NCPDP Electronic Signature Guidance
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

Office of State Controller, and the North Carolina Department of The
Office of State Controller, and the North Carolina Department of the Secretary of State, and North Carolina Department of Cultural Resources, Division of Archives and Records Digital Signature Policy Guidelines Version 1.1 March 2014 Contains corrected links to documents Table of Contents 1 Introduction ........................................................................................................................... 3 1.1 Purpose of Guideline ........................................................................................................ 3 1.2 Scope ............................................................................................................................... 3 2 Electronic Signature Background ........................................................................................ 3 2.1 Legislation ........................................................................................................................ 3 2.2 Definitions ......................................................................................................................... 4 2.3 Definition of an Electronic Signature* ................................................................................ 5 2.4 Electronic Signature versus Digital Signature ................................................................... 6 3 Expectations for Electronic Signatures ............................................................................... 7 3.1 Intended Goals ................................................................................................................ -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

Enhance Qualified Electronic Signatures with What You See Is What You Sign QES and WYSIWYS Service - Powered by Cryptomathic and Swisscom
Solution Brief Enhance Qualified Electronic Signatures with What You See Is What You Sign QES and WYSIWYS Service - Powered by Cryptomathic and Swisscom Qualified remote signing and Solution benefits WYSIWYS - hosted eID services The best way to deliver Qualified Electronic Signature ü Offer Advanced or Qualified (QES) services across different channels is to use Electronic Signatures compliant with remote signing technology. It integrates smoothly the Swiss signature law, ZertES, and the with any web application and does not require any EU eIDAS regulation on trust services. software install, plug in or additional components and can be used anywhere, at any time, from any device ü Improve the users’ signing with browsing capacity. Qualified remote signing experience for all channels incl. web provides the highest legal value and international portals, desktop applications, mobile & acceptance, while What You See Is What You Sign tablet platforms (WYSIWYS) technology delivers a seamless user experience with strong non-repudiation. Combining ü Demonstrate unrivalled non- QES with WYSIWYS is a strong enabler for businesses repudiation with WYSIWYS to provide ultimate security, trust and convenience funcionality with online transactions. This is exactly what the Cryptomathic – Swisscom solution offers, namely the ü Eliminate smartcards, card readers possibility to offer Advanced or Qualified Electronic and local software install Signatures using a zero-footprint remote signing hosted service, featuring WYSIWYS functionality. ü Solve data -
Global Guide to Electronic Signature
Global Guide to Electronic Signature Law: Country by country summaries of law and enforceability Table of contents Introduction 3 Germany 9 Republic of Korea 15 Definition of terms 4 Greece 9 Romania 9 Recommended practices for Hong Kong 10 Russian Federation 16 electronic agreements 4 Hungary 9 Singapore 16 India 10 Slovakia 9 Country summaries of Indonesia 11 Slovenia 9 electronic signature law Ireland 9 South Africa 17 Argentina 5 Israel 11 Spain 9 Australia 5 Italy 9 Sweden 9 Austria 9 Japan 12 Switzerland 17 Belgium 9 Latvia 9 Taiwan 18 Bermuda 6 Lithuania 9 Thailand 18 Brazil 6 Luxembourg 9 Turkey 19 Bulgaria 9 Malaysia 12 United Kingdom 9 Canada 7 Malta 9 United States 19 Chile 7 Mexico 13 Uruguay 20 China 8 Netherlands 9 Colombia 8 New Zealand 13 Croatia 9 Norway 14 Czech Republic 9 Peru 14 Denmark 9 Philippines 15 Estonia 9 Poland 9 European Union 9 Portugal 9 Finland 9 Republic of Cyprus 9 France 9 © Adobe Systems Incorporated 2016. This information is intended to help businesses understand the legal framework of electronic signatures. 2 However, Adobe cannot provide legal advice. This guide is not intended as legal advice and should not serve as a substitute for professional legal advice. You should consult an attorney regarding your specific legal questions. Introduction Electronic and digital signatures represent a tremendous opportunity for organizations to get documents signed and close deals faster. When rolling out e-signatures globally, you need to be aware of the variety of electronic signature laws across the globe. This guide gives you a great place to start. -

Qualified and Advanced Electronic Signatures)
R Terms and Conditions of Use Swisscom certification service (Qualified and advanced Electronic Signatures) Terms and Conditions of Use for the use of the Swisscom qualified certificate is permitted in connection with the use certification service with qualified and advanced certificates of the trust service in accordance with these Terms and Con- for qualified and advanced electronic signatures (Swisscom ditions of Use ("limitation of use"). certificate class "Saphir and Diamant") 2.2 Identity verification process and retention of the infor- mation Swisscom or the registration authority appointed by 1 Scope of these Terms and Conditions of Use Swisscom checks your identity in the identity verification pro- These Terms and Conditions of Use shall apply in the rela- cess. For qualified electronic signatures, this is done by tionship between you and Swisscom (Schweiz) AG, Alte means of your passport or an identity card allowing travel to Tiefenaustrasse 6, Worblaufen, Switzerland, company ID Switzerland. Depending in each case on the actual organisa- CHE-101.654.423 (hereinafter "Swisscom") for your use of tion of the identity verification process, you may be re- the Swisscom certification service with qualified and ad- quested in the verification process for advanced electronic vanced certificates for qualified and advanced electronic sig- signatures to also submit other documents than those re- natures. quired for qualified electronic signatures. 2 Swisscom’s Services Based on your identify verification process for qualified elec- tronic signatures, you may also create advanced electronic 2.1 Certification service in general signatures in accordance with these Terms and Conditions of For your certification services with qualified certificates, Use where the subscriber application used by you offers dif- Swisscom is an accredited certification services provider in ferent types of signatures. -

Eidas and E-SIGNATURE a LEGAL PERSPECTIVE: ELECTRONIC SIGNATURES in the EUROPEAN UNION
eIDAS AND E-SIGNATURE A LEGAL PERSPECTIVE: ELECTRONIC SIGNATURES IN THE EUROPEAN UNION WHITE PAPER TABLE OF CONTENTS Part 1: Introduction 3 Key Highlights of the eIDAS Regulation 4 Legal Effect of Different Types of Signatures 6 Regulation of Trust Services 7 Legal Best Practices 8 Part 2: Compliance With the Regulation 9 Advanced Electronic Signatures 9 Qualified Electronic Signatures 10 Format Standards 12 Additional Evidence 12 Conclusion 13 E-Signature Solution Checklist 14 About the Authors This paper is a collaboration between Lorna Brazell of Osborne Clarke LLP and OneSpan. In part one, Osborne Clarke provides a legal opinion on the legal validity of electronic signature in the European Union. Part two has been prepared by OneSpan, and summarizes best practices recommendations for legal compliance when implementing e-signatures. eIDAS & E-SIGNATURE: A LEGAL PERSPECTIVE FOLLOW US 2 PART 1 Introduction The 2014 Regulation on Electronic Identification and Trust Services for Electronic Transaction in the Internal Market1 (“eIDAS”) went into effect throughout the European Union (“EU”) on 1 July 2016, replacing the 1999 Directive on electronic signatures2 (“the Directive”). Although the Directive had not been the subject of any disputes in its 16-year history, neither had it been a success. Its objective, to enable the widespread use of electronic signatures to conduct business across borders within the EU, was not met. There Are Three Key Reasons for This: I. Most EU Member States’ laws do not specify any form of signature for commercial contracts other than guarantees or contracts assigning real property. II. Many people mistakenly believed that the Directive mandated the use of advanced electronic signatures supported by a qualified certificate3 in order for an electronic signature to be legally effective. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -
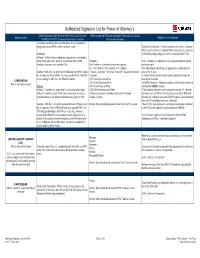
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -

Eidas Regulation Questions & Answers
eIDAS Regulation Questions & Answers on rules applicable to Trust Services as of 1 July 2016 The eIDAS Regulation (Regulation (EU) N°910/2014) on electronic identification and trust services for electronic transactions in the internal market (eIDAS Regulation) adopted by the co-legislators on 23 July 2014 is a milestone as it provides a predictable regulatory environment for electronic identification and trust services, including electronic signatures, seals, time stamps, registered delivery and website authentication. As of 1 July 2016, the provisions applicable to trust services apply directly in the 28 Member States. This means that trust services under eIDAS are no longer regulated by national laws. As a result, the qualified trust services are recognised independently of the Member State where the Qualified Trust Service Provider is established or where the specific qualified trust service is offered. What’s new? What changes with regard to the former eSignature Directive? What must be done at national level? How does it impact market operators? How does it benefit the users (citizens, businesses and public administrations)? What has the Commission done to facilitate the switchover? These questions and many others have been asked along the road since the adoption. We have compiled this Q&A document to help those of you who need to fully understand the new legal framework in order to implement it or reap the benefits of electronic transactions, as well as those of you who are curious about the Regulation’s various implications. I. What is new? How will the legal effect of electronic signature change under eIDAS (compared to the regime under the eSignature Directive) as from 1 July 2016? Since 1 July 2016, when the trust services’ provisions under the eIDAS Regulation entered into application, an electronic signature can only be used by a natural person to “sign”, i.e. -

Esign Law Explained
Electronic Signature Article ESIGN Electronic Commerce and Electronic Signature Law Clarified Copyright © Topaz Systems Inc. All rights reserved. For Topaz Systems, Inc. trademarks and patents, visit www.topazsystems.com/legal. ESIGN Law Clarified Table of Contents Overview ................................................................................................................................... 3 Abstract .................................................................................................................................... 3 Requirements for Legal Contract Enforcement .................................................................... 3 Digital Signature Technologies .............................................................................................. 4 PKI Digital Signatures ........................................................................................................................ 4 Handwritten Electronic Digitized Signatures ....................................................................................... 5 Email, Fax, and Other Simplistic Approaches ..................................................................................... 5 Digital Signature Technology in Open and Closed System Environments ........................ 6 Closed System and PKI ..................................................................................................................... 6 Closed System and Digitized Electronic Signatures ..........................................................................