NIST-PEC Meeting, December 2011: Enhanced Privacy ID (EPID)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Key Exchange with Anonymous Authentication Using DAA-SIGMA Protocol
Key Exchange with Anonymous Authentication using DAA-SIGMA Protocol Jesse Walker and Jiangtao Li Intel Labs {jesse.walker, jiangtao.li}@intel.com Abstract. Anonymous digital signatures such as Direct Anonymous Attestation (DAA) and group signatures have been a fundamental building block for anonymous entity authentication. In this paper, we show how to incorporate DAA schemes into a key exchange protocol between two entities to achieve anonymous authentication and to derive a shared key between them. We propose a modification to the SIGMA key exchange protocol used in the Internet Key Exchange (IKE) standards to support anonymous authentication using DAA. Our key exchange protocol can be also extended to support group signature schemes instead of DAA. We present a secure model for key exchange with anonymous authentication derived from the Canetti-Krawczyk key-exchange security model. We prove that our DAA-SIGMA protocol is secure under our security model. 1 Introduction Anonymous digital signatures such as group signatures [22, 2, 5, 6], Direct Anonymous Attestation (DAA) [7, 8, 23, 24, 14], and anonymous credentials [15–17] play an important role in privacy en- hanced technologies. They allow an entity (e.g., a user, a computer platform, or a hardware device) to create a signature without revealing its identity. Anonymous signatures also enable anonymous entity authentication. The concept of group signature scheme was first introduced by Chaum and van Heyst [22] in 1991. In a group signature scheme, all the group members share a group public key, yet each member has a unique private key. A group signature created by a group member is anonymous to all the entities except a trusted group manager. -

SGX Attestation Process Research Seminar in Cryptograpy
SGX attestation process Research seminar in Cryptograpy Author: Hiie Vill Supervisor: Pille Pullonen Introduction Software Guard Extensions (SGX) is a technology, the main function of which is to establish special protected software containers, also known as enclaves. These enclaves can be used for provisioning sensitive parts of a software executable in order to protect them from malicious entities. In order to verify remotely that an application is running securely within an enclave, a remote attestation must be performed. This report gives an overview of the attestation process, the background related to it and the necessary requirements for remote attestation [1][2]. 1. Software Guard Extensions Software Guard Extensions (SGX) is a technology introduced by Intel in 2015, which provides hardware assisted security for the application layer. In itself, SGX is a set of processor extensions for establishing a protected execution environment, referred to as an enclave, and the software related to it. More specifically, enclaves are protected areas of execution in memory, providing a trusted execution environment, even on a compromised platform. In order to protect an application from malicious entities, the software’s code, data and stack are stored within the enclave and protected by hardware enforced access control policies, making the application inaccessible to any malware on the platform. This means that SGX enables applications to defend themselves, protecting any sensitive data used by the application (for example credentials and cryptographic keys), while retaining its integrity and confidentiality [1][2]. 2. Preliminaries In this section, some terminology will be briefly explained that is used in the remote attestation process in order to familiarize the reader with the background information. -

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

No.Ntnu:Inspera:2546742.Pdf (10.61Mb)
Krishna Shingala An alternative to the Public Key Krishna Shingala Infrastructure for the Internet of Things Master’s thesis in Communication Technology Supervisor: Danilo Gligoroski, Katina Kralevska, Torstein Heggebø Master’s thesis Master’s June 2019 An alternative to PKI for IoT PKI for to An alternative NTNU Engineering Communication Technology Communication Department of Information Security and Department of Information Faculty of Information Technology and Electrical Technology of Information Faculty Norwegian University of Science and Technology of Science University Norwegian An alternative to the Public Key Infras- tructure for the Internet of Things Krishna Shingala Submission date: June 2019 Responsible professor: Danilo Gligoroski, IIK, NTNU Supervisor: Danilo Gligoroski, IIK, NTNU Co-Supervisor: Katina Kralevska, IIK, NTNU Co-Supervisor: Torstein Heggebø, Nordic Semiconductor ASA Norwegian University of Science and Technology Department of Information Technology and Electrical Engineering Title: An alternative to the Public Key Infrastructure for the Internet of Things Student: Krishna Shingala Problem description: Internet of Things(IoT) enables participation of constrained devices on the Internet. Limited resources, bandwidth, and power on the devices have led to new protocols. Some examples of IoT driven and driving protocols are: – MQTT, CoAP that are application protocols for IoT; – 6LoWPAN enables efficient support of IPv6 on low power lossy networks; – CBOR enables concise data formatting; and – DTLS enables secure channel establishment over unreliable transport like the UDP. Security is one of the key factors for the success of IoT. TLS/DTLS secures the channel between the servers and the devices. Confidentiality is an important aspect of such a secure channel. Establishing the identity of an entity another. -

Demystifying Internet of Things Security Successful Iot Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M
Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security: Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Chandler, AZ, USA Chandler, AZ, USA Ned Smith David M. Wheeler Beaverton, OR, USA Gilbert, AZ, USA ISBN-13 (pbk): 978-1-4842-2895-1 ISBN-13 (electronic): 978-1-4842-2896-8 https://doi.org/10.1007/978-1-4842-2896-8 Copyright © 2020 by The Editor(s) (if applicable) and The Author(s) This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons license, unless indicated otherwise in a credit line to the material. -

Downloads BC Cessful, Then L Proceeds with Querying S for Available 8: SU (I) Run REKEYING( (I)) in Next DB SU (I) S ∈C C Tepoch Channels
TrustSAS: A Trustworthy Spectrum Access System for the 3.5 GHz CBRS Band Mohamed Grissa⋆, Attila A. Yavuz‡, and Bechir Hamdaoui⋆ ⋆ Oregon State University, grissam,[email protected] ‡ University of South Florida, [email protected] Abstract—As part of its ongoing efforts to meet the increased PU s. GAA users, on the other hand, operate opportunistically, spectrum demand, the Federal Communications Commission in that they need to query the DBs to learn about which 150 3.5 (FCC) has recently opened up MHz in the GHz band spectrum portions are available—not being used by higher tier for shared wireless broadband use. Access and operations in this PU band, aka Citizens Broadband Radio Service (CBRS), will be ( or PAL) users. Even though both PAL and GAA users managed by a dynamic spectrum access system (SAS) to enable are considered as secondary users, in the remaining parts of seamless spectrum sharing between secondary users (SU s) and this paper, for ease of illustration, SU refers to a GAA user, incumbent users. Despite its benefits, SAS ’s design requirements, since only GAA users need to query DBs to learn spectrum SU as set by FCC, present privacy risks to s, merely because availability; PAL users acquire spectrum access via bidding. SU s are required to share sensitive operational information (e.g., location, identity, spectrum usage) with SAS to be able A. Key SAS Requirements to learn about spectrum availability in their vicinity. In this As stipulated by FCC [1], SAS’s capabilities will exceed paper, we propose TrustSAS , a trustworthy framework for SAS that synergizes state-of-the-art cryptographic techniques those of TVWS [4], allowing a more dynamic, responsive with blockchain technology in an innovative way to address these and generally capable support of a diverse set of operational privacy issues while complying with FCC’s regulatory design scenarios and heterogeneous networks [5]. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -
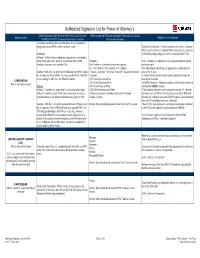
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -

Blockchain-Based Secure Storage Management with Edge Computing for Iot
Article Blockchain-Based Secure Storage Management with Edge Computing for IoT Baraka William Nyamtiga 1, Jose Costa Sapalo Sicato 2, Shailendra Rathore 2, Yunsick Sung 3 and Jong Hyuk Park 2,* 1 Department of Electrical and Information Engineering, Seoul National University of Science and Technology, Seoul 01811, Korea 2 Department of Computer Science and Engineering, Seoul National University of Science and Technology, Seoul 01811, Korea 3 Department of Multimedia Engineering, Dongguk University-Seoul, Seoul 04620, Korea * Correspondence: [email protected]; Tel.: +82-2-970-6702 Received: 27 May 2019; Accepted: 21 July 2019; Published: 25 July 2019 Abstract: As a core technology to manage decentralized systems, blockchain is gaining much popularity to deploy such applications as smart grid and healthcare systems. However, its utilization in resource-constrained mobile devices is limited due to high demands of resources and poor scalability with frequent-intensive transactions. Edge computing can be integrated to facilitate mobile devices in offloading their mining tasks to cloud resources. This integration ensures reliable access, distributed computation and untampered storage for scalable and secure transactions. It is imperative therefore that crucial issues of security, scalability and resources management be addressed to achieve successful integration. Studies have been conducted to explore suitable architectural requirements, and some researchers have applied the integration to deploy some specific applications. Despite these efforts, however, issues of anonymity, adaptability and integrity still need to be investigated further to attain a practical, secure decentralized data storage. We based our study on peer-to-peer and blockchain to achieve an Internet of Things (IoT) design supported by edge computing to acquire security and scalability levels needed for the integration. -

Direct Anonymous Attestation in the Wild 10Th January 2019, RWC 2019, San Jose
Direct Anonymous Attestation in the Wild 10th January 2019, RWC 2019, San Jose Matthew Casey, Liqun Chen, Thanassis Giannetsos, Chris Newton, Ralf Sasse, Steve Schneider, Helen Treharne, Jorden Whitefield 1 Outline DAA in Theory • History • Formal Analysis DAA in the Real World • Vehicular use case • Implementation challenges 2 Direct Anonymous Attestation (DAA) • Anonymous Digital Group Signature scheme • Strong but privacy-preserving authentication • ISO/IEC 20008 2013 • Hardware-backed attestation using Trusted Platform Modules (TPM) • Properties of DAA: • User-controlled Anonymity • User-controlled Traceability • Host controls whether signatures can be linked 3 DAA Schemes Valid • TPM 1.2 (RSA-based) [BCC04] measurement • ISO/IEC 20008-2 mechanism 2 ? • TPM 2.0 (pairing-based) [BCL08, BCL09] • ISO/IEC 20008-2 mechanism 4 & ISO/IEC 11889 • Smaller keys & signatures! • Proposed for FIDO 2 ABC • Enhanced Privacy ID (EPID) [BL07, BL11, BL12] • Used by Intel SGX • Improved revocation 4 TPM 2.0 DAA Vulnerabilities • TPM 2.0 API was insecure [ANZ13] • Static Diffie-Hellman oracle present • Fix: updated protocol • Use of BN P256 curve • 128-bit security reduced to 85-bit • Fix: Move to a larger curve • BN P638 already in standards 5 Overview of DAA Platform Host Non-anonymous attestation Issuer Platform or TPM manufacturer Issues credentials TTPM P JOIN M SIGN A no Valid signature nym ous from a certified * Slide inspired from Anja Lehmann att TPM? est atio https://goo.gl/srqeQk n Verifier Data collector, Bank ...? Formal Analysis of ECC-DAA