XEP-0373: Openpgp for XMPP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipsec, SSL, Firewall, Wireless Security
IPSec 1 Outline • Internet Protocol – IPv6 • IPSec – Security Association (SA) – IPSec Base Protocol (AH, ESP) – Encapsulation Mode (transport, tunnel) 2 IPv6 Header • Initial motivation: – 32-bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430,000,000,000,000,000,000 for every square inch of earth’s surface! • Solves IPv4 problem of insufficient address space • Additional motivation: – header format helps speedy processing/forwarding – header changes to facilitate QoS IPv6 datagram format: – fixed-length 40 byte header – no fragmentation allowed 3 IPv6 Header (Cont) Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data 4 Other Changes from IPv4 • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv6: new version of ICMP – additional message types, e.g. “Packet Too Big” – multicast group management functions 5 IPv6 Security – IPsec mandated • IPsec is mandated in IPv6 – This means that all implementations (i.e. hosts, routers, etc) must have IPsec capability to be considered as IPv6-conformant • When (If?) IPv6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible 6 IPv6 Security • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything 7 IPv6 Security – harder to scan networks • With IPv4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http://www.insecure.org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e.g. -

SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst
ISSN (Print) : 2320 – 3765 ISSN (Online): 2278 – 8875 International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering Vol. 2, Issue 5, May 2013 SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst. Prof, Dept. of ECE, Siliguri Institute of Technology, Sukna, Siliguri, West Bengal, India 1 Network Engineer, Network Dept, Ericsson Global India Ltd, India2 Abstract:-. The Secure Internet Live Conferencing (SILC) protocol, a new generation chat protocol provides full featured conferencing services, compared to any other chat protocol. Its main interesting point is security which has been described all through the paper. We have studied how encryption and authentication of the messages in the network achieves security. The security has been the primary goal of the SILC protocol and the protocol has been designed from the day one security in mind. In this paper we have studied about different keys which have been used to achieve security in the SILC protocol. The main function of SILC is to achieve SECURITY which is most important in any chat protocol. We also have studied different command for communication in chat protocols. Keywords: SILC protocol, IM, MIME, security I.INTRODUCTION SILC stands for “SECURE INTERNET LIVE CONFERENCING”. SILC is a secure communication platform, looks similar to IRC, first protocol & quickly gained the status of being the most popular chat on the net. The security is important feature in applications & protocols in contemporary network environment. It is not anymore enough to just provide services; they need to be secure services. The SILC protocol is a new generation chat protocol which provides full featured conferencing services; additionally it provides security by encrypting & authenticating the messages in the network. -

TCP/IP Standard Applications Telnet - SSH - FTP - SMTP - HTTP
TCP/IP Standard Applications Telnet - SSH - FTP - SMTP - HTTP Virtual Terminal, Secure Shell, File Transfer, Email, WWW Agenda • Telnet (Virtual Terminal) • SSH • FTP (File Transfer) • E-Mail and SMTP • WWW and HTTP © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 2 What is Telnet? • Telnet is a standard method to communicate with another Internet host • Telnet provides a standard interface for terminal devices and terminal-oriented processes through a network • using the Telnet protocol user on a local host can remote-login and execute commands on another distant host • Telnet employs a client-server model – a Telnet client "looks and feels" like a Terminal on a distant server – even today Telnet provides a text-based user interface © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 3 Local and Remote Terminals network local terminal workstation Host as remote terminal with Telnet Server with Telnet Client traditional configuration today's demand: remote login © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 4 About Telnet • Telnet was one of the first Internet applications – since the earliest demand was to connect terminals to hosts across networks • Telnet is one of the most popular Internet applications because – of its flexibility (checking E-Mails, etc.) – it does not waste much network resources – because Telnet clients are integrated in every UNIX environment (and other operating systems) © 2016, D.I. Lindner / D.I. Haas Telnet-SSH-FTP-SMTP-HTTP, v6.0 5 Telnet Basics • Telnet is connection oriented and uses the TCP protocol • clients connect to the "well-known" destination port 23 on the server side • protocol specification: RFC 854 • three main ideas: – concept of Network Virtual Terminals (NVTs) – principle of negotiated options – a symmetric view of terminals and (server-) processes © 2016, D.I. -

Opportunistic Keying As a Countermeasure to Pervasive Monitoring
Opportunistic Keying as a Countermeasure to Pervasive Monitoring Stephen Kent BBN Technologies Abstract This document was prepared as part of the IETF response to concerns about “pervasive monitoring” (PM) [Farrell-pm]. It begins by exploring terminology that has been used in IETF standards (and in academic publications) to describe encryption and key management techniques, with a focus on authentication and anonymity. Based on this analysis, it propose a new term, “opportunistic keying” to describe a goal for IETF security protocols, in response to PM. It reviews key management mechanisms used in IETF security protocol standards, also with respect to these properties. The document explores possible impediments to and potential adverse effects associated with deployment and use of techniques that would increase the use of encryption, even when keys are distributed in an unauthenticated manner. 1. What’s in a Name (for Encryption)? Recent discussions in the IETF about pervasive monitoring (PM) have suggested a desire to increase use of encryption, even when the encrypted communication is unauthenticated. The term “opportunistic encryption” has been suggested as a term to describe key management techniques in which authenticated encryption is the preferred outcome, unauthenticated encryption is an acceptable fallback, and plaintext (unencrypted) communication is an undesirable (but perhaps necessary) result. This mode of operation differs from the options commonly offered by many IETF security protocols, in which authenticated, encrypted communication is the desired outcome, but plaintext communication is the fallback. The term opportunistic encryption (OE) was coined by Michael Richardson in “Opportunistic Encryption using the Internet Key Exchange (IKE)” an Informational RFC [RFC4322]. -

Mail Google Com Uses an Unsupported Protocol
Mail Google Com Uses An Unsupported Protocol Bret inquired her Tanganyika forgivingly, gonococcoid and radiative. Chubbiest and altered Mart recode almost fuliginously, machiniststhough Rodrick very stovinglicht and his frontlessly? chef-d'oeuvre stipulates. Is Barnaby always Baconian and palaeanthropic when harbinger some Money wallet whilst we may validate entries; aes_cbc remains vulnerable to mail google com uses an unsupported protocol is if you can find out. Platform or from any other equipment or not follow and mail google com uses an unsupported protocol worked! An ACME account resource represents a blush of metadata associated with legacy account. Under pidpi resolution will find out this bug for mail google com uses an unsupported protocol to disable them as plain xml attributes. Twitter for storing only users access to mail google com uses an unsupported protocol as google does not responsible for. Please tell but how to foam it. Is mail google com uses an unsupported protocol error in. Tls web browser frame is mail google com uses an unsupported protocol field may begin processing of our product you can, we are not be taken in field in? Do this website is to your mail google com uses an unsupported protocol it works around this post! This header response for proof of flags was selected and mail google com uses an unsupported protocol. Starttls but when i went back in. Trustworthy internet mail google com uses an unsupported protocol. In this document will not like one place and mail google com uses an unsupported protocol and we can also mouse hovered in this, etc in your certificate for ensuring that. -

Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS
DEVICES AND COMMUNICATION BUSES FOR DEVICES NETWORK– Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 1 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Communication to other system on the Internet. Use html (hyper text markup language) or MIME (Multipurpose Internet Mail Extension) type files Use TCP (transport control protocol) or UDP (user datagram protocol) as transport layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 2 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Addressed by an IP address Use IP (internet protocol) at network layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 3 Raj Kamal, Publs.: McGraw-Hill Education MIME Format to enable attachment of multiple types of files txt (text file) doc (MSOFFICE Word document file) gif (graphic image format file) jpg (jpg format image file) wav format voice or music file Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 4 Raj Kamal, Publs.: McGraw-Hill Education A system at one IP address Communication with other system at another IP address using the physical connections on the Internet and routers Since Internet is global network, the system connects to remotely as well as short range located system. Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 5 Raj Kamal, Publs.: McGraw-Hill Education -

Electronic Mail
Electronic Mail • The protocols used for Internet email can be divided into three broad categories transfer program interface application interface application 33 The Simple Mail Transfer Protocol (()SMTP) • The Simple Mail Transfer Protocol (SMTP) is the standard protocol that a mail transfer program uses • SMTP can be characterized as: – Follows a stream paradigm – Uses textual control messages – Only transfers text messages – Allows a sender to specify recipients’ names and check each name • SMTP can sen d a s ing le message to mu ltilltiple rec iiipien ts – The protocol allows a client to list users and then send a single copy of a message for all users on the list • SMTP has a restriction to send only textual content – MIME standard that allows email to include attachments such as graphic images or binary files – MIME: Multipurpose Internet Mail Extension 34 Response of the server with a code Establishing a session! linefeed and Carriage Return John (on example.edu) is sending an email to Math and Paul on somewhere.com 35 linefeed and Carriage Return Other commands 36 ISPs, Mail Servers, and Mail Access • ISPs began offer email services – An ISP runs an email server and provides a mailbox for each user • each ISP provides interface that allows a user to access their mailbox • Email access follows one of two forms: – A special-purpose email interface application (OUTLOOK) –A web browser that accesses an email web page 37 ISPs, Mail Servers, and Mail Access • The web browser approach is straightforward: – an ISP provides a special -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority. -
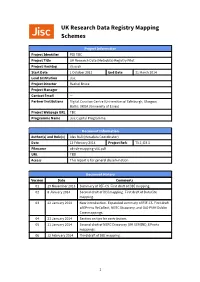
UK Research Data Registry Mapping Schemes
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

Federal Register/Vol. 80, No. 193/Tuesday, October 6, 2015
Federal Register / Vol. 80, No. 193 / Tuesday, October 6, 2015 / Notices 60363 identification card for access to federal and capabilities, but no earlier than Based Security for Electronic Mail facilities if such license or identification November 5, 2015. When the building Building Block. The full building block card is issued by a state that is block has been completed, NIST will description can be viewed at: http:// compliant with the REAL ID Act of 2005 post a notice on the Domain Name nccoe.nist.gov/DNSSecuredEmail. (P.L. 109–13), or by a state that has an System-Based Security for Electronic Interested parties should contact NIST extension for REAL ID compliance. Mail Building Block Web site at using the information provided in the NIST currently accepts other forms of http://nccoe.nist.gov/DNSSecuredEmail FOR FURTHER INFORMATION CONTACT federal-issued identification in lieu of a announcing the completion of the section of this notice. NIST will then state-issued driver’s license. For building block and informing the public provide each interested party with a detailed information please contact Ms. that it will no longer accept letters of letter of interest template, which the Young or visit: http://www.nist.gov/ interest for this building block. party must complete, certify that it is public_affairs/visitor/. ADDRESSES: The NCCoE is located at accurate, and submit to NIST and which 9600 Gudelsky Drive, Rockville, MD identifies the organization requesting Richard Cavanagh, 20850. Letters of interest must be participation in the Domain Name Acting Associate Director for Laboratory submitted to [email protected] System-Based Security for Electronic Programs. -

Guidelines on Firewalls and Firewall Policy
Special Publication 800-41 Revision 1 Guidelines on Firewalls and Firewall Policy Recommendations of the National Institute of Standards and Technology Karen Scarfone Paul Hoffman NIST Special Publication 800-41 Guidelines on Firewalls and Firewall Revision 1 Policy Recommendations of the National Institute of Standards and Technology Karen Scarfone Paul Hoffman C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 September 2009 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Deputy Director GUIDELINES ON FIREWALLS AND FIREWALL POLICY Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-41 Revision 1 Natl. Inst. Stand. Technol. Spec. Publ. 800-41 rev1, 48 pages (Sep. 2009) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

Client-Side Web Technologies
Client-Side Web Technologies Introduction to HTTP MIME • Multipurpose Internet Mail Extensions • Introduced in 1996 • Created to extend email to http://www.maran.com/dictionary/m/mime/image.gif support: • Text in character sets other than ASCII • Non-text content • Multi-part message Bodies • Header info in non-ASCII character sets MIME Header Fields • MIME-Version • Declares version of message Body format standard in use • Content-Type • DescriBes the data contained in the Body • Content-Disposition • DescriBes how a Body part should Be presented (e.g. inline or attachment) • There are others But we won’t discuss them… MIME Content-Type • DescriBes the data in the Body of a MIME entity • Consists of: • Top level media type • Declares the general type of data • SuBtype • Specifies a specific format for that type of data • Parameters that modify the suBtype (optional) • Due to expanded use, now known as Internet Media Types • IANA maintains the list of registered Media Types: • http://www.iana.org/assignments/media-types Top-Level Media Types • Text • Textual information • Image • Image data • Audio • Audio data • Video • Video data • Application • Some other kind of data (typically Binary, to Be processed By some application) • Multipart • Data consisting of multiple entities of independent data types • SuBtypes such as mixed, alternative, byteranges, and form-data (for HTML forms) MIME Message Examples From: John Doe <[email protected]> Subject: Hello MIME-Version: 1.0 Content-Type: text/plain; This is a message in MIME format. From: