Bit Manipulation in C and C++
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ADSP-21065L SHARC User's Manual; Chapter 2, Computation
&20387$7,2181,76 Figure 2-0. Table 2-0. Listing 2-0. The processor’s computation units provide the numeric processing power for performing DSP algorithms, performing operations on both fixed-point and floating-point numbers. Each computation unit executes instructions in a single cycle. The processor contains three computation units: • An arithmetic/logic unit (ALU) Performs a standard set of arithmetic and logic operations in both fixed-point and floating-point formats. • A multiplier Performs floating-point and fixed-point multiplication as well as fixed-point dual multiply/add or multiply/subtract operations. •A shifter Performs logical and arithmetic shifts, bit manipulation, field deposit and extraction operations on 32-bit operands and can derive exponents as well. ADSP-21065L SHARC User’s Manual 2-1 PM Data Bus DM Data Bus Register File Multiplier Shifter ALU 16 × 40-bit MR2 MR1 MR0 Figure 2-1. Computation units block diagram The computation units are architecturally arranged in parallel, as shown in Figure 2-1. The output from any computation unit can be input to any computation unit on the next cycle. The computation units store input operands and results locally in a ten-port register file. The Register File is accessible to the processor’s pro- gram memory data (PMD) bus and its data memory data (DMD) bus. Both of these buses transfer data between the computation units and internal memory, external memory, or other parts of the processor. This chapter covers these topics: • Data formats • Register File data storage and transfers -

Pdp11-40.Pdf
processor handbook digital equipment corporation Copyright© 1972, by Digital Equipment Corporation DEC, PDP, UNIBUS are registered trademarks of Digital Equipment Corporation. ii TABLE OF CONTENTS CHAPTER 1 INTRODUCTION 1·1 1.1 GENERAL ............................................. 1·1 1.2 GENERAL CHARACTERISTICS . 1·2 1.2.1 The UNIBUS ..... 1·2 1.2.2 Central Processor 1·3 1.2.3 Memories ........... 1·5 1.2.4 Floating Point ... 1·5 1.2.5 Memory Management .............................. .. 1·5 1.3 PERIPHERALS/OPTIONS ......................................... 1·5 1.3.1 1/0 Devices .......... .................................. 1·6 1.3.2 Storage Devices ...................................... .. 1·6 1.3.3 Bus Options .............................................. 1·6 1.4 SOFTWARE ..... .... ........................................... ............. 1·6 1.4.1 Paper Tape Software .......................................... 1·7 1.4.2 Disk Operating System Software ........................ 1·7 1.4.3 Higher Level Languages ................................... .. 1·7 1.5 NUMBER SYSTEMS ..................................... 1-7 CHAPTER 2 SYSTEM ARCHITECTURE. 2-1 2.1 SYSTEM DEFINITION .............. 2·1 2.2 UNIBUS ......................................... 2-1 2.2.1 Bidirectional Lines ...... 2-1 2.2.2 Master-Slave Relation .. 2-2 2.2.3 Interlocked Communication 2-2 2.3 CENTRAL PROCESSOR .......... 2-2 2.3.1 General Registers ... 2-3 2.3.2 Processor Status Word ....... 2-4 2.3.3 Stack Limit Register 2-5 2.4 EXTENDED INSTRUCTION SET & FLOATING POINT .. 2-5 2.5 CORE MEMORY . .... 2-6 2.6 AUTOMATIC PRIORITY INTERRUPTS .... 2-7 2.6.1 Using the Interrupts . 2-9 2.6.2 Interrupt Procedure 2-9 2.6.3 Interrupt Servicing ............ .. 2-10 2.7 PROCESSOR TRAPS ............ 2-10 2.7.1 Power Failure .............. -

Most Computer Instructions Can Be Classified Into Three Categories
Introduction: Data Transfer and Manipulation Most computer instructions can be classified into three categories: 1) Data transfer, 2) Data manipulation, 3) Program control instructions » Data transfer instruction cause transfer of data from one location to another » Data manipulation performs arithmatic, logic and shift operations. » Program control instructions provide decision making capabilities and change the path taken by the program when executed in computer. Data Transfer Instruction Typical Data Transfer Instruction : LD » Load : transfer from memory to a processor register, usually an AC (memory read) ST » Store : transfer from a processor register into memory (memory write) MOV » Move : transfer from one register to another register XCH » Exchange : swap information between two registers or a register and a memory word IN/OUT » Input/Output : transfer data among processor registers and input/output device PUSH/POP » Push/Pop : transfer data between processor registers and a memory stack MODE ASSEMBLY REGISTER TRANSFER CONVENTION Direct Address LD ADR ACM[ADR] Indirect Address LD @ADR ACM[M[ADR]] Relative Address LD $ADR ACM[PC+ADR] Immediate Address LD #NBR ACNBR Index Address LD ADR(X) ACM[ADR+XR] Register LD R1 ACR1 Register Indirect LD (R1) ACM[R1] Autoincrement LD (R1)+ ACM[R1], R1R1+1 8 Addressing Mode for the LOAD Instruction Data Manipulation Instruction 1) Arithmetic, 2) Logical and bit manipulation, 3) Shift Instruction Arithmetic Instructions : NAME MNEMONIC Increment INC Decrement DEC Add ADD Subtract SUB Multiply -

Lecture 04 Linear Structures Sort
Algorithmics (6EAP) MTAT.03.238 Linear structures, sorting, searching, etc Jaak Vilo 2018 Fall Jaak Vilo 1 Big-Oh notation classes Class Informal Intuition Analogy f(n) ∈ ο ( g(n) ) f is dominated by g Strictly below < f(n) ∈ O( g(n) ) Bounded from above Upper bound ≤ f(n) ∈ Θ( g(n) ) Bounded from “equal to” = above and below f(n) ∈ Ω( g(n) ) Bounded from below Lower bound ≥ f(n) ∈ ω( g(n) ) f dominates g Strictly above > Conclusions • Algorithm complexity deals with the behavior in the long-term – worst case -- typical – average case -- quite hard – best case -- bogus, cheating • In practice, long-term sometimes not necessary – E.g. for sorting 20 elements, you dont need fancy algorithms… Linear, sequential, ordered, list … Memory, disk, tape etc – is an ordered sequentially addressed media. Physical ordered list ~ array • Memory /address/ – Garbage collection • Files (character/byte list/lines in text file,…) • Disk – Disk fragmentation Linear data structures: Arrays • Array • Hashed array tree • Bidirectional map • Heightmap • Bit array • Lookup table • Bit field • Matrix • Bitboard • Parallel array • Bitmap • Sorted array • Circular buffer • Sparse array • Control table • Sparse matrix • Image • Iliffe vector • Dynamic array • Variable-length array • Gap buffer Linear data structures: Lists • Doubly linked list • Array list • Xor linked list • Linked list • Zipper • Self-organizing list • Doubly connected edge • Skip list list • Unrolled linked list • Difference list • VList Lists: Array 0 1 size MAX_SIZE-1 3 6 7 5 2 L = int[MAX_SIZE] -
Specification of Bit Handling Routines AUTOSAR CP Release 4.3.1
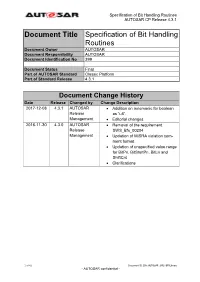
Specification of Bit Handling Routines AUTOSAR CP Release 4.3.1 Document Title Specification of Bit Handling Routines Document Owner AUTOSAR Document Responsibility AUTOSAR Document Identification No 399 Document Status Final Part of AUTOSAR Standard Classic Platform Part of Standard Release 4.3.1 Document Change History Date Release Changed by Change Description 2017-12-08 4.3.1 AUTOSAR Addition on mnemonic for boolean Release as “u8”. Management Editorial changes 2016-11-30 4.3.0 AUTOSAR Removal of the requirement Release SWS_Bfx_00204 Management Updation of MISRA violation com- ment format Updation of unspecified value range for BitPn, BitStartPn, BitLn and ShiftCnt Clarifications 1 of 42 Document ID 399: AUTOSAR_SWS_BFXLibrary - AUTOSAR confidential - Specification of Bit Handling Routines AUTOSAR CP Release 4.3.1 Document Change History Date Release Changed by Change Description 2015-07-31 4.2.2 AUTOSAR Updated SWS_Bfx_00017 for the Release return type of Bfx_GetBit function Management from 1 and 0 to TRUE and FALSE Updated chapter 8.1 for the defini- tion of bit addressing and updated the examples of Bfx_SetBit, Bfx_ClrBit, Bfx_GetBit, Bfx_SetBits, Bfx_CopyBit, Bfx_PutBits, Bfx_PutBit Updated SWS_Bfx_00017 for the return type of Bfx_GetBit function from 1 and 0 to TRUE and FALSE without changing the formula Updated SWS_Bfx_00011 and SWS_Bfx_00022 for the review comments provided for the exam- ples In Table 2, replaced Boolean with boolean In SWS_Bfx_00029, in example re- placed BFX_GetBits_u16u8u8_u16 with Bfx_GetBits_u16u8u8_u16 2014-10-31 4.2.1 AUTOSAR Correct usage of const in function Release declarations Management Editoral changes 2014-03-31 4.1.3 AUTOSAR Editoral changes Release Management 2013-10-31 4.1.2 AUTOSAR Improve description of how to map Release functions to C-files Management Improve the definition of error classi- fication Editorial changes 2013-03-15 4.1.1 AUTOSAR Change return value of Test Bit API Administration to boolean. -

RISC-V Bitmanip Extension Document Version 0.90
RISC-V Bitmanip Extension Document Version 0.90 Editor: Clifford Wolf Symbiotic GmbH [email protected] June 10, 2019 Contributors to all versions of the spec in alphabetical order (please contact editors to suggest corrections): Jacob Bachmeyer, Allen Baum, Alex Bradbury, Steven Braeger, Rogier Brussee, Michael Clark, Ken Dockser, Paul Donahue, Dennis Ferguson, Fabian Giesen, John Hauser, Robert Henry, Bruce Hoult, Po-wei Huang, Rex McCrary, Lee Moore, Jiˇr´ıMoravec, Samuel Neves, Markus Oberhumer, Nils Pipenbrinck, Xue Saw, Tommy Thorn, Andrew Waterman, Thomas Wicki, and Clifford Wolf. This document is released under a Creative Commons Attribution 4.0 International License. Contents 1 Introduction 1 1.1 ISA Extension Proposal Design Criteria . .1 1.2 B Extension Adoption Strategy . .2 1.3 Next steps . .2 2 RISC-V Bitmanip Extension 3 2.1 Basic bit manipulation instructions . .4 2.1.1 Count Leading/Trailing Zeros (clz, ctz)....................4 2.1.2 Count Bits Set (pcnt)...............................5 2.1.3 Logic-with-negate (andn, orn, xnor).......................5 2.1.4 Pack two XLEN/2 words in one register (pack).................6 2.1.5 Min/max instructions (min, max, minu, maxu)................7 2.1.6 Single-bit instructions (sbset, sbclr, sbinv, sbext)............8 2.1.7 Shift Ones (Left/Right) (slo, sloi, sro, sroi)...............9 2.2 Bit permutation instructions . 10 2.2.1 Rotate (Left/Right) (rol, ror, rori)..................... 10 2.2.2 Generalized Reverse (grev, grevi)....................... 11 2.2.3 Generalized Shuffleshfl ( , unshfl, shfli, unshfli).............. 14 2.3 Bit Extract/Deposit (bext, bdep)............................ 22 2.4 Carry-less multiply (clmul, clmulh, clmulr).................... -

The Central Processor Unit
Systems Architecture The Central Processing Unit The Central Processing Unit – p. 1/11 The Computer System Application High-level Language Operating System Assembly Language Machine level Microprogram Digital logic Hardware / Software Interface The Central Processing Unit – p. 2/11 CPU Structure External Memory MAR: Memory MBR: Memory Address Register Buffer Register Address Incrementer R15 / PC R11 R7 R3 R14 / LR R10 R6 R2 R13 / SP R9 R5 R1 R12 R8 R4 R0 User Registers Booth’s Multiplier Barrel IR Shifter Control Unit CPSR 32-Bit ALU The Central Processing Unit – p. 3/11 CPU Registers Internal Registers Condition Flags PC Program Counter C Carry IR Instruction Register Z Zero MAR Memory Address Register N Negative MBR Memory Buffer Register V Overflow CPSR Current Processor Status Register Internal Devices User Registers ALU Arithmetic Logic Unit Rn Register n CU Control Unit n = 0 . 15 M Memory Store SP Stack Pointer MMU Mem Management Unit LR Link Register Note that each CPU has a different set of User Registers The Central Processing Unit – p. 4/11 Current Process Status Register • Holds a number of status flags: N True if result of last operation is Negative Z True if result of last operation was Zero or equal C True if an unsigned borrow (Carry over) occurred Value of last bit shifted V True if a signed borrow (oVerflow) occurred • Current execution mode: User Normal “user” program execution mode System Privileged operating system tasks Some operations can only be preformed in a System mode The Central Processing Unit – p. 5/11 Register Transfer Language NAME Value of register or unit ← Transfer of data MAR ← PC x: Guard, only if x true hcci: MAR ← PC (field) Specific field of unit ALU(C) ← 1 (name), bit (n) or range (n:m) R0 ← MBR(0:7) Rn User Register n R0 ← MBR num Decimal number R0 ← 128 2_num Binary number R1 ← 2_0100 0001 0xnum Hexadecimal number R2 ← 0x40 M(addr) Memory Access (addr) MBR ← M(MAR) IR(field) Specified field of IR CU ← IR(op-code) ALU(field) Specified field of the ALU(C) ← 1 Arithmetic and Logic Unit The Central Processing Unit – p. -

KTS-A Memory Management Control User's Guide Digital Equipment Corporation • Maynard, Massachusetts
--- KTS-A memory management control user's guide E K- KTOSA-U G-001 digital equipment corporation • maynard, massachusetts 1st Edition , July 1978 Copyright © 1978 by Digital Equipment Corporation The material in this manual is for informational purposes and is subject to change without notice. Digital Equipment Corporation assumes no responsibility for any errors which may appear in this manual. Printed in U.S.A. This document was set on DIGITAL's DECset-8000 com puterized typesetting system. The following are trademarks of Digital Equipment Corporation, Maynard, Massachusetts: DIGITAL D ECsystem-10 MASSBUS DEC DECSYSTEM-20 OMNIBUS POP DIBOL OS/8 DECUS EDUSYSTEM RSTS UNI BUS VAX RSX VMS IAS CONTENTS Page CHAPTER 1 INTRODUCTION 1 . 1 SCOPE OF MANUAL ..................................................................................................................... 1-1 1.2 GENERAL DESCRI PTION ............................................................................................................. 1-1 1 .3 KT8-A SPECIFICATION S.............................................................................................................. 1-3 1.4 RELATED DOCUMENTS ............................................................................................................... 1-4 1 .5 SOFTWARE ..................................................................................................................................... 1-5 1.5.1 Diagnostic ............................................................................................................................. -

Reference Guide for X86-64 Cpus
REFERENCE GUIDE FOR X86-64 CPUS Version 2019 TABLE OF CONTENTS Preface............................................................................................................. xi Audience Description.......................................................................................... xi Compatibility and Conformance to Standards............................................................ xi Organization....................................................................................................xii Hardware and Software Constraints...................................................................... xiii Conventions....................................................................................................xiii Terms............................................................................................................xiv Related Publications.......................................................................................... xv Chapter 1. Fortran, C, and C++ Data Types................................................................ 1 1.1. Fortran Data Types....................................................................................... 1 1.1.1. Fortran Scalars.......................................................................................1 1.1.2. FORTRAN real(2).....................................................................................3 1.1.3. FORTRAN 77 Aggregate Data Type Extensions.................................................. 3 1.1.4. Fortran 90 Aggregate Data Types (Derived -

X86 Intrinsics Cheat Sheet Jan Finis [email protected]
x86 Intrinsics Cheat Sheet Jan Finis [email protected] Bit Operations Conversions Boolean Logic Bit Shifting & Rotation Packed Conversions Convert all elements in a packed SSE register Reinterpet Casts Rounding Arithmetic Logic Shift Convert Float See also: Conversion to int Rotate Left/ Pack With S/D/I32 performs rounding implicitly Bool XOR Bool AND Bool NOT AND Bool OR Right Sign Extend Zero Extend 128bit Cast Shift Right Left/Right ≤64 16bit ↔ 32bit Saturation Conversion 128 SSE SSE SSE SSE Round up SSE2 xor SSE2 and SSE2 andnot SSE2 or SSE2 sra[i] SSE2 sl/rl[i] x86 _[l]rot[w]l/r CVT16 cvtX_Y SSE4.1 cvtX_Y SSE4.1 cvtX_Y SSE2 castX_Y si128,ps[SSE],pd si128,ps[SSE],pd si128,ps[SSE],pd si128,ps[SSE],pd epi16-64 epi16-64 (u16-64) ph ↔ ps SSE2 pack[u]s epi8-32 epu8-32 → epi8-32 SSE2 cvt[t]X_Y si128,ps/d (ceiling) mi xor_si128(mi a,mi b) mi and_si128(mi a,mi b) mi andnot_si128(mi a,mi b) mi or_si128(mi a,mi b) NOTE: Shifts elements right NOTE: Shifts elements left/ NOTE: Rotates bits in a left/ NOTE: Converts between 4x epi16,epi32 NOTE: Sign extends each NOTE: Zero extends each epi32,ps/d NOTE: Reinterpret casts !a & b while shifting in sign bits. right while shifting in zeros. right by a number of bits 16 bit floats and 4x 32 bit element from X to Y. Y must element from X to Y. Y must from X to Y. No operation is SSE4.1 ceil NOTE: Packs ints from two NOTE: Converts packed generated. -

Bit Manipulation
jhtp_appK_BitManipulation.fm Page 1 Tuesday, April 11, 2017 12:28 PM K Bit Manipulation K.1 Introduction This appendix presents an extensive discussion of bit-manipulation operators, followed by a discussion of class BitSet, which enables the creation of bit-array-like objects for setting and getting individual bit values. Java provides extensive bit-manipulation capabilities for programmers who need to get down to the “bits-and-bytes” level. Operating systems, test equipment software, networking software and many other kinds of software require that the programmer communicate “directly with the hardware.” We now discuss Java’s bit- manipulation capabilities and bitwise operators. K.2 Bit Manipulation and the Bitwise Operators Computers represent all data internally as sequences of bits. Each bit can assume the value 0 or the value 1. On most systems, a sequence of eight bits forms a byte—the standard storage unit for a variable of type byte. Other types are stored in larger numbers of bytes. The bitwise operators can manipulate the bits of integral operands (i.e., operations of type byte, char, short, int and long), but not floating-point operands. The discussions of bit- wise operators in this section show the binary representations of the integer operands. The bitwise operators are bitwise AND (&), bitwise inclusive OR (|), bitwise exclu- sive OR (^), left shift (<<), signed right shift (>>), unsigned right shift (>>>) and bitwise complement (~). The bitwise AND, bitwise inclusive OR and bitwise exclusive OR oper- ators compare their two operands bit by bit. The bitwise AND operator sets each bit in the result to 1 if and only if the corresponding bit in both operands is 1. -

Bit-Level Transformation and Optimization for Hardware
Bit-Level Transformation and Optimization for Hardware Synthesis of Algorithmic Descriptions Jiyu Zhang*† , Zhiru Zhang+, Sheng Zhou+, Mingxing Tan*, Xianhua Liu*, Xu Cheng*, Jason Cong† *MicroProcessor Research and Development Center, Peking University, Beijing, PRC † Computer Science Department, University Of California, Los Angeles, CA 90095, USA +AutoESL Design Technologies, Los Angeles, CA 90064, USA {zhangjiyu, tanmingxing, liuxianhua, chengxu}@mprc.pku.edu.cn {zhiruz, zhousheng}@autoesl.com, [email protected] ABSTRACT and more popularity [3-6]. However, high-quality As the complexity of integrated circuit systems implementations are difficult to achieve automatically, increases, automated hardware design from higher- especially when the description of the functionality is level abstraction is becoming more and more important. written in a high-level software programming language. However, for many high-level programming languages, For bitwise computation-intensive applications, one of such as C/C++, the description of bitwise access and the main difficulties is the lack of bit-accurate computation is not as direct as hardware description descriptions in high-level software programming languages, and hardware synthesis of algorithmic languages. The wide use of bitwise operations in descriptions may generate sub-optimal implement- certain application domains calls for specific bit-level tations for bitwise computation-intensive applications. transformation and optimization to assist hardware In this paper we introduce a bit-level