Group Signature-Based Vehicular PKI Without Thousands of Pseudonym Certificates
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -
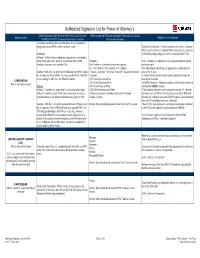
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -
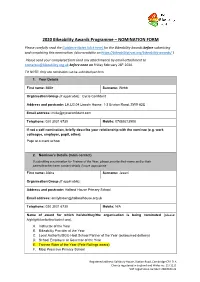
Nomination Form
2020 Bikeability Awards Programme – NOMINATION FORM Please carefully read the Guidance Notes (click here) for the Bikeability Awards before submitting and completing this nomination. (also available on https://bikeabilitytrust.org/bikeability-awards/ ) Please send your completed form (and any attachments) by email attachment to [email protected] before noon on Friday February 28th 2020. TO NOTE: Only one nomination can be submitted per form. 1. Your Details First name: Millie Surname: Webb Organisation/Group (if applicable): Cycle Confident Address and postcode: LH.LG.04 Lincoln House, 1-3 Brixton Road, SW9 6DE Email address: [email protected] Telephone: 020 3031 6730 Mobile: 07889213908 If not a self-nomination, briefly describe your relationship with the nominee (e.g. work colleague, employer, pupil, other): Pupil at a client school 2. Nominee’s Details (main contact) If submitting a nomination for Trainee of the Year, please provide their name and/or their parent/teacher/carer contact details if more appropriate. First name: Aisha Surname: Jesani Organisation/Group (if applicable): Address and postcode: Holland House Primary School Email address: [email protected] Telephone: 020 3031 6730 Mobile: N/A Name of award for which he/she/they/the organisation is being nominated (please highlight/underline/select one): A. Instructor of the Year B. Bikeability Provider of the Year C. Local Authority/SGO Host School Partner of the Year (outsourced delivery) D. School Employee or Governor of the Year E. Trainee Rider of the Year (Pete Rollings award) F. Most Proactive Primary School Registered address: Salisbury House, Station Road, Cambridge CB1 2LA Charity registered in England and Wales no: 1171111 VAT registration number: 268 0103 23 1. -

NIST-PEC Meeting, December 2011: Enhanced Privacy ID (EPID)
Enhanced Privacy ID (EPID) Ernie Brickell and Jiangtao Li Intel Corporation 1 Agenda • EPID overview • EPID usages – Device Authentication – Government Issued ID • EPID performance and standardization efforts 2 Overview of EPID Message, EPID EPID Signature pub-key Message Sign Verify … pvt-key pvt-key pvt-key 1 2 n EPID Signature True / False • EPID is a digital signature scheme with special properties – One group public key corresponds to multiple private keys – Each unique private key can be used to generate a signature – Signature can be verified using the group public key 3 Enhanced Privacy ID (EPID) • Direct Anonymous Attestation (DAA) – A crypto scheme for providing anonymous signatures – DAA is designed specifically for TPM – RSA based DAA scheme adopted by TCG TPM Spec v1.2 • EPID is an extension of DAA – Flexible key generation and signature creation options – Additional revocation capabilities – Pairing based EPID scheme has improved efficiency 4 What is EPID Knows Issuer Secret Issuer EPID group public key Join • Each Member obtains a unique EPID private key Verifier Knows Private key Member Verify • Verifies EPID signature using Sign the group public key • Signs a message using his private key and outputs a signature 5 Privacy Features of DAA/EPID • EPID key issuing can be blinded – Issuer does not need to know Member Private Key • EPID signatures are anonymous • EPID signatures are untraceable – Nobody including the issuer can open an EPID signature and identify the member – This is the main difference between group signatures -

APPLICATION FORM for Recognition As a Refugee Or a Person Who Needs Complementary Protection
APPROVED by Order of the Ministry of Internal Affairs of Ukraine No. 649, dd. 07.09.2011 APPLICATION FORM for recognition as a refugee or a person who needs complementary protection D/M/Y __ __________ 20__ No. I, (Last Name, First Name, Patronymic) hereby request recognition as refugee or person who needs complementary protection because (state the reason(s) of granting the refugee status) Family Members: Husband/Wife Children under 18 Passport: Series __________ No. ________________, Date of Issue and Issuing Authority (if available) Citizenship/Nationality Country of Permanent Residence Place of Residence in Ukraine Availability of Permit for Stay in Ukraine and Its Expiration Date ___ Applicant’s Signature ______________ "___" _________ 20 Legal Representative’s Signature ___________ "___" _________ 20 Translator’s Signature ________________ "___" _________ 20 Supplement. List of attached documents (Part 7, Article 7 of the Law of Ukraine “On Refugees and Persons Who Need Complementary or Temporary Protection in Ukraine") Submitted for further consideration on "___"_____________ 20 (Last Name, Position, Signature of Official of the Migration Service Office/Body) QUESTIONNAIRE for a person applying for recognition as refugee or person who needs complementary protection Case No. _______________ Photo Application’s Registration No. 40 х 60 mm size Registration Date 1. APPLICANT’S DATA 1.1. Last Name 1.1.1. If applicable, indicate the applicant’s previous last name (if a female, indicate maiden name) 1.2. First Name (other names) 1.2.1. Indicate the applicant’s previous first name (if applicable) 1.3. Patronymic 1.4. Sex: Male/Female 1.4.1. -

Application for Schengen Visa This Application Form Is Free
Harmonised application form (1) Application for Schengen Visa This application form is free. Photo 1 Surname (Family name) (x) Write your last name as mentioned on your passport FOR OFFICIAL USE ONLY 2 Surname at birth (Former family name(s)) (x) N/A Date of application: Visa application number: 3 First name(s) (Given name(s)) (x) Write your first name as mentioned on your passport Application lodged at 4 Date of birth (day-month-year) 5 Place of birth 7 Current nationality Write your place of birth as mentioned on Nationality at birth, if different: Embassy/consulate your passport Write your date of birth in day-month-year CAC 6Country of birth order. Example: 25-01-1900 Write Your passport Nationality Write the name of your country Service provider 8 Sex 9 Marital status Commercial intermediary Male Female Single Married Separated Divorced Widow(er) Border Other (please specify) Specify your Gender Specify your Marital status Name: 10 In the case of minors: Surname, first name, address (if different from applicant's) and nationality of parental authority/legal guardian Write the legal guardian Name, Address and Nationality. This section is applicable for Minor applicant (below 18 years). Other File handled by: 11 National identity number, where applicable N/A Supporting documents: 12 Type of travel document Travel document Ordinary passport Diplomatic passport Service passport Official passport Special passport Means of subsistence Other travel document (please specify) Invitation Specify the type of your passport Means of transport 13 Number of travel document 14 Date of issue 15 Valid until 16 Issued by TMI Write your passport number as Specify the authority that issued the passport mentioned on your passport Ex:01-12-1900 Ex:01-12-1905 and the place of issue. -

Cascaded Authorization with Anonymous-Signer Aggregate Signatures Danfeng Yao, Roberto Tamassia
Proceedings of the 2006 IEEE Workshop on Information Assurance United States Military Academy, West Point, NY, 21-23 June 2006 Cascaded Authorization with Anonymous-Signer Aggregate Signatures Danfeng Yao, Roberto Tamassia Abstract— For privacy concerns, the identity of a user or an au- We introduce a decentralized trust management model thorizer may be sensitive information in e-commerce, e- called anonymous role-based cascaded delegation. In this medicine, or peer-to-peer file-sharing (e.g., Kazaa) appli- model, a delegator can issue authorizations on behalf of her role without revealing her identity. This type of delegation cations. An authorizor may not want to reveal his or her protects the sensitive membership information of a delega- identity and role membership at each authorization or au- tor and hides the internal structure of an organization. To thentication. In addition, organizations may want to hide provide an efficient storage and transmission mechanism for credentials used in anonymous role-based cascaded delega- their internal structures from the outside world. tion, we present a new signature scheme that supports both To address these privacy concerns, an anonymous role- signer anonymity and signature aggregation. Our scheme based delegation protocol can be implemented with group has compact role signatures that make it especially suitable for ubiquitous computing environments, where users may signatures, in which a signature proves the membership of a have mobile computing devices with narrow communication signer without revealing the identity [17]. The anonymous bandwidth and small storage units. signing feature of group signatures is particularly suitable for role-based delegation, because what is essential to ver- Keywords: Delegation, anonymity, aggregate signature ifying a delegation credential is the proof of the delega- I. -

Form DS-160 Questions & Answers
Form DS-160 Questions & Answers PERSONAL INFORMATION 1 Surname: Enter your surname as it appears in your passport. Your surname is your last name (or family name). If your surname consists of multiple names, please enter them all. Given Names: Enter your given name as it appears in your passport. Given name includes both your first and middle name. Please enter the exact spelling and name in the order indicated in your passport. Full Name in Native Alphabet: Click “does not apply” if your native language utilizes the alphabet. Have you ever used other names (i.e. maiden, religious, professional, alias, etc.)? If not, select ‘No’. If you used any other names in the past, select ‘Yes’ and list them here. If there are different variations of your name in different documents, you can enter those variations here. Do you have a telecode that represents your name? If yes (i.e., your native language does not utilize the alphabet), you will need to list it here. Sex: Self-explanatory. Marital Status: Self-explanatory. Date of Birth: Enter in the order of ‘day, month, year’. Make sure this date matches your passport. Place of birth: Place where you were born. Write down the city (village/town), state/province and country you were born. Use the current city name (e.g., use “Ho Chi Minh City” and not “Saigon”). State/Province of birth: If State/Province is not applicable, check “does not apply”. Country of birth: Use the current country name. PERSONAL INFORMATION 2 Country/Region of Origin (Nationality): Your nationality is your citizenship country, which may be different from your birth country. -

UHM KLFC MA Application Form
KOREAN LANGUAGE FLAGSHIP CENTER (KLFC) MASTER OF ARTS DEGREE IN KOREAN FOR PROFESIONALS How did you hear about the Korean Language Flagship Center? Please check all that apply. □ Korean-language newspaper □ UHM website □ Korean-language TV/radio □ Former and/or current KLFC student □ University newspaper □ Other Please specify. Please check all the financial aid for which you have applied. □ David L. Boren fellowship □ Korea Foundation Graduate Studies fellowship □ UHM Center for Korean Studies fellowships □ Foreign Language and Area Studies (FLAS) scholarship (administered by UHM School of Pacific and Asian Studies) □ Korean American Scholarship Foundation (KASF) scholarship □ FAFSA-based financial aid □ Other Please specify. Please submit the following application materials in one envelope. 1. KLFC MA program application (six pages plus a 600-word statement of purpose) 2. Three letters of recommendation printed on the recommender’s institutional letterhead, signed, and sealed. *** The letters may be submitted separately by the recommender. By signing below, I certify that all information submitted in the admission process—including the application, the statement of purpose, any supplements, and any other supporting materials—is my own work, is factually true, and is honestly presented. Printed full name Signature Date Page 2 PART I. BIODATA Full name LAST, first, middle Current address Street address City, State Zip Permanent address Street address City, State Zip E-mail UH Email: Non-UH Email: Telephone number Home Cell □ College senior to receive undergraduate degree by August □ Graduate student to receive Master’s degree by August Academic status □ Graduate student to receive doctoral degree by August □ Other Please specify highest degree earned.