International Journal of Soft Computing and Engineering
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

The Republic of the Sudan Jamhuryat Es-Sudan Constitution and Government
1444 THE SUDAN THE REPUBLIC OF THE SUDAN JAMHURYAT ES-SUDAN CONSTITUTION AND GOVERNMENT. The Sudan was proelaimed a sovereign independent republic on 1 Jan.. 1956. On 19 Dee. 1955 the Sudanese parliament passed unanimously a declaration tbat a fully inde· pendent state sbould be set up fortbwitb, and tbat a Couneil of State of 5 sbould temporarily assume tbe duties of Read of State. The Co-domini, tbe UK and Egypt, gave their assent on 31 Dee. 1955. For tbe history of tbe Condominium and the steps leading to independence, see 'l'HE STATESMAN'S YEAR-BooK, 1955, pp. 340-41. Nationalflag: Blue, yellow, green (horizontal). On 17 Nov. 1958 tbe Army took over the government. Tbe Couneil of State and the cabinet were dismissed, parliament and all poiitical parties were declared dissolved, and the provisional eonstitution was suspended. The supreme authority was vested in the Supreme Couneil of the Armed Forees under Lieut.-Gen. Ibrahim Abboud. On 25 Oet. 1964 President Abboud dissolved the Supreme Couneil and dismissed the Cabinet. On 30 Oet. President Abboud appointed a civilian Oabinet witb Ser al-Khatm Khalifa as Prime Minister. On 15 Nov. 1964 President Abboud resigned as chief oi' state and supreme eommander. In eonformity with the provisional eonstitution of 1956 a 5-member Oouncil of Sovereignty replaced the presidency. On 8 July 1965 the Oonstituent Assembly elected Ismail EI-Azhari as President of the Supreme Council; its otber member" are Abdel Rahman Abdoun, Felman Majok, Khidir Ramad and Abdullah Alfadil EI-Mahdi. Prime Minister: Sadik ei-Mahdi, Foreign Affairs and Justice: Mohamed Ibrahim Khalil. -

Regional Directoiy of Environmental Resource Persons and Research in West a Sill
Regional Office for West Asia (ROWA) Regional Directoiy of Environmental Resource Persons and Research in West A Sill '994 CrnpiIed in the Regional Office of West Asia P.O.Box 1088() TJanama, State of Bahrwn Regional Office for West Asia (ROWA) Regional Directory of Environmental Resource Persons and Research in West Asia 1994 C- Compiled in the Regional Office of West Asia P.O. Box 10880 Mananw, State of Bahrain Contents I - Experts Information Sorted According to Countries .................... 1 1.JORDAN ......................................................................................... i 2. EMIRATES ..................................................................................... 11 3.BAIIRAIN ....................................................................................... 16 SAUDI ARABIA ............................................................................. 23 SYRIA .............................................................................................. 33 IRAQ .................................................................................. .............40 OMAN ............................................................................................43 8.PALESTINE ................................................................................... 44 QATAR ............................................................................................ 45 KUWAIT ........................................................................................ 50 LEBANON....................................................................................54 -

United Nations Economic and Social Council LIST of PARTICIPANTS
United Nations E/CN.15/2011/INF/2/Rev.1 Economic and Social Council Distr. Limited 26 April 2011 Original: English, French, Spanish COMMISSION ON CRIME PREVENTION AND CRIMINAL JUSTICE Twentieth session Vienna, 11 to 15 April 2011 LIST OF PARTICIPANTS States members of the Commission on Crime Prevention and Criminal Justice ALGERIA Taous FEROUKHI, Ambassadeur, Représentant Permanent, Mission Permanente auprès des Nations Unies, Vienne Mokhtar LAKHDARI, Directeur des Affaires Pénales et des Grâces, Ministère de la Justice Nabil HATTALI, Chargé de Mission Zohra ZERERA, Conseiller, Mission Permanente auprès des Nations Unies, Vienne Baziz LARRAS, Chef de Bureau, Direction Générale de la Sûreté Nationale Mélissa LAKEHAL, Chef de Bureau, Ministère des Affaires Etrangères ANGOLA Pascoal António JOAQUIM, Deputy Attorney General Fidelino Loy de Jesus FIGUEIREDO, Ambassador, Permanent Representative, Permanent Mission to the United Nations, Vienna Jacinto Rangel Lopes CORDEIRO NETO, Minister Counsellor, Advisor to the Permanent Representative, Permanent Mission to the United Nations, Vienna Kuku Elizabeth DAVID, Deputy Provincial Attorney Dulce GOMES, First Secretary, Division for International Organizations, Ministry of Foreign Affairs Efigénia Perpétua dos Prazeres JORGE, Third Secretary, Advisor to the Permanent Representative, Permanent Mission to the United Nations, Vienna V.11-83007 (E) *1183007* E/CN.15/2011/INF/2/Rev.1 Antónia Osvaldina SIMÃO DA CRUZ, Technician, Legal Department, Ministry of Justice Adriano RAMOS, Legal Advisor, Office -

Tahiyyat.Pdf
Николай Николаевич Дьяков Saint Petersburg State University Faculty of Asian and African studies TAHIYYAT Festschrift in Honour of Professor Nikolay Dyakov Middle Eastern and Islamic Studies Saint Petersburg 2013 Санкт-Петербургский государственный университет Восточный факультет ТАХИЙЙАТ Сборник статей в честь профессора Н. Н. Дьякова Арабистика — Исламоведение — Этнография Санкт-Петербург 2013 УДК 81'22 ББК 81.2 Т24 Составители: И. В. Герасимов, А. С. Матвеев Издание осуществлено при поддержке Фонда Марджани Т24 «Тахиййат»: Сборник статей в честь Н. Н. Дьякова. Арабистика — Исламоведение — Этнография / Составители: И. В. Герасимов, А. С. Матвеев. — СПб.: ВФ СПбГУ, 2013. — 347 с. ISBN 978-5-4391-0059-0 Сборник статей в честь доктора исторических наук, профессо- ра Николая Николаевича Дьякова, уже почти четверть века воз- главляющего кафедру истории стран Ближнего Востока Вос- точного факультета СПбГУ, приурочен к шестидесятилетию ученого. В сборнике приняли участие специалисты по Ближне- му Востоку и исламоведению из России, Азербайджана, Египта, Греции, Великобритании, Норвегии, США. Широкий круг научных интересов и академических контак- тов юбиляра определяет и круг авторов сборника, и широ- ту тем и проблематики статей, охватывающих самые разные аспекты ближневосточных и исламоведческих исследований. В сборнике рассматриваются проблемы бытования ислама на Ближнем Востоке и за его пределами, истории христиано- мусульманских отношений, арабской этнографии, философии и филологии, военного дела средневекового Востока и другие вопросы истории -

Reproductions Supplied by EDRS Are the Best That Can Be Made from the Original Document
DOCUMENT RESUME ED 369 549 PS 022 317 TITLE Directory of Child-to-Child Activities Worldwide. INSTITUTION Child-to-Child Trust, London (England). Inst. of Education. PUB DATE Jun 93 NOTE 69p. PUB TYPE Reports Descriptive (141) Reference Materials Directories/Catalogs (132) EDRS PRICE MF01/PC03 Plus Postage. DESCRIPTORS *Child Health; Children; *Health Education; *Health Promotion; International Programs; Learning Activities; Program Descriptions IDENTIFIERS *Child to Child Program ABSTRACT Child-to-Child ideas and activities represent an approach to health education. Not an alternative programbut instead a component of other programs,Child-to-Child emphasizes the role of children as partners within families and communities inpromoting better health practices and promotes Child-to-Childactivities. This booklet describes approximately 200 knownChild-to-Child activities in over 70 countries and lists European and NorthAmerican-based partners in the promotion of internationalChild-to-Child activities. Over 30 projects are described in greater detail in orderto give examples of the range of different activities. There are seven sections in the book. The first section discusses theChild-to-Child idea and its implementation. The second section listsdifferent activities grouped in the following three categories:Child-to-Child materials as a resource for health education;Child-to-Child approaches within the formal education system; andChild-to-Child action organized outside formal education. Thethird section lists Child-to-Child activities by country. The fourth sectionlists the European and North American-based partners in thepromotion of international Child-to-Child activities. Expanded profilesof 32 selected Child-to-Child programs and projects areincluded in the fifth section. The sixth and seventh sections listChild-to-Child publications available from TALC (Teaching-Aids at LowCost) and various other sources. -

African Nationals in Allsvenskan, 1977– 2010
APPENDIX A African Nationals in Allsvenskan, 1977– 2010 African nationality and/or African place of birth Name Club and season in Allsvenskan (appearances/goals) Position Previous club/country prior to Allsvenskan / Subsequent club/country after Allsvenskan Algeria Samir Beloufa 2007– 2008 Helsingborgs IF 15/1 Defender K.V.C. Westerlo (Belgium First Division 2006) / Royal Olympic Club de Charleroi- Marchienne (Belgium Third Division 2010) Angola João Yamba Asha (alternatively Yamba Asha João) 2006 Östers IF 4/0 Defender Atlético Sport Aviação (Angola First Division 2005) / Petro Atlético Luanda (Angola First Division 2007) Paulo José Lopes de Figueiredo 2006 Östers IF 13/1 Midfielder Varzim SC (Portugal Second Division 2005) / FC Ceahlău (Romania Second Divi- sion 2007) Benin Razak Omotoyossi 2007– 2008 Helsingborgs IF 33/16 Forward 154 O Appendix A FC Sheriff Tiraspol (Moldova First Division 2007) / Al-Nassr FC (Saudi Arabia First Division 2008) Cameroon Eric Magloire Bassombeng 2008– 2010 Örebro SK 35/5 Midfielder Les Astres FC (Cameroon First Division 2007) Joseph Elanga 2001– 2005, 2010 Malmö FF 131/5 Defender Apollon Limassol (Cyprus First Division 2000) / Brøndby IF (Denmark First Divi- sion 2005) AC Horsens (Denmark First Division 2009 on loan from Brøndby IF) Patrice Kwedi 2004 IFK Göteborg 3/0 Defender NK Pomorac Kostrena (Croatia First Division 2003) / AGF Aarhus (Denmark First Division 2005) Bertin Samuel Zé Ndille 2008– 2010 Örebro SK 17/0 Defender Canon Sportif de Yaoundé (Cameroon First Division 2007) Joseph Nguijol 2005 Gefle IF 2/0 Midfielder AV.S. Frontignan A.C. (France Third Division 2004) / Carlstad United (Sweden Second Division 2006) Cape Verde Mateus Lopes 2005 Assyriska FF 4/0 Forward Portimonense S.C. -

Conference Program
Conference Program March 27-29, 2018 Kyoto, Japan ACEAIT Annual Conference on Engineering and Information Technology APLSBE Asia-Pacific Conference on Life Science and Biological Engineering ICBASS International Conference on Business and Social Science ACEAIT Annual Conference on Engineering and Information Technology ISBN: 978-986-89298-6-9 APLSBE Asia-Pacific Conference on Life Science and Biological Engineering ISBN: 978-986-5654-49-8 ICBASS International Conference on Business and Social Science ISBN: 978-986-89298-7-6 Content General Information for Participants .................................................................................. 3 International Committees ...................................................................................................... 5 International Committees ...................................................................................................... 9 Special Thanks to Session Chairs ....................................................................................... 13 Conference Venue Information ........................................................................................... 14 Kyoto Research Park ........................................................................................................... 17 Conference Schedule ............................................................................................................ 18 Natural Sciences Keynote Speech (1) ................................................................................. 22 Natural -

Abstarct Book IJEAT V4i5 Jun
Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. Deepak Garg Professor, Department of Computer Science and Engineering, Thapar University, Patiala (Punjab), India, Senior Member of IEEE, Secretary of IEEE Computer Society (Delhi Section), Life Member of Computer Society of India (CSI), Indian Society of Technical Education (ISTE), Indian Science Congress Association Kolkata. Dr. Vijay Anant Athavale Director of SVS Group of Institutions, Mawana, Meerut (U.P.) India/ U.P. Technical University, India Dr. T.C. Manjunath Principal & Professor, HKBK College of Engg, Nagawara, Arabic College Road, Bengaluru-560045, Karnataka, India Dr. Kosta Yogeshwar Prasad Director, Technical Campus, Marwadi Education Foundation’s Group of Institutions, Rajkot-Morbi Highway, Gauridad, Rajkot, Gujarat, India Dr. -

Abstarct Book IJEAT V5i1 Octo
Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. Deepak Garg Professor, Department of Computer Science and Engineering, Thapar University, Patiala (Punjab), India, Senior Member of IEEE, Secretary of IEEE Computer Society (Delhi Section), Life Member of Computer Society of India (CSI), Indian Society of Technical Education (ISTE), Indian Science Congress Association Kolkata. Dr. Vijay Anant Athavale Director of SVS Group of Institutions, Mawana, Meerut (U.P.) India/ U.P. Technical University, India Dr. T.C. Manjunath Principal & Professor, HKBK College of Engg, Nagawara, Arabic College Road, Bengaluru-560045, Karnataka, India Dr. Kosta Yogeshwar Prasad Director, Technical Campus, Marwadi Education Foundation’s Group of Institutions, Rajkot-Morbi Highway, Gauridad, Rajkot, Gujarat, India Dr. -
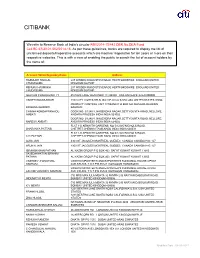
Details of Unclaimed Deposits / Inoperative Accounts
CITIBANK We refer to Reserve Bank of India’s circular RBI/2014-15/442 DBR.No.DEA Fund Cell.BC.67/30.01.002/2014-15. As per these guidelines, banks are required to display the list of unclaimed deposits/inoperative accounts which are inactive/ inoperative for ten years or more on their respective websites. This is with a view of enabling the public to search the list of account holders by the name of: Account Holder/Signatory Name Address HASMUKH HARILAL 207 WISDEN ROAD STEVENAGE HERTFORDSHIRE ENGLAND UNITED CHUDASAMA KINGDOM SG15NP RENUKA HASMUKH 207 WISDEN ROAD STEVENAGE HERTFORDSHIRE ENGLAND UNITED CHUDASAMA KINGDOM SG15NP GAUTAM CHAKRAVARTTY 45 PARK LANE WESTPORT CT.06880 USA UNITED STATES 000000 VAIDEHI MAJMUNDAR 1109 CITY LIGHTS DR ALISO VIEJO CA 92656 USA UNITED STATES 92656 PRODUCT CONTROL UNIT CITIBANK P O BOX 548 MANAMA BAHRAIN KRISHNA GUDDETI BAHRAIN CHINNA KONDAPPANAIDU DOOR NO: 3/1240/1, NAGENDRA NAGAR,SETTYGUNTA ROAD, NELLORE, AMBATI ANDHRA PRADESH INDIA INDIA 524002 DOOR NO: 3/1240/1, NAGENDRA NAGAR,SETTYGUNTA ROAD, NELLORE, NARESH AMBATI ANDHRA PRADESH INDIA INDIA 524002 FLAT 1-D,KENWITH GARDENS, NO 5/12,MC'NICHOLS ROAD, SHARANYA PATTABI CHETPET,CHENNAI TAMILNADU INDIA INDIA 600031 FLAT 1-D,KENWITH GARDENS, NO 5/12,MC'NICHOLS ROAD, C D PATTABI . CHETPET,CHENNAI TAMILNADU INDIA INDIA 600031 ALKA JAIN 4303 ST.JACQUES MONTREAL QUEBEC CANADA CANADA H4C 1J7 ARUN K JAIN 4303 ST.JACQUES MONTREAL QUEBEC CANADA CANADA H4C 1J7 IBRAHIM KHAN PATHAN AL KAZMI GROUP P O BOX 403 SAFAT KUWAIT KUWAIT 13005 SAJEDAKHATUN IBRAHIM PATHAN AL KAZMI -

Official Gazettb
llm'*$ THE OFFICIAL GAZETTB I OF THB COLONY AI\D PROTECTORATB OF ! KENYA Published under the Authority of rlis Excelency thc Governor of tte Colony and protectoratc of Kenya Vol. XLI-No. 12 NAIROBI, March 14, lg3g Price 50 Cents fcd.brd el e Ncrrprpcr et thc G.p.O. Publl&d cvcry ltcrdey TABLE OF CONTENTS Govt.NoticeNo. r76-Bill-for. introduction inlo^-Legisrative PAGE -.:--- council_A--'- Bill to Amend thc Miuing Ordinance, 1933 . _ __ .:. 275 ,, ,, ,, L77-Arrivals, Departures, Appointments, etc. Proclamations 293 Nos. 26-7--The Diseases of Animals Ordinance 294 Govt. Notice No. 178-The Income Tax Ordinance, !93l_Appointments 294 ,, ,, ,, 179-The Shop Hours Ordinance, 1925 295 ,, l8G-The Native Christian Marriage and Divorce Ordinance, mcnts .. l93l-Appoint- ,, t . IEI-The Liquor Ordinance-Appointments 295 . - 295 Govt. NoticesNos. r82-3-The Townships ordinance, r930-Appointments 295 Govt. NoticcNo. 184-The Game Ordinance, l937_Appointmeni .. 295 Govt. Notices Nos. I 85-9-The courts ordinance, I 93 l-Appointments 296 I Govt. Noticc No' l9G-The King's African Rifles Reserve Forces ordinance 296 Govt, Noticcs Nos. r9t-2-The Farmers Assistance ordinance, r936-stay order, etc. 297 Govt. Notice No. 193-The Transport Licensing ordinance, r937-Appointment . 297 ,, ,, 194-The Crop production ,, and Live Stock Ordinance, 1926 297 ,' 195-The Resident Native Labourers ', " ordinance, I925-Appointment 297 General Noticcs Nos. 372-425 297 SUPPLEMENT Kpxya Pnoclau,rrtons, Rules ANp Reour,erroNs, No. 12 I 274 THE OFFICIAL GAZETTE Irlarch 11, 1939 The definitions of "Native Lands Trust Board" and "Native Reserve" in section 2 of. the Principal Ordinance which it is proposed to rePlace : - 2. -
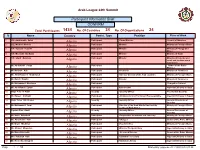
Participant Information Brief CONFIRM
Arab League 24th Summit Participant Information Brief CONFIRM Total Participants 1434 No. Of Countries 34 No. Of Organizations 24 S Name Country Partici. Type Position Place of Work 1 H.E. Abdelmalek Sellal Algeria Participant -Prime Minister Council of Ministers 2 H.E. Mourad Medelci Algeria Participant Minister Ministry of Foreign Affairs 3 H.E. Youssef Youssfi Participant Minister Ministry of Energy and Algeria Mines 4 H.E. Moustafa Bin Bada Algeria Participant Minister Ministry of Trade 5 H.E. Sharif Rahmani Participant Minister Ministry of Industry and Algeria small and medium-sized enterprises 6 Mr. Abdulkadir Perga Participant - Tasked to the Prime Algeria Minister 7 Mr. Radwan Alili Algeria Participant Counselor Ministry of Commerce 8 Mr. Abdelhameed Shabshoub Algeria Participant -Director-General of the Arab countries Ministry of Foreign Affairs 9 Mr. Mehdi Thaalbi Algeria Participant Director Ministry of Commerce 10 Mr. Mohammad Morzkane Algeria Participant - Charged in Protocol 11 Mr. Abdelfattah Ziyani Algeria Participant Ambassador Algerian Embassy in Qatar 12 Major Adel Al Arabi Algeria Security -Security Officer Presidential Security 13 Mr. Nazeer Alarbawi Algeria Participant -Ambassador and Permanent Representative Algerian Embassy in Egypt 14 Major Tahar Bin Khaled Security -Security Officer General Directorate of Algeria Security 15 Mr. Mohammad Yarqi Participant -Director of the Arab Middle East and the Ministry of Foreign Affairs Algeria League of Arab States 16 Captain Riad Khalfi Security -Security Officer General Directorate of Algeria Security 17 Mr. Saed Belaabed Algeria Participant -Responsible for studies and summary Ministry of Foreign Affairs 18 Mr. Abdelkarim Yahi Algeria Participant -Charged Dewan of the Prime Minister 19 Mr.