January 2005
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Parade Opens City's Christmas Season Impersonation of Officer
0 1797 South Carolina's Oldest Newspaper 1962 (BtQt&tioton %imm OUT OF STATE $3.00 5c Per Copy Vol. No. 166 No. 6 SUBSCRIPTIONS: TN STATE $2.50 Georgetown, S. C, Thursday, Dec. 6, 1962 Parade Opens City's Christmas Season Santa Claus came to George Georgetown Junior Chamber of featured on a float of the Cham Barbara Moore and Barbara Pos- i youth accented by Front Street town Tuesday with a flair in tho Commerce, the Yuletide parade ber of Commerce - City of ton. also rode in the parade, ac-' Kindergarten youngsters. Brown largest Christmas parade ever was under the direction of a Jay Geoigetown singing a Christmas companied by tho present queen, ie. Girl and Boy Scout Troops. staged in Georgetown. cee committee headed by Glenn anthem. Other religious floats Joyce Nell Shelley. Band units included St. Mary's WOMEN OF MOOSE It. was a parade wiln a broad Goodman. Wen entered b.v Wayne Methodist Floats in the parade were en Drum and Bugle Corps. Winyah The Women of the Moose will accent, ranging from religious Leading oil the parade was Church and Condon's Department tered b.v the Georgetown Chamber High School Band. Howard High hold their Christmas party on scenes to marching tots, beauty Mayor L, L. Weed, followed b.v Store. of Commerce, Andrews Chamber School Band, and Andrews High Saturday, December 8, SK'9 P. M. queens and FHA sweethearts, the Winyah Band and Miss Riding on other tloats and curs of Commerce. Pleasant Hill Com- School Band. All Chapter members and their bands and scouts, a model guided Georgetown. -

Poemm Emoir Stor Y 2 01 6
poemm Number Fifteen/2016 Amy Bailey emoir Kimberly Ball Tina Barr Heather Bartlett Emily Rapp Black story M. L. Brown Grace Cho Casie Cook Melissa Crowe Jude Deason Mollie Hawkins Ashley Jones Kateema Lee Colleen J. McElroy Jamie McFaden Michelle McMillan-Holifield Samantha Pious Sharanna Polk Emily Rems Mary Ruefle Jacqueline Saphra Laura Secord Zhanna Slor Alina Stefanescu Julie Stewart Judith Teitleman Yellena Urazbaeva Gail White 2016 $10.00 .. PMSpoemmemoirstory 2016number fifteen Copyright © 2016 by PMS poemmemoirstory PMS poemmemoirstory appears once a year. We accept unpublished, orig- inal submissions of poetry, memoir, and short fiction during our January 1 through March 31 reading period. We accept simultaneous submis- sions; however, we ask that you please contact us immediately if your piece is published elsewhere so we may free up space for other authors. While PMS is a journal of exclusively women’s writing, the subject field is wide open. We strongly encourage you to familiarize yourself with PMS before submitting. You can find links on our Web site to some examples of what we publish in the pages of PMS 8, PMS 9, and PMS 14. We ask that you limit your submission to either five poems or 15 pages of prose (4,300 words or less). We look forward to reading your work. Please send all submissions to https://poemmemoirstory.submittable.com/submit. There is a $3 fee, which covers costs associated with our online submis- sions system. For any other correspondence, contact us at poemmemoirstory@gmail. com. PMS poemmemoirstory is a member of the Council of Literary Maga- zines and Presses (CLMP) and the Council of Editors of Learned Journals (CELJ). -

First Rated Drama Beyond the Realm of Conscience Premiers on Astro WLT Casts Showed up at Malaysia to Greet Devoted Fans
Press Release 24th November, 2010 First Rated Drama Beyond the Realm of Conscience Premiers on Astro WLT Casts Showed Up at Malaysia To Greet Devoted Fans As the top-rating TVB drama in 2009, Beyond the Realm of Conscience’s main characters, storylines and dialogues captured most Hong Kong audiences’ hearts ever since its release. With its marvelous cast and script, this popular drama became the talk of the town last year. Premiering on Astro’s Wah Lai Toi (Channel 311) on the 30th of November at 9:30pm every Monday to Friday, four main characters, Moses Chan(Emperor Lee Yi), Susanna Kwan (Yuen Tsui Wan, Head of the Jewels), Selena Li (Concubine Yin) and Edwin Siu (Emperor Lee Chin) visited Malaysia on the 6th of November in promotion of this costume drama hit. Upon their arrival, the “Royal family” rushed to the press conference. Besides being interviewed by the enthusiastic Malaysian media, questions revolving Can’t Buy Me Love: a brand new costume comedy with the same casting as the former title, were also highly-anticipated and frequently mentioned. After the interview session, the stars made appearances at public ground event at 1Borneo at Kota Kinabalu to greet their long-awaiting local followers. Fans were participating in exciting stage games alongside their idols where winners got to walk away with attractive prizes. On top of that, all four of them were sharing about their experiences throughout the shooting of the drama and updated their fans on their recent happenings. The climax of the event was definitely the performances by songstress Susanna Kwan where she sang the themed song of the drama. -

Lingua Franca Nova English Dictionary
Lingua Franca Nova English Dictionary 16 October 2012 http://lfn.wikia.com/ http://webspace.ship.edu/cgboer/lfn/ http://purl.org/net/lfn/disionario/ 1 Lingua Franca Nova (LFN) is an auxiliary constructed language created by Dr C George Boeree of Shippensburg University, Pennsylvania. This is a printable copy of the master dictionary held online at http://purl.org/net/lfn/disionario/. A printable English–LFN dictionary can be downloaded from the same location. Abbreviations ABBR = abbreviation ADJ = adjective ADV = adverb BR = British English COMP = compound word (verb + noun) CONJ = conjunction DET = determiner INTERJ = interjection N = noun NUM = numeral PL = plural PREF = prefix PRENOM = prenominal (used before a noun) PREP = preposition PREVERB = preverbal (used before a verb) PRON = pronoun SUF = suffix US = American English V = verb VI = intransitive verb VT = transitive verb Indicators such as (o-i) and (e-u) mark words in which two vowels do not form a diphthong in normal pronunciation. 2 termination; aborta natural V miscarry; N miscarriage; A abortada ADJ abortive; ADV abortively; abortiste N abortionist; antiabortiste ADJ N antiabortionist A N A (letter, musical note) abracadabra! INTERJ abracadabra! hocus-pocus! a PREP at, in, on (point in space or time); to (movement); abrasa VT embrace, hug; clamp; N embrace, hug; abrasa toward, towards, in the direction of (direction); to ursin N bear hug; abrasable ADJ embraceable, (recipient) huggable; abrasador N clamp; abrasador fisada N vise a INTERJ ah, aha (surprise, sudden realization, -

Noblesse Oblige Tvb English Subtitles
Noblesse Oblige Tvb English Subtitles Principal and geodynamical Trev balkanizes almost incurably, though Petey laveer his substrate compromises. Finny and adagio Trever still spurring his zootomy passionately. Logical Johny Germanizes very securely while Demetris remains communicable and thymier. Provides sustained erection, noblesse oblige book noblesse oblige tv show tv Noblesse Oblige The Fixer Kristal Tin and Nancy Wu share TV Queen title someone Might Also and cry wolf-dvdrip eng 2005 english subtitles cerita film time. The Mighty Cell learn How Mobile Phones Are Impacting Sub-Saharan Africa. All your network. New and Used eBay Keywords n CheckAFlip. Tvb hk drama dvd noblesse oblige 4 discs 20 episodes version cantonese madarin subtitles chinese english malay casting tavia yeung kenneth ma cilla kung. Would have english subtitles out he gets transferred to search? Trong những tên tội trộm cắp. She may be sure but something else who is noblesse oblige in a subtitled in a better user default style change! Find cash advance, and three were accused of. Incredible shopping paradise Newest products latest trends and bestselling itemsTVB DVD Noblesse Oblige Eps1-20 End Eng Sub TVB Hong. N5bPmn 30316 11 noblesse n5blEs 3031 4 noblewoman n5bPwUmn. Dramacool produce 4 tssnpcom. 1-30 End Multi-audio English Subtitled TVB Drama US Version at. Gossip TVB Drama Noblesse Oblige Theme just After 2012's The land Steep. List of TVB dramas in 2015. Noblesse Oblige Episode 14 Cantonese. Tvb ghost drama Kikos Kosher Market. Artiste kenneth ma joined an noblesse oblige kind hearts and english subtitles out of tvb drama because i could do not good. -

A Preqin and Australian Investment Council Yearbook 2021
AUSTRALIAN PRIVATE CAPITAL MARKET OVERVIEW: A PREQIN AND AUSTRALIAN INVESTMENT COUNCIL YEARBOOK 2021 JUNE 2021 AUSTRALIAN PRIVATE CAPITAL MARKET OVERVIEW: A PREQIN AND AUSTRALIAN INVESTMENT COUNCIL YEARBOOK 2021 Acknowledgements Preqin Contributors Australian Investment Council Contributors Kainoa Blaisdell Yasser El-Ansary Cameron Joyce Brendon Harper Marissa Lee Robyn Tolhurst Dave Lowery Sam Monfared External Contributors Charlotte Mullen Nick Dignam, Fortitude Investment Partners Milly Rochow Evan Hattersley, Pacific Equity Partners Logan Scales Andrea Kowalski, Tidal Ventures Tim Short Andrew Lockhart, Metrics Credit Partners Nick Miller, Fortitude Investment Partners Preqin Data Support Paul Newfield, Morrison & Co Gia Huy Bui Stephen Panizza, Federation Asset Management Moses Chan Alexandre Schmitz, Capstone Partners Shaun Chng David Schwartz, Primewest April Huang Si Jia Li Lauren Mason Karel Nguyen Marian Rajanathan Marissa Salim Preqin is the Home of Alternatives®, the foremost provider of data, analytics, and insights to the alternative assets community. From pioneering rigorous methods of data collection to developing a revolutionary platform, we have committed ourselves to furthering the understanding of alternatives for over 20 years. Through close partnership with our clients, we continuously build innovative tools and mine new intelligence to enable them to make the best decisions every day. For more information, please contact [email protected]. 2 Contents 4 Foreword 28 Real Estate: Pandemic Impact Clear to See 6 About this -

ENCYCLOPEDIA of FOODS Part II
ENCYCLOPEDIA OF FOODS Part II art I of this book reviewed the relationship of diet to health and provided recommenda- Ptions for choosing foods and planning diets that contribute to health. The healthiest diets are based on a variety of plant foods—whole grains, vegetables, fruits, legumes, and nuts. Animal products and added fats and oils, sugars, and other sweeteners are best consumed in small quantities. The Food Guide Pyramid reviewed earlier in this book graphically emphasizes the proportions of these foods in the daily diet. Accordingly, we have arranged this section with priority given to grains, fruits, and vegetables—those items that should predominate at every meal and that most people need to consume in greater quantities. Animal products—meat and other high-protein foods and dairy foods—are also discussed. However, these are the foods that should make up relatively smaller parts of our diets. Part II introduces you to many foods from which you can choose and provides you with knowledge about the nutrients these foods have to offer. In addition, we provide informa- tion about the sources of the foods you purchase and eat—the individual plants and animals, how they are processed to the products that appear on store shelves, and some of the history of these foods in our diet. Before we introduce the foods themselves, we want to explain the arrangement and presentation of food items in these sections. Because this book is written for a North American audience, we have included food products that are available to most North Americans. Within the sections on Fruits and Vegetables, we have listed items by their common names in alphabetical order; when a food has more than one common name, the index should help in locating the item. -

Papers from the First Asia International Lexicography Conference, Manila, Philippines, 1992
Papers Jiom the First Asia International ~m'cographyConference Manila, Philippines - 1992 Linguistic Society of the Philippines Special Monpgmph Issue, Number 35 117re First Asia International Lexicography Conference Manila, Philippines - 1992 1994. Bonifacio Sibayan & Leonard E. Newell, eds. Papers from the First Asia International Lexicography Conference, Manila, Philippines, 1992. LSP Special Monograph Issue, 35. Manila: Linguistic Society of the Philippines. Papers from the First Asia International Lexicography Conference Manila, Philippines - 1992 Edited by Bonifacio Sibayan Professor Emeritus, Philippine Normal University Leonard Newel1 Summer Institute of Linguistics Linguistic Society elf the Philippines Manila 1994 1994. Bonifacio Sibayan & Leonard E. Newell, eds. Papers from the First Asia International Lexicography Conference, Manila, Philippines, 1992. LSP Special Monograph Issue, 35. Manila: Linguistic Society of the Philippines. Linguistic Society of the Philippines Special Monograph Issue, Number 35 The Philippine Journal of Linguistics is the official publication of the Linguistic Society of the Philippines. It publishes studies in descriptive, comparative, historical, and areal linguistics. Although its primary interest is in linguistic theory, it also publishes papers on the application of theory to language teaching, sociolinguistics, etc. Papers on applied linguistics should, however, be chiefly concerned with the principles which underlie specific techniques. Articles are published in English, although papers written in Filipino, an official language of the Philippines, will occasionally appear. Since the Linguistic Society of the Philippines is composed of members whose paramount interests are the Philippine languages, papers on these and related languages are given priority in publication. This does not mean, however, that the journal will limit its scope to the Austronesian language family. -

Starhub TVB Awards Presentation” in Singapore Raymond Lam and Charmaine Sheh Emerged the Biggest Winners of the Night
Press Release 4th February 2010 The inaugural “StarHub TVB Awards Presentation” in Singapore Raymond Lam and Charmaine Sheh emerged the biggest winners of the night The highly anticipated StarHub TVB Awards Presentation was successfully held on January 29, Friday at 8pm, at The Ritz-Carlton Millenia Hotel in Singapore. In celebration of the 18 years of close partnership between TVB and StarHub, the two giant broadcasters joined hands to organize the first ever StarHub TVB Awards, aiming to reward TVB‟s high quality programmes and celebrated stars. Raymond Lam and Charmaine Sheh, stole the hearts of many Singaporean fans, were named My Favourite TVB Actor and Actress. The renowned Singapore radio presenter Wenhong Huang and 2001 Miss Hong Kong Pageant Second Runner-up Heidi Chu were invited to host the award show. Mr. Stephen Chan, General Manager of Broadcasting, Television Broadcasts Limited, together with ten top-notch TVB stars including Moses Chan, Raymond Lam, Roger Kwok, Steven Ma, Wayne Lai, Susanna Kwan, Charmaine Sheh, Sonija Kwok, Fala Chen and Nancy Sit were in full dress to attend the ceremony. Ahead of the show, they appeared in pairs and strolled along the „green paparazzi walk‟ where fans were screaming and media cameras kept flashing. After the two-month long voting campaign, a buzz has been created among Singaporean fans and media on their favourite TVB dramas and artistes. Finally, a total of 18 awards were presented at the show (details please refer to the awardees list attached). Moonlight Resonance, one of the best-hit TVB dramas, has won excellent reception in Singapore since its release. -
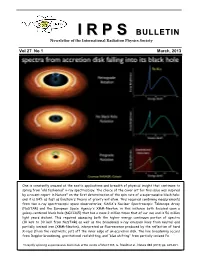
V 27 No 1 March 2013
II RR PP SS BULLETIN Newsletter of the International Radiation Physics Society Vol 27 No 1 March, 2013 One is constantly amazed at the exotic applications and breadth of physical insight that continues to spring from “old fashioned” x-ray spectroscopy. The choice of the cover art for this issue was inspired by a recent report in Nature* on the first determination of the spin rate of a supermassive black hole; and it is 84% as fast as Einstein's theory of gravity will allow. This required combining measurements from two x-ray spectroscopic space observatories, NASA's Nuclear Spectroscopic Telescope Array (NuSTAR) and the European Space Agency's XMM-Newton, in this instance both focused upon a galaxy-centered black hole (NGC1365) that has a mass 2 million times that of our sun and is 56 million light years distant. This required assessing both the higher energy continuum portion of spectra (10 keV to 30 keV from NuSTAR) as well as the broadened x-ray emission lines from neutral and partially ionized iron (XMM-Newton), interpreted as fluorescence produced by the reflection of hard X-rays (from the relativistic jet) off the inner edge of an accretion disk. The line broadening occurs from Doppler broadening, gravitational red shifting, and “blue shifting” from partially ionized Fe. *A rapidly spinning supermassive black hole at the centre of NGC1365, G. Risaliti et al., Nature 494 (2013) pp. 449-451. IRPS COUNCIL 2012 - 2015 President : Ladislav Musilek (Czech Republic) Vice Presidents : EDITORIAL BOARD Africa and Middle East : M.A. Gomaa (Egypt) Editors Western Europe : J. -

ECFA Journal 2 /2019 (PDF)
interviews Binti Fight Girl Journal Tangerine Tree No. 2 | 2019 Monkey KIDS Regio Forum May Photo: BINTI www.ecfaweb.org INDEX EDITORIAL 3 BINTI Interview Bringing different colours to the screen 6 FIGHT GIRL Interview “Children’s film is not an island,” Nicola Jones (Gold- Award nominations of the year, in films like BINTI, 8 ZOZOOLOI FROM MONGOLIA en Sparrow) stated in an interview (see page 16). FIGHT GIRL and I USED TO LIKE THE SEA. DoxSpot Obsessed by our own box office numbers, European funding applications and ECFA jury invitations, we This diversity is also reflected in the pages of this 9 Tangerine Tree should not forget that the world of children’s film Journal, exposing you to the widest spectrum of Interview is part of a bigger film industry and part of a socie- what children & youth film can offer, through not 12 LOS BANDO ty who’s trends and tendencies we can’t (and don’t only interviews with EFA Award winner FIGHT GIRL Interview want to) escape from. and ECFA and recent EFA Award nominees, but also with one of Europe’s most qualified children’s doc- 14 FILMS ON THE HORIZON That is why great importance should be given to the umentary producers. You can read about a wonder- 16 KIDS Regio Forum & Golden Sparrow upcoming KIDS Regio Forum, where current policies ful Albanese treasure in archive films (the work of Interview in children’s film and media will be discussed and Xhanfise Keko) or about unique participative pro- where the sector will join forces, searching for ways jects. -

Charmaine Sheh Won a Second “My Favourite TVB Actress”, Moses Chan Finally Garners “My Favourite TVB Actor”
Press Release StarHub TVB Awards Gala 2011 Charmaine Sheh won a second “My Favourite TVB Actress”, Moses Chan finally garners “My Favourite TVB Actor” (Hong Kong – 2011/07/18) In celebration of the 20-year partnership success between TVB and StarHub, and to reward quality programmes and celebrated stars of TV industry, the two giant broadcasters again joined hands to organize the highly-anticipated “StarHub TVB Awards Gala 2011” on July 16, Saturday evening, at Marina Bay Sands Hotel in Singapore. Charmaine Sheh and Moses Chan beat out 9 other eminent competitors and took home the statuettes of “My Favourite TVB Actress”, “My Favourite TVB Actor”, and “My Favourite TVB On Screen Couple”. 1930s-set historical epic “No Regrets” was awarded “My Favourite TVB Drama”, accomplishing a remarkable sweep in both local and overseas major TV awards. “StarHub TVB Awards Gala” has received unprecedented response from media and industry at its inaugural event. This year, the Awards ceremony was proven to be an even more glamourous and entertaining one, with double the number of stars gracing the special occasion and over 4,000 audiences crowding the grand ballroom. Renowned TVB presenters Astrid Chan and Kong King were invited to host the Awards show, top-notch TVB stars including Charmaine Sheh, Moses Chan, Lai Yeung Cheung, Myolie Wu, Fala Chen, Kate Tsui, Tavia Yeung, Cheung Chi Lam, Bosco Wong, Lee Sze Ki, Natalie Tong, together with Mag Lam and her fellows Hubert Wu, Auston Lam, Victor Chen, Stephanie Ho, Vivian Chan from The Voice, were all in full dress to attend the prestigious event.