A Short History of Army Intelligence
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
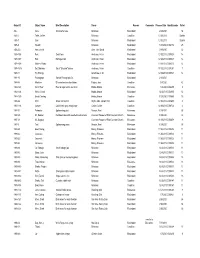
D4 DEACCESSION LIST 2019-2020 FINAL for HLC Merged.Xlsx
Object ID Object Name Brief Description Donor Reason Comments Process Date Box Barcode Pallet 496 Vase Ornamental vase Unknown Redundant 2/20/2020 54 1975-7 Table, Coffee Unknown Condition 12/12/2019 Stables 1976-7 Saw Unknown Redundant 12/12/2019 Stables 1976-9 Wrench Unknown Redundant 1/28/2020 C002172 25 1978-5-3 Fan, Electric Baer, John David Redundant 2/19/2020 52 1978-10-5 Fork Small form Anderson, Helen Redundant 12/12/2019 C001523 14 1978-10-7 Fork Barbeque fork Anderson, Helen Redundant 12/12/2019 C001523 14 1978-10-9 Masher, Potato Anderson, Helen Redundant 12/12/2019 C001523 14 1978-10-16 Set, Dishware Set of "Bluebird" dishes Anderson, Helen Condition 11/12/2019 C001351 7 1978-11 Pin, Rolling Grantham, C. W. Redundant 12/12/2019 C001523 14 1981-10 Phonograph Sonora Phonograph Co. Unknown Redundant 2/11/2020 1984-4-6 Medicine Dr's wooden box of antidotes Fugina, Jean Condition 2/4/2020 42 1984-12-3 Sack, Flour Flour & sugar sacks, not local Hobbs, Marian Relevance 1/2/2020 C002250 9 1984-12-8 Writer, Check Hobbs, Marian Redundant 12/3/2019 C002995 12 1984-12-9 Book, Coloring Hobbs, Marian Condition 1/23/2020 C001050 15 1985-6-2 Shirt Arrow men's shirt Wythe, Mrs. Joseph Hills Condition 12/18/2019 C003605 4 1985-11-6 Jumper Calvin Klein gray wool jumper Castro, Carrie Condition 12/18/2019 C001724 4 1987-3-2 Perimeter Opthamology tool Benson, Neal Relevance 1/29/2020 36 1987-4-5 Kit, Medical Cardboard box with assorted medical tools Covenant Women of First Covenant Church Relevance 1/29/2020 32 1987-4-8 Kit, Surgical Covenant -

Integrating the Army Geospatial Enterprise: Synchronizing Geospatial-Intelligence to the Dismounted Soldier
Integrating the Army Geospatial Enterprise: Synchronizing Geospatial-Intelligence to the Dismounted Soldier by James E. Richards Bachelors of Science in Mechanical Engineering, United States Military Academy, 2001 Master of Science, Engineering Management, University of Missouri-Rolla, Rolla, Missouri, 2005 SUBMITTED TO THE SYSTEM DESIGN AND MANAGEMENT PROGRAM IN PARTIAL FULFILLMENT OF THE REQUIREMENTS OF THE DEGREE OF MASTER OF SCIENCE IN ENGINEERING AND MANAGEMENT at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY June 2010 The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part in any medium now known or hereafter created. 1 [This Page Intentionally Left Blank] 2 Army‘s Geospatial Architecture: delivering Geospatial-Intelligence of complex and urban terrain to the dismounted Soldier by James E. Richards ABSTRACT The Army‘s Geospatial Enterprise (AGE) has an emerging identity and value proposition arising from the need to synchronize geospatial information activities across the Army in order to deliver value to military decision makers. Recently, there have been significant efforts towards increasing the capability of the enterprise to create value for its diverse stakeholder base, ranging from the warfighter, to early stage research and development. The AGE has many architectural alternatives to consider as it embarks upon geospatial transformation within the Army, each of these alternatives must deliver value through an increasingly wide range of operating environments characterized by the uncertainty of both future technology and the evolution of future operations. This research focuses on understanding how the Army‘s geospatial foundation data layers propagate through the battlefield and enable well informed tactical decisions. -

Do You Know Where This
The SAR Colorguardsman National Society, Sons of the American Revolution Vol. 6 No. 3 Oct 2017 Inside This Issue From the Commander From the Vice-Commander Ad Hoc Committee Update Do you Firelock Drill positions Color Guard Commanders SAR Vigil at Mt Vernon know where Reports from the Field - 13 Societies Congress Color Guard Breakfast this is? Change of Command Ring Ritual Color Guardsman of the Year National Historic Sites Calendar Color Guard Events 2017 The SAR Colorguardsman Page 2 The purpose of this Commander’s Report Magazine is to It has been a very active two month period since the Knoxville Congress in provide July. I have had the honor of commanding the Color Guard at the Installation interesting Banquet in Knoxville, at the Commemoration of the Battle of Blue Licks in articles about the Kentucky, at the Fall Leadership Meeting in Louisville,the grave markings of Revolutionary War and Joshua Jones and George Vest, and at the Anniversary of the Battle of Kings Mountain in South Carolina. information regarding the I have also approved 11 medals - 6 Molly Pitcher Medals and 5 Silver Color activities of your chapter Guard Medals. Please review the Color Guard Handbook for the qualifica- tions for these medals as well as the National Von Steuben Medal for Sus- and/or state color guards tained Activity. The application forms for these can be found on the National website. THE SAR The following goals have been established for the National Color Guard COLORGUARDSMAN for 2017 to 2018: The SAR Colorguardsman is 1) Establish published safety protocols and procedures with respect to Color Guard conduct published four times a year and use of weaponry at events. -

Fm 6-02 Signal Support to Operations
FM 6-02 SIGNAL SUPPORT TO OPERATIONS SEPTEMBER 2019 DISTRIBUTION RESTRICTION: Approved for public release; distribution is unlimited. This publication supersedes FM 6-02, dated 22 January 2014. HEADQUARTERS, DEPARTMENT OF THE ARMY This publication is available at the Army Publishing Directorate site (https://armypubs.army.mil/) and the Central Army Registry site (https://atiam.train.army.mil/catalog/dashboard). *FM 6-02 Field Manual Headquarters No. 6-02 Department of the Army Washington, D.C., 13 September 2019 Signal Support to Operations Contents Page PREFACE..................................................................................................................... v INTRODUCTION ........................................................................................................ vii Chapter 1 OVERVIEW OF SIGNAL SUPPORT ........................................................................ 1-1 Section I – The Operational Environment ............................................................. 1-1 Challenges for Army Signal Support ......................................................................... 1-1 Operational Environment Overview ........................................................................... 1-1 Information Environment ........................................................................................... 1-2 Trends ........................................................................................................................ 1-3 Threat Effects on Signal Support ............................................................................. -

The Spies That Founded America: How the War for Independence Revolutionized American Espionage
Portland State University PDXScholar Young Historians Conference Young Historians Conference 2020 Apr 27th, 9:00 AM - 10:00 AM The Spies that Founded America: How the War for Independence Revolutionized American Espionage Masaki Lew Clackamas High School Follow this and additional works at: https://pdxscholar.library.pdx.edu/younghistorians Part of the History Commons, Political Science Commons, and the Sociology Commons Let us know how access to this document benefits ou.y Lew, Masaki, "The Spies that Founded America: How the War for Independence Revolutionized American Espionage" (2020). Young Historians Conference. 19. https://pdxscholar.library.pdx.edu/younghistorians/2020/papers/19 This Event is brought to you for free and open access. It has been accepted for inclusion in Young Historians Conference by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. The Spies that Founded America: How the War for Independence Revolutionized American Espionage Masaki Lew Humanities Western Civilization 102 March 16, 2020 1 Continental Spy Nathan Hale, standing below the gallows, spoke to his British captors with nothing less than unequivocal patriotism: “I only regret that I have but one life to lose for my country.”1 American History idolizes Hale as a hero. His bravery as the first pioneer of American espionage willing to sacrifice his life for the growing colonial sentiment against a daunting global empire vindicates this. Yet, behind Hale’s success as an operative on -

THE-POLISH-TRACE-Ebook.Pdf
8 THE POLISH TRACE COMPOSED FROM COMMONLY AVAILABLE SOURCES BY LECH POLKOWSKI FOR IJCRS2017 FOREWORD It is a desire of many participants of conferences to learn as much as possible about the history and culture of he visited country and place and organizers try to satisfy this desire by providing excursions into attractive places and sites. IJCRS2017 also tries to take participants to historic sites of Warmia and Mazury and to show elements of local culture. As an innovation, we propose a booklet showing some achievements of Polish scientists and cryptographers, no doubt many of them are known universally, but some probably not. What bounds all personages described here is that they all suffered due to world wars, th efirst and the second. These wars ruined their homes, made them refugees and exiles, destroyed their archives and libraries, they lost many colleagues, friends and students but were lucky enough to save lives and in some cases to begin the career overseas. We begin with the person of Jan Czochralski, world famous metallurgist, discoverer of the technique of producing metal monocrystals `the Czochralski methode’ and inventor of duraluminum and the `bahnalloy’ who started his career and obtained its heights in Germany, later returned to Poland, became a professor at the Warsaw Polytechnical, played an important role in cultural life of Warsaw, lived in Warsaw through the second world war and the Warsaw Uprising of August-September 1944 and after the war was accused of cooperating ith occupying German forces and though judged innocent was literally erased from the public life and any information about him obliterated. -

PDF for Download
THE AUSTRALIAN WAR MEMORIAL National Collection Development Plan The Australian War Memorial commemorates the sacrifice of Australian servicemen and servicewomen who have died in war. Its mission is to help Australians to remember, interpret and understand the Australian experience of war and its enduring impact on Australian society. The Memorial was conceived as a shrine, museum and archive that supports commemoration through understanding. Its development through the years has remained consistent with this concept. Today the Memorial is a commemorative centrepiece; a museum, housing world-class exhibitions and a diverse collection of material relating to the Australian experience of war; and an archive holding extensive official and unofficial documents, diaries and papers, making the Memorial a centre of research for Australian military history. The Australian War Records Section Trophy Store at Peronne. AWM E03684 The National Collection The Australian War Memorial houses one of Australia’s most significant museum collections. Consisting of historical material relating to Australian military history, the National Collection is one of the most important means by which the Memorial presents the stories of Australians who served in war. The National Collection is used to support exhibitions in the permanent galleries, temporary and travelling exhibitions, education and public programs, and the Memorial’s website. Today, over four million items record the details of Australia’s involvement in military conflicts from colonial times to the present day. Donating to the National Collection The National Collection is developed largely by donations received from serving or former members of Australia’s military forces and their families. These items come to the Memorial as direct donations or bequests, or as donations under the Cultural Gifts program. -

RESOURCES Forgotten Battles, Forgotten Maps
79 RESOURCES Forgotten Battles, Forgotten Maps: Resources for Reconstructing Historical Topographical Intelligence Using Army Map Service Materials John M. Anderson opographical intelligence is the information gathered about terrain, facilities, and transportation networks in enemy territory.1 This in- Tformation, collected to aid in military operations, remains a noble cartographic resource that historical geographers can use in a variety of ways. One map collection based on topographical intelligence languishes underused and underappreciated in many university map libraries. Falling somewhere between the glorious old maps and the newest digital cartographic products are the venerable United States Army Map Service (AMS) materials. This essay will briefly discuss the history of the AMS and how its materi- als became available in library collections. This essay also will explain topo- graphical intelligence’s importance and present the results of a survey of an AMS map collection that identified map series with high potential as research sources. Finally, it will present the locations of AMS map collections and work- ing aids for interpreting the material. Army Map Service—Background Although the American military did not have a centralized system for producing and distributing maps at the time of the Pearl Harbor attack, the U.S. Army was addressing wartime map requirements before 1941. During 1940 and 1941, the Engineer Reproduction Plant, the AMS’s predecessor, concentrated on printing topographic maps depicting Army camps and ma- neuver areas. Construction of a new building to house the Engineer Repro- John M. Anderson is Map Librarian in the Cartographic Information Center of the Department of Geogra- phy and Anthropology at Louisiana State University in Baton Rouge. -

The Quandary of Allied Logistics from D-Day to the Rhine
THE QUANDARY OF ALLIED LOGISTICS FROM D-DAY TO THE RHINE By Parker Andrew Roberson November, 2018 Director: Dr. Wade G. Dudley Program in American History, Department of History This thesis analyzes the Allied campaign in Europe from the D-Day landings to the crossing of the Rhine to argue that, had American and British forces given the port of Antwerp priority over Operation Market Garden, the war may have ended sooner. This study analyzes the logistical system and the strategic decisions of the Allied forces in order to explore the possibility of a shortened European campaign. Three overall ideas are covered: logistics and the broad-front strategy, the importance of ports to military campaigns, and the consequences of the decisions of the Allied commanders at Antwerp. The analysis of these points will enforce the theory that, had Antwerp been given priority, the war in Europe may have ended sooner. THE QUANDARY OF ALLIED LOGISTICS FROM D-DAY TO THE RHINE A Thesis Presented to the Faculty of the Department of History East Carolina University In Partial Fulfillment of the Requirements for the Degree Master of Arts in History By Parker Andrew Roberson November, 2018 © Parker Roberson, 2018 THE QUANDARY OF ALLIED LOGISTICS FROM D-DAY TO THE RHINE By Parker Andrew Roberson APPROVED BY: DIRECTOR OF THESIS: Dr. Wade G. Dudley, Ph.D. COMMITTEE MEMBER: Dr. Gerald J. Prokopowicz, Ph.D. COMMITTEE MEMBER: Dr. Michael T. Bennett, Ph.D. CHAIR OF THE DEP ARTMENT OF HISTORY: Dr. Christopher Oakley, Ph.D. DEAN OF THE GRADUATE SCHOOL: Dr. Paul J. -

Polska Myśl Techniczna W Ii Wojnie Światowej
CENTRALNA BIBLIOTEKA WOJSKOWA IM. MARSZAŁKA JÓZEFA PIŁSUDSKIEGO POLSKA MYŚL TECHNICZNA W II WOJNIE ŚWIATOWEJ W 70. ROCZNICĘ ZAKOŃCZENIA DZIAŁAŃ WOJENNYCH W EUROPIE MATERIAŁY POKONFERENCYJNE poD REDAkcJą NAUkoWą DR. JANA TARCZYńSkiEGO WARSZAWA 2015 Konferencja naukowa Polska myśl techniczna w II wojnie światowej. W 70. rocznicę zakończenia działań wojennych w Europie Komitet naukowy: inż. Krzysztof Barbarski – Prezes Instytutu Polskiego i Muzeum im. gen. Sikorskiego w Londynie dr inż. Leszek Bogdan – Dyrektor Wojskowego Instytutu Techniki Inżynieryjnej im. profesora Józefa Kosackiego mgr inż. Piotr Dudek – Prezes Stowarzyszenia Techników Polskich w Wielkiej Brytanii gen. dyw. prof. dr hab. inż. Zygmunt Mierczyk – Rektor-Komendant Wojskowej Akademii Technicznej im. Jarosława Dąbrowskiego płk mgr inż. Marek Malawski – Szef Inspektoratu Implementacji Innowacyjnych Technologii Obronnych Ministerstwa Obrony Narodowej mgr inż. Ewa Mańkiewicz-Cudny – Prezes Federacji Stowarzyszeń Naukowo-Technicznych – Naczelnej Organizacji Technicznej prof. dr hab. Bolesław Orłowski – Honorowy Członek – założyciel Polskiego Towarzystwa Historii Techniki – Instytut Historii Nauki Polskiej Akademii Nauk kmdr prof. dr hab. Tomasz Szubrycht – Rektor-Komendant Akademii Marynarki Wojennej im. Bohaterów Westerplatte dr Jan Tarczyński – Dyrektor Centralnej Biblioteki Wojskowej im. Marszałka Józefa Piłsudskiego prof. dr hab. Leszek Zasztowt – Dyrektor Instytutu Historii Nauki Polskiej Akademii Nauk dr Czesław Andrzej Żak – Dyrektor Centralnego Archiwum Wojskowego im. -

The Crossing of Heaven
The Crossing of Heaven Memoirs of a Mathematician Bearbeitet von Karl Gustafson, Ioannis Antoniou 1. Auflage 2012. Buch. xvi, 176 S. Hardcover ISBN 978 3 642 22557 4 Format (B x L): 15,5 x 23,5 cm Gewicht: 456 g Weitere Fachgebiete > Mathematik > Numerik und Wissenschaftliches Rechnen > Angewandte Mathematik, Mathematische Modelle Zu Inhaltsverzeichnis schnell und portofrei erhältlich bei Die Online-Fachbuchhandlung beck-shop.de ist spezialisiert auf Fachbücher, insbesondere Recht, Steuern und Wirtschaft. Im Sortiment finden Sie alle Medien (Bücher, Zeitschriften, CDs, eBooks, etc.) aller Verlage. Ergänzt wird das Programm durch Services wie Neuerscheinungsdienst oder Zusammenstellungen von Büchern zu Sonderpreisen. Der Shop führt mehr als 8 Millionen Produkte. 4. Computers and Espionage ...and the world’s first spy satellite... It was 1959 and the Cold War was escalating steadily, moving from a state of palpable sustained tension toward the overt threat to global peace to be posed by the 1962 Cuban Missile Crisis – the closest the world has ever come to nuclear war. Quite by chance, I found myself thrust into this vortex, involved in top-level espionage work. I would soon write the software for the world’s first spy satellite. It was a summer romance, in fact, that that led me unwittingly to this particular role in history. In 1958 I had fallen for a stunning young woman from the Washington, D.C., area, who had come out to Boulder for summer school. So while the world was consumed by the escalating political and ideological tensions, nuclear arms competition, and Space Race, I was increasingly consumed by thoughts of Phyllis. -

Thank God Such Men Lived
Thank God Such Men Lived BY KEN WRIGHT ‘For I am writing not history, and the truth is that the most brilliant exploits often tell us nothing of the virtues of the men who performed them, while on the other hand, a chance remark or a joke may reveal far more of a mans character than the mere feat of winning battles in which thousands fall or of the marshalling of great armies or laying siege to cities’ - Greek philosopher Plutarch, about 110 AD The Coastwatchers Memorial Lighthouse was erected by public subscription and by money from the Commonwealth of Australia in 1959 at Kalibobo Point in Madang, Papua New Guinea. Shaped like a rocket or a bomb, the 80-feet high reinforced concrete column has an attractive base surround and a cruciform pathway approach. This memorial lighthouse was also designed to be a practical navigational aid with provision for the installation of a powerful one million candlepower beam that would be visible up to ten miles out to sea. Part of the inscription on the dedication plate reads: ‘In honour and grateful memory of the Coastwatchers and of the loyal natives who assisted them in their heroic service behind enemy lines during the Second World War in providing intelligence vital to the conduct of Allied operations. Not only did the Coastwatchers transmit by means of teleradio from their jungle hideouts information which led to the sinking of numerous enemy warships but they were able to give timely warning of impending enemy air attacks. The contribution towards the Allied victory in the Pacific by a small body of men who constituted the Coastwatchers was out of all proportion to their numbers’.