Blockchain Consensus: an Analysis of Proof-Of-Work and Its Applications. Amitai Porat1, Avneesh Pratap2, Parth Shah3, and Vinit Adkar4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

American Bar Association Business Law Section Committee on Derivatives and Futures Law
American Bar Association Business Law Section Committee on Derivatives and Futures Law Winter Meeting 2018 Naples, Florida Friday, January 19, 2018 10:15 a.m. to 11:30 a.m. NEW PRODUCTS / FINANCIAL TECHNOLOGY Moderator for the Program: Conrad G. Bahlke, Willkie Farr &Gallagher LLP Speakers: Geoffrey F. Aronow, Sidley Austin LLP Debra W. Cook, Depository Trust & Clearing Corporation Katherine Cooper, Law Office of Katherine Cooper Isabelle Corbett, R3 David Lucking, Allen & Overy LLP Brian D. Quintenz, Commissioner, U.S. Commodity Futures Trading Commission ABA BUSINESS LAW SECTION DERIVATIVES & FUTURES LAW COMMITTEE 2018 WINTER MEETING NEW PRODUCTS / FIN TECH PANEL 2017 Developments in US Regulation of Virtual Currencies and Related Products: Yin and Yang January 5, 2018 By Katherine Cooper1 2017 was a year during which virtual currencies began to move into the mainstream financial markets. This generated significant legal and regulatory developments as U.S. regulators faced numerous novel products attempting to blend the old with the new. Although facing so many novel issues, the regulators’ responses tell a familiar story of the struggle to balance the yin of customer protection with the yang of encouraging financial innovation and competition. Below is a summary of 2017 developments from the SEC, CFTC, OCC, FinCEN and the States. I. Securities and Exchange Commission a. Bitcoin Exchange-Traded Products A number of sponsors of proposed Bitcoin exchange traded products had applications for approval pending before the Securities and Exchange Commission at the beginning of 2017. In March 2017, the SEC rejected a proposal backed by Tyler and Cameron Winklevoss.2 The Bats Exchange proposed a rule amendment which would list the shares of the Winklevoss Bitcoin Trust for trading. -

Introducing Ethereum and Solidity Foundations of Cryptocurrency and Blockchain Programming for Beginners
C. Dannen Introducing Ethereum and Solidity Foundations of Cryptocurrency and Blockchain Programming for Beginners ▶ First book on the market that teaches Ethereum and Solidity for technical thinkers of all types ▶ Written by a technology journalist trained in breaking down technical concepts into easy-to-understand prose ▶ Updates you on the last three years of progress since Bitcoin became popular - a new frontier replete with opportunity for new products and services Learn how to use Solidity and the Ethereum project – second only to Bitcoin in market capitalization. Blockchain protocols are taking the world by storm, and the Ethereum project, with its Turing-complete scripting language Solidity, has rapidly become a front-runner. This book presents the blockchain phenomenon in context; then situates Ethereum in a world pioneered by Bitcoin. 1st ed., XXI, 185 p. 34 illus., 31 illus. in color. A product of Apress See why professionals and non-professionals alike are honing their skills in smart contract patterns and distributed application development. You'll review the fundamentals of programming and networking, alongside its introduction to the new discipline of crypto- Printed book economics. You'll then deploy smart contracts of your own, and learn how they can serve as a back-end for JavaScript and HTML applications on the Web. Softcover ISBN 978-1-4842-2534-9 Many Solidity tutorials out there today have the same flaw: they are written for“advanced” ▶ 44,99 € | £39.99 JavaScript developers who want to transfer their skills to a blockchain environment. ▶ *48,14 € (D) | 49,49 € (A) | CHF 53.50 Introducing Ethereum and Solidity is accessible to technology professionals and enthusiasts of “all levels.” You’ll find exciting sample code that can move forward real world assets in both the academic and the corporate arenas. -

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

Beauty Is Not in the Eye of the Beholder
Insight Consumer and Wealth Management Digital Assets: Beauty Is Not in the Eye of the Beholder Parsing the Beauty from the Beast. Investment Strategy Group | June 2021 Sharmin Mossavar-Rahmani Chief Investment Officer Investment Strategy Group Goldman Sachs The co-authors give special thanks to: Farshid Asl Managing Director Matheus Dibo Shahz Khatri Vice President Vice President Brett Nelson Managing Director Michael Murdoch Vice President Jakub Duda Shep Moore-Berg Harm Zebregs Vice President Vice President Vice President Shivani Gupta Analyst Oussama Fatri Yousra Zerouali Vice President Analyst ISG material represents the views of ISG in Consumer and Wealth Management (“CWM”) of GS. It is not financial research or a product of GS Global Investment Research (“GIR”) and may vary significantly from those expressed by individual portfolio management teams within CWM, or other groups at Goldman Sachs. 2021 INSIGHT Dear Clients, There has been enormous change in the world of cryptocurrencies and blockchain technology since we first wrote about it in 2017. The number of cryptocurrencies has increased from about 2,000, with a market capitalization of over $200 billion in late 2017, to over 8,000, with a market capitalization of about $1.6 trillion. For context, the market capitalization of global equities is about $110 trillion, that of the S&P 500 stocks is $35 trillion and that of US Treasuries is $22 trillion. Reported trading volume in cryptocurrencies, as represented by the two largest cryptocurrencies by market capitalization, has increased sixfold, from an estimated $6.8 billion per day in late 2017 to $48.6 billion per day in May 2021.1 This data is based on what is called “clean data” from Coin Metrics; the total reported trading volume is significantly higher, but much of it is artificially inflated.2,3 For context, trading volume on US equity exchanges doubled over the same period. -

Bitcoin Tumbles As Miners Face Crackdown - the Buttonwood Tree Bitcoin Tumbles As Miners Face Crackdown
6/8/2021 Bitcoin Tumbles as Miners Face Crackdown - The Buttonwood Tree Bitcoin Tumbles as Miners Face Crackdown By Haley Cafarella - June 1, 2021 Bitcoin tumbles as Crypto miners face crackdown from China. Cryptocurrency miners, including HashCow and BTC.TOP, have halted all or part of their China operations. This comes after Beijing intensified a crackdown on bitcoin mining and trading. Beijing intends to hammer digital currencies amid heightened global regulatory scrutiny. This marks the first time China’s cabinet has targeted virtual currency mining, which is a sizable business in the world’s second-biggest economy. Some estimates say China accounts for as much as 70 percent of the world’s crypto supply. Cryptocurrency exchange Huobi suspended both crypto-mining and some trading services to new clients from China. The plan is that China will instead focus on overseas businesses. BTC.TOP, a crypto mining pool, also announced the suspension of its China business citing regulatory risks. On top of that, crypto miner HashCow said it would halt buying new bitcoin mining rigs. Crypto miners use specially-designed computer equipment, or rigs, to verify virtual coin transactions. READ MORE: Sustainable Mineral Exploration Powers Electric Vehicle Revolution This process produces newly minted crypto currencies like bitcoin. “Crypto mining consumes a lot of energy, which runs counter to China’s carbon neutrality goals,” said Chen Jiahe, chief investment officer of Beijing-based family office Novem Arcae Technologies. Additionally, he said this is part of China’s goal of curbing speculative crypto trading. As result, bitcoin has taken a beating in the stock market. -

User Manual Ledger Nano S
User Manual Ledger Nano S Version control 4 Check if device is genuine 6 Buy from an official Ledger reseller 6 Check the box contents 6 Check the Recovery sheet came blank 7 Check the device is not preconfigured 8 Check authenticity with Ledger applications 9 Summary 9 Learn more 9 Initialize your device 10 Before you start 10 Start initialization 10 Choose a PIN code 10 Save your recovery phrase 11 Next steps 11 Update the Ledger Nano S firmware 12 Before you start 12 Step by step instructions 12 Restore a configuration 18 Before you start 19 Start restoration 19 Choose a PIN code 19 Enter recovery phrase 20 If your recovery phrase is not valid 20 Next steps 21 Optimize your account security 21 Secure your PIN code 21 Secure your 24-word recovery phrase 21 Learn more 22 Discover our security layers 22 Send and receive crypto assets 24 List of supported applications 26 Applications on your Nano S 26 Ledger Applications on your computer 27 Third-Party applications on your computer 27 If a transaction has two outputs 29 Receive mining proceeds 29 Receiving a large amount of small transactions is troublesome 29 In case you received a large amount of small payments 30 Prevent problems by batching small transactions 30 Set up and use Electrum 30 Set up your device with EtherDelta 34 Connect with Radar Relay 36 Check the firmware version 37 A new Ledger Nano S 37 A Ledger Nano S in use 38 Update the firmware 38 Change the PIN code 39 Hide accounts with a passphrase 40 Advanced Passphrase options 42 How to best use the passphrase feature 43 -

Crypto-Asset Markets: Potential Channels for Future Financial Stability
Crypto-asset markets Potential channels for future financial stability implications 10 October 2018 The Financial Stability Board (FSB) is established to coordinate at the international level the work of national financial authorities and international standard-setting bodies in order to develop and promote the implementation of effective regulatory, supervisory and other financial sector policies. Its mandate is set out in the FSB Charter, which governs the policymaking and related activities of the FSB. These activities, including any decisions reached in their context, shall not be binding or give rise to any legal rights or obligations under the FSB’s Articles of Association. Contacting the Financial Stability Board Sign up for e-mail alerts: www.fsb.org/emailalert Follow the FSB on Twitter: @FinStbBoard E-mail the FSB at: [email protected] Copyright © 2018 Financial Stability Board. Please refer to: www.fsb.org/terms_conditions/ Contents Executive Summary ................................................................................................................... 1 1. Introduction ......................................................................................................................... 3 2. Primary risks in crypto-asset markets ................................................................................. 5 2.1 Market liquidity risks ............................................................................................... 5 2.2 Volatility risks ......................................................................................................... -

Blockchain & Distributed Ledger Technologies
Science, Technology Assessment, SEPTEMBER 2019 and Analytics WHY THIS MATTERS Distributed ledger technology (e.g. blockchain) allows users to carry out digital transactions without the need SCIENCE & TECH SPOTLIGHT: for a centralized authority. It could fundamentally change the way government and industry conduct BLOCKCHAIN & DISTRIBUTED business, but questions remain about how to mitigate fraud, money laundering, and excessive energy use. LEDGER TECHNOLOGIES /// THE TECHNOLOGY What is it? Distributed ledger technologies (DLT) like blockchain are a secure way of conducting and recording transfers of digital assets without the need for a central authority. DLT is “distributed” because multiple participants in a computer network (individuals, businesses, etc.), share and synchronize copies of the ledger. New transactions are added in a manner that is cryptographically secured, permanent, and visible to all participants in near real time. Figure 2. How blockchain, a form of distributed ledger technology, acts as a means of payment for cryptocurrencies. Cryptocurrencies like Bitcoin are a digital representation of value and represent the best-known use case for DLT. The regulatory and legal frameworks surrounding cryptocurrencies remain fragmented across Figure 1. Difference between centralized and distributed ledgers. countries, with some implicitly or explicitly banning them, and others allowing them. How does it work? Distributed ledgers do not need a central, trusted authority because as transactions are added, they are verified using what In addition to cryptocurrencies, there are a number of other efforts is known as a consensus protocol. Blockchain, for example, ensures the underway to make use of DLT. For example, Hyperledger Fabric is ledger is valid because each “block” of transactions is cryptographically a permissioned and private blockchain framework created by the linked to the previous block so that any change would alert all other Hyperledger consortium to help develop DLT for a variety of business users. -

Asymmetric Proof-Of-Work Based on the Generalized Birthday Problem
Equihash: Asymmetric Proof-of-Work Based on the Generalized Birthday Problem Alex Biryukov Dmitry Khovratovich University of Luxembourg University of Luxembourg [email protected] [email protected] Abstract—The proof-of-work is a central concept in modern Long before the rise of Bitcoin it was realized [20] that cryptocurrencies and denial-of-service protection tools, but the the dedicated hardware can produce a proof-of-work much requirement for fast verification so far made it an easy prey for faster and cheaper than a regular desktop or laptop. Thus the GPU-, ASIC-, and botnet-equipped users. The attempts to rely on users equipped with such hardware have an advantage over memory-intensive computations in order to remedy the disparity others, which eventually led the Bitcoin mining to concentrate between architectures have resulted in slow or broken schemes. in a few hardware farms of enormous size and high electricity In this paper we solve this open problem and show how to consumption. An advantage of the same order of magnitude construct an asymmetric proof-of-work (PoW) based on a compu- is given to “owners” of large botnets, which nowadays often tationally hard problem, which requires a lot of memory to gen- accommodate hundreds of thousands of machines. For prac- erate a proof (called ”memory-hardness” feature) but is instant tical DoS protection, this means that the early TLS puzzle to verify. Our primary proposal Equihash is a PoW based on the schemes [8], [17] are no longer effective against the most generalized birthday problem and enhanced Wagner’s algorithm powerful adversaries. -

Initial Coin Offerings: Financing Growth with Cryptocurrency Token
Initial Coin Offerings: Financing Growth with Cryptocurrency Token Sales Sabrina T. Howell, Marina Niessner, and David Yermack⇤ June 21, 2018 Abstract Initial coin offerings (ICOs) are sales of blockchain-based digital tokens associated with specific platforms or assets. Since 2014 ICOs have emerged as a new financing instrument, with some parallels to IPOs, venture capital, and pre-sale crowdfunding. We examine the relationship between issuer characteristics and measures of success, with a focus on liquidity, using 453 ICOs that collectively raise $5.7 billion. We also employ propriety transaction data in a case study of Filecoin, one of the most successful ICOs. We find that liquidity and trading volume are higher when issuers offer voluntary disclosure, credibly commit to the project, and signal quality. s s ss s ss ss ss s ⇤NYU Stern and NBER; Yale SOM; NYU Stern, ECGI and NBER. Email: [email protected]. For helpful comments, we are grateful to Bruno Biais, Darrell Duffie, seminar participants at the OECD Paris Workshop on Digital Financial Assets, Erasmus University, and the Swedish House of Finance. We thank Protocol Labs and particularly Evan Miyazono and Juan Benet for providing data. Sabrina Howell thanks the Kauffman Foundation for financial support. We are also grateful to all of our research assistants, especially Jae Hyung (Fred) Kim. Part of this paper was written while David Yermack was a visiting professor at Erasmus University Rotterdam. 1Introduction Initial coin offerings (ICOs) may be a significant innovation in entrepreneurial finance. In an ICO, a blockchain-based venture raises capital by selling cryptographically secured digital assets, usually called “tokens.” These ventures often resemble the startups that conventionally finance themselves with angel or venture capital (VC) investment, though there are many scams, jokes, and tokens that have nothing to do with a new product or business. -

Bitcoin Making Gold Redundant?
March 2021 Edition BloombergMarch 2021 GalaxyEdition Crypto Index (BGCI) Bloomberg Crypto Outlook 2021 Bloomberg Crypto Outlook Bitcoin Making Gold Redundant? `There's No Alternative' Tilting Toward Bitcoin vs. Gold, Stocks Bitcoin $40,000-$60,000 Consolidation and 60/40 Mix Migration Grayscale Bitcoin Trust Discount May Signal March to $100,000 Bitcoin Replacing Gold Is Happening -- A Question of Endurance Death, Taxes and Bitcoin Volatility Dropping Toward Gold, Amazon Worried About Bitcoin Sellers? They Appear Similar to 2017 Start 1 March 2021 Edition Bloomberg Crypto Outlook 2021 CONTENTS 3 Overview 3 60/40 Mix Migration 5 Rising Bitcoin Wave and GBTC 5 Bitcoin Is Replacing Gold 6 Bitcoin Volatity In Decline 7 Diminishing Bitcon Supply, Reluctant Sellers 2 March 2021 Edition Bloomberg Crypto Outlook 2021 Learn more about Bloomberg Indices Most data and outlook as of March 2, 2021 Mike McGlone – BI Senior Commodity Strategist BI COMD (the commodity dashboard) Note ‐ Click on graphics to get to the Bloomberg terminal `There's No Alternative' Tilting Toward Bitcoin vs. Gold, Stocks $100,000 May Be Bitcoin's Next Threshold. Maturation makes sense in the Bitcoin price-discovery process, but we see the upward trajectory more likely to simply stay the Performance: Bloomberg Galaxy Cypto Index (BGCI) course on rising demand vs. declining supply and an February +24%, 2021 to March 2: +77% increasingly favorable macroeconomic environment. Having February +40%, 2021 +64% Bitcoin met the initial 2021 threshold just above $50,000 and a $1 trillion market cap, the benchmark crypto asset is ripe to (Bloomberg Intelligence) -- Bitcoin in 2021 is transitioning stabilize for awhile, with $40,000 marking initial retracement from a speculative risk asset to a global digital store-of-value, support. -
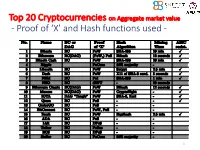
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5.