The Syntax of Phonology a Radically Substance-Free Approach Sylvia Blaho
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using 'North Wind and the Sun' Texts to Sample Phoneme Inventories
Blowing in the wind: Using ‘North Wind and the Sun’ texts to sample phoneme inventories Louise Baird ARC Centre of Excellence for the Dynamics of Language, The Australian National University [email protected] Nicholas Evans ARC Centre of Excellence for the Dynamics of Language, The Australian National University [email protected] Simon J. Greenhill ARC Centre of Excellence for the Dynamics of Language, The Australian National University & Department of Linguistic and Cultural Evolution, Max Planck Institute for the Science of Human History [email protected] Language documentation faces a persistent and pervasive problem: How much material is enough to represent a language fully? How much text would we need to sample the full phoneme inventory of a language? In the phonetic/phonemic domain, what proportion of the phoneme inventory can we expect to sample in a text of a given length? Answering these questions in a quantifiable way is tricky, but asking them is necessary. The cumulative col- lection of Illustrative Texts published in the Illustration series in this journal over more than four decades (mostly renditions of the ‘North Wind and the Sun’) gives us an ideal dataset for pursuing these questions. Here we investigate a tractable subset of the above questions, namely: What proportion of a language’s phoneme inventory do these texts enable us to recover, in the minimal sense of having at least one allophone of each phoneme? We find that, even with this low bar, only three languages (Modern Greek, Shipibo and the Treger dialect of Breton) attest all phonemes in these texts. -

Grapheme-To-Phoneme Transcription in Hungarian
International Journal of Computational Linguistics and Applications vol. 7, no. 1, 2016, pp. 161–173 Received 08/02/2016, accepted 07/03/2016, final 20/06/2016 ISSN 0976-0962, http://ijcla.bahripublications.com Grapheme-to-Phoneme Transcription in Hungarian ATTILA NOVÁK1 AND BORBÁLA SIKLÓSI2 1 MTA-PPKE Hungarian Language Technology Research Group, Hungary 2 Pázmány Péter Catholic University, Hungary ABSTRACT A crucial component of text-to-speech systems is the one respon- sible for the transcription of the written text to its phonemic rep- resentation. although the complexity of the relation between the written and spoken form of languages varies, most languages have their regular and irregular phonological set of rules. In this paper, we present a system for the phonemic transcription of Hungarian. Beside the implementation of rules describing default letter-to-phoneme correspondences and morphophonological al- ternations, the tool incorporates the knowledge of a Hungarian morphological analyzer in order to be able to detect compound and other morpheme boundaries, and it contains a rich lexicon of entries with irregular pronunciation. It is shown that the system performs well even on texts containing a high number of foreign names. 1 INTRODUCTION In the research reported about in this study, our goal was to imple- ment a system that can automatically transform written Hungarian to its phonemic representation. The original intent of the system This is a pre-print version of the paper, before proper formatting and copyediting by the editorial staff. 162 ATTILA NOVÁK AND BORBÁLA SIKLÓSI was to transcribe a database of Hungarian geographic terms. How- ever, due to certain design decisions, our system proved to perform well also on texts containing a high ratio of foreign names and suf- fixed forms. -
![Russian Voicing Assimilation, Final Devoicing, and the Problem of [V] (Or, the Mouse That Squeaked)*](https://docslib.b-cdn.net/cover/8163/russian-voicing-assimilation-final-devoicing-and-the-problem-of-v-or-the-mouse-that-squeaked-388163.webp)
Russian Voicing Assimilation, Final Devoicing, and the Problem of [V] (Or, the Mouse That Squeaked)*
Russian voicing assimilation, final devoicing, and the problem of [v] (or, The mouse that squeaked)* Jaye Padgett - University of California, Santa Cruz "...the Standard Russian V...occupies an obviously intermediate position between the obstruents and the sonorants." Jakobson (1978) 1. Introduction Like the mouse that roared, the Russian consonant [v] has a status in phonology out of proportion to its size. Besides leaving a trail of special descriptive comments, this segment has played a key role in discussions about abstractness in phonology, about the manner in which long-distance spreading occurs, and about the the larger organization of phonology. This is largely because of the odd behavior of [v] with respect to final devoicing and voicing assimilation in Russian. Russian obstruents devoice word-finally, as in kniga 'book (nom. sg.) vs. knik (gen. pl.), and assimilate to the voicing of a following obstruent, gorodok 'town (nom. sg.)' vs. gorotka (gen. sg.). The role of [v] in this scenario is puzzling: like an obstruent, it devoices word-finally, krovi 'blood (gen. sg.)' vs. krofj (nom. sg.), and undergoes voicing assimilation, lavok 'bench (gen. pl.)' vs. lafka (nom. sg.). But like a sonorant, it does not trigger voicing assimilation: compare dverj 'door' and tverj 'Tver' (a town). As we will see, [v] behaves unusually in other ways as well. Why is Russian [v] special in this way? The best-known answer to this question posits that [v] is underlyingly /w/ and therefore behaves as a sonorant with respect to voicing assimilation (Lightner 1965, Daniels 1972, Coats and Harshenin 1971, Hayes 1984, Kiparsky 1985). -

[Paper on the Alignment of Low Postnuclear F0 Valleys in Dutch
ALIGNMENT OF “PHRASE ACCENT” LOWS IN DUTCH FALLING-RISING QUESTIONS: THEORETICAL AND METHODOLOGICAL IMPLICATIONS Robin J. Lickley*, Astrid Schepman** and D. Robert Ladd*** *Queen Margaret University College, Edinburgh **University of Abertay, Dundee *** Edinburgh University, Edinburgh Running Head: Dutch phrase accent lows Acknowledgements The research reported here was funded by the UK Economic and Research Council (ESRC) under grant no. R000-23-7447 to Edinburgh University, Principal Investigator D. R. Ladd. We are grateful to: Ellen Gurman Bard, for useful discussions about how to use the Map Task; Ineke Mennen for her help in devising sentences for the woon je in task; Andrew Ladd, for preparing new drawings for the Dutch maps; Carlos Gussenhoven, for providing access to the Nijmegen phonetics lab and its helpful staff, and for helping us to recruit speakers; Angela Vonk, for transcribing the Map Task corpus; Michael Bennett, Eddie Dubourg, Cedric Macmartin, and Stewart Smith, for much technical assistance in Edinburgh; the audience at the Colloquium of the British Association of Academic Phoneticians in Newcastle in March 2002, who made comments on a preliminary version of this paper; Francis Nolan and Vincent van Heuven, who read the paper as referees for Language and Speech and made many important suggestions for improvement; and above all our speakers, without whom there would have been nothing to study. Address for correspondence: Dr Robin J. Lickley, Speech and Hearing Sciences, Queen Margaret University College, Edinburgh, EH12 8TS, Scotland, UK. Email: [email protected]. 2 Abstract In the first part of this study, we measured the alignment (relative to segmental landmarks) of the low F0 turning points between the accentual fall and the final boundary rise in short Dutch falling-rising questions of the form Do you live in [place name]? produced as read speech in a laboratory setting. -

The Processing of Reduced Word Pronunciation Variants by Natives and Foreign Language Learners
The processing of reduced word pronunciaton variants by natves and learners Evidence from French casual speech Sophie Brand 6 511381-L-os-brand Processed on: 14-7-2017 The processing of reduced word pronunciation variants by natives and foreign language learners Evidence from French casual speech 2017, Sophie Brand ISBN: 978-90-76203-87-4 Cover image: Jolijn Ceelen Printed and bound by Ipskamp Drukkers b.v. The processing of reduced word pronunciation variants by natives and foreign language learners Evidence from French casual speech Proefschrift ter verkrijging van de graad van doctor aan de Radboud Universiteit Nijmegen op gezag van de rector magnificus prof. dr. J.H.J.M. van Krieken, volgens besluit van het college van decanen in het openbaar te verdedigen op woensdag 27 september 2017 om 16.30 uur precies door Sophie Wijnanda Maria Brand geboren op 25 augustus 1985 te Roermond Promotor: Prof. dr. M.T.C. Ernestus Copromotor: Dr. E. Janse Manuscriptcommissie: Prof. dr. R.W.N.M. van Hout Prof. dr. N. Warner (University of Arizona, Verenigde Staten) Dr. A. Bürki (Universität Potsdam, Duitsland) Prof. dr. H.M.G.M. Jacobs Dr. M.B.P. Starren The research reported in this dissertation was supported by a Consolidator grant from the European Research Council [grant number 284108] awarded to Prof. dr. M.T.C. Ernestus. ‘I don’t know what I may seem to the world, but, as to myself, I seem to have been only like a boy playing on the sea-shore, and diverting myself in now and then finding a smoother pebble or a prettier shell than ordinary, whilst the great ocean of truth lay all undiscovered before me’. -
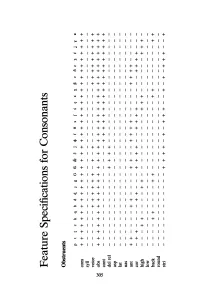
Feature Specifications for Consonants
Feature Specifications for Consonants Obstruents P t t c k q b d <l J g G is dZ c j 41 f 9 s I g ~ x X p v Oz 3 Z i Y B cons ++++++++++++ + + ++++++++++++++++++++ syll voice -++++++-+ + +++++++++ w obs ++++++++++++ + + ++++++++++++++++++++ 5i cont - --++++++++++++++++++ del rei + + + + asp lat nas ant ++----++---- + + --++++-----++++----- cor - + + - - - - + + - - - + + + + - - + + + + - - - + + + + - high + + + + + + + - - - - + + + - low back --++----++ -- --- + + - - - + + round stri - + + ++-+-+++--+-+-+++--+ Sonorants m n Q P g N § w v ~ l j A r R r Y " I 1 1: cons + + + + + + + + + + syll voice +++++++++++++++++++++ VJ obs ~ cont + + + + + + + + + + + + + del rei asp lat + + + nas + + + + + + ant + + + + + + + + + + cor + + + + + + + + + high + + + + + + low back + + + + + round + + Sample Answers to Exercises Chapter 1 c. Polish The devoiced allophone occurs between voi~less sounds, and between a voiceless sound and a word boundary. G. Tamil (a) #_; m_; V_V. Pb] 1m} (b) Ipl - [{3] I V V (c) PeJ] I 0- } /kI _ {[g] I g_ } It! - [ts] I V_V [V] I V_V (d) Yes: #_; l'I....- (e) [£1; voiced retroflex fricative: [~]. (f) Yes. [s] is the intervocalic allophone of IC!. 3. Tamil The [w] allophone occurs word-finally when the preceding vowel is unrounded. Chapter 2 C. English Irl _ {0 -. {~} } [~] I vOlceless segment _ E. Japanese Verbs (a) [eba]; [ta] and [da]. (b) [mats] and [mat]; Imat!. (c) [tswkwc] and [tswkwt]; Itwkwcl and Itwkwt!. For Itwkwt!: It! _ [c] I V_V For Itwkwc/: Icl_ [t] I_t (or: a voiceless segment) Both involve assimilation: intervocalic voicing and devoicing before a voiceless segment. 307 308 Sample Answers to Exercises The stem and the provisional form of 'wait' show that Itl does not become [1"] between vowels. -

On the Creation of a Pronunciation Dictionary for Hungarian
On the creation of a pronunciation dictionary for Hungarian Stephen M. Grimes [email protected] August 2007 Abstract This report describes the process of creating a pronunciation dictionary and phonological lexicon for Hungarian for the purpose of aiding in linguistic research on Hungarian phonology and phonotactics. The pronunciation dictionary was created by transforming orthographic forms to pronunciation representations by taking advantage of systematic deviations between Hungarian orthography and pronunciation. It is argued that the “automated” creation of such a dictionary is reasonably expected to be accurate due to the relative similarity of Hungarian orthography to actual pronunciation. This document includes discussion of goals and standards for creating a Hungarian pronunciation dictionary, and each phonological change creating a mismatch between orthography and pronunciation is highlighted. Future developments and additions to the current dictionary are also suggested as well as strategies for evaluating the quality of the dictionary. Finally, potential applications to linguistic research are discussed. 1 Introduction While students of the English language quickly learn that English spelling is by no means consistent, many Hungarians believe that the Hungarian alphabet is completely phonetic. Here, a phonetic alphabet refers to the existence of a one-to-one mapping between symbol and sound. It can quite easily be demonstrated by counter-example that 1 Hungarian orthography is not phonetic, and in fact several types of orthographic- pronunciation discrepancies exist. Consider as an example the word /szabadság/ 1 [sabatʃ:a:g] ‘freedom, liberty’ , in which no fewer than four orthographic-pronunciation discrepancies can be identified with the written form of this word: (1) a. -

Phonetic Documentation in Three Collections: Topics and Evolution
Phonetic documentation in three collections: Topics and evolution D. H. Whalen City University of New York (also Haskins Laboratories and Yale University) [email protected] Christian DiCanio University at Buffalo [email protected] Rikker Dockum Swarthmore College [email protected] Phonetic aspects of many languages have been documented, though the breadth and focus of such documentation varies substantially. In this survey, phonetic aspects (here called ‘categories’) that are typically reported were assessed in three English-language collections – the Illustrations of the IPA from the Journal of the International Phonetic Association, articles from the Journal of Phonetics, and papers from the Ladefoged/Maddieson Sounds of the World’s Languages (SOWL) documentation project. Categories were defined for consonants (e.g. Voice Onset Time (VOT) and frication spec- trum; 10 in total), vowels (e.g. formants and duration; 7 in total) and suprasegmentals (e.g. stress and distinctive vowel length, 6 in total). The Illustrations, due to their brevity, had, on average, limited coverage of the selected categories (12% of the 23 categories). Journal of Phonetics articles were typically theoretically motivated, but 64 had sufficient measurements to count as phonetic documentation; these also covered 12% of the cate- gories. The SOWL studies, designed to cover as much of the phonetic structure as feasible in an article-length treatment, achieved 41% coverage on average. Four book-length stud- ies were also examined, with an average of 49% coverage. Phonetic properties of many language families have been studied, though Indo-European is still disproportionately rep- resented. Physiological measures were excluded as being less common, and perceptual measures were excluded as being typically more theoretical. -

Friction Between Phonetics and Phonology the Status of Affricates
Friction between Phonetics and Phonology The status of affricates Published by LOT phone: +31 30 253 5775 Trans 10 3512 JK Utrecht e-mail: [email protected] The Netherlands http://www.lotschool.nl ISBN: 978-94-6093-122-2 NUR 616 Copyright © 2013 by Janine Berns. All rights reserved. Friction between Phonetics and Phonology The status of affricates Proefschrift ter verkrijging van de graad van doctor aan de Radboud Universiteit Nijmegen op gezag van de rector magnificus prof. mr. S.C.J.J. Kortmann, volgens besluit van het college van decanen in het openbaar te verdedigen op vrijdag 8 november 2013 om 10.30 uur precies door Janine Katharina Maria Berns geboren op 18 juni 1985 te Kerkrade Promotoren: Prof. dr. Haike Jacobs Prof. dr. Bernard Laks (Université Paris Ouest Nanterre la Défense) Manuscriptcommissie: Prof. dr. Anneke Neijt Prof. dr. Barbara Bullock (University of Texas) Prof. dr. Marie-Hélène Côté (University of Ottawa) Prof. dr. Frans Hinskens (Vrije Universiteit Amsterdam) Prof. dr. Jeroen van de Weijer (Shanghai International Studies University) “As a rule,” said Holmes, “the more bizarre a thing is the less mysterious it proves to be”. Sir Arthur Conan Doyle. The Adventures of Sherlock Holmes, The Red-headed League. (1891) Acknowledgements I would like to dedicate the very first lines of this thesis to my two supervisors, Haike Jacobs and Bernard Laks. Haike, thank you for giving me the freedom to develop my own interests and insights, but also for being there with your enlightening comments when I felt lost or when I was complicating things too much. -

Hungarian Vowel Harmony Meets Ot*
HUNGARIAN VOWEL HARMONY MEETS OT* John T. Jensen Margaret Stong-Jensen University of Ottawa Independent Scholar Hungarian vowel harmony has been described in a number of phonological frameworks, from pre-SPE (Hall 1938) to SPE (Jensen 1972; Vago 1974, 1980), Autosegmental phonology (Clements 1977), Lexical phonology (Jensen 1984), Government phonology (Polgárdi & Rebrus 1998) and Optimality theory (Ringen & Vago 1998b; Hayes & Cziráki-Londe 2006). According to Ringen & Vago (1998b:393), “no comprehensive and completely satisfactory account in a rule-based theory exists” for Hungarian vowel harmony. We submit that OT also does not solve the problems, and that indeed new ones arise. There is no completely satisfactory OT account of Hungarian vowel harmony, and a rule- based account seems to be the most satisfactory account after all. 1. Back and Round Harmony Types in Hungarian. In (1) we give the phonetic vowel system of Hungarian, in the dialect that Polgárdi & Rebrus call the “high-mid ë” dialect, which distinguishes two front nonhigh short vowels, represented in Hungarian dialect studies as <ë> for the higher-mid and <e> for the lower mid, which is sometimes characterized as low (Ringen & Vago 1998b:408). Ringen & Vago use the phonetic symbol [ɛ] for this vowel, which however properly represents a lower-mid or lax mid vowel, while the symbol [æ] is the proper symbol for the low vowel. Without committing ourselves to the exact phonetic values of these two vowels, the important thing is that they are distinguished in this dialect, but neutralized in the standard variety of Budapest to [ɛ]. In terms of alternations, the lower [æ] alternates with the low back vowel [ɒ] and the mid <ë> alternates with the mid vowels [o] and [ö]. -

On Hungarian Morphology Andr ´As Kornai
ON HUNGARIAN MORPHOLOGY ANDRAS´ KORNAI Abstract The aim of this study is to provide an autosegmental description of Hungarian morphology. Chap- ter 1 sketches the (meta)theoretical background and summarizes the main argument. In Chapter 2 phonological prerequisites to morphological analysis are discussed. Special attention is paid to Hungarian vowel harmony. In Chapter 3 a universal theory of lexical categories is proposed, and the category system of Hungarian is described within it. The final chapter presents a detailed descrip- tion of nominal and verbal inflection in Hungarian, and describes the main features of a computer implementation based on the analyses provided here. 1 0. Preface 3 1. Introduction 5 1.1 The methods of the investigation 6 1.2 Summary of new results 8 1.3 Vowel harmony 9 1.4 Summary of conclusions 12 2. Phonology 14 2.1 The feature system: vowels 14 2.2 Consonants 23 2.3 Vowel harmony 29 2.4 Syllable structure 47 2.5 Postlexical rules 53 2.6 Appendix 57 3. Words and paradigms 67 3.1 Some definitions 67 3.2 The lexical categories of Hungarian 76 4. Inflectional morphology 81 4.1 Conjugation 81 4.2 Declension 106 4.3 Implementation 116 4.4 Conclusion 147 5. Bibliography 149 2 0 Preface This thesis was written in 1984-1986 – the first publicly circulated version (Version 1.4) was defended at the Hungarian Academy of Sciences (HAS) Institute of Linguistics in September 1986. An extended Version 2 was submitted to the HAS Scientific Qualifications Committee in August 1988, and was formally defended in September 1989. -

Hungarian in the United States*
JB[v.20020404] Prn:13/04/2005; 11:49 F: IMP2009.tex / p.1 (49-130) View metadata, citation and similar papers at core.ac.uk brought to you by CORE Chapter 9 provided by SZTE Publicatio Repozitórium - SZTE - Repository of... HungarianintheUnitedStates* Anna Fenyvesi . Introduction This chapter provides an overview of the Hungarian minority in the United States, the Hungarian-Americans, and their language. Since no study on the sociolinguistic situation of the entire Hungarian-American population of the United States exists, the description of the sociolinguistic aspects of this community is based on census records and the available comprehensive studies of the sociolinguistic and linguistic aspects of four Hungarian-American communities. These latter are the following: Kontra (1990), the first such study, on Hungarian as spoken in South Bend, Indiana (for a review of it in English, see Kerek 1992); Bartha (1993), on Hungarian in the Delray neighborhood of Detroit, Michigan; Fenyvesi (1995a), on Hungarian in McKeesport, Pennsylvania, a small town just outside Pitts- burgh; and Polgár (2001), on the sociolinguistic aspects of Hungarian-Americans in the Birmingham neighborhood of Toledo, Ohio. Sociolinguistic aspects . The origin of the contact situation Groups of Hungarian immigrants started arriving in the United States in the mid-19th century. Before this time, only sporadically did Hungarian individuals resettle in or visit this country. Allegedly, one Hungarian sailed with Leif Ericsson in the 10th century and another with Sir Humphrey Gilbert, one of Elizabethan England’s colonists in the New World, in the 16th. Hungarian volunteers fought in the American Revolution and were followed by Hungarian travelers, naturalists and explorers in the 19th cen- tury.