University of Groningen Design and Verification of Lock-Free Parallel
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Special Forces' Wear of Non-Standard Uniforms*
Special Forces’ Wear of Non-Standard Uniforms* W. Hays Parks** In February 2002, newspapers in the United States and United Kingdom published complaints by some nongovernmental organizations (“NGOs”) about US and other Coalition special operations forces operating in Afghanistan in “civilian clothing.”1 The reports sparked debate within the NGO community and among military judge advocates about the legality of such actions.2 At the US Special Operations Command (“USSOCOM”) annual Legal Conference, May 13–17, 2002, the judge advocate debate became intense. While some attendees raised questions of “illegality” and the right or obligation of special operations forces to refuse an “illegal order” to wear “civilian clothing,” others urged caution.3 The discussion was unclassified, and many in the room were not * Copyright © 2003 W. Hays Parks. ** Law of War Chair, Office of General Counsel, Department of Defense; Special Assistant for Law of War Matters to The Judge Advocate General of the Army, 1979–2003; Stockton Chair of International Law, Naval War College, 1984–1985; Colonel, US Marine Corps Reserve (Retired); Adjunct Professor of International Law, Washington College of Law, American University, Washington, DC. The views expressed herein are the personal views of the author and do not necessarily reflect an official position of the Department of Defense or any other agency of the United States government. The author is indebted to Professor Jack L. Goldsmith for his advice and assistance during the research and writing of this article. 1 See, for example, Michelle Kelly and Morten Rostrup, Identify Yourselves: Coalition Soldiers in Afghanistan Are Endangering Aid Workers, Guardian (London) 19 (Feb 1, 2002). -
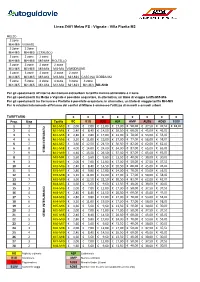
Polimetriche Per Linea STIBM Area Nord.Xlsx
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM
SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM HEINEMANN: AUSTRALIA First published in 1987 by HEINEMANN PUBLISHERS AUSTRALIA (A division of Octopus Publishing Group/Australia Pty Ltd) 85 Abinger Street, Richmond, Victoria, 3121. Copyright (c) 1987 by Peter Wright ISBN 0-85561-166-9 All Rights Reserved. No part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without the prior written permission of the publisher. TO MY WIFE LOIS Prologue For years I had wondered what the last day would be like. In January 1976 after two decades in the top echelons of the British Security Service, MI5, it was time to rejoin the real world. I emerged for the final time from Euston Road tube station. The winter sun shone brightly as I made my way down Gower Street toward Trafalgar Square. Fifty yards on I turned into the unmarked entrance to an anonymous office block. Tucked between an art college and a hospital stood the unlikely headquarters of British Counterespionage. I showed my pass to the policeman standing discreetly in the reception alcove and took one of the specially programmed lifts which carry senior officers to the sixth-floor inner sanctum. I walked silently down the corridor to my room next to the Director-General's suite. The offices were quiet. Far below I could hear the rumble of tube trains carrying commuters to the West End. I unlocked my door. In front of me stood the essential tools of the intelligence officer’s trade - a desk, two telephones, one scrambled for outside calls, and to one side a large green metal safe with an oversized combination lock on the front. -

I Was Happy and Flattered to Be Invited to Deliver This Lecture Because Like So Many Others Who Knew Michael Quinlan I Was an Impassioned Admirer
I was happy and flattered to be invited to deliver this lecture because like so many others who knew Michael Quinlan I was an impassioned admirer. Yet I cannot this evening avoid being a little daunted by the memory of an occasion twenty years ago, when we both attended a talk given by a general newly returned from the Balkans. Michael said to me afterwards: ‘Such a pity, isn’t it, when a soldier who has done really quite well on a battlefield simply lacks the intellectual firepower to explain coherently afterwards what he has been doing’. Few of us, alas, possess the ‘intellectual firepower’ to meet Michael’s supremely and superbly exacting standard. I am a hybrid, a journalist who has written much about war as a reporter and commentator; and also a historian. I am not a specialist in intelligence, either historic or contemporary. By the nature of my work, however, I am a student of the intelligence community’s impact upon the wars both of the 20th century and of our own times. I have recently researched and published a book about the role of intelligence in World War II, which confirmed my impression that while the trade employs some clever people, it also attracts some notably weird ones, though maybe they would say the same about historians. Among my favourite 1939-45 vignettes, there was a Japanese spy chief whose exploits caused him to be dubbed by his own men Lawrence of Manchuria. Meanwhile a German agent in Stockholm warned Berlin in September 1944 that the allies were about to stage a mass parachute drop to seize a Rhine bridge- the Arnhem operation. -

1 Introduction
Notes 1 Introduction 1. Donald Macintyre, Narvik (London: Evans, 1959), p. 15. 2. See Olav Riste, The Neutral Ally: Norway’s Relations with Belligerent Powers in the First World War (London: Allen and Unwin, 1965). 3. Reflections of the C-in-C Navy on the Outbreak of War, 3 September 1939, The Fuehrer Conferences on Naval Affairs, 1939–45 (Annapolis: Naval Institute Press, 1990), pp. 37–38. 4. Report of the C-in-C Navy to the Fuehrer, 10 October 1939, in ibid. p. 47. 5. Report of the C-in-C Navy to the Fuehrer, 8 December 1939, Minutes of a Conference with Herr Hauglin and Herr Quisling on 11 December 1939 and Report of the C-in-C Navy, 12 December 1939 in ibid. pp. 63–67. 6. MGFA, Nichols Bohemia, n 172/14, H. W. Schmidt to Admiral Bohemia, 31 January 1955 cited by Francois Kersaudy, Norway, 1940 (London: Arrow, 1990), p. 42. 7. See Andrew Lambert, ‘Seapower 1939–40: Churchill and the Strategic Origins of the Battle of the Atlantic, Journal of Strategic Studies, vol. 17, no. 1 (1994), pp. 86–108. 8. For the importance of Swedish iron ore see Thomas Munch-Petersen, The Strategy of Phoney War (Stockholm: Militärhistoriska Förlaget, 1981). 9. Churchill, The Second World War, I, p. 463. 10. See Richard Wiggan, Hunt the Altmark (London: Hale, 1982). 11. TMI, Tome XV, Déposition de l’amiral Raeder, 17 May 1946 cited by Kersaudy, p. 44. 12. Kersaudy, p. 81. 13. Johannes Andenæs, Olav Riste and Magne Skodvin, Norway and the Second World War (Oslo: Aschehoug, 1966), p. -

The Evolution of British Intelligence Assessment, 1940-41
University of Calgary PRISM: University of Calgary's Digital Repository Graduate Studies Legacy Theses 1999 The evolution of British intelligence assessment, 1940-41 Tang, Godfrey K. Tang, G. K. (1999). The evolution of British intelligence assessment, 1940-41 (Unpublished master's thesis). University of Calgary, Calgary, AB. doi:10.11575/PRISM/18755 http://hdl.handle.net/1880/25336 master thesis University of Calgary graduate students retain copyright ownership and moral rights for their thesis. You may use this material in any way that is permitted by the Copyright Act or through licensing that has been assigned to the document. For uses that are not allowable under copyright legislation or licensing, you are required to seek permission. Downloaded from PRISM: https://prism.ucalgary.ca THE UNIVERSITY OF CALGARY The Evolution of British Intelligence Assessment, 1940-41 by Godfiey K. Tang A THESIS SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FLTLFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS DEPARTMENT OF HISTORY CALGARY, ALBERTA JANUARY, 1999 O Godfiey K Tang 1999 National Library Biblioth4que nationale #*lof Canada du Canada Acquisitions and Acquisitions et Bibliographic Services services bibliographiques 395 Wellington Street 395, rue Wellington OnawaON K1AON4 Ottawa ON KIA ON4 Canada Canada The author has granted a non- L'auteur a accorde une licence non exclusive licence allowing the exclusive pernettant Pla National Library of Canada to Blbliotheque nationale du Canada de reproduce, loan, distribute or sell reproduire, preter, distciiuer ou copies of this thesis in microform, vendre des copies de cette these sous paper or electronic formats. la forme de microfiche/f&n, de reproduction sur papier ou sur format Bectronique. -

A Visual Motion Detection Circuit Suggested by Drosophila Connectomics
ARTICLE doi:10.1038/nature12450 A visual motion detection circuit suggested by Drosophila connectomics Shin-ya Takemura1, Arjun Bharioke1, Zhiyuan Lu1,2, Aljoscha Nern1, Shiv Vitaladevuni1, Patricia K. Rivlin1, William T. Katz1, Donald J. Olbris1, Stephen M. Plaza1, Philip Winston1, Ting Zhao1, Jane Anne Horne2, Richard D. Fetter1, Satoko Takemura1, Katerina Blazek1, Lei-Ann Chang1, Omotara Ogundeyi1, Mathew A. Saunders1, Victor Shapiro1, Christopher Sigmund1, Gerald M. Rubin1, Louis K. Scheffer1, Ian A. Meinertzhagen1,2 & Dmitri B. Chklovskii1 Animal behaviour arises from computations in neuronal circuits, but our understanding of these computations has been frustrated by the lack of detailed synaptic connection maps, or connectomes. For example, despite intensive investigations over half a century, the neuronal implementation of local motion detection in the insect visual system remains elusive. Here we develop a semi-automated pipeline using electron microscopy to reconstruct a connectome, containing 379 neurons and 8,637 chemical synaptic contacts, within the Drosophila optic medulla. By matching reconstructed neurons to examples from light microscopy, we assigned neurons to cell types and assembled a connectome of the repeating module of the medulla. Within this module, we identified cell types constituting a motion detection circuit, and showed that the connections onto individual motion-sensitive neurons in this circuit were consistent with their direction selectivity. Our results identify cellular targets for future functional investigations, and demonstrate that connectomes can provide key insights into neuronal computations. Vision in insects has been subject to intense behavioural1,physiological2 neuroanatomy14. Given the time-consuming nature of such recon- and anatomical3 investigations, yet our understanding of its underlying structions, we wanted to determine the smallest medulla volume, neural computations is still far from complete. -

Framing Youth Suicide in a Multi-Mediated World: the Construction of the Bridgend Problem in the British National Press
City Research Online City, University of London Institutional Repository Citation: Akrivos, Dimitrios (2015). Framing youth suicide in a multi-mediated world: the construction of the Bridgend problem in the British national press. (Unpublished Doctoral thesis, City University London) This is the accepted version of the paper. This version of the publication may differ from the final published version. Permanent repository link: https://openaccess.city.ac.uk/id/eprint/13648/ Link to published version: Copyright: City Research Online aims to make research outputs of City, University of London available to a wider audience. Copyright and Moral Rights remain with the author(s) and/or copyright holders. URLs from City Research Online may be freely distributed and linked to. Reuse: Copies of full items can be used for personal research or study, educational, or not-for-profit purposes without prior permission or charge. Provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way. City Research Online: http://openaccess.city.ac.uk/ [email protected] FRAMING YOUTH SUICIDE IN A MULTI-MEDIATED WORLD THE CONSTRUCTION OF THE BRIDGEND PROBLEM IN THE BRITISH NATIONAL PRESS DIMITRIOS AKRIVOS PhD Thesis CITY UNIVERSITY LONDON DEPARTMENT OF SOCIOLOGY SCHOOL OF ARTS AND SOCIAL SCIENCES 2015 THE FOLLOWING PARTS OF THIS THESIS HAVE BEEN REDACTED FOR COPYRIGHT REASONS: p15, Fig 1.1 p214, Fig 8.8 p16, Fig 1.2 p216, Fig 8.9 p17, Fig -

Fossil Corals As an Archive of Secular Variations in Seawater Chemistry Since the Mesozoic
Available online at www.sciencedirect.com ScienceDirect Geochimica et Cosmochimica Acta 160 (2015) 188–208 www.elsevier.com/locate/gca Fossil corals as an archive of secular variations in seawater chemistry since the Mesozoic Anne M. Gothmann a,⇑, Jarosław Stolarski b, Jess F. Adkins c, Blair Schoene a, Kate J. Dennis a, Daniel P. Schrag d, Maciej Mazur e, Michael L. Bender a a Princeton University, Geosciences, Princeton, NJ, United States b Institute of Paleobiology, Polish Academy of Sciences, Warsaw, Poland c California Institute of Technology, Geological and Planetary Sciences, Pasadena, CA, United States d Harvard University, Earth and Planetary Sciences, Cambridge, MA, United States e University of Warsaw, Department of Chemistry, Warsaw, Poland Received 17 July 2014; accepted in revised form 16 March 2015; available online 25 March 2015 Abstract Numerous archives suggest that the major ion and isotopic composition of seawater have changed in parallel with large variations in geologic processes and Earth’s climate. However, our understanding of the mechanisms driving secular changes in seawater chemistry on geologic timescales is limited by the resolution of data in time, large uncertainties in seawater chem- istry reconstructions, and ambiguities introduced by sample diagenesis. We validated the preservation of a suite of 60 unrecrystallized aragonitic fossil scleractinian corals, ranging in age from Triassic through Recent, for use as new archives of past seawater chemistry. Optical and secondary electron microscopy (SEM) studies reveal that fossil coral crystal fabrics are similar to those of modern coralline aragonite. X-ray diffractometry (XRD), cathodoluminescence microscopy (CL), and Raman studies confirm that these specimens contain little to no secondary calcite. -

Michigan-Specific Reporting Requirements
Version: February 28, 2020 MEDICARE-MEDICAID CAPITATED FINANCIAL ALIGNMENT MODEL REPORTING REQUIREMENTS: MICHIGAN-SPECIFIC REPORTING REQUIREMENTS Issued February 28, 2020 MI-1 Version: February 28, 2020 Table of Contents Michigan-Specific Reporting Requirements Appendix ......................................... MI-3 Introduction ....................................................................................................... MI-3 Definitions .......................................................................................................... MI-3 Variations from the Core Reporting Requirements Document ..................... MI-4 Quality Withhold Measures .............................................................................. MI-5 Reporting on Assessments and IICSPs Completed Prior to First Effective Enrollment Date ................................................................................. MI-6 Guidance on Assessments and IICSPs for Members with a Break in Coverage ............................................................................................................ MI-6 Reporting on Passively Enrolled and Opt-In Enrolled Members .................. MI-8 Reporting on Disenrolled and Retro-disenrolled Members ........................... MI-9 Hybrid Sampling ................................................................................................ MI-9 Value Sets ........................................................................................................ MI-10 Michigan’s Implementation, Ongoing, -

The Baghdad Set
The Baghdad Set Also by Adrian O’Sullivan: Nazi Secret Warfare in Occupied Persia (Iran): The Failure of the German Intelligence Services, 1939–45 (Palgrave, 2014) Espionage and Counterintelligence in Occupied Persia (Iran): The Success of the Allied Secret Services, 1941–45 (Palgrave, 2015) Adrian O’Sullivan The Baghdad Set Iraq through the Eyes of British Intelligence, 1941–45 Adrian O’Sullivan West Vancouver, BC, Canada ISBN 978-3-030-15182-9 ISBN 978-3-030-15183-6 (eBook) https://doi.org/10.1007/978-3-030-15183-6 Library of Congress Control Number: 2019934733 © The Editor(s) (if applicable) and The Author(s), under exclusive licence to Springer Nature Switzerland AG 2019 This work is subject to copyright. All rights are solely and exclusively licensed by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the pub- lisher nor the authors or the editors give a warranty, express or implied, with respect to the material contained herein or for any errors or omissions that may have been made. -

Monday/Tuesday Playoff Schedule
2013 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey1 Hockey2 Hockey3 Hockey4 Hockey5 Ulti A Soccer 3A Soccer 3B Cricket E1 Cricket E2 Cricket N1 Cricket N2 Field X 8:00 9:15 MI13 MI14 TI13 TI14 TI15 TI16 MI1 MI2 MI3 MI4 MI15 MI16 9:20 10:35 MI17 MI18 TI17 TI18 TI19 TI20 MI5 MI6 10:40 11:55 MI19 MI20 MC1 MC2 MC3 MI21 MI7 MI8 12:00 1:15 MI9* TI21* TI22 TI23 TI24 MI10 MI11 MI12 1:20 2:35 MI22 MC4 MC6 MC5 MI23 TC1 MI24 MI25 2:40 3:55 TI1 TI2 MC7 TI3 MI26 TC2 TR1 TR2 MI27 4:00 5:15 MC8* TC3 MC10 MC9 TI4 TC4 TR3 TR4 5:20 6:35 TC5* TI5 TI6 TI7 TI8 TC6 TR5 TR6 6:40 7:55 TI9* TC7 TI10 TI11 TI12 TC8 TR8 TR7 Games are to 15 points Half time at 8 points Games are 1 hour and 15 minutes long Soft cap is 10 minutes before the end of game, +1 to highest score 2 Timeouts per team, per game NO TIMEOUTS AFTER SOFT CAP Footblocks not allowed, unless captains agree otherwise 2013 TUC Monday Competitive Playoffs - 1st to 7th Place 3rd Place Bracket Loser of MC4 Competitive Teams Winner of MC9 MC9 Allth Darth (1) Allth Darth (1) 3rd Place Slam Dunks (2) Loser of MC5 The Ligers (3) Winner of MC4 MC4 Krash Kart (4) Krash Kart (4) The El Guapo Sausage Party (5) MC1 Wonky Pooh (6) Winner of MC1 Disc Horde (7) The El Guapo Sausage Winner of MC8 Party (5) MC8 Slam Dunks (2) Champions Winner of MC2 MC2 Disc Horde (7) MC5 The Ligers (3) Winner of MC5 MC3 Winner of MC3 Wonky Pooh (6) Time Hockey3 Score Spirit Hockey4 Score Spirit Hockey5 Score Spirit Score Spirit 10:40 Krash Kart (4) Slam Dunks (2) The Ligers (3) to vs.