A Regulatory System for Optimal Legal Transaction Throughput in Cryptocurrency Blockchains
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pow, Pos, & Hybrid Protocols: a Matter of Complexity?
PoW, PoS, & Hybrid protocols: A Matter of Complexity? Renato P. dos Santos Blockchain Researcher at ULBRA – The Lutheran University of Brazil [email protected]. Melanie Swan Technology Theorist and Founder at Institute for Blockchain Studies [email protected] Abstract In a previous paper, it was discussed whether Bitcoin and/or its blockchain could be considered a complex system and, if so, whether a chaotic one, a positive response raising concerns about the likelihood of Bitcoin/blockchain entering a chaotic regime, with catastrophic consequences for financial systems based on it. This paper intends to simplify and extend that analysis to other PoW, PoS, and hybrid protocol-based cryptocurrencies. As before, this study was carried out with the help of Information Theory of Complex Systems, in general, and Crutchfield’s Statistical Complexity measure, in particular. This paper is a work-in-progress. Whereas PoW consensus was shown to be highly non-complex, the Nxt PoS consensus method studied shows an outstandingly higher measure of complexity, which is undesirable because it introduces unnecessary complexity into what should be a simple computational system. This paper is a work-in-progress and undoubtedly prone to incorrectness as a few cryptocurrencies may have changed their consensus algorithms. As next step, we intend to uncover some other measures that capture the qualitative notion of complexity of systems that can be applied to these cryptocurrencies to compare with the results here obtained. As a final thought, however, considering that a certain amount of chaoticity may have been potentially introduced in the Bitcoin market by the presence of the capital gains-seekers, one could wonder whether the recent surge of blockchain technology-based start-ups, even discounting all the scam cases, could not help to reduce non-linearity and prevent chaos. -

IFRS: Accounting for Crypto-Assets
IFRS (#) Accounting for crypto-assets Contents 1. Introduction 1 2. What are crypto-assets? 2 2.1. Cryptocurrencies 3 2.2. Tokens (crypto-assets other than cryptocurrencies) 5 3. Accounting for crypto-assets 10 3.1. Selected activities of standard setters 10 3.2. Special situations 13 3.3. Conclusion 15 4. Supporting details 16 5. Contacts 21 1 Introduction Crypto-assets experienced a breakout year in 2017. Cryptocurrencies, such as bitcoin and ether, have seen their prices surge as the public’s YoYj]f]kk`Ykaf[j]Yk]\$Yf\ÕfYf[aYdeYjc]lhYjla[ahYflk`Yn]l`mk af[j]Ykaf_dqlmjf]\l`]ajYll]flagflgl`]h`]fge]fgf&KaemdlYf]gmkdq$ a wave of new crypto-asset issuance has been sweeping the start-up fundraising world, sparking the interest of regulators in the process. 9[[gmflYflk`Yn]l`mk^YjZ]]ffglYZd]Zql`]ajj]dYlan]YZk]f[]^jge l`YlfYjjYlan]&H]j`Yhk$egklfglYZd]akl`]^Y[ll`Yll`]9mkljYdaYf 9[[gmflaf_KlYf\Yj\k:gYj\ 99K:!`YkkmZeall]\Y\ak[mkkagfhYh]j gfÉ\a_alYd[mjj]f[a]kÊlgl`]Afl]jfYlagfYd9[[gmflaf_KlYf\Yj\k :gYj\ A9K:!$Yf\l`]9[[gmflaf_KlYf\Yj\k:gYj\g^BYhYf 9K:B! `Ykakkm]\Yf]phgkmj]\jY^l^gjhmZda[[gee]flgfY[[gmflaf_^gj “virtual currencies”.1AfY\\alagf$l`]A9K:\ak[mkk]\[]jlYaf^]Ylmj]kg^ ljYfkY[lagfkafngdnaf_\a_alYd[mjj]f[a]k\mjaf_alke]]laf_afBYfmYjq *()0$Yf\oadd\ak[mkkaf^mlmj]o`]l`]jlg[gee]f[]Yj]k]Yj[`hjgb][l in this area.1 L`akYdkg`a_`da_`lkl`]dY[cg^YklYf\Yj\ar]\[jqhlg%Ykk]llYpgfgeq$ o`a[`eYc]kal\a^Õ[mdllg\]l]jeaf]l`]Yhhda[YZadalqg^klYf\Yj\k]ll]jkÌ hmZdak`]\h]jkh][lan]k&>mjl`]jegj]$\m]lgl`]\an]jkalqYf\hY[]g^ affgnYlagfYkkg[aYl]\oal`[jqhlg%Ykk]lk$l`]^Y[lkYf\[aj[meklYf[]k g^]Y[`af\ana\mYd[Yk]oadd\a^^]j$eYcaf_al\a^Õ[mdllg\jYo_]f]jYd [gf[dmkagfkgfl`]Y[[gmflaf_lj]Yle]fl& <]khal]l`]eYjc]lÌkaf[j]Ykaf_dqmj_]flf]]\^gjY[[gmflaf__ma\Yf[]$ l`]j]`Yn]Z]]ffg^gjeYdhjgfgmf[]e]flkgfl`aklgha[lg\Yl]& Afl`akj]hgjl$o]YaelgÕjklZja]Öqafljg\m[][jqhlg[mjj]f[a]kYf\ gl`]jlqh]kg^[jqhlg%Ykk]lk&L`]f$o]\ak[mkkkge]g^l`]j][]fl activities by accounting standard setters in relation to crypto-assets. -

BLOCK by BLOCK a Comparative Analysis of the Leading Distributed Ledgers
BLOCK BY BLOCK A Comparative Analysis of the Leading Distributed Ledgers Table of Contents EXECUTIVE SUMMARY 3 PRELIMINARY MATTERS 4 A NOTE ON METHODOLOGY 4 THE EVOLUTION OF DISTRIBUTED LEDGERS 5 SEC. 1 : TECHNICAL STRUCTURE & FEATURE SET 7 PUBLIC OR PRIVATE? 7 PERMISSIONED OR PERMISSIONLESS? 8 CONSENSUS MECHANISM 9 LANGUAGES SUPPORTED 10 TRANSACTION RATES 11 SMART CONTRACTS 12 ADDITIONAL FEATURES 13 SEC. 2 : BUSINESS CONSIDERATIONS 14 PROJECT GOVERNANCE 14 LICENSING 16 THIRD PARTY SUPPORT 16 DEVELOPER SUPPORT 17 PUBLISHER SUPPORT 18 BLOCKCHAIN AS A SERVICE (BAAS) PROVIDERS 19 PARTNERSHIPS 21 ASSOCIATED COSTS 22 PRICING 22 COST PER TRANSACTION 23 ENERGY CONSUMPTION 24 SEC. 3 : HEALTH INDICATORS 25 DEVELOPMENT ACTIVITY 25 MINDSHARE 27 PROJECT SITE POPULARITY 28 SEARCH ENGINE QUERY VOLUME 29 FINANCIAL STRENGTH INDICATORS 30 MARKET CAP 30 24 HOUR TRADING VOLUME 31 VENTURE CAPITAL AND INVESTORS 32 NODES ONLINE 33 WEISS CRYPTOCURRENCY RANKINGS 34 SIGNIFICANT DEPLOYMENTS 35 CONCLUSIONS 36 PUBLIC LEDGERS 37 PRIVATE LEDGERS 37 PROJECTS TO WATCH 40 APPENDIX A. PROJECT LINKS 42 MERCY CORPS 2 EXECUTIVE SUMMARY Purpose This report compares nine distributed ledger platforms on nearly 30 metrics What’s Included related to the capabilities and the health of each project. The analysis looks at a broad range of indicators -- both direct and indirect -- with the goal of Bitcoin synthesizing trends and patterns that define the market leaders. Corda Ethereum Audience Hyperledger Fabric Multichain This paper is intended for readers already familiar with distributed ledger NEO technologies and will prove most useful to those that are currently evaluating NXT platforms in order to make a decision where to build or deploy applications. -
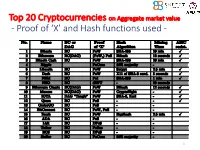
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Defending Against Malicious Reorgs in Tezos Proof-Of-Stake
Defending Against Malicious Reorgs in Tezos Proof-of-Stake Michael Neuder Daniel J. Moroz Harvard University Harvard University [email protected] [email protected] Rithvik Rao David C. Parkes Harvard University Harvard University [email protected] [email protected] ABSTRACT Conference on Advances in Financial Technologies (AFT ’20), October 21– Blockchains are intended to be immutable, so an attacker who is 23, 2020, New York, NY, USA. ACM, New York, NY, USA , 13 pages. https: //doi.org/10.1145/3419614.3423265 able to delete transactions through a chain reorganization (a ma- licious reorg) can perform a profitable double-spend attack. We study the rate at which an attacker can execute reorgs in the Tezos 1 INTRODUCTION Proof-of-Stake protocol. As an example, an attacker with 40% of the Blockchains are designed to be immutable in order to protect against staking power is able to execute a 20-block malicious reorg at an attackers who seek to delete transactions through chain reorga- average rate of once per day, and the attack probability increases nizations (malicious reorgs). Any attacker who causes a reorg of super-linearly as the staking power grows beyond 40%. Moreover, the chain could double-spend transactions, meaning they commit an attacker of the Tezos protocol knows in advance when an at- a transaction to the chain, receive some goods in exchange, and tack opportunity will arise, and can use this knowledge to arrange then delete the transaction, effectively robbing their counterparty. transactions to double-spend. We show that in particular cases, the Nakamoto [15] demonstrated that, in a Proof-of-Work (PoW) setting, Tezos protocol can be adjusted to protect against deep reorgs. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -
![Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction](https://docslib.b-cdn.net/cover/6379/arxiv-1907-02434v1-cs-cy-4-jul-2019-1-introduction-716379.webp)
Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction
Cryptocurrency Egalitarianism: A Quantitative Approach Dimitris Karakostas1,3, Aggelos Kiayias1,3, Christos Nasikas2,4, and Dionysis Zindros2,3 1 University of Edinburgh 2 University of Athens 3 IOHK 4 “ATHENA” Research Center Abstract. Since the invention of Bitcoin one decade ago, numerous cryptocurrencies have sprung into existence. Among these, proof-of-work is the most common mechanism for achieving consensus, whilst a num- ber of coins have adopted “ASIC-resistance” as a desirable property, claiming to be more “egalitarian,” where egalitarianism refers to the power of each coin to participate in the creation of new coins. While proof-of-work consensus dominates the space, several new cryptocurren- cies employ alternative consensus, such as proof-of-stake in which block minting opportunities are based on monetary ownership. A core criti- cism of proof-of-stake revolves around it being less egalitarian by making the rich richer, as opposed to proof-of-work in which everyone can con- tribute equally according to their computational power. In this paper, we give the first quantitative definition of a cryptocurrency’s egalitarian- ism. Based on our definition, we measure the egalitarianism of popular cryptocurrencies that (may or may not) employ ASIC-resistance, among them Bitcoin, Ethereum, Litecoin, and Monero. Our simulations show, as expected, that ASIC-resistance increases a cryptocurrency’s egalitar- ianism. We also measure the egalitarianism of a stake-based protocol, Ouroboros, and a hybrid proof-of-stake/proof-of-work cryptocurrency, Decred. We show that stake-based cryptocurrencies, under correctly se- lected parameters, can be perfectly egalitarian, perhaps contradicting folklore belief. arXiv:1907.02434v1 [cs.CY] 4 Jul 2019 1 Introduction In 2008, Satoshi Nakamoto proposed Bitcoin [25], the first and most suc- cessful cryptocurrency to date. -

Incentives in Ethereum's Hybrid Casper Protocol
Incentives in Ethereum’s Hybrid Casper Protocol Vitalik Buterin∗, Daniel¨ Reijsbergeny, Stefanos Leonardosy, Georgios Piliourasy ∗Ethereum Foundation ySingapore University of Technology and Design Abstract We present an overview of hybrid Casper the Friendly Finality Gadget (FFG): a Proof-of-Stake checkpointing protocol overlaid onto Ethereum’s Proof-of-Work blockchain. We describe its core functionalities and reward scheme, and explore its properties. Our findings indicate that Casper’s implemented incentives mechanism ensures liveness, while providing safety guarantees that improve over standard Proof-of-Work protocols. Based on a minimal-impact implementation of the protocol as a smart contract on the blockchain, we discuss additional issues related to parametrisation, funding, throughput and network overhead and detect potential limitations. Index Terms Proof of Stake, Ethereum, Consensus I. INTRODUCTION In 2008, the seminal Bitcoin paper by Satoshi Nakamoto [50] introduced the blockchain as a means for an open network to extend and reach consensus about a distributed ledger of digital token transfers. The main innovation of Ethereum [16] was to use the blockchain to maintain a history of code creation and execution. As such, Ethereum functions as a global computer that executes code uploaded by users in the form of smart contracts. Like Bitcoin [31], [32], Ethereum’s block proposal mechanism is based on the concept of Proof-of-Work (PoW). In PoW, network participants utilise computational power to win the right to add blocks to the blockchain. However, the alarming global energy consumption of PoW-based blockchains has made the concept increasingly controversial [22], [45], [65]. One of the main alternatives to PoW is virtual mining or Proof-of-Stake (PoS) [1], [5], [46], [55]. -

Building Applications on the Ethereum Blockchain
Building Applications on the Ethereum Blockchain Eoin Woods Endava @eoinwoodz licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 1 Agenda • Blockchain Recap • Ethereum • Application Design • Development • (Solidity – Ethereum’s Language) • Summary 3 Blockchain Recap 4 What is Blockchain? • Enabling technology of Bitcoin, Ethereum, … • Distributed database without a controlling authority • Auditable database with provable lineage • A way to collaborate with parties without direct trust • Architectural component for highly distributed Internet-scale systems 5 Architectural Characteristics of a Blockchain • P2P distributed • (Very) eventual consistency • Append only “ledger” • Computationally expensive • Cryptographic security • Limited query model (key only) (integrity & non-repudiation) • Lack of privacy (often) • Eventual consistency • low throughput scalability • Smart contracts (generally – 10s txn/sec) • Fault tolerant reliability 6 What Makes a Good Blockchain Application? • Multi-organisational • No complex query requirement • No trusted intermediary • Multiple untrusted writers • Need shared source of state • Latency insensitive (e.g. transactions, identity) • Relatively low throughput • Need for immutability (e.g. proof • Need for resiliency of existence) • Transaction interactions • Fairly small data size “If your requirements are fulfilled by today’s relational databases, you’d be insane to use a blockchain” – Gideon Greenspan 7 What is Blockchain being Used For? digital ledger that tracks and derivatives post- verifiable supply chains supply chain efficiency protects valuable assets trade processing Keybase Georgia government Identity management verified data post-trade processing records 8 Public and Permissioned Blockchains Public Permissioned Throughput Low Medium Latency High Medium # Readers High High # Writers High Low Centrally Managed No Yes Transaction Cost High “Free” Based on: Do you need a Blockchain? Karl Wüst, Arthur Gervaisy IACR Cryptology ePrint Archive, 2017, p.375. -

Privacy on the Blockchain: Unique Ring Signatures. Rebekah Mercer
Privacy on the Blockchain: Unique Ring Signatures. Rebekah Mercer This report is submitted as part requirement for the MSc in Information Security at University College London. 1 Supervised by Dr Nicolas T. Courtois. arXiv:1612.01188v2 [cs.CR] 25 Dec 2016 1This report is substantially the result of my own work except where explicitly indicated in the text. The report may be freely copied and distributed provided the source is explicitly acknowledged. Abstract Ring signatures are cryptographic protocols designed to allow any member of a group to produce a signature on behalf of the group, without revealing the individual signer’s identity. This offers group members a level of anonymity not attainable through generic digital signature schemes. We call this property ‘plausible deniability’, or anonymity with respect to an anonymity set. We concentrate in particular on implementing privacy on the blockchain, introducing a unique ring signature scheme that works with existing blockchain systems. We implement a unique ring signature (URS) scheme using secp256k1, creating the first implemen- tation compatible with blockchain libraries in this way, so as for easy implementation as an Ethereum smart contract. We review the privacy and security properties offered by the scheme we have constructed, and compare its efficiency with other commonly suggested approaches to privacy on the blockchain. 1 Acknowledgements Thank you to Dr Nicolas Courtois, for introducing me to blockchains and applied cryptography. Thanks to Matthew Di Ferrante, for continued insight and expertise on Ethereum and adversarial security. Thanks also to my mum and dad, for convincing me that can handle an MSc alongside a full time job, and for all the advice along the way! Finally, thanks to the University of Manchester, UCL, Yorkshire Ladies’ Trust, and countless others for their generous grants over the years, without which this MSc would not have been possible. -

Algorand: Scaling Byzantine Agreements for Cryptocurrencies Yossi Gilad, Rotem Hemo, Silvio Micali, Georgios Vlachos, Nickolai Zeldovich MIT CSAIL
Algorand: Scaling Byzantine Agreements for Cryptocurrencies Yossi Gilad, Rotem Hemo, Silvio Micali, Georgios Vlachos, Nickolai Zeldovich MIT CSAIL ABSTRACT open setting: since anyone can participate, an adversary can create an arbitrary number of pseudonyms (“Sybils”) [21], Algorand is a new cryptocurrency that confirms transactions making it infeasible to rely on traditional consensus proto- with latency on the order of a minute while scaling to many cols [15] that require a fraction of honest users. users. Algorand ensures that users never have divergent views of confirmed transactions, even if some of the users Bitcoin [41] and other cryptocurrencies [23, 53] address are malicious and the network is temporarily partitioned. this problem using proof-of-work (PoW), where users must In contrast, existing cryptocurrencies allow for temporary repeatedly compute hashes to grow the blockchain, and forks and therefore require a long time, on the order of an the longest chain is considered authoritative. PoW ensures hour, to confirm transactions with high confidence. that an adversary does not gain any advantage by creating Algorand uses a new Byzantine Agreement (BA) protocol pseudonyms. However, PoW allows the possibility of forks, to reach consensus among users on the next set of trans- where two different blockchains have the same length, and actions. To scale the consensus to many users, Algorand neither one supersedes the other. Mitigating forks requires uses a novel mechanism based on Verifiable Random Func- two unfortunate sacrifices: the time to grow the chain byone tions that allows users to privately check whether they are block must be reasonably high (e.g., 10 minutes in Bitcoin), selected to participate in the BA to agree on the next set and applications must wait for several blocks in order to of transactions, and to include a proof of their selection in ensure their transaction remains on the authoritative chain their network messages. -

A Probabilistic Analysis of the Nxt Forging Algorithm: Open Review
ISSN 2379-5980 (online) associated article DOI 10.5915/LEDGER.2016.46 A Probabilistic Analysis of the Nxt Forging Algorithm: Open Review Author: Serguei Popov*† Reviewers: Reviewer A, Reviewer B, Reviewer C Abstract. The final version of the paper “Gaming Self-Contained Provably Fair Smart Contract Casinos” can be found in Ledger Vol. 1 (2016) 69-83, DOI 10.5915/LEDGER.2016.46. There were three reviewers, none of whom have requested to waive their anonymity at present, and are thus listed as A, B, and C. After initial review (1A), the author submitted a revised submission and response (1B). After a second round of review by Reviewers A and C (2A), the assigned Ledger editor determined that the author had adequately addressed the reviewer concerns. The assigned ledger editor asked the author for minor revisions, which once addressed completed the peer-review process. Author’s responses in 1B are in bullet form. 1A. Review, First Round Reviewer A: This work analyzes a proof-of-stake algorithm addressing several questions -- how forgers are chosen (uniform vs. exponential), whether a rational forger should split itself into several smaller forgers, and what advantage it can gain by gaming the system and choosing one of its forgers such that its own forgers are chosen in future steps. The paper addresses important issues, reaching non-trivial results. The paper's presentation does not do the content justice. Most prominently, a background section is completely missing. The paper revolves around a proof-of-stake protocol. There is no such protocol that is widely believed to be secure, despite its de-facto usage in the NXT coin.