How to Leak a Secret: Theory and Applications of Ring Signatures
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(Linkable) Ring Signature from Hash-Then-One-Way Signature
(Linkable) Ring Signature from Hash-Then-One-Way Signature Xingye Lu Man Ho Au ∗ Zhenfei Zhang Department of Computing Department of Computing Algorand The Hong Kong Polytechnic University The Hong Kong Polytechnic University Boston, USA Hong Kong Hong Kong [email protected] [email protected] [email protected] Abstract—In this paper, we revisit the generic construction of (such as RSA) and three-move type (Type-T) signatures ring signatures from hash-then-one-way type (Type-H) signatures (discrete log (DL) based schemes such as Schnorr). While in proposed by Abe et al. (AOS) in 2004 from the following principle similar to the concrete instantiations, security proof aspects. First, we give a proof for the generic construction, in a strengthened security model. Previously, this was only done for for the AOS generic construction is not formally presented. concrete instantiations, in a weaker model. Second, we extend AOS’s framework to generically construct one-time linkable In 1994, Shor presented a quantum algorithm [4] which can ring signatures from Type-H signatures and one-time signatures. be used to break RSA and DL type digital signatures. Since Lastly, we instantiate the generic construction with an NTRU- then, significant effort has been made to develop practical based Type-H signature: FALCON and obtain a post-quantum quantum computers. Facing the potential threat from quantum linkable ring signature scheme. Our analysis shows that the computers, post-quantum cryptography has attracted more and resulting linkable signature is more efficient than any existing lattice based solutions for small to moderate number of users. -

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

Unique Ring Signatures: a Practical Construction
Unique Ring Signatures: A Practical Construction Matthew Franklin and Haibin Zhang Dept. of Computer Science, University of California, Davis, California 95616, USA {franklin,hbzhang}@cs.ucdavis.edu Abstract. We propose unique ring signatures that simplify and capture the spirit of linkable ring signatures. We use new techniques to provide an instantiation which can be tightly related to the DDH problem in the random oracle model, leading to the most efficient linkable/unique ring signature. Keywords: anonymity, authentication, e-voting system, provable secu- rity, ring signature, tight reduction, unique signature, verifiable random function. 1 Introduction Ring signatures [23] are very useful tools for many privacy-preserving applica- tions. However, they are not adequate in settings where some degree of priva- cy for users must be balanced against limited access. For example, a service provider might have the list of public keys that correspond to all users that have purchased a single access to some confidential service for that day (re- quiring anonymous authentication). For this kind of application, a number of restricted-use ring signatures are proposed. Notable examples include linkable ring signatures [1, 7, 19, 20, 25, 26] and traceable ring signatures [13, 14]. Linkable ring signature asks that if a user signs any two messages (same or different) with respect to the same ring, then an efficient public procedure can verify that the signer was the same (although the user's identity is not revealed). Traceable ring signature is a ring signature scheme where each message is signed not only with respect to a list of ring members, but also with respect to an issue (e.g., identifying label of a specific election or survey). -

Mechanics of Mobilecoin: First Edition
Mechanics of MobileCoin: First Edition exploring the foundations of a private digital currency April 6, 2021, Preview (10/11) v0.0.39 koe1,2 DRAFT INFORMATION: This is just a draft, and may not always be available wher- ever it is currently hosted. The final version will be available at https://github.com/ mobilecoinfoundation. License: `Mechanics of MobileCoin: First Edition' is released into the public domain. 1 [email protected] 2 Author `koe' worked on this document as part of a private contract with, then as an employee of, MobileCoin, Inc. Abstract Cryptography. It may seem like only mathematicians and computer scientists have access to this obscure, esoteric, powerful, elegant topic. In fact, many kinds of cryptography are simple enough that anyone can learn their fundamental concepts. It is common knowledge that cryptography is used to secure communications, whether they be coded letters or private digital interactions. Another application is in so-called cryptocurrencies. These digital moneys use cryptography to assign and transfer ownership of funds. To ensure that no piece of money can be duplicated or created at will, cryptocurrencies usually rely on `blockchains', which are public, distributed ledgers containing records of currency transactions that can be verified by third parties [115]. It might seem at first glance that transactions need to be sent and stored in plain text format to make them publicly verifiable. In truth, it is possible to conceal a transaction's participants, as well as the amounts involved, using cryptographic tools that nevertheless allow transactions to be verified and agreed upon by observers [151]. This is exemplified in the cryptocurrency MobileCoin. -

A Permissioned Blockchain Secure from Both Classical and Quantum Attacks
PQFabric: A Permissioned Blockchain Secure from Both Classical and Quantum Attacks Amelia Holcomb Geovandro Pereira Bhargav Das∗ Michele Mosca Computer Science Combinatorics & Optimization Computer Science Combinatorics & Optimization University of Waterloo University of Waterloo University of Waterloo University of Waterloo Waterloo, Canada Waterloo, Canada Waterloo, Canada Waterloo, Canada [email protected] [email protected] [email protected] [email protected] Abstract—Hyperledger Fabric is a prominent and flexible so- the end of Round 3, about an year from now. A fourth round lution for building permissioned distributed ledger platforms. is also expected in order to select alternate candidates for Access control and identity management relies on a Mem- later standardization. bership Service Provider (MSP) whose cryptographic interface only handles standard PKI methods for authentication: RSA Open source implementations of such algorithms, for and ECDSA classical signatures. Also, MSP-issued credentials instance those provided by the Open Quantum Safe (OQS) may use only one signature scheme, tying the credential- project [1], continually change in order to keep up-to- related functions to classical single-signature primitives. RSA date with both progress in cryptanalysis and per-algorithm and ECDSA are vulnerable to quantum attacks, with an ongoing parameter modifications and optimizations. However, de- post-quantum standardization process to identify quantum- safe drop-in replacements. In this paper, we propose a redesign signing, approving, and implementing post-quantum cryp- of Fabric’s credential-management procedures and related tographic standards is only the first step. There is also the specifications in order to incorporate hybrid digital signatures, gargantuan task of integrating these algorithms into the protecting against both classical and quantum attacks using wide range of existing systems that depend on and are one classical and one quantum-safe signature. -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

Privacy on the Blockchain: Unique Ring Signatures. Rebekah Mercer
Privacy on the Blockchain: Unique Ring Signatures. Rebekah Mercer This report is submitted as part requirement for the MSc in Information Security at University College London. 1 Supervised by Dr Nicolas T. Courtois. arXiv:1612.01188v2 [cs.CR] 25 Dec 2016 1This report is substantially the result of my own work except where explicitly indicated in the text. The report may be freely copied and distributed provided the source is explicitly acknowledged. Abstract Ring signatures are cryptographic protocols designed to allow any member of a group to produce a signature on behalf of the group, without revealing the individual signer’s identity. This offers group members a level of anonymity not attainable through generic digital signature schemes. We call this property ‘plausible deniability’, or anonymity with respect to an anonymity set. We concentrate in particular on implementing privacy on the blockchain, introducing a unique ring signature scheme that works with existing blockchain systems. We implement a unique ring signature (URS) scheme using secp256k1, creating the first implemen- tation compatible with blockchain libraries in this way, so as for easy implementation as an Ethereum smart contract. We review the privacy and security properties offered by the scheme we have constructed, and compare its efficiency with other commonly suggested approaches to privacy on the blockchain. 1 Acknowledgements Thank you to Dr Nicolas Courtois, for introducing me to blockchains and applied cryptography. Thanks to Matthew Di Ferrante, for continued insight and expertise on Ethereum and adversarial security. Thanks also to my mum and dad, for convincing me that can handle an MSc alongside a full time job, and for all the advice along the way! Finally, thanks to the University of Manchester, UCL, Yorkshire Ladies’ Trust, and countless others for their generous grants over the years, without which this MSc would not have been possible. -

ID-Based Ring Signature and Proxy Ring Signature Schemes from Bilinear Pairings
ID-based Ring Signature and Proxy Ring Signature Schemes from Bilinear Pairings Amit K Awasthi1 and Sunder Lal2 1 Department of Applied Science Hindustan College of Science and Technology Farah, Mathura -281122, INDIA awasthi [email protected] 2 Department of Mathematics I. B. S. Khandari, Agra - INDIA Abstract. In 2001, Rivest et al. rstly introduced the concept of ring signatures. A ring signature is a simpli ed group signature without any manager. It protects the anonymity of a signer. The rst scheme proposed by Rivest et al. was based on RSA cryptosystem and certi cate based public key setting. The rst ring signature scheme based on DLP was proposed by Abe, Ohkubo, and Suzuki. Their scheme is also based on the general certi cate-based public key setting too. In 2002, Zhang and Kim proposed a new ID-based ring signature scheme using pairings. Later Lin and Wu proposed a more ecient ID-based ring signature scheme. Both these schemes have some inconsistency in computational aspect. In this paper we propose a new ID-based ring signature scheme and a proxy ring signature scheme. Both the schemes are more ecient than existing one. These schemes also take care of the inconsistencies in above two schemes. Keywords: Cryptography, Digital Signature, Ring Signature, Bilinear pairings, ID-based. 1 Introduction The concept of ring signature was introduced by Rivest, Shamir and Tauman in [13]. The ring signature allows a user from a set of possible signers to convince the veri er that the author of the signature belongs to the set but identity of the author is not disclosed. -

Cryptonote V 2.0 1 Introduction 2 Bitcoin Drawbacks and Some
CryptoNote v 2.0 Nicolas van Saberhagen October 17, 2013 1 Introduction \Bitcoin" [1] has been a successful implementation of the concept of p2p electronic cash. Both professionals and the general public have come to appreciate the convenient combination of public transactions and proof-of-work as a trust model. Today, the user base of electronic cash is growing at a steady pace; customers are attracted to low fees and the anonymity provided by electronic cash and merchants value its predicted and decentralized emission. Bitcoin has effectively proved that electronic cash can be as simple as paper money and as convenient as credit cards. Unfortunately, Bitcoin suffers from several deficiencies. For example, the system's distributed nature is inflexible, preventing the implementation of new features until almost all of the net- work users update their clients. Some critical flaws that cannot be fixed rapidly deter Bitcoin's widespread propagation. In such inflexible models, it is more efficient to roll-out a new project rather than perpetually fix the original project. In this paper, we study and propose solutions to the main deficiencies of Bitcoin. We believe that a system taking into account the solutions we propose will lead to a healthy competition among different electronic cash systems. We also propose our own electronic cash, \CryptoNote", a name emphasizing the next breakthrough in electronic cash. 2 Bitcoin drawbacks and some possible solutions 2.1 Traceability of transactions Privacy and anonymity are the most important aspects of electronic cash. Peer-to-peer payments seek to be concealed from third party's view, a distinct difference when compared with traditional banking. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -
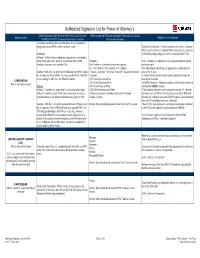
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number. -

Ring Confidential Transactions
ISSN 2379-5980 (online) DOI 10.5195/LEDGER.2016.34 RESEARCH ARTICLE Ring Confidential Transactions Shen Noether,∗ Adam Mackenzie, the Monero Research Lab† Abstract. This article introduces a method of hiding transaction amounts in the strongly decentralized anonymous cryptocurrency Monero. Similar to Bitcoin, Monero is a cryptocur- rency which is distributed through a proof-of-work “mining” process having no central party or trusted setup. The original Monero protocol was based on CryptoNote, which uses ring signatures and one-time keys to hide the destination and origin of transactions. Recently the technique of using a commitment scheme to hide the amount of a transaction has been dis- cussed and implemented by Bitcoin Core developer Gregory Maxwell. In this article, a new type of ring signature, A Multilayered Linkable Spontaneous Anonymous Group signature is described which allows one to include a Pedersen Commitment in a ring signature. This construction results in a digital currency with hidden amounts, origins and destinations of transactions with reasonable efficiency and verifiable, trustless coin generation. The author would like to note that early drafts of this were publicized in the Monero Community and on the #bitcoin-wizards IRC channel. Blockchain hashed drafts are available showing that this work was started in Summer 2015, and completed in early October 2015.17 An eprint is also available at http://eprint.iacr.org/2015/1098. 1. Introduction Recall that in Bitcoin each transaction is signed by the owner of the coins being sent and these signatures verify that the owner is allowed to send the coins. This is entirely analogous to the signing of a check from your bank.