Paycrypto: Proof-Of-Stake Vs Proof-Of-Work
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Beauty Is Not in the Eye of the Beholder
Insight Consumer and Wealth Management Digital Assets: Beauty Is Not in the Eye of the Beholder Parsing the Beauty from the Beast. Investment Strategy Group | June 2021 Sharmin Mossavar-Rahmani Chief Investment Officer Investment Strategy Group Goldman Sachs The co-authors give special thanks to: Farshid Asl Managing Director Matheus Dibo Shahz Khatri Vice President Vice President Brett Nelson Managing Director Michael Murdoch Vice President Jakub Duda Shep Moore-Berg Harm Zebregs Vice President Vice President Vice President Shivani Gupta Analyst Oussama Fatri Yousra Zerouali Vice President Analyst ISG material represents the views of ISG in Consumer and Wealth Management (“CWM”) of GS. It is not financial research or a product of GS Global Investment Research (“GIR”) and may vary significantly from those expressed by individual portfolio management teams within CWM, or other groups at Goldman Sachs. 2021 INSIGHT Dear Clients, There has been enormous change in the world of cryptocurrencies and blockchain technology since we first wrote about it in 2017. The number of cryptocurrencies has increased from about 2,000, with a market capitalization of over $200 billion in late 2017, to over 8,000, with a market capitalization of about $1.6 trillion. For context, the market capitalization of global equities is about $110 trillion, that of the S&P 500 stocks is $35 trillion and that of US Treasuries is $22 trillion. Reported trading volume in cryptocurrencies, as represented by the two largest cryptocurrencies by market capitalization, has increased sixfold, from an estimated $6.8 billion per day in late 2017 to $48.6 billion per day in May 2021.1 This data is based on what is called “clean data” from Coin Metrics; the total reported trading volume is significantly higher, but much of it is artificially inflated.2,3 For context, trading volume on US equity exchanges doubled over the same period. -
Proof of 'X' and Hash Functions Used
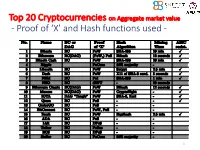
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Short Selling Attack: a Self-Destructive but Profitable 51% Attack on Pos Blockchains
Short Selling Attack: A Self-Destructive But Profitable 51% Attack On PoS Blockchains Suhyeon Lee and Seungjoo Kim CIST (Center for Information Security Technologies), Korea University, Korea Abstract—There have been several 51% attacks on Proof-of- With a PoS, the attacker needs to obtain 51% of the Work (PoW) blockchains recently, including Verge and Game- cryptocurrency to carry out a 51% attack. But unlike PoW, Credits, but the most noteworthy has been the attack that saw attacker in a PoS system is highly discouraged from launching hackers make off with up to $18 million after a successful double spend was executed on the Bitcoin Gold network. For this reason, 51% attack because he would have to risk of depreciation the Proof-of-Stake (PoS) algorithm, which already has advantages of his entire stake amount to do so. In comparison, bad of energy efficiency and throughput, is attracting attention as an actor in a PoW system will not lose their expensive alternative to the PoW algorithm. With a PoS, the attacker needs mining equipment if he launch a 51% attack. Moreover, to obtain 51% of the cryptocurrency to carry out a 51% attack. even if a 51% attack succeeds, the value of PoS-based But unlike PoW, attacker in a PoS system is highly discouraged from launching 51% attack because he would have to risk losing cryptocurrency will fall, and the attacker with the most stake his entire stake amount to do so. Moreover, even if a 51% attack will eventually lose the most. For these reasons, those who succeeds, the value of PoS-based cryptocurrency will fall, and attempt to attack 51% of the PoS blockchain will not be the attacker with the most stake will eventually lose the most. -

Bitflyer Raises Approximately JPY 130 Million in Funds
bitFlyer, Inc Yuzo Kano, CEO bitFlyer Raises JPY 130 million in Funds We are delighted to announce that bitFlyer (Company Headquarters: Chiyoda-ku, Tokyo, Yuzo Kano, CEO), in order to expand its comprehensive Bitcoin platform and marketplace, has closed a fundraising round of approximately JPY 130 million. We are pleased to have received an investment from several third party investment organizations, including the below (titles omitted, in no particular order): RSP Fund No. 5 (Headquarters: Chuo-ku, Tokyo, Akihiko Okamoto, President) GMO Venture Partners (Headquarters: Shibuya-ku, Tokyo, Masatoshi Kumagai, CEO) Bitcoin Opportunity Corp (Headquarters: New York, USA, Barry Silbert, CEO) The purpose of this funding will be to further strengthen our Bitcoin related businesses in the domestic as well as international markets, set up overseas offices, recruit new talent, accelerate service development, and carry out marketing and advertising campaigns to promote business growth. In addition, the synergies gained through close collaboration with our investment partners, customer base expansion, and the strengthening of our revenue base will help to facilitate our global business expansion. We will continue to pursue our primary goals of improving security while providing the best possible services to our customers. Thank you for using bitFlyer. Reference 1. Information Regarding our Investment Partners RSP Fund No. 5 RSP Fund No. 5 is a wholly owned subsidiary of Recruit Holdings, Co., Ltd. Headquartered in Tokyo and with offices in Silicon Valley, RSP invests in and provides management support to IT companies that provide innovative products and services around the world. GMO Venture Partners GMO Venture Partners is the venture capital arm of GMO Internet Group, investing more than JPY 5 billion to 51 companies in total, including 8 listed companies. -
![Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction](https://docslib.b-cdn.net/cover/6379/arxiv-1907-02434v1-cs-cy-4-jul-2019-1-introduction-716379.webp)
Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction
Cryptocurrency Egalitarianism: A Quantitative Approach Dimitris Karakostas1,3, Aggelos Kiayias1,3, Christos Nasikas2,4, and Dionysis Zindros2,3 1 University of Edinburgh 2 University of Athens 3 IOHK 4 “ATHENA” Research Center Abstract. Since the invention of Bitcoin one decade ago, numerous cryptocurrencies have sprung into existence. Among these, proof-of-work is the most common mechanism for achieving consensus, whilst a num- ber of coins have adopted “ASIC-resistance” as a desirable property, claiming to be more “egalitarian,” where egalitarianism refers to the power of each coin to participate in the creation of new coins. While proof-of-work consensus dominates the space, several new cryptocurren- cies employ alternative consensus, such as proof-of-stake in which block minting opportunities are based on monetary ownership. A core criti- cism of proof-of-stake revolves around it being less egalitarian by making the rich richer, as opposed to proof-of-work in which everyone can con- tribute equally according to their computational power. In this paper, we give the first quantitative definition of a cryptocurrency’s egalitarian- ism. Based on our definition, we measure the egalitarianism of popular cryptocurrencies that (may or may not) employ ASIC-resistance, among them Bitcoin, Ethereum, Litecoin, and Monero. Our simulations show, as expected, that ASIC-resistance increases a cryptocurrency’s egalitar- ianism. We also measure the egalitarianism of a stake-based protocol, Ouroboros, and a hybrid proof-of-stake/proof-of-work cryptocurrency, Decred. We show that stake-based cryptocurrencies, under correctly se- lected parameters, can be perfectly egalitarian, perhaps contradicting folklore belief. arXiv:1907.02434v1 [cs.CY] 4 Jul 2019 1 Introduction In 2008, Satoshi Nakamoto proposed Bitcoin [25], the first and most suc- cessful cryptocurrency to date. -

A Regulatory System for Optimal Legal Transaction Throughput in Cryptocurrency Blockchains
A Regulatory System for Optimal Legal Transaction Throughput in Cryptocurrency Blockchains Aditya Ahuja Vinay J. Ribeiro Ranjan Pal Indian Institute of Technology Indian Institute of Technology University of Michigan Delhi Bombay Ann Arbor, USA New Delhi, India Mumbai, India [email protected] [email protected] [email protected] ABSTRACT correctness of the underlying computational principles, which are a Permissionless blockchain consensus protocols have been designed basis of the efficacy of these economies. More specifically, in order primarily for defining decentralized economies for the commercial to sustain these cryptocurrency based decentralized economies, trade of assets, both virtual and physical, using cryptocurrencies. blockchain consensus protocols serve as a technical foundation. In most instances, the assets being traded are regulated, which man- Existing blockchain protocols for cryptocurrencies address one dates that the legal right to their trade and their trade value are of (or any combination of) the following system goals: speed, se- determined by the governmental regulator of the jurisdiction in curity and decentralization. Unfortunately, these system goals are which the trade occurs. Unfortunately, existing blockchains do not necessary but insufficient. Illegal activities propelled through the formally recognise proposal of legal cryptocurrency transactions, as strategic use of blockchain based cryptocurrencies, is a serious part of the execution of their respective consensus protocols, result- problem staring at the face of many world governments today ing in rampant illegal activities in the associated crypto-economies. [47]. These illegal activities exploit the permissionless nature of In this contribution, we motivate the need for regulated blockchain the blockchain networks for illegal trade, to strategically defeat consensus protocols with a case study of the illegal, cryptocurrency regulation by obfuscating the jurisdictions of the blockchain users based, Silk Road darknet market. -

Blockchain in Japan
Blockchain in Japan " 1" Blockchain in Japan " "The impact of Blockchain is huge. Its importance is similar to the emergence of Internet” Ministry of Economy, Trade and Industry of Japan1 1 Japanese Trade Ministry Exploring Blockchain Tech in Study Group, Coindesk 2" Blockchain in Japan " About this report This report has been made by Marta González for the EU-Japan Centre for Industrial Cooperation, a joint venture between the European Commission and the Japanese Ministry of Economy, Trade and Industry (METI). The Centre aims to promote all forms of industrial, trade and investment cooperation between Europe and Japan. For that purpose, it publishes a series of thematic reports designed to support research and policy analysis of EU-Japan economic and industrial issues. To elaborate this report, the author has relied on a wide variety of sources. She reviewed the existing literature, including research papers and press articles, and interviewed a number of Blockchain thought leaders and practitioners to get their views. She also relied on the many insights from the Japanese Blockchain community, including startups, corporation, regulators, associations and developers. Additionally, she accepted an invitation to give a talk1 about the state of Blockchain in Europe, where she also received input and interest from Japanese companies to learn from and cooperate with the EU. She has also received numerous manifestations of interest during the research and writing of the report, from businesses to regulatory bodies, revealing a strong potential for cooperation between Europe and Japan in Blockchain-related matters. THE AUTHOR Marta González is an Economist and Software Developer specialized in FinTech and Blockchain technology. -

Incentives in Ethereum's Hybrid Casper Protocol
Incentives in Ethereum’s Hybrid Casper Protocol Vitalik Buterin∗, Daniel¨ Reijsbergeny, Stefanos Leonardosy, Georgios Piliourasy ∗Ethereum Foundation ySingapore University of Technology and Design Abstract We present an overview of hybrid Casper the Friendly Finality Gadget (FFG): a Proof-of-Stake checkpointing protocol overlaid onto Ethereum’s Proof-of-Work blockchain. We describe its core functionalities and reward scheme, and explore its properties. Our findings indicate that Casper’s implemented incentives mechanism ensures liveness, while providing safety guarantees that improve over standard Proof-of-Work protocols. Based on a minimal-impact implementation of the protocol as a smart contract on the blockchain, we discuss additional issues related to parametrisation, funding, throughput and network overhead and detect potential limitations. Index Terms Proof of Stake, Ethereum, Consensus I. INTRODUCTION In 2008, the seminal Bitcoin paper by Satoshi Nakamoto [50] introduced the blockchain as a means for an open network to extend and reach consensus about a distributed ledger of digital token transfers. The main innovation of Ethereum [16] was to use the blockchain to maintain a history of code creation and execution. As such, Ethereum functions as a global computer that executes code uploaded by users in the form of smart contracts. Like Bitcoin [31], [32], Ethereum’s block proposal mechanism is based on the concept of Proof-of-Work (PoW). In PoW, network participants utilise computational power to win the right to add blocks to the blockchain. However, the alarming global energy consumption of PoW-based blockchains has made the concept increasingly controversial [22], [45], [65]. One of the main alternatives to PoW is virtual mining or Proof-of-Stake (PoS) [1], [5], [46], [55]. -

Building Applications on the Ethereum Blockchain
Building Applications on the Ethereum Blockchain Eoin Woods Endava @eoinwoodz licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 1 Agenda • Blockchain Recap • Ethereum • Application Design • Development • (Solidity – Ethereum’s Language) • Summary 3 Blockchain Recap 4 What is Blockchain? • Enabling technology of Bitcoin, Ethereum, … • Distributed database without a controlling authority • Auditable database with provable lineage • A way to collaborate with parties without direct trust • Architectural component for highly distributed Internet-scale systems 5 Architectural Characteristics of a Blockchain • P2P distributed • (Very) eventual consistency • Append only “ledger” • Computationally expensive • Cryptographic security • Limited query model (key only) (integrity & non-repudiation) • Lack of privacy (often) • Eventual consistency • low throughput scalability • Smart contracts (generally – 10s txn/sec) • Fault tolerant reliability 6 What Makes a Good Blockchain Application? • Multi-organisational • No complex query requirement • No trusted intermediary • Multiple untrusted writers • Need shared source of state • Latency insensitive (e.g. transactions, identity) • Relatively low throughput • Need for immutability (e.g. proof • Need for resiliency of existence) • Transaction interactions • Fairly small data size “If your requirements are fulfilled by today’s relational databases, you’d be insane to use a blockchain” – Gideon Greenspan 7 What is Blockchain being Used For? digital ledger that tracks and derivatives post- verifiable supply chains supply chain efficiency protects valuable assets trade processing Keybase Georgia government Identity management verified data post-trade processing records 8 Public and Permissioned Blockchains Public Permissioned Throughput Low Medium Latency High Medium # Readers High High # Writers High Low Centrally Managed No Yes Transaction Cost High “Free” Based on: Do you need a Blockchain? Karl Wüst, Arthur Gervaisy IACR Cryptology ePrint Archive, 2017, p.375. -

Trading and Arbitrage in Cryptocurrency Markets
Trading and Arbitrage in Cryptocurrency Markets Igor Makarov1 and Antoinette Schoar∗2 1London School of Economics 2MIT Sloan, NBER, CEPR December 15, 2018 ABSTRACT We study the efficiency, price formation and segmentation of cryptocurrency markets. We document large, recurrent arbitrage opportunities in cryptocurrency prices relative to fiat currencies across exchanges, which often persist for weeks. Price deviations are much larger across than within countries, and smaller between cryptocurrencies. Price deviations across countries co-move and open up in times of large appreciations of the Bitcoin. Countries that on average have a higher premium over the US Bitcoin price also see a bigger widening of arbitrage deviations in times of large appreciations of the Bitcoin. Finally, we decompose signed volume on each exchange into a common and an idiosyncratic component. We show that the common component explains up to 85% of Bitcoin returns and that the idiosyncratic components play an important role in explaining the size of the arbitrage spreads between exchanges. ∗Igor Makarov: Houghton Street, London WC2A 2AE, UK. Email: [email protected]. An- toinette Schoar: 62-638, 100 Main Street, Cambridge MA 02138, USA. Email: [email protected]. We thank Yupeng Wang and Yuting Wang for outstanding research assistance. We thank seminar participants at the Brevan Howard Center at Imperial College, EPFL Lausanne, European Sum- mer Symposium in Financial Markets 2018 Gerzensee, HSE Moscow, LSE, and Nova Lisbon, as well as Anastassia Fedyk, Adam Guren, Simon Gervais, Dong Lou, Peter Kondor, Gita Rao, Norman Sch¨urhoff,and Adrien Verdelhan for helpful comments. Andreas Caravella, Robert Edstr¨omand Am- bre Soubiran provided us with very useful information about the data. -

Algorand: Scaling Byzantine Agreements for Cryptocurrencies Yossi Gilad, Rotem Hemo, Silvio Micali, Georgios Vlachos, Nickolai Zeldovich MIT CSAIL
Algorand: Scaling Byzantine Agreements for Cryptocurrencies Yossi Gilad, Rotem Hemo, Silvio Micali, Georgios Vlachos, Nickolai Zeldovich MIT CSAIL ABSTRACT open setting: since anyone can participate, an adversary can create an arbitrary number of pseudonyms (“Sybils”) [21], Algorand is a new cryptocurrency that confirms transactions making it infeasible to rely on traditional consensus proto- with latency on the order of a minute while scaling to many cols [15] that require a fraction of honest users. users. Algorand ensures that users never have divergent views of confirmed transactions, even if some of the users Bitcoin [41] and other cryptocurrencies [23, 53] address are malicious and the network is temporarily partitioned. this problem using proof-of-work (PoW), where users must In contrast, existing cryptocurrencies allow for temporary repeatedly compute hashes to grow the blockchain, and forks and therefore require a long time, on the order of an the longest chain is considered authoritative. PoW ensures hour, to confirm transactions with high confidence. that an adversary does not gain any advantage by creating Algorand uses a new Byzantine Agreement (BA) protocol pseudonyms. However, PoW allows the possibility of forks, to reach consensus among users on the next set of trans- where two different blockchains have the same length, and actions. To scale the consensus to many users, Algorand neither one supersedes the other. Mitigating forks requires uses a novel mechanism based on Verifiable Random Func- two unfortunate sacrifices: the time to grow the chain byone tions that allows users to privately check whether they are block must be reasonably high (e.g., 10 minutes in Bitcoin), selected to participate in the BA to agree on the next set and applications must wait for several blocks in order to of transactions, and to include a proof of their selection in ensure their transaction remains on the authoritative chain their network messages. -

Financial Services | New York Attorney General Investigates
Financial Services New York Attorney General Launches Cryptocurrency Exchange Inquiry By: Jolene E. Negre On April 17, the New York Attorney General’s Office released a statement that it has launched a fact- finding inquiry into 13 cryptocurrency exchanges. Questionnaires were sent to the following exchanges: Coinbase, Inc. (GDAX) Gemini Trust Company bitFlyer USA, Inc. iFinex Inc. (Bitfinex) Bitstamp USA Inc. Payward, Inc. (Kraken) Bittrex, Inc. Circle Internet Financial Limited (Poloniex LLC) Binance Limited Elite Way Developments LLP (Tidex.com) Gate Technology Incorporated (Gate.io) itBit Trust Company Huobi Global Limited (Huobi.Pro) The text of the questionnaires can be found here. The Attorney General’s release suggests that the inquiry is part of a broader investor protection effort and emphasizes a greater need for transparency and accountability. The questionnaires relate to the following categories: Ownership and control Basic operation and fees Trading policies and procedures Outages and other suspensions of trading Internal controls Privacy and money laundering Protections against risks to customer funds Written materials New York State's action comes on the heels of reports in March that the US Securities and Exchange Commission (SEC) issued subpoenas to as many as 80 entities and individuals involved in the virtual currency space over the preceding several months. As additional regulators enter the fray, cryptocurrency exchanges would be well served to consult with counsel regarding their business practices. Contact Us Jolene E. Negre Corporate [email protected] | Download V-Card David Bitkower Investigations, Compliance and Defense [email protected] | Download V-Card Meet our FinTech Team © 2018 Jenner & Block LLP.