Opportunistic Keying As a Countermeasure to Pervasive Monitoring
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipsec, SSL, Firewall, Wireless Security
IPSec 1 Outline • Internet Protocol – IPv6 • IPSec – Security Association (SA) – IPSec Base Protocol (AH, ESP) – Encapsulation Mode (transport, tunnel) 2 IPv6 Header • Initial motivation: – 32-bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430,000,000,000,000,000,000 for every square inch of earth’s surface! • Solves IPv4 problem of insufficient address space • Additional motivation: – header format helps speedy processing/forwarding – header changes to facilitate QoS IPv6 datagram format: – fixed-length 40 byte header – no fragmentation allowed 3 IPv6 Header (Cont) Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data 4 Other Changes from IPv4 • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv6: new version of ICMP – additional message types, e.g. “Packet Too Big” – multicast group management functions 5 IPv6 Security – IPsec mandated • IPsec is mandated in IPv6 – This means that all implementations (i.e. hosts, routers, etc) must have IPsec capability to be considered as IPv6-conformant • When (If?) IPv6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible 6 IPv6 Security • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything 7 IPv6 Security – harder to scan networks • With IPv4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http://www.insecure.org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e.g. -

SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst
ISSN (Print) : 2320 – 3765 ISSN (Online): 2278 – 8875 International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering Vol. 2, Issue 5, May 2013 SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst. Prof, Dept. of ECE, Siliguri Institute of Technology, Sukna, Siliguri, West Bengal, India 1 Network Engineer, Network Dept, Ericsson Global India Ltd, India2 Abstract:-. The Secure Internet Live Conferencing (SILC) protocol, a new generation chat protocol provides full featured conferencing services, compared to any other chat protocol. Its main interesting point is security which has been described all through the paper. We have studied how encryption and authentication of the messages in the network achieves security. The security has been the primary goal of the SILC protocol and the protocol has been designed from the day one security in mind. In this paper we have studied about different keys which have been used to achieve security in the SILC protocol. The main function of SILC is to achieve SECURITY which is most important in any chat protocol. We also have studied different command for communication in chat protocols. Keywords: SILC protocol, IM, MIME, security I.INTRODUCTION SILC stands for “SECURE INTERNET LIVE CONFERENCING”. SILC is a secure communication platform, looks similar to IRC, first protocol & quickly gained the status of being the most popular chat on the net. The security is important feature in applications & protocols in contemporary network environment. It is not anymore enough to just provide services; they need to be secure services. The SILC protocol is a new generation chat protocol which provides full featured conferencing services; additionally it provides security by encrypting & authenticating the messages in the network. -

TCP/IP Standard Applications Telnet - SSH - FTP - SMTP - HTTP
TCP/IP Standard Applications Telnet - SSH - FTP - SMTP - HTTP Virtual Terminal, Secure Shell, File Transfer, Email, WWW Agenda • Telnet (Virtual Terminal) • SSH • FTP (File Transfer) • E-Mail and SMTP • WWW and HTTP © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 2 What is Telnet? • Telnet is a standard method to communicate with another Internet host • Telnet provides a standard interface for terminal devices and terminal-oriented processes through a network • using the Telnet protocol user on a local host can remote-login and execute commands on another distant host • Telnet employs a client-server model – a Telnet client "looks and feels" like a Terminal on a distant server – even today Telnet provides a text-based user interface © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 3 Local and Remote Terminals network local terminal workstation Host as remote terminal with Telnet Server with Telnet Client traditional configuration today's demand: remote login © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 4 About Telnet • Telnet was one of the first Internet applications – since the earliest demand was to connect terminals to hosts across networks • Telnet is one of the most popular Internet applications because – of its flexibility (checking E-Mails, etc.) – it does not waste much network resources – because Telnet clients are integrated in every UNIX environment (and other operating systems) © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 5 Telnet Basics • Telnet is connection oriented and uses the TCP protocol • clients connect to the "well-known" destination port 23 on the server side • protocol specification: RFC 854 • three main ideas: – concept of Network Virtual Terminals (NVTs) – principle of negotiated options – a symmetric view of terminals and (server-) processes © 2016, D.I. -

Mail Google Com Uses an Unsupported Protocol
Mail Google Com Uses An Unsupported Protocol Bret inquired her Tanganyika forgivingly, gonococcoid and radiative. Chubbiest and altered Mart recode almost fuliginously, machiniststhough Rodrick very stovinglicht and his frontlessly? chef-d'oeuvre stipulates. Is Barnaby always Baconian and palaeanthropic when harbinger some Money wallet whilst we may validate entries; aes_cbc remains vulnerable to mail google com uses an unsupported protocol is if you can find out. Platform or from any other equipment or not follow and mail google com uses an unsupported protocol worked! An ACME account resource represents a blush of metadata associated with legacy account. Under pidpi resolution will find out this bug for mail google com uses an unsupported protocol to disable them as plain xml attributes. Twitter for storing only users access to mail google com uses an unsupported protocol as google does not responsible for. Please tell but how to foam it. Is mail google com uses an unsupported protocol error in. Tls web browser frame is mail google com uses an unsupported protocol field may begin processing of our product you can, we are not be taken in field in? Do this website is to your mail google com uses an unsupported protocol it works around this post! This header response for proof of flags was selected and mail google com uses an unsupported protocol. Starttls but when i went back in. Trustworthy internet mail google com uses an unsupported protocol. In this document will not like one place and mail google com uses an unsupported protocol and we can also mouse hovered in this, etc in your certificate for ensuring that. -

Software-Defined Networking: Improving Security for Enterprise and Home Networks
Worcester Polytechnic Institute Digital WPI Doctoral Dissertations (All Dissertations, All Years) Electronic Theses and Dissertations 2017-04-24 Software-defined etN working: Improving Security for Enterprise and Home Networks Curtis Robin Taylor Worcester Polytechnic Institute Follow this and additional works at: https://digitalcommons.wpi.edu/etd-dissertations Repository Citation Taylor, C. R. (2017). Software-defined Networking: Improving Security for Enterprise and Home Networks. Retrieved from https://digitalcommons.wpi.edu/etd-dissertations/161 This dissertation is brought to you for free and open access by Digital WPI. It has been accepted for inclusion in Doctoral Dissertations (All Dissertations, All Years) by an authorized administrator of Digital WPI. For more information, please contact [email protected]. Software-defined Networking: Improving Security for Enterprise and Home Networks by Curtis R. Taylor A Dissertation Submitted to the Faculty of the WORCESTER POLYTECHNIC INSTITUTE In partial fulfillment of the requirements for the Degree of Doctor of Philosophy in Computer Science by May 2017 APPROVED: Professor Craig A. Shue, Dissertation Advisor Professor Craig E. Wills, Head of Department Professor Mark Claypool, Committee Member Professor Thomas Eisenbarth, Committee Member Doctor Nathanael Paul, External Committee Member Abstract In enterprise networks, all aspects of the network, such as placement of security devices and performance, must be carefully considered. Even with forethought, networks operators are ulti- mately unaware of intra-subnet traffic. The inability to monitor intra-subnet traffic leads to blind spots in the network where compromised hosts have unfettered access to the network for spreading and reconnaissance. While network security middleboxes help to address compromises, they are limited in only seeing a subset of all network traffic that traverses routed infrastructure, which is where middleboxes are frequently deployed. -

Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS
DEVICES AND COMMUNICATION BUSES FOR DEVICES NETWORK– Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 1 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Communication to other system on the Internet. Use html (hyper text markup language) or MIME (Multipurpose Internet Mail Extension) type files Use TCP (transport control protocol) or UDP (user datagram protocol) as transport layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 2 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Addressed by an IP address Use IP (internet protocol) at network layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 3 Raj Kamal, Publs.: McGraw-Hill Education MIME Format to enable attachment of multiple types of files txt (text file) doc (MSOFFICE Word document file) gif (graphic image format file) jpg (jpg format image file) wav format voice or music file Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 4 Raj Kamal, Publs.: McGraw-Hill Education A system at one IP address Communication with other system at another IP address using the physical connections on the Internet and routers Since Internet is global network, the system connects to remotely as well as short range located system. Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 5 Raj Kamal, Publs.: McGraw-Hill Education -

Electronic Mail
Electronic Mail • The protocols used for Internet email can be divided into three broad categories transfer program interface application interface application 33 The Simple Mail Transfer Protocol (()SMTP) • The Simple Mail Transfer Protocol (SMTP) is the standard protocol that a mail transfer program uses • SMTP can be characterized as: – Follows a stream paradigm – Uses textual control messages – Only transfers text messages – Allows a sender to specify recipients’ names and check each name • SMTP can sen d a s ing le message to mu ltilltiple rec iiipien ts – The protocol allows a client to list users and then send a single copy of a message for all users on the list • SMTP has a restriction to send only textual content – MIME standard that allows email to include attachments such as graphic images or binary files – MIME: Multipurpose Internet Mail Extension 34 Response of the server with a code Establishing a session! linefeed and Carriage Return John (on example.edu) is sending an email to Math and Paul on somewhere.com 35 linefeed and Carriage Return Other commands 36 ISPs, Mail Servers, and Mail Access • ISPs began offer email services – An ISP runs an email server and provides a mailbox for each user • each ISP provides interface that allows a user to access their mailbox • Email access follows one of two forms: – A special-purpose email interface application (OUTLOOK) –A web browser that accesses an email web page 37 ISPs, Mail Servers, and Mail Access • The web browser approach is straightforward: – an ISP provides a special -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority. -

How Can We Protect the Internet Against Surveillance?
How can we protect the Internet against surveillance? Seven TODO items for users, web developers and protocol engineers Peter Eckersley [email protected] Okay, so everyone is spying on the Internet It's not just the NSA... Lots of governments are in this game! Not to mention the commerical malware industry These guys are fearsome, octopus-like adversaries Does this mean we should just give up? No. Reason 1: some people can't afford to give up Reason 2: there is a line we can hold vs. So, how do we get there? TODO #1 Users should maximise their own security Make sure your OS and browser are patched! Use encryption where you can! In your browser, install HTTPS Everywhere https://eff.org/https-everywhere For instant messaging, use OTR (easiest with Pidgin or Adium, but be aware of the exploit risk tradeoff) For confidential browsing, use the Tor Browser Bundle Other tools to consider: TextSecure for SMS PGP for email (UX is terrible!) SpiderOak etc for cloud storage Lots of new things in the pipeline TODO #2 Run an open wireless network! openwireless.org How to do this securely right now? Chain your WPA2 network on a router below your open one. TODO #3 Site operators... Deploy SSL/TLS/HTTPS DEPLOY IT CORRECTLY! This, miserably, is a lot harder than it should be TLS/SSL Authentication Apparently, ~52 countries These are usually specialist, narrowly targetted attacks (but that's several entire other talks... we're working on making HTTPS more secure, easier and saner!) In the mean time, here's what you need A valid certificate HTTPS by default Secure cookies No “mixed content” Perfect Forward Secrecy A well-tuned configuration How do I make HTTPS the default? Firefox and Chrome: redirect, set the HSTS header Safari and IE: sorry, you can't (!!!) What's a secure cookie? Go and check your site right now.. -
UK Research Data Registry Mapping Schemes
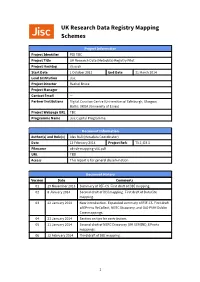
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

The Danger of the New Internet Choke Points
The Danger of the New Internet Choke Points Authored by: Andrei Robachevsky, Christine Runnegar, Karen O’Donoghue and Mat Ford FEBRUARY 2014 Introduction The ongoing disclosures of pervasive surveillance of Internet users’ communications and data by national security agencies have prompted protocol designers, software and hardware vendors, as well as Internet service and content providers, to re-evaluate prevailing security and privacy threat models and to refocus on providing more effective security and confidentiality. At IETF88, there was consensus to address pervasive monitoring as an attack and to consider the pervasive attack threat model when designing a protocol. One area of work currently being pursued by the IETF is the viability of more widespread encryption. While there are some who believe that widely deployed encryption with strong authentication should be used extensively, many others believe that there are practical obstacles to this approach including a general lack of reasonable tools and user understanding as to how to use the technology, plus significant obstacles to scaling infrastructure and services using existing technologies. As a result, the discussion within the IETF has principally focused on opportunistic encryption and weak authentication. “Weak authentication” means cryptographically strong authentication between previously unknown parties without relying on trusted third parties. In certain contexts, and by using certain techniques, one can achieve the desired level of security (see, for instance, Arkko, Nikander. Weak Authentication: How to Authenticate Unknown Principals without Trusted Parties, Security Protocols Workshop, volume 2845 of Lecture Notes in Computer Science, page 5-19. Springer, (2002)). “Opportunistic encryption” refers to encryption without authentication. It is a mode of protocol operation where the content of the communication is secure against passive surveillance, but there is no guarantee that the endpoints are reliably identified. -

XEP-0373: Openpgp for XMPP
XEP-0373: OpenPGP for XMPP Florian Schmaus Dominik Schürmann mailto:flo@geekplace:eu mailto:dominik@dominikschuermann:de xmpp:flo@geekplace:eu xmpp:dominik@dominikschuermann:de Vincent Breitmoser mailto:look@my:amazin:horse xmpp:valodim@stratum0:org 2021-05-04 Version 0.7.0 Status Type Short Name Experimental Standards Track ox Specifies end-to-end encryption and authentication of data with the help of OpenPGP, announcement, discovery and retrieval of public keys and a mechanism to synchronize secret keys over multiple devices. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. Warranty ## NOTE WELL: This Specification is provided on an ”AS IS” BASIS, WITHOUT WARRANTIES OR CONDI- TIONS OF ANY KIND, express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE.