Nomination Form
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

Reputation Systems for Anonymous Networks
Reputation Systems for Anonymous Networks Elli Androulaki, Seung Geol Choi, Steven M. Bellovin, and Tal Malkin Department of Computer Science, Columbia University {elli,sgchoi,smb,tal}@cs.columbia.edu Abstract. We present a reputation scheme for a pseudonymous peer-to-peer (P2P) system in an anonymous network. Misbehavior is one of the biggest prob- lems in pseudonymous P2P systems, where there is little incentive for proper behavior. In our scheme, using ecash for reputation points, the reputation of each user is closely related to his real identity rather than to his current pseudonym. Thus, our scheme allows an honest user to switch to a new pseudonym keeping his good reputation, while hindering a malicious user from erasing his trail of evil deeds with a new pseudonym. 1 Introduction Pseudonymous System. Anonymity is a desirable attribute to users (or peers) who par- ticipate in peer-to-peer (P2P) system. A peer, representing himself via a pseudonym, is free from the burden of revealing his real identity when carrying out transactions with others. He can make his transactions unlinkable (i.e., hard to tell whether they come from the same peer) by using a different pseudonym in each transaction. Com- plete anonymity, however, is not desirable for the good of the whole community in the system: an honest peer has no choice but to suffer from repeated misbehaviors (e.g. sending an infected file to others) of a malicious peer, which lead to no consequences in this perfectly pseudonymous world. Reputation System. We present a reputation system as a reasonable solution to the above problem. -
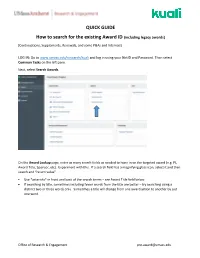
QUICK GUIDE How to Search for the Existing Award ID (Including Legacy
QUICK GUIDE How to search for the existing Award ID (including legacy awards) (Continuations, Supplements, Renewals, and some P&As and Internals) LOG IN: Go to www.umass.edu/research/kuali and log in using your NetID and Password. Then select Common Tasks on the left pane. Next, select Search Awards. On the Award Lookup page, enter as many search fields as needed to hone in on the targeted award (e.g. PI, Award Title, Sponsor, etc). Experiment with this. If a search field has a magnifying glass icon, select it and then search and “return value”. • Use *asterisks* in front and back of the search terms – see Award Title field below. • If searching by title, sometimes including fewer words from the title are better – try searching using a distinct two or three words only. Sometimes a title will change from one award action to another by just one word. Office of Research & Engagement [email protected] • After searching, run a report by selecting spreadsheet (seen below this chart on the left). Suggestions: Save as an Excel Workbook when multiple award records appear in order to hone in on the correct version. Delete columns as needed and add a filter to help with the sort and search process. Office of Research & Engagement [email protected] Identify the correct award Always select the so-called “Parent” award – the suffix is always “-00001” Note: To confirm linkage with the correct legacy award record: • In Kuali, select Medusa in the “-00001” record. • In the list that appears, select any award record except for the “-00001” Parent (the legacy data does not reside in the “Parent” record). -

Diptico Quiropractica Copia
VIII QUEEN Award Guidelines María CHIROPRACTIC Cristina Sponsored by the Banco Santander Award Call for Papers: VIII Queen María Cristina Award. The Real Centro Universitario Escorial-María Cristina invites authors from all nations to submit papers for this award sponsored by the Santander Bank. Category: CHIROPRACTIC AWARD GUIDELINES 1 In regard to the award, an author may submit one or more papers. The paper must be unpublished and authored by one or more people. This is an international award and the papers may be presented in English or Spanish. The research paper must be original, neither published in any journal nor presented to other award contests or conferences. 2 The research papers may be on Basic Sciences (experimental models, Anatomy, Physiology, Biomechanics, Immunology, etc), Clinical Sciences (Analytical and Diagnostic Methods, including intra- and inter-examiner reliability), Clinical Trials, Retrospective Cohort Studies, and areas of specific interest (Anthropology, Epidemiology, and Education) related to Chiropractic. 3 Papers need to be submitted using Times New Roman font in 12 pt with 1.5 line spacing, in a Word-format (.doc or .docx) to the email address [email protected] from an account that ought not to revel the identity of the author. On the first page, the category should be indicated (CHIROPRACTIC), title of the paper, and the pseudonym (pen name) of the author. The real name(s) of the author(s) may not appear on the front page or any page throughout the paper. If the real name is found in any part of the paper or the sending address displays the real identity of the sender, it will be considered disqualified for the award. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -
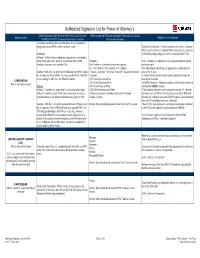
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -

Program Book
PROGRAM BOOK U.S. Congress’ Award for Youth The official guide to earning The Congressional Award, complete with program requirements, best practices, and Record Book. YOUR JOURNEY STARTS HERE The United States Congress established Public Law 96-114: The Congressional Award Act on November 16, 1979 to recognize initiative, service, and achievement in young people. Today, The Congressional Award remains Congress’ only charity and the highest honor a member of the U.S. Senate or House of Representatives may bestow upon a youth civilian. We hope that through your pursuit of this coveted honor, you will not only serve your community and sharpen your own skills, but discover your passions, equip yourself for your future, and see humanity through a new perspective. Your journey awaits. 2 PROGRAM BOOK - V.19 TABLE OF CONTENTS GETTING STARTED 04 PROGRAM REQUIREMENTS 06 PROGRAM AREAS 08 GENERAL ELIGIBILTY 14 AWARD PRESENTATIONS 18 ADVISORS & VALIDATORS 19 RECORD BOOK 21 OUR IMPACT 27 PROGRAM BOOK - V.19 3 GETTING STARTED Earning The Congressional Award is a proactive and enriching way to get involved. This is not an award for past accomplishments. Instead, youth are honored for setting personally challenging goals and meeting the needs of their community. The program is non-partisan, voluntary, and non-competitive. Young people may register when they turn 13 1/2 years old and must complete their activities by their 24th birthday. Participants earn Bronze, Silver, and Gold Congressional Award Certificates and Bronze, Silver, and Gold Congressional Award Medals. Each level involves setting goals in four program areas: Voluntary Public Service, Personal Development, Physical Fitness, and Expedition/Exploration. -
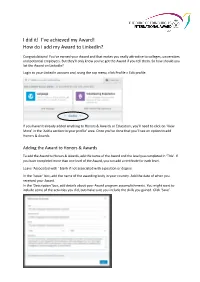
I Did It! I've Achieved My Award! How Do I Add My Award to Linkedin?
I did it! I’ve achieved my Award! How do I add my Award to LinkedIn? Congratulations! You’ve earned your Award and that makes you really attractive to colleges, universities and potential employers. But they’ll only know you’ve got the Award if you tell them. So how should you list the Award on LinkedIn? Login to your LinkedIn account and, using the top menu, click Profile > Edit profile. If you haven’t already added anything to Honors & Awards or Education, you’ll need to click on ‘View More’ in the ‘Add a section to your profile’ area. Once you’ve done that you’ll see an option to add Honors & Awards. Adding the Award to Honors & Awards To add the Award to Honors & Awards, add the name of the Award and the level you completed in ‘Title’. If you have completed more than one level of the Award, you can add a certificate for each level. Leave ‘Associated with ’ blank if not associated with a position or degree. In the ‘Issuer’ box, add the name of the awarding body in your country. Add the date of when you received your Award. In the ‘Description’ box, add details about your Award program accomplishments. You might want to include some of the activities you did, but make sure you include the skills you gained. Click ‘Save’. Adding the Award to Education You can add the Award to Education if you completed your Award through your school, college or university. Once you have added the name of your school and the dates you attended, you can add the name of the Award to ‘Activities and Societies’. -

Form Phs-6342-2
DEPARTMENT OF HEALTH AND HUMAN SERVICES Public Health Service Commissioned Corps INDIVIDUAL HONOR AWARD NOMINATION RECORD PART I OFFICER’S NAME (Last, First, MI) ENTRY ON DUTY DATE PHS RANK (O - 1 through O - 10) PHS PROFESSIONAL CATEGORY SERNO CURRENT ORGANIZATION ORGANIZATIONAL TITLE OR POSITION PROPOSED AWARD PERIOD COVERED (mm/dd/yyyy) From To NOTE: (Synopsis of specific achievement for which the individual is being nominated must be limited to 150 characters.) CITED FOR The nominator certifies that the officer is deserving of the proposed award, and that the accompanying documentation accurately and completely reflects the relevant information. Additionally, the nominator certifies that the officer has not received nor is being nominated for another award for which the basis overlaps this nomination (except as specifically cited). Fill-in Name/Title and Date before Digitally Signing as these and all fields above will lock. NOMINATOR (SIGNATURE) NAME AND TITLE (TYPED) DATE ENDORSEMENTS SUPERVISORY / LINE AUTHORITY SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE OPERATING DIVISION (OPDIV) OR NON-HHS ORGANIZATION AWARDS BOARD CHAIRPERSON SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE APPROVING AUTHORITY SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE OPDIV OR NON-HHS ORGANIZATION AWARDS COORDINATOR SIGNATURE NAME AND TITLE (TYPED) AWARD ENDORSED* DATE *NOTE: If a lower level award is endorsed, give reason in "comment" section below. Also, use the section below to document external agency concurrence as needed. COMMENT DATE ACTION COMMENTS CCIAB Recommended Not Recommended DATE ACTION COMMENTS PHS-CCAB Recommended Not Recommended DATE ACTION COMMENTS SURGEON GENERAL Approved Not Approved PHS-6342-2 (Rev. -

Group Signature-Based Vehicular PKI Without Thousands of Pseudonym Certificates
International Journal of Computer Science and Electronics Engineering (IJCSEE) Volume 4, Issue 3 (2016) ISSN 2320–4028 (Online) Group Signature-based Vehicular PKI without Thousands of Pseudonym Certificates Sokjoon Lee, Hyeok Chan Kwon and Byung Ho Chung communication and its related security technologies. Abstract—V2V(Vehicle-to-Vehicle) communication is a To make V2V message trusted and verifiable, vehicular PKI technology to reduce auto accidents through information or V-PKI that can issue and manage digital certificate is exchange among cars in road such as road status, traffic jam, necessary. SCMS(Security Credential Management System) driving data, etc. To make V2V message trusted and verifiable, [6, 7] was proposed for V-PKI. In this system, pseudonym vehicular PKI or V-PKI that can issue and manage digital certificate is certificates are used to prevent tracking for user privacy. 3,120 necessary. SCMS(Security Credential Management System)[6, 7] was short term pseudonym certificates per OBE should be issued for proposed for V-PKI. In this system, thousands of pseudonym certificates are used to prevent tracking for user privacy, but there are three years. In this case, there are two problems. The first two problems. The first problem is that the private keys with 3,120 problem is that the private keys with 3,120 pseudonym pseudonym certificates should be kept and used timely in HSM of the certificates should be kept and used timely in HSM of the OBU. OBU. The second problem is that thousands certificates and privacy The second problem is that thousands certificates and privacy keys should be re-issued if they are exhausted after three years.