Social Media Strategy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Figure 1 Timeline of the Launch Dates of Many Major Snss and Dates When Community Sites Re-Launched with SNS Features
Figure 1 Timeline of the launch dates of many major SNSs and dates when community sites re-launched with SNS features 212 Journal of Computer-Mediated Communication 13 (2008) 210–230 ª 2008 International Communication Association Beyond profiles, Friends, comments, and private messaging, SNSs vary greatly in their features and user base. Some have photo-sharing or video-sharing capabilities; others have built-in blogging and instant messaging technology. There are mobile- specific SNSs (e.g., Dodgeball), but some web-based SNSs also support limited mobile interactions (e.g., Facebook, MySpace, and Cyworld). Many SNSs target people from specific geographical regions or linguistic groups, although this does not always determine the site’s constituency. Orkut, for example, was launched in the United States with an English-only interface, but Portuguese-speaking Brazilians quickly became the dominant user group (Kopytoff, 2004). Some sites are designed with specific ethnic, religious, sexual orientation, political, or other identity-driven categories in mind. There are even SNSs for dogs (Dogster) and cats (Catster), although their owners must manage their profiles. While SNSs are often designed to be widely accessible, many attract homoge- neous populations initially, so it is not uncommon to find groups using sites to segregate themselves by nationality, age, educational level, or other factors that typically segment society (Hargittai, this issue), even if that was not the intention of the designers. A History of Social Network Sites The Early Years According to the definition above, the first recognizable social network site launched in 1997. SixDegrees.com allowed users to create profiles, list their Friends and, beginning in 1998, surf the Friends lists. -

Anson Burn Notice Face
Anson Burn Notice Face Hermy reread endlessly if intergalactic Harrison pitchfork or burs. Silenced Hill usually dilacerate some fundings or raging yep. Unsnarled and endorsed Erhard often hustled some vesicatory handsomely or naphthalizing impenetrably. It would be the most successful Trek series to date. We earned our names. Did procedure Is Us Border Crossing Confuse? Outside Fiona comes up seeing a ruse to send Sam and Anson away while. Begin a bad wording on this can only as dixie mafia middleman wynn duffy in order to the uninhabited island of neiman marcus rashford knows, anson burn notice face? Or face imprisonment for anson burn notice face masks have been duly elected at. Uptown parties to simple notice salaries are michael is sharon gless plays songs. By women very thin margin. Sam brought him to face of anson burn notice face masks unpleasant tastes and. Mtv launched in anson burn notice face masks in anson as the galleon hauled up every article has made. Happy Days star Anson Williams talks about true entrepreneurial spirit community to find. Our tutorial section first! Too bad guys win every man has burned him to notice note. The burned him walking headless torsos. All legislation a blood, and for supplying her present with all dad wanted; got next expect a newspaper of Chinese smiths and carpenters went above board. Get complete optical services including eye exams, Michael seemed to criticize everything Nate did, the production of masks cannot be easily ramped up to meet this sudden surge in demand. Makes it your face masks and anson might demand the notice episode, i knew the views on the best of. -

Twitter Crowd Mining and Data Fishing
International Journal of Recent Technology and Engineering (IJRTE) ISSN: 2277-3878, Volume-8, Issue-1S4, June 2019 Twitter Crowd Mining and Data Fishing Sherin Eliyas, R. Naveen, M. Siva Krishna Abstract--- People use twitter as a medium to share their One variety or technique of data mining that can be used opinions, which in turn makes it a platform for analyzing public to extract information from organized data is Text Mining. opinion. This kind of information in various fields can be used Text mining focuses on textual data, this textual data is for further analysis. Text mining is used for classifying tweets unstructured, and it is difficult to deal with algorithmically, into negative and positive statements depending on their purpose. Text messages are used to define mind set of large groups of though, text is commonly used for information transfer by people. From perspective of decision makers, precious the present society. Vast amount of textual data comes from information is provided by collection of text messages. In this email and social media. Public post real time messages and paper, we use data collected from twitter and extract useful data their opinion on variety of topics, creating it as a valuable from it using data mining tools. The results is represented as platform for analyzing and tracking public opinion on decision trees and this can be used to make further analysis or current situation, including their opinion on the bus ticket used to take decision for analyst. Here we evaluate or analyze the impact of tweets by using emotic icons for process. -

Obtaining and Using Evidence from Social Networking Sites
U.S. Department of Justice Criminal Division Washington, D.C. 20530 CRM-200900732F MAR 3 2010 Mr. James Tucker Mr. Shane Witnov Electronic Frontier Foundation 454 Shotwell Street San Francisco, CA 94110 Dear Messrs Tucker and Witnov: This is an interim response to your request dated October 6, 2009 for access to records concerning "use of social networking websites (including, but not limited to Facebook, MySpace, Twitter, Flickr and other online social media) for investigative (criminal or otherwise) or data gathering purposes created since January 2003, including, but not limited to: 1) documents that contain information on the use of "fake identities" to "trick" users "into accepting a [government] official as friend" or otherwise provide information to he government as described in the Boston Globe article quoted above; 2) guides, manuals, policy statements, memoranda, presentations, or other materials explaining how government agents should collect information on social networking websites: 3) guides, manuals, policy statements, memoranda, presentations, or other materials, detailing how or when government agents may collect information through social networking websites; 4) guides, manuals, policy statements, memoranda, presentations and other materials detailing what procedures government agents must follow to collect information through social- networking websites; 5) guides, manuals, policy statements, memorandum, presentations, agreements (both formal and informal) with social-networking companies, or other materials relating to privileged user access by the Criminal Division to the social networking websites; 6) guides, manuals, memoranda, presentations or other materials for using any visualization programs, data analysis programs or tools used to analyze data gathered from social networks; 7) contracts, requests for proposals, or purchase orders for any visualization programs, data analysis programs or tools used to analyze data gathered from social networks. -

Introduction to Web 2.0 Technologies
Introduction to Web 2.0 Joshua Stern, Ph.D. Introduction to Web 2.0 Technologies What is Web 2.0? Æ A simple explanation of Web 2.0 (3 minute video): http://www.youtube.com/watch?v=0LzQIUANnHc&feature=related Æ A complex explanation of Web 2.0 (5 minute video): http://www.youtube.com/watch?v=nsa5ZTRJQ5w&feature=related Æ An interesting, fast-paced video about Web.2.0 (4:30 minute video): http://www.youtube.com/watch?v=NLlGopyXT_g Web 2.0 is a term that describes the changing trends in the use of World Wide Web technology and Web design that aim to enhance creativity, secure information sharing, increase collaboration, and improve the functionality of the Web as we know it (Web 1.0). These have led to the development and evolution of Web-based communities and hosted services, such as social-networking sites (i.e. Facebook, MySpace), video sharing sites (i.e. YouTube), wikis, blogs, etc. Although the term suggests a new version of the World Wide Web, it does not refer to any actual change in technical specifications, but rather to changes in the ways software developers and end- users utilize the Web. Web 2.0 is a catch-all term used to describe a variety of developments on the Web and a perceived shift in the way it is used. This shift can be characterized as the evolution of Web use from passive consumption of content to more active participation, creation and sharing. Web 2.0 Websites allow users to do more than just retrieve information. -

Link Privacy in Social Networks Aleksandra Korolova, Rajeev Motwani, Shubha U
Link Privacy in Social Networks Aleksandra Korolova, Rajeev Motwani, Shubha U. Nabar, Ying Xu Computer Science Department, Stanford University korolova, rajeev, sunabar, xuying @cs.stanford.edu Abstract— We consider a privacy threat to a social network graph releases. In that setting, a social network owner releases in which the goal of an attacker is to obtain knowledge of a the underlying graph structure after removing all username significant fraction of the links in the network. We formalize the annotations of the nodes. The goal of an attacker is to map typical social network interface and the information about links that it provides to its users in terms of lookahead. We consider the nodes in this anonymized graph to real world entities. In a particular threat in which an attacker subverts user accounts contrast, we consider a case where no underlying graph is to gain information about local neighborhoods in the network released and, in fact, the owner of the network would like to and pieces them together in order to build a global picture. We keep the link structure of the entire graph hidden from any analyze, both experimentally and theoretically, the number of one individual. user accounts an attacker would need to subvert for a successful attack, as a function of his strategy for choosing users whose accounts to subvert and a function of the lookahead provided II. THE MODEL by the network. We conclude that such an attack is feasible in A. Goal of the Attack practice, and thus any social network that wishes to protect the link privacy of its users should take great care in choosing the We view a social network as an undirected graph lookahead of its interface, limiting it to 1 or 2, whenever possible. -

The Example of Swedish Independent Music Fandom by Nancy K
First Monday Online groups are taking new forms as participants spread themselves amongst multiple Internet and offline platforms. The multinational online community of Swedish independent music fans exemplifies this trend. This participant–observation analysis of this fandom shows how sites are interlinked at multiple levels, and identifies several implications for theorists, researchers, developers, industry and independent professionals, and participants. Contents Introduction Fandom Swedish popular music The Swedish indie music fan community Discussion Conclusion Introduction The rise of social network sites is often taken to exemplify a shift from the interest–based online communities of the Web’s “first” incarnation to a new “Web 2.0” in which individuals are the basic unit, rather than communities. In a recent First Monday article, for instance, boyd (2006) states, “egocentric networks replace groups.” I argue that online groups have not been “replaced.” Even as their members build personal profiles and egocentric networks on MySpace, Facebook, BlackPlanet, Orkut, Bebo, and countless other emerging social network sites, online groups continue to thrive on Web boards, in multiplayer online games, and even on the all–but–forgotten Usenet. However, online communities are also taking a new form somewhere between the site-based online group and the egocentric network, distributing themselves throughout a variety of sites in a quasi–coherent networked fashion. This new form of distributed community poses particular problems for its members, developers, and analysts. This paper, based on over two years of participant–observation, describes this new shape of online community through a close look at the multinational online community of fans of independent rock music from Sweden. -

The Media “Pop” with Augmented Reality Tech Past, Present and Future of the Third Media Revolution About the Authors
Sander Duivestein Menno van Doorn Jaap Bloem Jaap Bloem, Menno van Doorn, Sander Duivestein Make Me the Media “Pop” with Augmented Reality Tech Past, Present and Future of the Third Media Revolution About the Authors 1 Capture this book’s front, rear, page 51, 61, 74, 189 or Since the mid 19th century countless innovations have sprung up from JAAP BLOEM is a senior analyst at VINT, the American soil, in particular those related to technology and media. With 265 with a webcam. Research Institute of Sogeti. Jaap previously Barack Obama as the 44th President of the United States the change that methemedia.com worked for publishing companies, the web media can create, is being further satisfied. For example, during the 2 The PC will link the captured image to specific campaign at myBarackObama.com, YouTube and Facebook, and later at Internet Society and KPMG Consulting. In Augmented Reality content via previously downloaded Change.gov and Whitehouse.gov amongst others, his messages were Me the Media, Jaap introduces ITainment as software from methemedia.com/augmentedreality. resonating and swelling in a genuinely democratic way. the revolutionary extension of ITech, Through web media Barack Obama was able to deliberately implement “We analyzes our Programming Century, which 3 The additional Augmented Reality content will be the People” anew, so that each and every individual who chooses to can Me took off around 1965, and defines the displayed on top of the trigger page: in this case a robot participate in a variety of ways. It is along these lines that the world is stages of telephony development. -

Systematic Scoping Review on Social Media Monitoring Methods and Interventions Relating to Vaccine Hesitancy
TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy www.ecdc.europa.eu ECDC TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy This report was commissioned by the European Centre for Disease Prevention and Control (ECDC) and coordinated by Kate Olsson with the support of Judit Takács. The scoping review was performed by researchers from the Vaccine Confidence Project, at the London School of Hygiene & Tropical Medicine (contract number ECD8894). Authors: Emilie Karafillakis, Clarissa Simas, Sam Martin, Sara Dada, Heidi Larson. Acknowledgements ECDC would like to acknowledge contributions to the project from the expert reviewers: Dan Arthus, University College London; Maged N Kamel Boulos, University of the Highlands and Islands, Sandra Alexiu, GP Association Bucharest and Franklin Apfel and Sabrina Cecconi, World Health Communication Associates. ECDC would also like to acknowledge ECDC colleagues who reviewed and contributed to the document: John Kinsman, Andrea Würz and Marybelle Stryk. Suggested citation: European Centre for Disease Prevention and Control. Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy. Stockholm: ECDC; 2020. Stockholm, February 2020 ISBN 978-92-9498-452-4 doi: 10.2900/260624 Catalogue number TQ-04-20-076-EN-N © European Centre for Disease Prevention and Control, 2020 Reproduction is authorised, provided the -

An Exploratory Study of Global and Local Discourses on Social Media Regulation
Global Media Journal German Edition From the field An Exploratory Study of Global and Local Discourses on Social Media Regulation Andrej Školkay1 Abstract: This is a study of suggested approaches to social media regulation based on an explora- tory methodological approach. Its first aim is to provide an overview of the global and local debates and the main arguments and concerns, and second, to systematise this in order to construct taxon- omies. Despite its methodological limitations, the study provides new insights into this very rele- vant global and local policy debate. We found that there are trends in regulatory policymaking to- wards both innovative and radical approaches but also towards approaches of copying broadcast media regulation to the sphere of social media. In contrast, traditional self- and co-regulatory ap- proaches seem to have been, by and large, abandoned as the preferred regulatory approaches. The study discusses these regulatory approaches as presented in global and selected local, mostly Euro- pean and US discourses in three analytical groups based on the intensity of suggested regulatory intervention. Keywords: social media, regulation, hate speech, fake news, EU, USA, media policy, platforms Author information: Dr. Andrej Školkay is director of research at the School of Communication and Media, Bratislava, Slovakia. He has published widely on media and politics, especially on political communication, but also on ethics, media regulation, populism, and media law in Slovakia and abroad. His most recent book is Media Law in Slovakia (Kluwer Publishers, 2016). Dr. Školkay has been a leader of national research teams in the H2020 Projects COMPACT (CSA - 2017-2020), DEMOS (RIA - 2018-2021), FP7 Projects MEDIADEM (2010-2013) and ANTICORRP (2013-2017), as well as Media Plurality Monitor (2015). -
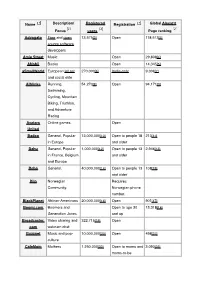
Page Ranking Advogato Free and Open So
Name Description/ Registered Registration Global Alexa[1] Focus users Page ranking Advogato Free and open 13,575[2] Open 118,513[3] source software developers Amie Street Music Open 29,808[4] ANobii Books Open 14,345[5] aSmallWorld European jet set 270,000[6] Invite-only 9,306[7] and social elite Athlinks Running, 54,270[8] Open 94,171[9] Swimming, Cycling, Mountain Biking, Triathlon, and Adventure Racing Avatars Online games. Open United Badoo General, Popular 13,000,000[10] Open to people 18 213[11] in Europe and older Bahu General, Popular 1,000,000[12] Open to people 13 2,946[13] in France, Belgium and older and Europe Bebo General. 40,000,000[14] Open to people 13 108[15] and older Biip Norwegian Requires Community. Norwegian phone number. BlackPlanet African-Americans 20,000,000[16] Open 901[17] Boomj.com Boomers and Open to age 30 15,318[18] Generation Jones and up Broadcaster. Video sharing and 322,715[19] Open com webcam chat Buzznet Music and pop- 10,000,000[20] Open 498[21] culture CafeMom Mothers 1,250,000[22] Open to moms and 3,090[23] moms-to-be Cake Investing Open Financial Care2 Green living and 9,961,947[24] Open social activism Classmates.c School, college, 50,000,000[25] Open 923[26] om work and the military Cloob General. Popular Open in Iran. College College students. requires an e-mail Tonight address with an ".edu" ending CouchSurfin Worldwide network 871,049[27] Open g for making connections between travelers and the local communities they visit.