint • Output • Receive data from computer • Send data to peripheral • Input • Receive data from peripheral • Send data to computer 2020 EE2222 5 Input/Output Connection(2) • Receive control signals from computer • Send control signals to peripherals • e.g. spin disk • Receive addresses from computer • e.g. port number to identify peripheral • Send interrupt signals (control) 2020 EE2222 6 What is a Bus? • A communication pathway connecting two or more devices • Usually broadcast (all components see signal) • Often grouped • A number of channels in one bus • e.g. 32 bit data bus is 32 separate single bit channels • Power lines may not be shown 2020 EE2222 7 Bus Interconnection Scheme 2020 EE2222 8 Data bus • Carries data • Remember that there is no difference between “data” and “instruction” at this level • Width is a key determinant of performance • 8, 16, 32, 64 bit 2020 EE2222 9 Address bus • Identify the source or destination of data • e.g. CPU needs to read an instruction (data) from a given location in memory • Bus width determines maximum memory capacity of system • e.g. -

What Is the Difference Between San and Nas and How Can I Use Them in My Qlikview Environment?
WHAT IS THE DIFFERENCE BETWEEN SAN AND NAS AND HOW CAN I USE THEM IN MY QLIKVIEW ENVIRONMENT? QlikView Technical Brief February 2012 qlikview.com This document will highlight some of the conceptual differences between the terms SAN and NAS and describe how they fit into a QlikView Server environment by suggesting some recommended implementations. It will also describe the definition of DAS (Direct-Attached Storage) and how it applies in SAN configurations. Using SAN and NAS in the QlikView Environment | Page 2 Table of Contents Definitions 4 SAN - Storage Area Network 4 Host adapters 4 Typical architecture 5 NAS - Network Attached Storage 7 Typical architecture 7 DAS - Direct-Attached Storage 8 Using SAN/NAS and QlikView Server 8 QlikView Server and Distribution Service cluster inter-communication 8 QlikView Server file storage conformity 9 QlikView file types explained 9 A note on the usage of .shared files 10 Considerations 10 Conclusions 11 Some suggestions 12 QlikView Server Configurations 12 QlikView Server cluster utilizing a virtual Windows based NAS using a SAN 12 QlikView Server cluster utilizing a physical NAS using a SAN 13 Single QlikView Server using a SAN as local storage 14 QlikView Server using a pure Windows based NAS as local storage 14 Using SAN and NAS in the QlikView Environment | Page 3 Definitions It is important to differentiate between the two terms SAN and NAS. Also, the term DAS will be involved to nuance the usage of a SAN. SAN - STORAGE AREA NETWORK A typical definition of a SAN could be; “SANs primarily are used to make storage devices (such as disk arrays, tape libraries, and optical jukeboxes) accessible to servers so that the devices appear as locally attached to the operating system.” (Wikipedia.org) SANs are often used in larger virtualization scenarios or where larger areas of high-speed access storage space is required. -

Getting Started with Your VXI-1394 Interface for Windows NT/98 And
VXI Getting Started with Your VXI-1394 Interface for Windows NT/98 VXI-1394 Interface for Windows NT/98 November 1999 Edition Part Number 322109D-01 Worldwide Technical Support and Product Information www.ni.com National Instruments Corporate Headquarters 11500 North Mopac Expressway Austin, Texas 78759-3504 USA Tel: 512 794 0100 Worldwide Offices Australia 03 9879 5166, Austria 0662 45 79 90 0, Belgium 02 757 00 20, Brazil 011 284 5011, Canada (Calgary) 403 274 9391, Canada (Ontario) 905 785 0085, Canada (Québec) 514 694 8521, China 0755 3904939, Denmark 45 76 26 00, Finland 09 725 725 11, France 01 48 14 24 24, Germany 089 741 31 30, Greece 30 1 42 96 427, Hong Kong 2645 3186, India 91805275406, Israel 03 6120092, Italy 02 413091, Japan 03 5472 2970, Korea 02 596 7456, Mexico (D.F.) 5 280 7625, Mexico (Monterrey) 8 357 7695, Netherlands 0348 433466, Norway 32 27 73 00, Poland 48 22 528 94 06, Portugal 351 1 726 9011, Singapore 2265886, Spain 91 640 0085, Sweden 08 587 895 00, Switzerland 056 200 51 51, Taiwan 02 2377 1200, United Kingdom 01635 523545 For further support information, see the Technical Support Resources appendix. To comment on the documentation, send e-mail to [email protected] © Copyright 1998, 1999 National Instruments Corporation. All rights reserved. Important Information Warranty The National Instruments VXI-1394 board is warranted against defects in materials and workmanship for a period of one year from the date of shipment, as evidenced by receipts or other documentation. National Instruments will, at its option, repair or replace equipment that proves to be defective during the warranty period. -

ECESATUSB1 This Expresscard Power Esata Port Controller Card
1 Port ExpressCard Power eSATA Controller Adapter Card StarTech ID: ECESATUSB1 This ExpressCard Power eSATA port controller card can be installed in an available ExpressCard 34/54 mm slot to provide a powered eSATA connection, and also alternatively provide either external SATA (data only) or USB 2.0 connectivity from one uniquely designed port if using with standard eSATA or USB devices. An ideal solution for using an eSATA SSD Flash drive on your laptop, the power eSATA card delivers both a high speed eSATA connection and power from the combined USB port. A versatile connectivity solution, the card features built-in port multiplier support, allowing multi-drive eSATA storage enclosures to be connected to the host computer using a single eSATA cable. Taking advantage of the transfer speed of eSATA connection and the 5V power output of the USB 2.0 port, the ExpressCard Power eSATA adapter is the perfect answer for connecting compatible mobile drive enclosures, similar to the built-in power eSATA port provided by the following laptop computers: Toshiba: Satellite E105, A350, Satellite Pro P300; Qosmio G50, X305, Portege A600, M750, R500, R600; and Tecra M10, R10, A10. Dell: Studio 15, 17; Latitude E6400, E6500; Precision M2400, M4400, M6400, M6400 Covet. Applications Connects to eSATA SSD Flash drives, such as OCZ Throttle, Kangaru e-Flash drives and Ridata Racer series flash drives Provides connectivity between Notebooks and PCs with ExpressCard slots to external drive enclosures with Power eSATA (eSATA+USB) port, or with regular eSATA -

Control Bus System and Application of Building Electric Zhai Long1*, Tan Bin2, Ren Min3 1.Xi’An Changqing Technology Engineering Co., Ltd., Xi'an 710018 ,China 2
ORIGINAL ARTICLE Control Bus System And Application of Building Electric Zhai Long1*, Tan Bin2, Ren Min3 1.Xi’an Changqing Technology Engineering Co., Ltd., Xi'an 710018 ,China 2. Xi'an Changqing Technology Engineering Co., Ltd., Xi'an 710018,China 3.The Fifth Oil Production Plant of Changqing Oilfield Company, Xi'an 710018,China ABSTRACT As the most important part of Building construction, the KEYWORDS electric part 's intelligent control is particularly important. the most Building electric important sign of The intelligent intelligent control is the application of Control Bus System control bus system, only select the appropriate control bus system, and CAN protocol achieve intelligent applications in buildings, elevators, fire, visualization, etc., can meet the household needs. Firstly, the design principle of the electrical control system will be described, and then the CAN - based bus system control principle and application are discussed, only used for reference. 1.Design Principles of Electric Control System Introduction As a primary prerequisite for intelligent building, For construction, the electric bus control technology is a Design of electrical control system should meet the relatively new technology. under the trend of the following principles: development of intelligent building in the future, application (1) It is needed to ensure meeting the needs under of control bus system has become the most important normal production environment . the mainstay of component of intelligent building . In the construction of the electrical system is designed to meet the production machinery and production process requirements. (2) building, the control bus system can not only make The overall design concept should be clear. -

Computer Organization and Architecture Designing for Performance Ninth Edition
COMPUTER ORGANIZATION AND ARCHITECTURE DESIGNING FOR PERFORMANCE NINTH EDITION William Stallings Boston Columbus Indianapolis New York San Francisco Upper Saddle River Amsterdam Cape Town Dubai London Madrid Milan Munich Paris Montréal Toronto Delhi Mexico City São Paulo Sydney Hong Kong Seoul Singapore Taipei Tokyo Editorial Director: Marcia Horton Designer: Bruce Kenselaar Executive Editor: Tracy Dunkelberger Manager, Visual Research: Karen Sanatar Associate Editor: Carole Snyder Manager, Rights and Permissions: Mike Joyce Director of Marketing: Patrice Jones Text Permission Coordinator: Jen Roach Marketing Manager: Yez Alayan Cover Art: Charles Bowman/Robert Harding Marketing Coordinator: Kathryn Ferranti Lead Media Project Manager: Daniel Sandin Marketing Assistant: Emma Snider Full-Service Project Management: Shiny Rajesh/ Director of Production: Vince O’Brien Integra Software Services Pvt. Ltd. Managing Editor: Jeff Holcomb Composition: Integra Software Services Pvt. Ltd. Production Project Manager: Kayla Smith-Tarbox Printer/Binder: Edward Brothers Production Editor: Pat Brown Cover Printer: Lehigh-Phoenix Color/Hagerstown Manufacturing Buyer: Pat Brown Text Font: Times Ten-Roman Creative Director: Jayne Conte Credits: Figure 2.14: reprinted with permission from The Computer Language Company, Inc. Figure 17.10: Buyya, Rajkumar, High-Performance Cluster Computing: Architectures and Systems, Vol I, 1st edition, ©1999. Reprinted and Electronically reproduced by permission of Pearson Education, Inc. Upper Saddle River, New Jersey, Figure 17.11: Reprinted with permission from Ethernet Alliance. Credits and acknowledgments borrowed from other sources and reproduced, with permission, in this textbook appear on the appropriate page within text. Copyright © 2013, 2010, 2006 by Pearson Education, Inc., publishing as Prentice Hall. All rights reserved. Manufactured in the United States of America. -

Design and Implementation Considerations for Storage Area Networks
Designing and Implementing a SAN 1 Running head: DESIGNING AND IMPLEMENTING A SAN Considerations for the Design and Implementation of a Storage Area Network (SAN) Al Spraker 15 July 2006 Designing and Implementing a SAN 2 Abstract With the ever-increasing need for businesses and organizations to maintain and manage large amounts of data, storage issues have become a concern and an investment priority. Organizations and business must have a good understanding of the features and characteristics of network storage in order to design and implement a network storage system that addresses their present and future needs. This paper will define and compare the storage area networks (SAN) with network-attached storage (NAS) as well as a historical perspective of directly-attached storage (DAS). Some of the benefits associated with establishing a network storage system will also be identified. This paper will identify some of the general characteristics of SAN architecture and protocols, such as Fibre Channel and iSCSI. Another area addressed will be management software issues and its critical role as part of successful SAN deployment. Not only must data be reliable and available at all times, data must also be kept confidential and protected. While the data is being transmitted over the network, security is also a concern that must be addressed. Designing and Implementing a SAN 3 Considerations for the Design and Implementation of a Storage Area Network (SAN) Today’s enterprises are using more complex, sophisticated, and resource-intensive software that generates massive amounts of data. The demand for businesses to maintain and manage large amounts of data has elevated storage issues to a level of significant priority. -

MAKING CODE ZERO Part 2
October 2018 Issue 23 PLUS MAKING CODE ZERO part 2 Includes material PLAY BLACKPOOL not in the video Report from the show! event... CONTENTS 32. RECREATED SPECTRUM Is it any good? 24. MIND YOUR LANGUAGE 18. Play Blackpool 2018 Micro-Prolog. The recent retro event. FEATURES GAME REVIEWS 4 News from 1987 DNA Warrior 6 Find out what was happening back in 1987. Bobby Carrot 7 14 Making Code Zero Devils of the Deep 8 Full development diary part 2. Spawn of Evil 9 18 Play Blackpool Report from the recent show. Hibernated 1 10 24 Mind Your Language Time Scanner 12 More programming languages. Maziacs 20 32 Recreated ZX Spectrum Bluetooth keyboard tested. Gift of the Gods 22 36 Grumpy Ogre Ah Diddums 30 Retro adventuring. Snake Escape 31 38 My Life In Adventures A personal story. Bionic Ninja 32 42 16/48 Magazine And more... Series looking at this tape based mag. And more…. Page 2 www.thespectrumshow.co.uk EDITORIAL Welcome to issue 23 and thank you for taking the time to download and read it. Those following my exploits with blown up Spectrums will be pleased to I’ll publish the ones I can, and provide hear they are now back with me answers where fit. Let’s try to get thanks to the great service from Mu- enough just for one issue at least, that tant Caterpillar Games. (see P29) means about five. There is your chal- Those who saw the review of the TZX All machines are now back in their lenge. Duino in episode 76, and my subse- cases and working fine ready for some quent tweet will know I found that this The old school magazines had many filming for the next few episodes. -
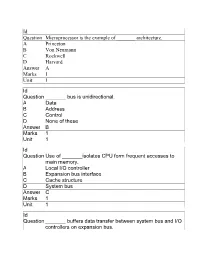
Id Question Microprocessor Is the Example of ___Architecture. A
Id Question Microprocessor is the example of _______ architecture. A Princeton B Von Neumann C Rockwell D Harvard Answer A Marks 1 Unit 1 Id Question _______ bus is unidirectional. A Data B Address C Control D None of these Answer B Marks 1 Unit 1 Id Question Use of _______isolates CPU form frequent accesses to main memory. A Local I/O controller B Expansion bus interface C Cache structure D System bus Answer C Marks 1 Unit 1 Id Question _______ buffers data transfer between system bus and I/O controllers on expansion bus. A Local I/O controller B Expansion bus interface C Cache structure D None of these Answer B Marks 1 Unit 1 Id Question ______ Timing involves a clock line. A Synchronous B Asynchronous C Asymmetric D None of these Answer A Marks 1 Unit 1 Id Question -----timing takes advantage of mixture of slow and fast devices, sharing the same bus A Synchronous B asynchronous C Asymmetric D None of these Answer B Marks 1 Unit 1 Id st Question In 1 generation _____language was used to prepare programs. A Machine B Assembly C High level programming D Pseudo code Answer B Marks 1 Unit 1 Id Question The transistor was invented at ________ laboratories. A AT &T B AT &Y C AM &T D AT &M Answer A Marks 1 Unit 1 Id Question ______is used to control various modules in the system A Control Bus B Data Bus C Address Bus D All of these Answer A Marks 1 Unit 1 Id Question The disadvantage of single bus structure over multi bus structure is _____ A Propagation delay B Bottle neck because of bus capacity C Both A and B D Neither A nor B Answer C Marks 1 Unit 1 Id Question _____ provide path for moving data among system modules A Control Bus B Data Bus C Address Bus D All of these Answer B Marks 1 Unit 1 Id Question Microcontroller is the example of _____ architecture. -

The ZX Spectrum on Your PC Emulators, Utilities and More
The ZX Spectrum on your PC Emulators, utilities and more C Woodcock www.cwoodcock.co.uk/zxf ZXF Magazine www.cwoodcock.co.uk/zxf Copyright © 2004 Colin Woodcock First published 2004 by CafePress.com Acknowledgements My thanks to Paul Dunn, Nick Humphries and Jonathan Needle for the valuable suggestions that came out of their proof-reading of the first draft of this book. Thanks also to Matthew Westcott for helping me to understand TR-DOS a little better. ZXF magazine delights in reporting on the achievements of the members of the Spectrum community and is indebited to them all for their efforts. In particular, ZXF could not have achieved its current distribution without the hosting offered by Martijn van der Heide at www.worldofspectrum.org, whose own contribution to the Spectrum scene goes well beyond the easily measurable. Contents Preface vii 1 Emulator basics 1 2 Finding files 15 3 Peripherals 19 4 Emulator extras 27 5 Utilities 32 6 Russian clones; TR-DOS 44 7 Other emulators 49 Appendix I: Key websites 58 Appendix II: Key documents 61 Appendix III: comp.sys.sinclair 63 Index 67 for Jack Preface So you've finally realised. You think that new technology is great - of course you do - but ever since you packed away that old Spectrum in a box and taped up the lid something has most definitely been missing. At last you understand you were turning your back on more than just an obsolete computer. The good news is that you don't have to fish the box out from under the bed just yet (or lament its sale on ebay or at the local car boot): the Spectrum is one of the most emulated computers (if not the most emulated computer) on the planet and the quality of its emulation is just superb. -

Compaq Alphaserver ES45 Client/Server System Using Oracle9i, R2 Enterprise Edition for Tru64 UNIX ® and Compaq Tru64 UNIX 5.1A®
TPC Benchmark C® Full Disclosure Report Compaq AlphaServer ES45 Client/Server System Using Oracle9i, R2 Enterprise Edition for Tru64 UNIX ® and Compaq Tru64 UNIX 5.1A® Company System Name Database Software Operating System Name Software Compaq CompaqAlphaServer ES45 Oracle9i, R2 Enterprise Compaq Computer 4 CPU Client/Server System Edition Tru64 UNIX V5.1A Corporation for Tru64 UNIX Availability Date: May 9, 2002 Total System Cost TPC-C Throughput Price Performance Sustained maximum throughput - Hardware of systemrunning TPC Total systemcost/ - Software Benchmark C expressed in TPC-C® throughput 3-Years Maintenance transactions per minute $763,829 50,117 $15.24 I First Printing - January 2002 Compaq Computer Corporation believes that the information in this document is accurate as of its publication date; such information is subject to change without notice. Compaq Computer Corporation is not responsible for any inadvertent errors. Compaq conducts its business in a manner that conserves the environment and protects the safety and health of its employees, customers, and the community. The performance information in this document is for guidance only. System performance is highly dependent on many factors, including systemhardware, systemand user software, and user application characteristics. Customerapplications must be carefully evaluated before estimating performance. Compaq Computer Corporation does not warrant or represent that a user can or will achieve similar performance expressed in transactions per minute (tpmC) or normalized price/performance ($/tpmC). No warranty on system performance or price/performance is expressed or implied in this document. Copyright © 2002 Compaq Computer Corporation All Rights Reserved. Printed in U.S.A. Permission is hereby granted to reproduce this document in whole or in part provided the copyright notice printed above is set forth in full text on the title page of each itemreproduced. -

Linux Journal | System Administration Special Issue | 2009
Cfengine VNC Billix Zenoss Thin Clients MySQL Heartbeat ™ SPECIAL SYSTEM ADMINISTRATION ISSUE Since 1994: The Original Magazine of the Linux Community 2009 | Supplement Issue | www.linuxjournal.com MAY THE SOURCE BE WITH YOU Billix: the Sysadmin Toolkit for Your Pocket Authentication with Fedora Directory Server Remote Desktop Administration with OpenSSH or VNC Manage Configuration Files with Cfengine Setting Up a PXE Boot Server Network Monitoring with Zenoss SPECIAL SYSTEM CONTENTS ADMINISTRATION ISSUE 5 SPECIAL_ISSUE.TAR.GZ 26 PXE MAGIC: FLEXIBLE System Administration: Instant NETWORK BOOTING WITH Gratification Edition MENUS Shawn Powers What if you never had to carry around an install or rescue CD 6 CFENGINE FOR again? Set up a PXE boot server ENTERPRISE with menus and put them all on CONFIGURATION the network. MANAGEMENT Kyle Rankin How to use cfengine to manage configuration files across large 30 CREATING VPNS WITH 17 ZENOSS numbers of machines. IPSEC AND SSL/TLS Scott Lackey The two most common and current techniques for creating VPNs. 10 SECURED REMOTE Rami Rosen Linux Journal DESKTOP/APPLICATION SESSIONS 34 MYSQL 5 STORED 2009 Lineup Different ways to control a Linux PROCEDURES: RELIC OR system over a network. REVOLUTION? JANUARY Mick Bauer Do MySQL 5 Stored Procedures Security produce tiers of joy or sorrow? FEBRUARY Guy Harrison Web Development 38 GETTING STARTED WITH MARCH Desktop HEARTBEAT Availability in a heartbeat. APRIL Daniel Bartholomew System Administration 14 BILLIX: A SYSADMIN’S MAY SWISS ARMY KNIFE 42 FEDORA DIRECTORY Cool Projects SERVER: THE EVOLUTION Build a toolbox in your pocket by JUNE installing Billix on that spare USB key.