DECEMBER 2015 DISTRIBUTION RESTRICTION: Approved for Public Release; Distribution Is Unlimited
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

+P+-+K+- +-+-+-+- B -+-+P+-+ W -+-+-+-+ Zlw-+P+R +-+-+-Z- P+-+N+Q+ P+-+-+-+ +-+-+-+- Z-+K+-+- -+-+-TP+ Kwqs-Z-S +-+-+RM- +-+-+-+
Contents Symbols 4 Introduction 5 Part 1: The Basics 1 Pin 7 2 Deflection 16 3 Overload 23 4 Decoy 28 5 Double Attack 36 6 Knight Fork 44 7 Discovered Attack 50 8 Clearance 56 9 Obstruction 64 10 Removing the Defender 71 11 The Power of the Pawn 77 12 Back-Rank Mate 85 13 Stalemate 91 14 Perpetual Check and Fortresses 96 Part 2: Advanced Tactics 15 f7: Weak by Presumption 103 16 The Vulnerable Rook’s Pawn 111 17 Attacking the Fianchetto 118 18 The Mystery of the Opposite-Coloured Bishops 125 19 Chess Highways: Open Files 131 20 Trapping a Piece 141 21 Practice Makes Perfect 149 Solutions 158 Index of Players 188 Index of Composers 191 KNIGHT FORK 6 Knight Fork The knight is considered to be the least powerful White is now a queen and two rooks down – piece in chess (besides the pawn, of course). As a deficit of approximately 19 ‘pawns’. His only the great world champion Jose Raul Capablanca remaining piece is a knight. But a brave one... taught us, the other minor piece, the bishop, is 3 Ìe3+ Êf6 4 Ìxd5+ Êf5 5 Ìxe7+ Êf6 6 better in 90% of cases. However, due to its spe- Ìxg8+ (D) cific qualities the knight is a tremendously dan- gerous piece. It is nimble and its jumps can be -+-+-+N+ quite shocking. That is why a double attack by a +-+-+p+- knight is usually distinguished from other dou- B ble attacks and called a fork. -+-+nm-M +-+-z-+- A single knight may cause incredible dam- age in the right circumstances: -+-+-+-+ +-+-+PZ- -+-+-+q+ -+-+-+-+ +-+r+p+- +-+-+-+- W -+N+nm-M +-+rz-+- The knight has managed to remove most of Black’s army. -

The Wangling Wizards the Chess Problems of the Warton Brothers
The Wangling Wizards The chess problems of the Warton brothers Compiled by Michael McDowell ½ û White to play and mate in 3 British Chess Problem Society 2005 The Wangling Wizards Introduction Tom and Joe Warton were two of the most popular British chess problem composers of the twentieth century. They were often compared to the American "Puzzle King" Sam Loyd because they rarely composed problems illustrating formal themes, instead directing their energies towards hoodwinking the solver. Piquant keys and well-concealed manoeuvres formed the basis of a style that became known as "Wartonesque" and earned the brothers the nickname "the Wangling Wizards". Thomas Joseph Warton was born on 18 th July 1885 at South Mimms, Hertfordshire, and Joseph John Warton on 22 nd September 1900 at Notting Hill, London. Another brother, Edwin, also composed problems, and there may have been a fourth composing Warton, as a two-mover appeared in the August 1916 issue of the Chess Amateur under the name G. F. Warton. After a brief flourish Edwin abandoned composition, although as late as 1946 he published a problem in Chess . Tom and Joe began composing around 1913. After Tom’s early retirement from the Metropolitan Police Force they churned out problems by the hundred, both individually and as a duo, their total output having been estimated at over 2600 problems. Tom died on 23rd May 1955. Joe continued to compose, and in the 1960s published a number of joints with Jim Cresswell, problem editor of the Busmen's Chess Review , who shared his liking for mutates. Many pleasing works appeared in the BCR under their amusing pseudonym "Wartocress". -

Pof: Proof-Of-Following for Vehicle Platoons
Verification of Platooning using Large-Scale Fading Ziqi Xu* Jingcheng Li* Yanjun Pan University of Arizona University of Arizona University of Arizona [email protected] [email protected] [email protected] Loukas Lazos Ming Li Nirnimesh Ghose University of Arizona University of Arizona University of Nebraska–Lincoln [email protected] [email protected] [email protected] Abstract—Cooperative vehicle platooning significantly im- I am AV proves highway safety, fuel efficiency, and traffic flow. In this 2 and I follow AV model, a set of vehicles move in line formation and coordinate 1 acceleration, braking, and steering using a combination of path physical sensing and vehicle-to-vehicle (V2V) messaging. The candidate verifier authenticity and integrity of the V2V messages are paramount to platooning AV AV safety. For this reason, recent V2V and V2X standards support 2 distance 1 the integration of a PKI. However, a PKI cannot bind a vehicle’s digital identity to the vehicle’s physical state (location, velocity, Fig. 1: Platooning of AV1 and AV2: The AV1 acts as a verifier etc.). As a result, a vehicle with valid cryptographic credentials to validate AV2’s claim that it follows the platoon. can impact platoons from a remote location. In this paper, we seek to provide the missing link between the However, the complex integration of multi-modal physical physical and the digital world in the context of vehicle platooning. sensing, computation, and communication creates a particu- We propose a new access control protocol we call Proof-of- larly challenging environment to safeguard. The safety of the Following (PoF) that verifies the following distance between a platoon relies on the veracity of the V2V messages exchanged candidate and a verifier. -

Шахматных Задач Chess Exercises Schachaufgaben
Всеволод Костров Vsevolod Kostrov Борис Белявский Boris Beliavsky 2000 Шахматных задач Chess exercises Schachaufgaben РЕШЕБНИК TACTICAL CHESS.. EXERCISES SCHACHUBUNGSBUCH Шахматные комбинации Chess combinations Kombinationen Часть 1-2 разряд Part 1700-2000 Elo 3 Teil 1-2 Klasse Русский шахматный дом/Russian Chess House Москва, 2013 В первых двух книжках этой серии мы вооружили вас мощными приёмами для успешного ведения шахматной борьбы. В вашем арсенале появились двойной удар, связка, завлечение и отвлечение. Новый «Решебник» обогатит вас более изысканным тактическим оружием. Не всегда до короля можно добраться, используя грубую силу. Попробуйте обхитрить партнёра с помощью плаща и кинжала. Маскируйтесь, как разведчик, и ведите себя, как опытный дипломат. Попробуйте найти слабое место в лагере противника и в нужный момент уничтожьте защиту и нанесите тонкий кинжальный удар. Кстати, чужие фигуры могут стать союзниками. Умелыми манёврами привлеките фигуры противника к их королю, пускай они его заблокируют так, чтобы ему, бедному, было не вздохнуть, и в этот момент нанесите решающий удар. Неприятно, когда все фигуры вашего противника взаимодействуют между собой. Может, стоить вбить клин в их порядки – перекрыть их прочной шахматной дверью. А так ли страшна атака противника на ваши укрепления? Стоит ли уходить в глухую оборону? Всегда ищите контрудар. Тонкий промежуточный укол изменит ход борьбы. Не сгрудились ли ваши фигуры на небольшом пространстве, не мешают ли они друг другу добраться до короля противника? Решите, кому всё же идти на штурм королевской крепости, и освободите пространство фигуре для атаки. Короля всегда надо защищать в первую очередь. Используйте это обстоятельство и совершите открытое нападение на него и другие фигуры. И тогда жернова вашей «мельницы» перемелют всё вражеское войско. -

IZA Discussion Paper No. 491 May 2002
IZA DP No. 491 On the Production of Victory: Empirical Determinants of Battlefield Success in Modern War Ralph Rotte Christoph M. Schmidt DISCUSSION PAPER SERIES DISCUSSION PAPER May 2002 Forschungsinstitut zur Zukunft der Arbeit Institute for the Study of Labor On the Production of Victory: Empirical Determinants of Battlefield Success in Modern War Ralph Rotte RWTH Aachen, CEPR London and IZA, Bonn Christoph M. Schmidt University of Heidelberg, CEPR London and IZA, Bonn Discussion Paper No. 491 May 2002 IZA P.O. Box 7240 D-53072 Bonn Germany Tel.: +49-228-3894-0 Fax: +49-228-3894-210 Email: [email protected] This Discussion Paper is issued within the framework of IZA’s research area The Future of Labor. Any opinions expressed here are those of the author(s) and not those of the institute. Research disseminated by IZA may include views on policy, but the institute itself takes no institutional policy positions. The Institute for the Study of Labor (IZA) in Bonn is a local and virtual international research center and a place of communication between science, politics and business. IZA is an independent, nonprofit limited liability company (Gesellschaft mit beschränkter Haftung) supported by the Deutsche Post AG. The center is associated with the University of Bonn and offers a stimulating research environment through its research networks, research support, and visitors and doctoral programs. IZA engages in (i) original and internationally competitive research in all fields of labor economics, (ii) development of policy concepts, and (iii) dissemination of research results and concepts to the interested public. The current research program deals with (1) mobility and flexibility of labor, (2) internationalization of labor markets, (3) welfare state and labor markets, (4) labor markets in transition countries, (5) the future of labor, (6) evaluation of labor market policies and projects and (7) general labor economics. -

THE SPY WHO FIRED ME the Human Costs of Workplace Monitoring by ESTHER KAPLAN
Garry Wills on the u A Lost Story by u William T. Vollmann Future of Catholicism Vladimir Nabokov Visits Fukushima HARPER’S MAGAZINE/MARCH 2015 $6.99 THE SPY WHO FIRED ME The human costs of workplace monitoring BY ESTHER KAPLAN u A GRAND JUROR SPEAKS The Inside Story of How Prosecutors Always Get Their Way BY GIDEON LEWIS-KRAUS GIVING UP THE GHOST The Eternal Allure of Life After Death BY LESLIE JAMISON REPORT THE SPY WHO FIRED ME The human costs of workplace monitoring By Esther Kaplan ast March, Jim data into metrics to be Cramer,L the host of factored in to your per- CNBC’s Mad Money, formance reviews and devoted part of his decisions about how show to a company much you’ll be paid. called Cornerstone Miller’s company is OnDemand. Corner- part of an $11 billion stone, Cramer shouted industry that also at the camera, is “a includes workforce- cloud-based-software- management systems as-a-service play” in the such as Kronos and “talent- management” “enterprise social” plat- field. Companies that forms such as Micro- use its platform can soft’s Yammer, Sales- quickly assess an em- force’s Chatter, and, ployee’s performance by soon, Facebook at analyzing his or her on- Work. Every aspect of line interactions, in- an office worker’s life cluding emails, instant can now be measured, messages, and Web use. and an increasing “We’ve been manag- number of corporations ing people exactly the and institutions—from same way for the last cosmetics companies hundred and fifty to car-rental agencies— years,” Cornerstone’s are using that informa- CEO, Adam Miller, tion to make hiring told Cramer. -

The Combat Effectiveness of Australian and American Infantry Battalions in Papua in 1942-1943 Bryce Michael Fraser University of Wollongong
University of Wollongong Research Online University of Wollongong Thesis Collection University of Wollongong Thesis Collections 2013 The combat effectiveness of Australian and American infantry battalions in Papua in 1942-1943 Bryce Michael Fraser University of Wollongong Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] Faculty of Arts School of History and Politics The combat effectiveness of Australian and American infantry battalions in Papua in 1942-1943 Bryce Michael Fraser, BA. This thesis is presented as the requirement for the Award of the Degree of Doctor of Philosophy University of Wollongong March 2013 CERTIFICATION I, Bryce Michael Fraser, declare that this thesis, submitted in fulfilment of the requirements for the award of Doctor of Philosophy, in the Department of History and Politics, University of Wollongong, is wholly my own work unless otherwise referenced or acknowledged. The document has not been submitted for qualifications at any other academic institution. B M Fraser 25 March 2013 ii TABLE OF CONTENTS LIST OF TABLES AND FIGURES iv ABBREVIATIONS vii ABSTRACT viii ACKNOWLEDGEMENTS x Introduction: 1 Chapter 1: Theory and methodology 13 Chapter 2: The campaign and the armies in Papua 53 Chapter 3: Review of literature and sources 75 Chapter 4 : The combat readiness of the battalions in the 14th Brigade 99 Chapter 5: Reinterpreting the site and the narrative of the battle of Ioribaiwa 135 Chapter 6: Ioribaiwa battle analysis 185 Chapter 7: Introduction to the Sanananda road 211 Chapter 8: American and Australian infantry battalions in attacks at the South West Sector on the Sanananda road 249 Chapter 9: Australian Militia and AIF battalions in the attacks at the South West Sector on the Sanananda road. -

Spy Culture and the Making of the Modern Intelligence Agency: from Richard Hannay to James Bond to Drone Warfare By
Spy Culture and the Making of the Modern Intelligence Agency: From Richard Hannay to James Bond to Drone Warfare by Matthew A. Bellamy A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (English Language and Literature) in the University of Michigan 2018 Dissertation Committee: Associate Professor Susan Najita, Chair Professor Daniel Hack Professor Mika Lavaque-Manty Associate Professor Andrea Zemgulys Matthew A. Bellamy [email protected] ORCID iD: 0000-0001-6914-8116 © Matthew A. Bellamy 2018 DEDICATION This dissertation is dedicated to all my students, from those in Jacksonville, Florida to those in Port-au-Prince, Haiti and Ann Arbor, Michigan. It is also dedicated to the friends and mentors who have been with me over the seven years of my graduate career. Especially to Charity and Charisse. ii TABLE OF CONTENTS Dedication ii List of Figures v Abstract vi Chapter 1 Introduction: Espionage as the Loss of Agency 1 Methodology; or, Why Study Spy Fiction? 3 A Brief Overview of the Entwined Histories of Espionage as a Practice and Espionage as a Cultural Product 20 Chapter Outline: Chapters 2 and 3 31 Chapter Outline: Chapters 4, 5 and 6 40 Chapter 2 The Spy Agency as a Discursive Formation, Part 1: Conspiracy, Bureaucracy and the Espionage Mindset 52 The SPECTRE of the Many-Headed HYDRA: Conspiracy and the Public’s Experience of Spy Agencies 64 Writing in the Machine: Bureaucracy and Espionage 86 Chapter 3: The Spy Agency as a Discursive Formation, Part 2: Cruelty and Technophilia -

News Release
NEWS RELEASE Visit http://www.mindef.gov.sg for more news and information about MINDEF and the SAF Date of issue: 5 Oct 2019 Training at Shoalwater Bay Training Area a Valuable Opportunity: Maliki Osman 1. Senior Minister of State for Defence Dr Mohamad Maliki Bin Osman visited the Singapore Armed Forces (SAF) troops participating in Exercise Wallaby 2019 at the Shoalwater Bay Training Area (SWBTA) in Queensland, Australia today. This year’s exercise, conducted from 24 Sep to 7 Nov 2019, involves about 3,000 personnel and 300 platforms from the Singapore Army and the Republic of Singapore Air Force (RSAF). 2. During his visit, Dr Maliki witnessed a Combat Search and Rescue demonstration on board the RSAF’s Super Puma helicopter and embarked on a familiarisation ride on the Light Strike Vehicle Mark II to experience the realistic training conditions in the SWBTA. He also interacted with exercise participants from the 1st Battalion, Singapore Guards and 6 Divisional Air Defence Artillery Battalion, and commended them for their professionalism and commitment. 3. Speaking at the end of his visit, Dr Maliki reaffirmed the strong bilateral defence ties with Australia and expressed appreciation for Australia’s strong support for the SAF’s training at the SWBTA over the past 29 years. Dr Maliki said, “We appreciate the support given by the Australian government, the Australian Defence Force and the local communities here in Rockhampton and Livingstone Shire… We treasure and cherish the relationship and friendship that we have with the local community”. Dr Maliki also emphasised the importance of overseas training in providing realistic and challenging training opportunities for the SAF to hone its operational competencies. -
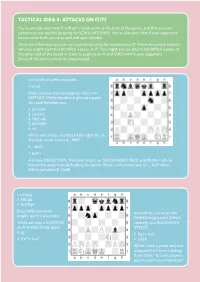
TACTICAL IDEA 4: ATTACKS on F7/F2
TACTICAL IDEA 4: ATTACKS ON f7/f2 You’ve already seen that f7 is Black’s weak point at the start of the game, and that you can sometimes win quickly by going for SCHOLAR’S MATE. You’ve also seen that if your opponent knows what to do you may well end up in trouble. There are other ways you can win quickly by using the weakness on f7. There are several reasons why you might want to SACRIFICE a piece on f7. You might also be able to SACRIFICE a piece at the other end of the board in order to capture on f7 and CHECKMATE your opponent. Some of the tactics are quite complicated. Let’s look at a few examples. 1. e4 c5 Black chooses the very popular SICILIAN DEFENCE. White decides to give up a pawn for rapid development. 2. d4 cxd4 3. c3 dxc3 4. Nxc3 d6 5. Bc4 Nf6 6. e5 White sets a trap, and Black falls right into it. The best move now is 6… Nfd7 6… dxe5 7. Bxf7+ A simple DEFLECTION. The black king is an OVERWORKED PIECE and White’s bishop forces him away from defending the queen. Black’s only move now is 7… Kxf7 when White just plays 8. Qxd8. 1. e4 Nc6 2. Nf3 d6 3. Bc4 Bg4 Black PINS the white Now White can move the knight, but it’s a mistake. PINNED knight with CHECK, White can play a SACRIFICE opening up a DISCOVERED on f7 to DECOY the black ATTACK. king. 5. -

Cavalry: an Optimized Capability for Ado
CAVALRY: AN OPTIMIZED CAPABILITY FOR ADO Maj R.M.R. Morin JCSP 41 PCEMI 41 Exercise Solo Flight Exercice Solo Flight Disclaimer Avertissement Opinions expressed remain those of the author and Les opinons exprimées n’engagent que leurs auteurs do not represent Department of National Defence or et ne reflètent aucunement des politiques du Canadian Forces policy. This paper may not be used Ministère de la Défense nationale ou des Forces without written permission. canadiennes. Ce papier ne peut être reproduit sans autorisation écrite. © Her Majesty the Queen in Right of Canada, as © Sa Majesté la Reine du Chef du Canada, représentée par represented by the Minister of National Defence, 2015. le ministre de la Défense nationale, 2015. CANADIAN FORCES COLLEGE – COLLÈGE DES FORCES CANADIENNES JCSP 41 – PCEMI 41 2014 – 2015 EXERCISE SOLO FLIGHT – EXERCICE SOLO FLIGHT CAVALRY: AN OPTIMIZED CAPABILITY FOR ADO Maj R.M.R. Morin “This paper was written by a student “La présente étude a été rédigée par un attending the Canadian Forces College stagiaire du Collège des Forces in fulfilment of one of the requirements canadiennes pour satisfaire à l'une des of the Course of Studies. The paper is a exigences du cours. L'étude est un scholastic document, and thus contains document qui se rapporte au cours et facts and opinions, which the author contient donc des faits et des opinions alone considered appropriate and que seul l'auteur considère appropriés et correct for the subject. It does not convenables au sujet. Elle ne reflète pas necessarily reflect the policy or the nécessairement la politique ou l'opinion opinion of any agency, including the d'un organisme quelconque, y compris le Government of Canada and the gouvernement du Canada et le ministère Canadian Department of National de la Défense nationale du Canada. -

The Time Value of Military Force in Modern Warfare the Airpower Advantage
The Time Value of Military Force in Modern Warfare The Airpower Advantage WALTER D. GIVHAN, Major, USAF School of Advanced Airpower Studies THESIS PRESENTED TO THE FACULTY OF THE SCHOOL OF ADVANCED AIRPOWER STUDIES, MAXWELL AIR FORCE BASE, ALABAMA, FOR COMPLETION OF GRADUATION REQUIREMENTS, ACADEMIC YEAR 1994–95. Air University Press Maxwell Air Force Base, Alabama March 1996 Disclaimer The author produced this paper in a Department of Defense school environment in the interest of academic freedom and the advancement of national defense-related concepts. The views expressed in this publication are those of the author and do not reflect the official policy or position of the Department of Defense or the United States government. This publication has been reviewed by security and policy review authorities and is cleared for public release. ii Contents Chapter Page DISCLAIMER . ii ABSTRACT . v ABOUT THE AUTHOR . vii ACKNOWLEDGMENTS . ix 1 INTRODUCTION . 1 Overview . 1 Methodology . 2 Definitions . 2 Limits of the Argument . 3 Notes . 3 2 TIME IN THE THEORY OF WAR . 5 War Theorists on Time . 6 Characteristics of Time in War . 7 Physical and Psychological Aspects of Time . 8 Political and Military Dynamics of Time . 9 Summary . 10 Notes . 11 3 THE ARAB-ISRAELI WAR OF 1967 . 13 The Course of the War . 13 Political Imperatives . 14 Military Imperatives . 15 The Time Problem . 15 Operational Consequences and Risk . 16 Airpower’s Role . 17 Summary . 19 Notes . 20 4 THE FALKLANDS WAR . 21 The Course of the War . 21 Political Imperatives . 22 Military Imperatives . 24 The Time Problem . 25 Operational Consequences and Risk .