Certification of First-Order Proofs in Classical and Intuitionistic Logics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paradoxes Situations That Seems to Defy Intuition
Paradoxes Situations that seems to defy intuition PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Tue, 08 Jul 2014 07:26:17 UTC Contents Articles Introduction 1 Paradox 1 List of paradoxes 4 Paradoxical laughter 16 Decision theory 17 Abilene paradox 17 Chainstore paradox 19 Exchange paradox 22 Kavka's toxin puzzle 34 Necktie paradox 36 Economy 38 Allais paradox 38 Arrow's impossibility theorem 41 Bertrand paradox 52 Demographic-economic paradox 53 Dollar auction 56 Downs–Thomson paradox 57 Easterlin paradox 58 Ellsberg paradox 59 Green paradox 62 Icarus paradox 65 Jevons paradox 65 Leontief paradox 70 Lucas paradox 71 Metzler paradox 72 Paradox of thrift 73 Paradox of value 77 Productivity paradox 80 St. Petersburg paradox 85 Logic 92 All horses are the same color 92 Barbershop paradox 93 Carroll's paradox 96 Crocodile Dilemma 97 Drinker paradox 98 Infinite regress 101 Lottery paradox 102 Paradoxes of material implication 104 Raven paradox 107 Unexpected hanging paradox 119 What the Tortoise Said to Achilles 123 Mathematics 127 Accuracy paradox 127 Apportionment paradox 129 Banach–Tarski paradox 131 Berkson's paradox 139 Bertrand's box paradox 141 Bertrand paradox 146 Birthday problem 149 Borel–Kolmogorov paradox 163 Boy or Girl paradox 166 Burali-Forti paradox 172 Cantor's paradox 173 Coastline paradox 174 Cramer's paradox 178 Elevator paradox 179 False positive paradox 181 Gabriel's Horn 184 Galileo's paradox 187 Gambler's fallacy 188 Gödel's incompleteness theorems -

Combinatorial Flows and Proof Compression Lutz Straßburger
Combinatorial Flows and Proof Compression Lutz Straßburger To cite this version: Lutz Straßburger. Combinatorial Flows and Proof Compression. [Research Report] RR-9048, Inria Saclay. 2017. hal-01498468 HAL Id: hal-01498468 https://hal.inria.fr/hal-01498468 Submitted on 30 Mar 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Combinatorial Flows and Proof Compression Lutz Straßburger RESEARCH REPORT N° 9048 March 2017 Project-Team Parsifal ISSN 0249-6399 ISRN INRIA/RR--9048--FR+ENG Combinatorial Flows and Proof Compression Lutz Straßburger Project-Team Parsifal Research Report n° 9048 — March 2017 — 16 pages Abstract: This paper introduces the notion of combinatorial flows as a generalization of combinatorial proofs that also includes cut and substitution as methods of proof compression. We show a normalization procedure for combinatorial flows, and how syntactic proofs in sequent calculus, deep inference, and Frege systems are translated into combinatorial flows and vice versa. Key-words: Combinatorial flows, deep inference, proof compression, cut elimination, substitution elimination RESEARCH CENTRE SACLAY – ÎLE-DE-FRANCE 1 rue Honoré d’Estienne d’Orves Bâtiment Alan Turing Campus de l’École Polytechnique 91120 Palaiseau Fleuves combinatoires et compression des preuves Resum´ e´ : Cet article introduit la notion de fleuves combinatoires comme gen´ eralisation´ des preuves combinatoires qui comprend egalement´ la coupure et la substitution comme methodes´ de compression des preuves. -

List of Paradoxes 1 List of Paradoxes
List of paradoxes 1 List of paradoxes This is a list of paradoxes, grouped thematically. The grouping is approximate: Paradoxes may fit into more than one category. Because of varying definitions of the term paradox, some of the following are not considered to be paradoxes by everyone. This list collects only those instances that have been termed paradox by at least one source and which have their own article. Although considered paradoxes, some of these are based on fallacious reasoning, or incomplete/faulty analysis. Logic • Barbershop paradox: The supposition that if one of two simultaneous assumptions leads to a contradiction, the other assumption is also disproved leads to paradoxical consequences. • What the Tortoise Said to Achilles "Whatever Logic is good enough to tell me is worth writing down...," also known as Carroll's paradox, not to be confused with the physical paradox of the same name. • Crocodile Dilemma: If a crocodile steals a child and promises its return if the father can correctly guess what the crocodile will do, how should the crocodile respond in the case that the father guesses that the child will not be returned? • Catch-22 (logic): In need of something which can only be had by not being in need of it. • Drinker paradox: In any pub there is a customer such that, if he or she drinks, everybody in the pub drinks. • Paradox of entailment: Inconsistent premises always make an argument valid. • Horse paradox: All horses are the same color. • Lottery paradox: There is one winning ticket in a large lottery. It is reasonable to believe of a particular lottery ticket that it is not the winning ticket, since the probability that it is the winner is so very small, but it is not reasonable to believe that no lottery ticket will win. -
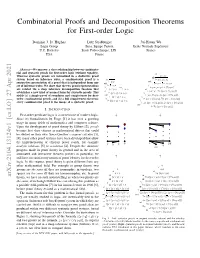
Combinatorial Proofs and Decomposition Theorems for First
Combinatorial Proofs and Decomposition Theorems for First-order Logic Dominic J. D. Hughes Lutz Straßburger Jui-Hsuan Wu Logic Group Inria, Equipe Partout Ecole Normale Sup´erieure U.C. Berkeley Ecole Polytechnique, LIX France USA France Abstract—We uncover a close relationship between combinato- rial and syntactic proofs for first-order logic (without equality). ax ⊢ pz, pz Whereas syntactic proofs are formalized in a deductive proof wk system based on inference rules, a combinatorial proof is a ax ⊢ pw, pz, pz ⊢ p,p wk syntax-free presentation of a proof that is independent from any wk ⊢ pw, pz, pz, ∀y.py set of inference rules. We show that the two proof representations ⊢ p,q,p ∨ ∨ ax ⊢ pw, pz, pz ∨ (∀y.py) are related via a deep inference decomposition theorem that ⊢ p ∨ q,p ⊢ p,p ∃ ∧ ⊢ pw, pz, ∃x.(px ∨ (∀y.py)) establishes a new kind of normal form for syntactic proofs. This ⊢ (p ∨ q) ∧ p,p,p ∀ yields (a) a simple proof of soundness and completeness for first- ctr ⊢ pw, ∀y.py, ∃x.(px ∨ (∀y.py)) ⊢ (p ∨ q) ∧ p,p ∨ order combinatorial proofs, and (b) a full completeness theorem: ∨ ⊢ pw ∨ (∀y.py), ∃x.(px ∨ (∀y.py)) ⊢ ((p ∨ q) ∧ p) ∨ p ∃ every combinatorial proof is the image of a syntactic proof. ⊢ ∃x.(px ∨ (∀y.py)), ∃x.(px ∨ (∀y.py)) ctr ⊢ ∃x.(px ∨ (∀y.py)) I. INTRODUCTION First-order predicate logic is a cornerstone of modern logic. ↓ ↓ Since its formalisation by Frege [1] it has seen a growing usage in many fields of mathematics and computer science. Upon the development of proof theory by Hilbert [2], proofs became first-class citizens as mathematical objects that could be studied on their own. -

Constructive Completeness Proofs and Delimited Control Danko Ilik
Constructive Completeness Proofs and Delimited Control Danko Ilik To cite this version: Danko Ilik. Constructive Completeness Proofs and Delimited Control. Software Engineering [cs.SE]. Ecole Polytechnique X, 2010. English. tel-00529021 HAL Id: tel-00529021 https://pastel.archives-ouvertes.fr/tel-00529021 Submitted on 24 Oct 2010 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Thèse présentée pour obtenir le grade de Docteur de l’Ecole Polytechnique Spécialité : Informatique par Danko ILIK´ Titre de la thèse : Preuves constructives de complétude et contrôle délimité Soutenue le 22 octobre 2010 devant le jury composé de : M. Hugo HERBELIN Directeur de thèse M. Ulrich BERGER Rapporteur M. Thierry COQUAND Rapporteur M. Olivier DANVY Rapporteur M. Gilles DOWEK Examinateur M. Paul-André MELLIÈS Examinateur M. Alexandre MIQUEL Examinateur M. Wim VELDMAN Examinateur Constructive Completeness Proofs and Delimited Control Danko ILIK´ ABSTRACT. Motivated by facilitating reasoning with logical meta-theory in- side the Coq proof assistant, we investigate the constructive versions of some completeness theorems. We start by analysing the proofs of Krivine and Berardi-Valentini, that classical logic is constructively complete with respect to (relaxed) Boolean models, and the algorithm behind the proof. -

CLMPS 2011 Volume of Abstracts
CLMPS 2011 Volume of Abstracts Division of Logic, Methodology and Philosophy of Science of the International Union of History and Philosophy of Science Congress Secretariat (Eds.) Volume of Abstracts CLMPS 2011 Special Topic Logic and Science Facing the New Technologies 14th International Congress of Logic, Methodology and Philosophy of Science Nancy, July 19–26, 2011 (France) Contents Editorial Notev Official Program2 I – Plenary Lectures3 II – Special Sessions7 Special Session 1.............................9 Special Session 2............................. 11 Special Session 3............................. 13 III – IUHPS – Joint Commission Symposium 15 IV – Ordinary Sessions 25 A. Logic...................................... 27 A1. Mathematical Logic........................ 29 A1. Invited Lectures..................... 29 A1. Contributed Papers.................. 34 A2. Philosophical Logic........................ 39 A2. Invited Lectures..................... 39 A2. Contributed Papers.................. 42 A2. Contributed Symposia................. 66 A3. Logic and Computation...................... 81 A3. Invited Lectures..................... 81 A3. Contributed Papers.................. 84 A3. Contributed Symposia................. 87 B. General Philosophy of Science....................... 91 B1. Methodology and Scientific Reasoning............. 93 B1. Invited Lectures..................... 93 B1. Contributed Papers................... 98 B1. Contributed Symposia................. 136 B2. Ethical Issues in the Philosophy of Science.......... 144 B2. -

Algorithmic Structuring and Compression of Proofs (ASCOP)
Project Presentation: Algorithmic Structuring and Compression of Proofs (ASCOP) Stefan Hetzl Institute of Discrete Mathematics and Geometry Vienna University of Technology Wiedner Hauptstraße 8-10, A-1040 Vienna, Austria [email protected] Abstract. Computer-generated proofs are typically analytic, i.e. they essentially consist only of formulas which are present in the theorem that is shown. In contrast, mathematical proofs written by humans almost never are: they are highly structured due to the use of lemmas. The ASCOP-project aims at developing algorithms and software which structure and abbreviate analytic proofs by computing useful lemmas. These algorithms will be based on recent groundbreaking results estab- lishing a new connection between proof theory and formal language the- ory. This connection allows the application of efficient algorithms based on formal grammars to structure and compress proofs. 1 Introduction Proofs are the most important carriers of mathematical knowledge. Logic has endowed us with formal languages for proofs which make them amenable to al- gorithmic treatment. From the early days of automated deduction to the current state of the art in automated and interactive theorem proving we have witnessed a huge increase in the ability of computers to search for, formalise and work with proofs. Due to the continuing formalisation of computer science (e.g. in areas such as hardware and software verification) the importance of formal proofs will grow further. Formal proofs which are generated automatically are usually difficult or even impossible to understand for a human reader. This is due to several reasons: one is a potentially extreme length as in the well-known cases of the four colour theorem or the Kepler conjecture. -

The Drinker Paradox and Its Dual
The Drinker Paradox and its Dual Louis Warren and Hannes Diener and Maarten McKubre-Jordens Department of Mathematics and Statistics University of Canterbury December 3, 2018 Abstract The Drinker Paradox is as follows. In every nonempty tavern, there is a person such that if that person is drinking, then everyone in the tavern is drinking. Formally, ∃xϕ →∀yϕ[x/y] . Due to its counterintuitive nature it is called a paradox, even though it actually is a classical tautology. However, it is not minimally (or even intuitionistically) provable. The same can be said of its dual, which is (equivalent to) the well-known principle of independence of premise, ϕ →∃xψ ⊢ ∃x(ϕ → ψ) where x is not free in ϕ. In this paper we study the implications of adding these and other formula schemata to minimal logic. We show first that these principles are independent of the law of excluded middle and of each other, and second how these schemata relate to other well-known princi- ples, such as Markov’s Principle of unbounded search, providing proofs and semantic models where appropriate. 1 Introduction Minimal logic [11] provides, as its name suggests, a minimal setting for logical investigations. Starting from minimal logic, we can get to intuitionistic logic by adding ex falso quodlibet (EFQ), and to classical logic, by adding double negation elimination (DNE).1 Therefore, every statement proven over minimal logic can also be proven in intuitionistic logic and classical logic. In addition, minimal logic has many structural advantages, and is easier to analyse. Of course, there is a price one has to pay for working within a weak framework. -
Recent Advances in the Modal Model Checker Meth8 and VŁ4 Universal Logic
Recent advances in the modal model checker Meth8 and VŁ4 universal logic © Copyright 2016-2021 by Colin James III All rights reserved. Updated abstract at ersatz-systems.com; email: info@cec-services dot com In applied and theoretical mathematics, assertions are categorized in alphabetical order as: axiom; conjecture; definition, entry; equation; expression; formula; functor; hypothesis; inequality; metatheorem; paradox; problem; proof; schema; system; theorem; and thesis. We evaluate 1292 artifacts in 9672 assertions to confirm 778 as tautology and 8894 as not (91.96%) in 2419 draft pages by the Meth8/VŁ4 model checker. Meth8 is the acronym for mechanical theorem proof assistant in 8-bits. The semantic content or predicate basis of some expressions on their face does not disqualify them from evaluation by Meth8 in classical modal logic. However, the rules of classical logic, as based on the corrected Square of Opposition by Meth8, apply to virtually any logic system. Consequently some numerical equations are mapped to classical logic as Meth8 scripts. The rationale for mapping quantifiers as modal operators is based on satisfiability and reproducibility of validation of the 24-syllogisms from the corrected Square of Opposition. Test results are refuted as not tautologous, confirmed as tautologous, or neither. For a paradox, not tautologous means it is not a paradox, but not necessarily a contradiction either. The experimental tests used variables for 4 propositions, 4 theorems, and 11 propositions. The size of truth tables are respectively for 16-, 256-, and 2048- truth values, using recent advances in look up table indexing. The Meth8 modal theorem prover implements the logic system variant VŁ4 which corrects the quaternary Ł4 of Łukasiewicz. -

Applications of Foundational Proof Certificates in Theorem Proving
Applications of Foundational Proof Certificates in theorem proving par M. Roberto Blanco Martínez Thèse de doctorat de l’ préparée à Spécialité de doctorat: Informatique École doctorale no 580 Sciences et technologies de l’information et de la communication nnt: XXX Thèse présentée et soutenue à Palaiseau, le XX décembre 2017 Composition du Jury: Mme Laura Kovács Professeure des universités Rapporteuse Technische Universität Wien & Chalmers tekniska högskola M. Dale Miller Directeur de recherche Directeur de thèse Inria & LIX/École polytechnique M. Claudio Sacerdoti Coen Professeur des universités Rapporteur Alma Mater Studiorum - Università di Bologna D D E E F F Applications of Foundational Proof Certificates in theorem proving For Jason. Contents Contents v List of figures ix Preface xiii 1 Introduction 1 I Logical foundations 7 2 Structural proof theory 9 2.1 Concept of proof . .9 2.2 Evolution of proof theory . 10 2.3 Classical and intuitionistic logics . 12 2.4 Sequent calculus . 13 2.5 Focusing . 20 2.6 Soundness and completeness . 25 2.7 Notes . 26 3 Foundational Proof Certificates 29 3.1 Proof as trusted communication . 29 3.2 Augmented sequent calculus . 32 3.3 Running example: CNF decision procedure . 38 3.4 Running example: oracle strings . 39 3.5 Running example: decide depth . 41 3.6 Running example: binary resolution . 42 3.7 Checkers, kernels, clients and certificates . 45 3.8 Notes . 48 v vi contents II Logics without fixed points 53 4 Logic programming in intuitionistic logic 55 4.1 Logic and computation . 55 4.2 Logic programming . 56 4.3 λProlog . 59 4.4 FPC kernels . -

Craig Interpolation and Proof Manipulation
Craig Interpolation and Proof Manipulation Theory and Applications to Model Checking Doctoral Dissertation submitted to the Faculty of Informatics of the Università della Svizzera Italiana in partial fulfillment of the requirements for the degree of Doctor of Philosophy presented by Simone Fulvio Rollini under the supervision of Prof. Natasha Sharygina February 2014 Dissertation Committee Prof. Rolf Krause Università della Svizzera Italiana, Switzerland Prof. Evanthia Papadopoulou Università della Svizzera Italiana, Switzerland Prof. Roberto Sebastiani Università di Trento, Italy Prof. Ofer Strichman Technion, Israel Dissertation accepted on 06 February 2014 Prof. Natasha Sharygina Prof. Igor Pivkin Prof. Stefan Wolf i I certify that except where due acknowledgement has been given, the work pre- sented in this thesis is that of the author alone; the work has not been submitted previously, in whole or in part, to qualify for any other academic award; and the content of the thesis is the result of work which has been carried out since the offi- cial commencement date of the approved research program. ii Abstract Model checking is one of the most appreciated methods for automated formal veri- fication of software and hardware systems. The main challenge in model checking, i.e. scalability to complex systems of extremely large size, has been successfully ad- dressed by means of symbolic techniques, which rely on an efficient representation and manipulation of the systems based on first order logic. Symbolic model checking has been considerably enhanced with the introduction in the last years of Craig interpolation as a means of overapproximation. Interpolants can be efficiently computed from proofs of unsatisfiability based on their structure. -

Resolution Proof Transformation for Compression and Interpolation
Resolution Proof Transformation for Compression and Interpolation S.F. Rollini1, R. Bruttomesso2, N. Sharygina1, and A. Tsitovich3 1 University of Lugano, Switzerland fsimone.fulvio.rollini, [email protected] 2 Atrenta Advanced R&D of Grenoble, France [email protected] 3 Phonak, Switzerland [email protected] Abstract. Verification methods based on SAT, SMT, and Theorem Proving often rely on proofs of unsatisfiability as a powerful tool to extract information in order to reduce the overall effort. For example a proof may be traversed to identify a minimal reason that led to unsatisfi- ability, for computing abstractions, or for deriving Craig interpolants. In this paper we focus on two important aspects that concern efficient han- dling of proofs of unsatisfiability: compression and manipulation. First of all, since the proof size can be very large in general (exponential in the size of the input problem), it is indeed beneficial to adopt techniques to compress it for further processing. Secondly, proofs can be manipulated as a flexible preprocessing step in preparation for interpolant computa- tion. Both these techniques are implemented in a framework that makes use of local rewriting rules to transform the proofs. We show that a care- ful use of the rules, combined with existing algorithms, can result in an effective simplification of the original proofs. We have evaluated several heuristics on a wide range of unsatisfiable problems deriving from SAT and SMT test cases. 1 Introduction Symbolic verification methods rely on a representation of the state space as a set of formulae, which are manipulated by formal engines such as SAT- and SMT- arXiv:1307.2028v3 [cs.LO] 15 Apr 2014 solvers.