Domain-Specific Pseudonymous Signatures Revisited
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards Formal Definitions
Covid Notions: Towards Formal Definitions – and Documented Understanding – of Privacy Goals and Claimed Protection in Proximity-Tracing Services Christiane Kuhn∗, Martin Becky, Thorsten Strufe∗z ∗ KIT Karlsruhe, fchristiane.kuhn, [email protected] y Huawei, [email protected] z Centre for Tactile Internet / TU Dresden April 17, 2020 Abstract—The recent SARS-CoV-2 pandemic gave rise to they are at risk, if they have been in proximity with another management approaches using mobile apps for contact tracing. individual that later tested positive for the disease), their The corresponding apps track individuals and their interactions, architecture (most protocols assume a server to participate in to facilitate alerting users of potential infections well before they become infectious themselves. Na¨ıve implementation obviously the service provision, c.f. PEPP-PT, [1], [2], [8]), and broadly jeopardizes the privacy of health conditions, location, activities, the fact that they assume some adversaries to aim at extracting and social interaction of its users. A number of protocol designs personal information from the service (sometimes also trolls for colocation tracking have already been developed, most of who could abuse, or try to sabotage the service or its users3). which claim to function in a privacy preserving manner. How- Most, if not all published proposals claim privacy, ever, despite claims such as “GDPR compliance”, “anonymity”, “pseudonymity” or other forms of “privacy”, the authors of these anonymity, or compliance with some data protection regu- designs usually neglect to precisely define what they (aim to) lations. However, none, to the best of our knowledge, has protect. actually formally defined threats, trust assumptions and ad- We make a first step towards formally defining the privacy versaries, or concrete protection goals. -

Relational-Cultural Perspectives of African American Women with Diabetes and Maintaining Multiple Roles
University of Massachusetts Amherst ScholarWorks@UMass Amherst Doctoral Dissertations Dissertations and Theses November 2017 Relational-Cultural Perspectives of African American Women with Diabetes and Maintaining Multiple Roles Ayesha Ali University of Massachusetts Amherst Follow this and additional works at: https://scholarworks.umass.edu/dissertations_2 Part of the Other Nursing Commons Recommended Citation Ali, Ayesha, "Relational-Cultural Perspectives of African American Women with Diabetes and Maintaining Multiple Roles" (2017). Doctoral Dissertations. 1042. https://doi.org/10.7275/10586793.0 https://scholarworks.umass.edu/dissertations_2/1042 This Open Access Dissertation is brought to you for free and open access by the Dissertations and Theses at ScholarWorks@UMass Amherst. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of ScholarWorks@UMass Amherst. For more information, please contact [email protected]. Relational-Cultural Perspectives of African American Women with Diabetes and Maintaining Multiple Roles A Dissertation Presented by Ayesha Ali Submitted to the Graduate School of the University of Massachusetts Amherst in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY September 2017 College of Nursing © Copyright by Ayesha Ali 2017 All Rights Reserved RELATIONAL-CULTURAL PERSPECTIVES OF AFRICAN AMERICAN WOMEN WITH DIABETES AND MAINTAINING MULTIPLE ROLES A Dissertation Presented By AYESHA ALI Approved as to style and content by: ________________________________________ Cynthia S. Jacelon, Chair ________________________________________ Genevieve E. Chandler, Member ________________________________________ Alexandrina Deschamps, Member ______________________________ Stephen Cavanagh, Dean College of Nursing DEDICATION This is dedicated to my mother and my always supportive husband. ACKNOWLEDGEMENTS I would like to give a heart-felt thanks to my advisor and chair of my dissertation committee, Cynthia Jacelon. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

A Signature Scheme with Unlinkable-Yet-Acountable Pseudonymity for Privacy-Preserving Crowdsensing
A Signature Scheme with Unlinkable-yet-Acountable Pseudonymity for Privacy-Preserving Crowdsensing Victor Sucasas, IEEE Member; Georgios Mantas, IEEE Member; Joaquim Bastos; Francisco Damia˜o; Jonathan Rodriguez, IEEE Senior Member Abstract—Crowdsensing requires scalable privacy-preserving Smart City and crowdsensing participants. From the Smart City authentication that allows users to send anonymously sensing perspective the security concern is twofold. Firstly, sensors reports, while enabling eventual anonymity revocation in case are distributed and carried be citizens who could be malicious of user misbehavior. Previous research efforts already provide users sensing fake data or honest users with defective sensors. efficient mechanisms that enable conditional privacy through Secondly, citizens are rewarded for contributing to the sensing pseudonym systems, either based on Public Key Infrastructure tasks, and hence selfish users could submit their reports several (PKI) or Group Signature (GS) schemes. However, previous schemes do not enable users to self-generate an unlimited number times to increase their profits. From the citizens’ perspective of pseudonyms per user to enable users to participate in diverse the main concern is the location privacy, since crowdsensing sensing tasks simultaneously, while preventing the users from participants submit sensing data together with geolocation participating in the same task under different pseudonyms, which information [7]. Thus the Smart City can identify and locate is referred to as sybil attack. This paper addresses this issue by citizens, which can discourage citizens from participating in providing a scalable privacy-preserving authentication solution the sensing tasks [8],[9],[10]. for crowdsensing, based on a novel pseudonym-based signature scheme that enables unlinkable-yet-accountable pseudonymity. -

The Indexing of Welsh Personal Names
The indexing of Welsh personal names Donald Moore Welsh personal names sometimes present the indexer with problems not encountered when dealing with English names. The Welsh patronymic system of identity is the most obvious; this was normal in the Middle Ages, and traces of its usage survived into the mid-nineteenth century. Patronymics have since been revived as alternative names in literary and bardic circles, while a few individuals, inspired by the precedents of history, are today attempting to use them regularly in daily life. Other sorts of alternative names, too, have been adopted by writers, poets, artists and musicians, to such effect that they are often better known to the Welsh public than the real names. A distinctive pseudonym has a special value in Wales, where a restricted selection of both first names and surnames has been the norm for the last few centuries. Apart from the names themselves, there is in Welsh a linguistic feature which can be disconcerting to those unfamiliar with the language: the 'mutation' or changing of the initial letter of a word in certain phonetic and syntactic contexts. This can also occur in place-names, which were discussed by the present writer in The Indexer 15 (1) April 1986. Some of the observations made there about the Welsh language will be relevant here also. Indexing English names 'Fitzwarin family' under 'F' and 'Sir John de la Mare' According to English practice a person is indexed under 'D' (the last, though French, being domiciled in under his or her surname. First names, taken in England).1 alphabetical order, word by word, are then used to Indexing Welsh names determine the sequence of entries when the same English conventions of nomenclature apply today in surname recurs in the index ('first' = 'Christian' = Wales as much as in England, but there are three 'baptismal' = 'given' = 'forename'). -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -

The DIGEST of Equal Employment Opportunity Law
Home > Federal Agencies > Digest of EEO Law The DIGEST Of Equal Employment Opportunity Law Fiscal Year 2017, Volume 4 Office of Federal Operations September 2017 Inside Selected EEOC Decisions on: Agency Processing Attorney's Fees Class Complaints Compensatory Damages Dismissals Findings on the Merits Under the ADEA Under the EPA Under Rehabilitation Act Under Title VII Under Multiple Bases Retaliation Official Time Remedies Sanctions Settlement Agreements Stating a Claim Summary Judgment Timeliness Article: RACE DISCRIMINATION IN THE 21ST CENTURY WORKPLACE The Digest of EEO Law is a quarterly publication of EEOC's Office of Federal Operations (OFO) Carlton M. Hadden, Director, OFO Jamie Price, Assistant Director, OFO's Special Operations Division Digest Staff Editor: Robyn Dupont Writers: Paula Rene Bruner, Robyn Dupont, Laurel Michel, Saliha Moore, Brittan Muir, Shannon Mumaw, Joseph Popiden, Navarro Pulley, Daniel Tarolli The Digest is now available online through EEOC's homepage at www.eeoc.gov/federal/digest/index.cfm. (The Commission will now redact Complainants' names when it publishes decisions. Beginning on October 1, 2015, all federal sector appellate decisions issued for publication will use a randomly generated name as a substitute for the name of the complainant, rather than the generic term "Complainant." This randomly generated name will consist of a first name and last initial, and will be assigned using a computer program that selects names from a list of pseudonyms bearing no relation to the complainant's actual name.) SELECTED EEOC DECISIONS Agency Processing Agency Failed to Conduct Adequate Investigation. The Commission found that the Agency's investigation was inadequate and lacked the thoroughness required for the fact finder to address whether discrimination occurred. -
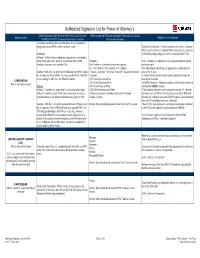
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -

Group Signature-Based Vehicular PKI Without Thousands of Pseudonym Certificates
International Journal of Computer Science and Electronics Engineering (IJCSEE) Volume 4, Issue 3 (2016) ISSN 2320–4028 (Online) Group Signature-based Vehicular PKI without Thousands of Pseudonym Certificates Sokjoon Lee, Hyeok Chan Kwon and Byung Ho Chung communication and its related security technologies. Abstract—V2V(Vehicle-to-Vehicle) communication is a To make V2V message trusted and verifiable, vehicular PKI technology to reduce auto accidents through information or V-PKI that can issue and manage digital certificate is exchange among cars in road such as road status, traffic jam, necessary. SCMS(Security Credential Management System) driving data, etc. To make V2V message trusted and verifiable, [6, 7] was proposed for V-PKI. In this system, pseudonym vehicular PKI or V-PKI that can issue and manage digital certificate is certificates are used to prevent tracking for user privacy. 3,120 necessary. SCMS(Security Credential Management System)[6, 7] was short term pseudonym certificates per OBE should be issued for proposed for V-PKI. In this system, thousands of pseudonym certificates are used to prevent tracking for user privacy, but there are three years. In this case, there are two problems. The first two problems. The first problem is that the private keys with 3,120 problem is that the private keys with 3,120 pseudonym pseudonym certificates should be kept and used timely in HSM of the certificates should be kept and used timely in HSM of the OBU. OBU. The second problem is that thousands certificates and privacy The second problem is that thousands certificates and privacy keys should be re-issued if they are exhausted after three years. -
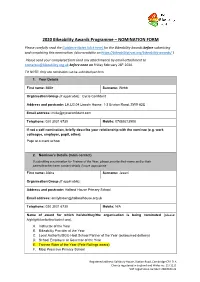
Nomination Form
2020 Bikeability Awards Programme – NOMINATION FORM Please carefully read the Guidance Notes (click here) for the Bikeability Awards before submitting and completing this nomination. (also available on https://bikeabilitytrust.org/bikeability-awards/ ) Please send your completed form (and any attachments) by email attachment to [email protected] before noon on Friday February 28th 2020. TO NOTE: Only one nomination can be submitted per form. 1. Your Details First name: Millie Surname: Webb Organisation/Group (if applicable): Cycle Confident Address and postcode: LH.LG.04 Lincoln House, 1-3 Brixton Road, SW9 6DE Email address: [email protected] Telephone: 020 3031 6730 Mobile: 07889213908 If not a self-nomination, briefly describe your relationship with the nominee (e.g. work colleague, employer, pupil, other): Pupil at a client school 2. Nominee’s Details (main contact) If submitting a nomination for Trainee of the Year, please provide their name and/or their parent/teacher/carer contact details if more appropriate. First name: Aisha Surname: Jesani Organisation/Group (if applicable): Address and postcode: Holland House Primary School Email address: [email protected] Telephone: 020 3031 6730 Mobile: N/A Name of award for which he/she/they/the organisation is being nominated (please highlight/underline/select one): A. Instructor of the Year B. Bikeability Provider of the Year C. Local Authority/SGO Host School Partner of the Year (outsourced delivery) D. School Employee or Governor of the Year E. Trainee Rider of the Year (Pete Rollings award) F. Most Proactive Primary School Registered address: Salisbury House, Station Road, Cambridge CB1 2LA Charity registered in England and Wales no: 1171111 VAT registration number: 268 0103 23 1.