Research and Applied Perspective to Blockchain Technology: a Comprehensive Survey
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

YEUNG-DOCUMENT-2019.Pdf (478.1Kb)
Useful Computation on the Block Chain The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Yeung, Fuk. 2019. Useful Computation on the Block Chain. Master's thesis, Harvard Extension School. Citable link https://nrs.harvard.edu/URN-3:HUL.INSTREPOS:37364565 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA 111 Useful Computation on the Block Chain Fuk Yeung A Thesis in the Field of Information Technology for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2019 Copyright 2019 [Fuk Yeung] Abstract The recent growth of blockchain technology and its usage has increased the size of cryptocurrency networks. However, this increase has come at the cost of high energy consumption due to the processing power needed to maintain large cryptocurrency networks. In the largest networks, this processing power is attributed to wasted computations centered around solving a Proof of Work algorithm. There have been several attempts to address this problem and it is an area of continuing improvement. We will present a summary of proposed solutions as well as an in-depth look at a promising alternative algorithm known as Proof of Useful Work. This solution will redirect wasted computation towards useful work. We will show that this is a viable alternative to Proof of Work. Dedication Thank you to everyone who has supported me throughout the process of writing this piece. -

Blockchain Healthcare & Policy Synopsis
Blockchain Healthcare & Policy Synopsis AN EXECUTIVE REPORT OF THE U.S. DEPARTMENT OF HEALTH AND HUMAN SERVICES & NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY’S BLOCKCHAIN CHALLENGE October 2016 digitalchamber.org Table of Contents PART I: Blockchain in Healthcare and Research Workshop | 3 | I. Overview & Key Takeaways | 3 | II. Introduction: The White House II.I. Tim Polk, The White House, Office of Science and Technology Policy | 4 | III. Blockchain Level Setting III.I. John Kelsey, National Institute of Standards and Technology | 4 | III.II. Lily Chen, National Institute of Standards and Technology | 5 | IV. Blockchain Reality Check - Alternative IV.I. Evaluating Blockchain and Alternatives: Mance Harmon, Ping Identity | 5 | IV.II. Blockchain Challenges in Real Life: Stephen Wilson, Constellation Research | 6 | IV.III. “Fit for Purpose” Distributed Ledger Technology: Drummond Reed, Respect Network | 6 | V. Blockchain Reality Check - Challenges V.I. DHS Identity Innovations Grants: Many Sporny, Digital Bazaar | 7 | V.II. IoT Device Identity: Tiana Laurence and Andrew Yashchuk, Factom IRIS | 7 | V.III. Decentralized Identifiers (DIDs): Solving the Root Identity Problem, Drummond Reed, Respect Network | 7 | V.IV. Decentralized Certification Service, Adam Migus, XCELERATE Solutions | 8 | VI. Blockchain Challenge Presentations VI.I. Blockchain: The Chain of Trust and its Potential to Transform Healthcare – IBM’s Point of View Srini Attili and Shahram Ebdollahi, IBM Global Business Service Public Sector | 8 | VI.II. Blockchain: Securing -

Chancen Und Herausforderungen Von DLT (Blockchain) in Mobilität Und Logistik
Chancen und Herausforderungen von DLT (Blockchain) in Mobilität und Logistik FRAUNHOFER-INSTITUT FÜR ANGEWANDTE INFORMATIONSTECHNIK FIT CHANCEN UND HERAUSFORDERUNGEN VON DLT (BLOCKCHAIN) IN MOBILITÄT UND LOGISTIK Prof. Dr. Gilbert Fridgen Prof. Dr. Nikolas Guggenberger Prof. Dr. Thomas Hoeren Prof. Wolfgang Prinz (PhD) Prof. Dr. Nils Urbach Johannes Baur, Henning Brockmeyer, Wolfgang Gräther, Elisaweta Rabovskaja, Vincent Schlatt, André Schweizer, Johannes Sedlmeir, Lars Wederhake Vielen Dank den weiteren Mitwirkenden: Matthias Babel, Martin Brennecke, Patrick Camus, Benedict Drasch, Tobias Guggenberger, Luis Lämmermann, Jannik Lockl, Sven Radszuwill, Alexander Rieger, Marco Schmidt, Nico Thanner, Patrick Troglauer, Florian Vogt, Malte Weißert, Felix Würmseher Inhalt 1 Management Summary .......................................................................................................... 1 1.1 Zielsetzung des Gutachtens ..............................................................................................................1 1.2 Allgemeine Analyse..........................................................................................................................2 1.2.1 Technische Betrachtung ...................................................................................................................................... 2 1.2.2 Gesellschaftlich-ökonomische Perspektive ......................................................................................................... 3 1.2.2.1 Status quo ...................................................................................................................................................... -

User Manual Ledger Nano S
User Manual Ledger Nano S Version control 4 Check if device is genuine 6 Buy from an official Ledger reseller 6 Check the box contents 6 Check the Recovery sheet came blank 7 Check the device is not preconfigured 8 Check authenticity with Ledger applications 9 Summary 9 Learn more 9 Initialize your device 10 Before you start 10 Start initialization 10 Choose a PIN code 10 Save your recovery phrase 11 Next steps 11 Update the Ledger Nano S firmware 12 Before you start 12 Step by step instructions 12 Restore a configuration 18 Before you start 19 Start restoration 19 Choose a PIN code 19 Enter recovery phrase 20 If your recovery phrase is not valid 20 Next steps 21 Optimize your account security 21 Secure your PIN code 21 Secure your 24-word recovery phrase 21 Learn more 22 Discover our security layers 22 Send and receive crypto assets 24 List of supported applications 26 Applications on your Nano S 26 Ledger Applications on your computer 27 Third-Party applications on your computer 27 If a transaction has two outputs 29 Receive mining proceeds 29 Receiving a large amount of small transactions is troublesome 29 In case you received a large amount of small payments 30 Prevent problems by batching small transactions 30 Set up and use Electrum 30 Set up your device with EtherDelta 34 Connect with Radar Relay 36 Check the firmware version 37 A new Ledger Nano S 37 A Ledger Nano S in use 38 Update the firmware 38 Change the PIN code 39 Hide accounts with a passphrase 40 Advanced Passphrase options 42 How to best use the passphrase feature 43 -

2016-05-31 Overview of Swirlds Hashgraph
Overview of Swirlds Hashgraph Leemon Baird [email protected] May 31, 2016 The hashgraph data structure and Swirlds consensus algorithm provide a new platform for distributed consensus. This paper gives an overview of some of its properties, and comparisons with the Bitcoin blockchain. In this paper, the term “blockchain” will generally refer to the system used in Bitcoin, rather than the large number of variants that have been proposed. The goal of a distributed consensus algorithm is to allow a community of users to come to an agreement on the order in which some of them generated transactions, when no single member is trusted by everyone. In this way, it is a system for generating trust, when individuals do not already trust each other. The Swirlds hashgraph system achieves this along with being fair, fast, provable, Byzantine, ACID compliant, efficient, inexpensive, timestamped, DoS resistant, and optionally non-permissioned. This is what those terms mean: The hashgraph is fair, because no individual can manipulate the order of the transactions. For example, imagine a stock market, where Alice and Bob both try to buy the last available share of a stock at the same moment for the same price. In blockchain, a miner might put both those transactions in a single block, and have complete freedom to choose what order they occur. Or the miner might choose to only include Alice’s transaction, and delay Bob’s to some future block. In the hashgraph, there is no way for an individual to affect the consensus order of those transactions. The best Alice can do is to invest in a better internet connection so that her transaction reaches everyone before Bob’s. -

The Performance, Interoperability and Integration of Distributed Ledger Technologies
LICENTIATE T H E SIS Emanuel Palm Palm Emanuel Department of Computer Science and Electrical Engineering Division of EISLAB The Performance, Interoperability ISSN 1402-1757 The Performance, Interoperability and Integration of Distributed Ledger Technologies and Integration Interoperability of Distributed Ledger The Performance, and Integration of ISBN 978-91-7790-402-1 (print) ISBN 978-91-7790-403-8 (pdf) Luleå University of Technology 2019 Distributed Ledger Technologies Emanuel Palm Industrial Electronics The Performance, Interoperability and Integration of Distributed Ledger Technologies EmanuelK.Palm Dept. of Computer Science and Electrical Engineering Lule˚a University of Technology Lule˚a, Sweden Supervisors: Ulf Bodin, Olov Schel´en and Jerker Delsing Printed by Luleå University of Technology, Graphic Production 2019 ISSN 1402-1757 ISBN 978-91-7790-402-1 (print) ISBN 978-91-7790-403-8 (pdf) Luleå 2019 www.ltu.se To my beloved wife, Sofia. iii iv Abstract In the wake of the financial crisis of 2008, Bitcoin emerged as a radical new alternative to the fiat currencies of the traditional banking sector. Through the use of a novel kind of probabilistic consensus algorithm, Bitcoin proved it possible to guarantee the integrity of a digital currency by relying on network majority votes instead of trusted institutions. By showing that it was technically feasible to, at least to some extent, replace the entire banking sector with computers, many significant actors started asking what else this new technology could help automate. A subsequent, seemingly inevitable, wave of efforts produced a multitude of new distributed ledger systems, architectures and applications, all somehow attempting to leverage distributed consensus algorithms to replace trusted intermediaries, facilitating value ownership, transfer and regulation. -
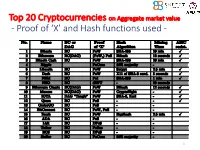
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Artificial Intelligence Integrated Blockchain Technology for Decentralized Applications and Smart Contracts
International Journal of Advanced Science and Technology Vol. 29, No.02, (2020), pp. 1023-1031 Artificial Intelligence Integrated Blockchain Technology for Decentralized Applications and Smart Contracts MAAN NAWAF ABBOOD Al-Imam Al-Adham college Abstract In the present period, Blockchain Technology is one of the key regions of research just as execution explicitly in the space of Cryptocurrency. Presently days, various advanced digital forms of money are very conspicuous and shared all through the world in spite of enormous analysis and debates. These cryptographic forms of money incorporate BitCoin, Ethereum, LiteCoin, PeerCoin, GridCoin, PrimeCoin, Ripple, Nxt, DogeCoin, NameCoin, AuroraCoin, Dash, Neo, NEM, PotCoin, TitCoin, Verge, Stellar, VertCoin, Tether, Zcash and numerous others. These blockchain based digital forms of money don't have any middle of the road bank or installment passage to record the log of the transactions. That is the primary reason in light of which numerous nations are not permitting the cryptographic forms of money as legitimate cash transaction. In any case, these blockchain based cryptographic forms of money are extremely celebrated and utilized as a result of colossal security highlights. This manuscript is focusing on the blockchain technology that is directly associated as the application domain of artificial intelligence. Keywords: Artificial Intelligence, AI, AI based Blockchain, Blockchain Security Introduction The blockchain organize is having a square of records in which every single record is related with the dynamic cryptography so every one of the transactions can be scrambled with no likelihood of sniffing or hacking endeavors [1, 2]. In current situation, the blockchain innovation is progressively engaged towards cryptographic forms of money in which the disseminated record is kept up for the transactions [3, 4]. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Performance-Based Analysis of Blockchain Scalability Metric
ISSN 1846-6168 (Print), ISSN 1848-5588 (Online) Subject review https://doi.org/10.31803/tg-20210205103310 Performance-Based Analysis of Blockchain Scalability Metric Jyoti Yadav*, Ranjana Shevkar Abstract: Cryptocurrencies like Bitcoin and Ethereum, are widely known applications of blockchain technology, have drawn much attention and are largely recognized in recent years. Initially Bitcoin and Ethereum processed 7 and 15 Transactions Per Second (TPS) respectively, whereas VISA and Paypal process 1700 and 193 TPS respectively. The biggest challenge to blockchain adoption is scalability, defined as the capacity to change the block size to handle the growing amount of load. This paper attempts to present the existing scalability solutions which are broadly classified into three layers: Layer 0 solutions focus on optimization of propagation protocol for transactions and blocks, Layer 1 solutions are based on the consensus algorithms and data structure, and Layer 2 solutions aims to decrease the load of the primary chain by implementing solutions outside the chain. We present a classification and comparison of existing blockchain scalability solutions based on performance along with their pros and cons. Keywords: consensus; decentralization; latency; scalability; security; throughput 1 INTRODUCTION sectors such as health care, media, logistics, supply chain management, power and utilities, Government, property, E- Blockchain is a decentralized, distributed, immutable voting etc. Apart from attractive features and interesting ledger with a sequence of blocks interlinked and secured applications, the most challenging task of blockchain is its using cryptography. Block is a basic unit of blockchain that scalability. bundles a set of transactions initiated by participating nodes This paper attempts to classify and compare existing in the blockchain network. -

Impossibility of Full Decentralization in Permissionless Blockchains
Impossibility of Full Decentralization in Permissionless Blockchains Yujin Kwon*, Jian Liuy, Minjeong Kim*, Dawn Songy, Yongdae Kim* *KAIST {dbwls8724,mjkim9394,yongdaek}@kaist.ac.kr yUC Berkeley [email protected],[email protected] ABSTRACT between achieving good decentralization in the consensus protocol Bitcoin uses the proof-of-work (PoW) mechanism where nodes earn and not relying on a TTP exists. rewards in return for the use of their computing resources. Although this incentive system has attracted many participants, power has, CCS CONCEPTS at the same time, been significantly biased towards a few nodes, • Security and privacy → Economics of security and privacy; called mining pools. In addition, poor decentralization appears not Distributed systems security; only in PoW-based coins but also in coins that adopt proof-of-stake (PoS) and delegated proof-of-stake (DPoS) mechanisms. KEYWORDS In this paper, we address the issue of centralization in the consen- Blockchain; Consensus Protocol; Decentralization sus protocol. To this end, we first define ¹m; ε; δº-decentralization as a state satisfying that 1) there are at least m participants running 1 INTRODUCTION a node, and 2) the ratio between the total resource power of nodes Traditional currencies have a centralized structure, and thus there run by the richest and the δ-th percentile participants is less than exist several problems such as a single point of failure and corrup- or equal to 1 + ε. Therefore, when m is sufficiently large, and ε and tion. For example, the global financial crisis in 2008 was aggravated δ are 0, ¹m; ε; δº-decentralization represents full decentralization, by the flawed policies of banks that eventually led to many bank which is an ideal state. -
![Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction](https://docslib.b-cdn.net/cover/6379/arxiv-1907-02434v1-cs-cy-4-jul-2019-1-introduction-716379.webp)
Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction
Cryptocurrency Egalitarianism: A Quantitative Approach Dimitris Karakostas1,3, Aggelos Kiayias1,3, Christos Nasikas2,4, and Dionysis Zindros2,3 1 University of Edinburgh 2 University of Athens 3 IOHK 4 “ATHENA” Research Center Abstract. Since the invention of Bitcoin one decade ago, numerous cryptocurrencies have sprung into existence. Among these, proof-of-work is the most common mechanism for achieving consensus, whilst a num- ber of coins have adopted “ASIC-resistance” as a desirable property, claiming to be more “egalitarian,” where egalitarianism refers to the power of each coin to participate in the creation of new coins. While proof-of-work consensus dominates the space, several new cryptocurren- cies employ alternative consensus, such as proof-of-stake in which block minting opportunities are based on monetary ownership. A core criti- cism of proof-of-stake revolves around it being less egalitarian by making the rich richer, as opposed to proof-of-work in which everyone can con- tribute equally according to their computational power. In this paper, we give the first quantitative definition of a cryptocurrency’s egalitarian- ism. Based on our definition, we measure the egalitarianism of popular cryptocurrencies that (may or may not) employ ASIC-resistance, among them Bitcoin, Ethereum, Litecoin, and Monero. Our simulations show, as expected, that ASIC-resistance increases a cryptocurrency’s egalitar- ianism. We also measure the egalitarianism of a stake-based protocol, Ouroboros, and a hybrid proof-of-stake/proof-of-work cryptocurrency, Decred. We show that stake-based cryptocurrencies, under correctly se- lected parameters, can be perfectly egalitarian, perhaps contradicting folklore belief. arXiv:1907.02434v1 [cs.CY] 4 Jul 2019 1 Introduction In 2008, Satoshi Nakamoto proposed Bitcoin [25], the first and most suc- cessful cryptocurrency to date.